This is the multi-page printable view of this section. Click here to print.
Documentation
- 1: Getting Started
- 2: SamurAI Portal User Guide
- 2.1: Security Incidents
- 2.1.1: The Situation Room
- 2.2: Threat Review
- 2.2.1: Threat Review Detail
- 2.3: Dashboard
- 2.3.1: Telemetry Dashboard
- 2.3.2: Alerts Dashboard
- 2.3.3: Security Incident Dashboard
- 2.4: Telemetry
- 2.4.1: Telemetry Monitoring
- 2.4.2: Integrations
- 2.4.2.1: Supported Integrations
- 2.4.2.2: Create
- 2.4.2.3: High Availability
- 2.4.2.4: Details and Status
- 2.4.2.5: Delete
- 2.4.2.6: Generic Log Sources
- 2.4.3: Collectors
- 2.4.3.1: SamurAI Local Collector
- 2.4.3.2: SamurAI Cloud Collector
- 2.4.4: Network Traffic Analyzer (NTA)
- 2.4.4.1: Requirements
- 2.4.4.2: Deployment
- 2.4.4.3: NTA Details
- 2.4.5: SamurAI Endpoint Agent
- 2.4.5.1: Support and Pre-requisites
- 2.4.5.2: Download and Installation
- 2.4.5.2.1: Download
- 2.4.5.2.2: Microsoft Windows
- 2.4.5.3: Management
- 2.4.5.3.1: Settings and Updates
- 2.4.5.4: Uninstall
- 2.4.5.5: FAQ
- 2.5: Analysis
- 2.5.1: Advanced Query
- 2.5.1.1: Advanced Query Functionality
- 2.5.1.2: Constructing an Advanced Query
- 2.5.1.3: Event field data types
- 2.5.2: Alerts
- 2.5.2.1: Alerts View
- 2.6: Reports
- 2.7: Admin
- 2.7.1: User Management
- 2.7.2: User Settings
- 2.8: Product Integration Guides
- 2.8.1: Amazon CloudTrail
- 2.8.2: Amazon Elastic Load Balancer (ELB)
- 2.8.3: Amazon Virtual Private Cloud Flow Logs
- 2.8.4: Amazon Web Application Firewall (WAF)
- 2.8.5: Apache HTTP Server
- 2.8.6: Aruba Networks ClearPass
- 2.8.7: Azure Virtual Networks
- 2.8.8: BeyondTrust Endpoint Privilege Management (EPM)
- 2.8.9: Blackberry CylancePROTECT
- 2.8.10: Check Point Harmony SASE
- 2.8.11: Check Point Next-Generation Firewall
- 2.8.12: Cisco Identity Services Engine (ISE)
- 2.8.13: Cisco IOS Routers and Switches
- 2.8.14: Cisco Meraki MX Security Appliances
- 2.8.15: Cisco Secure Endpoint
- 2.8.16: Cisco Secure Firewall (ASA Appliances)
- 2.8.17: Cisco Secure Firewall (Firepower Threat Defense)
- 2.8.18: Cisco Umbrella
- 2.8.19: Citrix Netscaler (Formely Netscaler ADC)
- 2.8.20: Claroty Continuous Threat Detection (CTD)
- 2.8.21: Claroty xDome
- 2.8.22: Clavister NetWall
- 2.8.23: Click Studios Passwordstate
- 2.8.24: Crowdstrike Falcon Insight
- 2.8.25: CyberArk Privileged Access Security (PAS)
- 2.8.26: Digital Arts i-Filter
- 2.8.27: ESET PROTECT
- 2.8.28: F5 Application Security Module (ASM)
- 2.8.29: F5 BIG-IP LTM
- 2.8.30: Fortinet FortiAnalyzer
- 2.8.31: Fortinet FortiEDR Cloud
- 2.8.32: Fortinet FortiEDR On-Premise
- 2.8.33: Fortinet FortiGate Next-Generation Firewall
- 2.8.34: Fortinet FortiWeb
- 2.8.35: GestioIP IPAM
- 2.8.36: Google Workspace
- 2.8.37: Heimdal Security
- 2.8.38: Infoblox DDI
- 2.8.39: Linux Authentication
- 2.8.40: Microsoft Azure Activity Logs
- 2.8.41: Microsoft Azure Application Gateway
- 2.8.42: Microsoft Azure Firewall
- 2.8.43: Microsoft Azure Key Vault
- 2.8.44: Microsoft Defender Advanced Hunting
- 2.8.45: Microsoft DHCP Server
- 2.8.46: Microsoft DNS Server
- 2.8.47: Microsoft Entra ID
- 2.8.48: Microsoft Graph (Security)
- 2.8.49: Microsoft IIS
- 2.8.50: Microsoft Office 365
- 2.8.51: Microsoft Windows Event Log
- 2.8.52: Nozomi Networks Guardian
- 2.8.53: Okta Workforce Identity Cloud
- 2.8.54: Palo Alto Networks Cortex XDR Pro
- 2.8.55: Palo Alto Networks: Next-Generation Firewall
- 2.8.56: Palo Alto Networks: Panorama
- 2.8.57: PowerDNS Recursor
- 2.8.58: Proofpoint Targeted Attack Protection (TAP)
- 2.8.59: Samba AD
- 2.8.60: Sophos Central
- 2.8.61: Squid Cache
- 2.8.62: Trellix Endpoint Security (ENS)
- 2.8.63: Trellix Endpoint Security (HX)
- 2.8.64: Trend Micro Vision One
- 2.8.65: Veeam Backup & Replication
- 2.8.66: VMware Carbon Black Cloud Enterprise EDR
- 2.8.67: WatchGuard Firebox
- 2.8.68: Zscaler Internet Access (ZIA)
- 2.8.69: Zscaler Private Access (ZPA)
- 2.9: Assistant
- 3: Knowledgebase
- 3.1: SamurAI MDR
- 3.1.1: What are the Integration Table fields?
- 3.1.2: Best Practices for Custom Status Thresholds
- 3.1.3: Boost Scoring
- 3.1.4: How do I know if my integration is functioning?
- 3.1.5: SamurAI Glossary of Terms
- 3.1.6: Telemetry Data Source Categorization
- 3.2: Support
- 3.2.1: Getting Help
- 4: Services
- 4.1: Managed Detection and Response (MDR)
- 4.1.1: Managed Detection & Response (MDR) Service Description
- 4.1.2: MDR Security Incident Management
- 4.1.3: MDR Threat Reviews
- 4.1.4: Onboarding Managed Detection and Response (MDR)
- 4.2: Additional Subscriptions
- 4.2.1: Dynamic Blocklist
- 4.3: Consulting and Supplemental Services
- 4.3.1: Data Discovery Service Description
- 4.3.2: Incident Response Retainer Service Description
- 4.3.3: SamurAI Cybersecurity Advisor Service Description
- 4.3.4: SamurAI Onboarding Service Description
- 4.3.5: Table-Top Exercise Service Description
- 4.4: Superseded Documents
- 4.4.1: Superseded Managed Detection & Response Service Descriptions
- 4.4.1.1: Managed Detection & Response (MDR) Service Description (v2.0 2025-05-01)
- 4.4.1.2: Managed Detection & Response (MDR) Service Description (v1.0 2023-09-11)
- 4.4.1.3: Managed Detection & Response (MDR) Service Description (v3.0 2025-10-11)
- 4.4.2: Superseded Onboarding Managed Detection & Response
- 5: Reference
- 5.1: What's New in Samurai MDR!
- 5.1.1: SamurAI MDR Release Notes
- 5.2: Announcements
- 5.2.1: SamurAI Portal Authentication Updates
- 5.2.2: Samurai Ticketing and Documentation
- 5.2.3: Samurai MDR Security Incidents and The Situation Room
- 5.3: Legal
- 5.3.1: Beta Product Terms
- 5.3.2: Cookie Statement
- 5.3.3: Data Processing Agreement
- 5.3.4: List of Sub-processors
- 5.3.5: Master Partner Agreement
- 5.3.6: NTT Software Terms of Use
- 5.3.7: Privacy Policy
- 5.3.8: Service Descriptions
- 5.3.9: Support Policy
- 5.3.10: Terms of Service
- 5.3.11: Third Party Software Terms
- 5.3.12: Website Terms and Conditions
- 5.4: Superseded Documents
- 5.4.1: Beta Product Terms
- 5.4.1.1: Product Beta Terms (v1.0 2023-05-25)
- 5.4.1.2: Product Beta Terms (v2.0 2025-06-11)
- 5.4.2: Data Processing Agreement
- 5.4.2.1: Data Processing Agreement (v1.0 2023-05-25)
- 5.4.2.2: Data Processing Agreement (v2 2025-06-11)
- 5.4.3: List of sub processors
- 5.4.4: Master Partner Agreement
- 5.4.4.1: Master Partner Agreement (v1.0 2023-05-25)
- 5.4.4.2: Master Partner Agreement (v2.0 2024-04-25)
- 5.4.4.3: Master Partner Agreement (v3.0 2025-06-11)
- 5.4.5: NTT Software Terms of Use
- 5.4.5.1: NTT Software Terms of Use (v1.0 2023-05-25)
- 5.4.5.2: NTT Software Terms of Use (v2.0 2025-06-11)
- 5.4.6: Terms of Service
- 5.4.6.1: Terms of Service (v1.0 2023-05-25)
- 5.4.6.2: Terms of Service (v2.0 2023-10-24)
- 5.4.6.3: Terms of Service (v3.0 2025-06-11)
- 5.4.7: Third Party Software Terms
1 - Getting Started
1.1 - Getting Started with SamurAI Managed Detection & Response (MDR)
Welcome to the SamurAI MDR service!
Our service requires you to activate and access the SamurAI Portal, therefore follow the steps to get started:
- Complete Activation for access to the application
- Complete Setup to begin sending telemetry data to the SamurAI platform
Activation
You shall receive an email from no-reply@security.ntt to activate your SamurAI Portal account. Follow the instructions to Register Account and gain access.
If you have not received a registration email:
- Check your email filters and ensure no-reply@security.ntt is safe-listed.
- Contact your Account Manager
- Complete the Account Details and Create a Password

- Setup Two-Factor Authentication by following the instructions to download and setup an authenticator app of your choice.

- Once completed enter the verification code from your authenticator app.

- You will now be logged into the SamurAI Portal - Congratulations!
- Bookmark the SamurAI Portal for quick access!
- You will likely want to add additional users, select Management to learn how to invite users to your tenant
- Review Samurai Portal Overview which will get you started with the SamurAI Portal
Now What?
You now have the ability to submit and review tickets via the SamurAI Portal.
With a subscription to the Managed Detection & Response service:
- We will contact you very soon, please review On-boarding Managed Detection and Response (MDR) for an overview of what to expect.
- If you want to get a head start before we contact you please review SamurAI Portal Overview for more information or follow Setup below.
Setup
With access to the SamurAI Portal, you can begin Setup. The data sources we gather telemetry data from may require configuration, download and deployment of a local collector(s) - this is typically for data sources deployed within your network. For cloud based products or services, a cloud collector is typically used which is native to the SamurAI platform and visible in the application..
Collector(s)
Please review SamurAI Collectors to understand and determine what type of collectors you require.
If you already know you require a local collector, jump directly to SamurAI Local Collector for steps to configure, download and deploy a local Collector.
Integrations
Once you have worked through your collector requirements you can then move to integrations. Review Integrations Overview for more information and then select Integrations for steps to integrate your products with the SamurAI platform.
If you have any questions please submit a ticket in the SamurAI Portal
2 - SamurAI Portal User Guide
What is the SamurAI platform?
The SamurAI platform is a vendor-agnostic, cloud native, scalable, API-driven, advanced threat detection, and response platform. The platform is used to deliver the Managed Detection and Response (MDR) service.
What is the SamurAI Portal?
The SamurAI Portal is a centralized web-based application that provides users with access to a variety of features, information and tools - it is essentially your visibility into the Managed Detection and Response service, examples features include:
- self service capabilities to manage and monitor telemetry integrations
- query your data ingested into the SamurAI platform
- view alerts generating by the SamurAI platform and integrated products
- view, update and track security incidents reported to your organization
- submit tickets to the SamurAI Security Operation Center (SOC)
- reporting and summary information on various aspects of the service
Which web browsers are supported?
The SamurAI Portal supports all major browsers, including Chrome, Firefox, Edge and Safari.
Who uses the SamurAI Portal?
Different teams or individuals may use the portal based on their specific areas of responsibility, but generally anyone within your organization that requires service visibility and/or to configure aspects of the service.
Why use the SamurAI Portal?
The SamurAI Portal provides self service capabilities, e.g the ability to configure and download Local Collector(s) which may be required for you to integrate your telemetry data sources and/or add additional users. Once you have integrated your telemetry sources you can review general service metrics and start to query your data. Importantly for the MDR service, the SamurAI Portal also provides access to Security Incidents and the ability to raise tickets as required. Please review useful links below covering various features:
How do I get help?
Review our Getting Help guide for information. You may also wish to review our Support Policy.
What’s next?
If you have not already done so, the first place to start is by integrating your products with the SamurAI platform - this may require you to deploy local collector(s). Review SamurAI Collectors to understand more.
2.1 - Security Incidents
Security Incidents represent actionable security concerns or threat(s) identified as a result of an investigation by our SOC analysts. The Security Incident contains information about the threat(s) and how best to mitigate or minimize the risk.
Security Incidents are reported to you following our Incident Management process and are associated with tickets within the SamurAI Portal and downloadable in PDF format if desired.
Security Incident Notification
As per the Managed Detection and Response Service Description, notifications are provided by telephone or email based on severity:
- Critical severity: Phone / E-mail notifications.
- Low, Medium, High severity: E-mail notifications.
Information capture for notifications are completed during the MDR on-boarding process, however you can update contact details or telephone numbers by raising a ticket, during Threat Reviews and contact with your Cybersecurity Advisor (CSA).
Viewing Security Incidents
To access Security Incidents, click on  Security Incidents from the main menu.
Security Incidents from the main menu.

Figure 1: Example Security Incidents
Security Incident Dashboard

Figure 2: Example dashboard
The Security Incidents dashboard panel displays summary information as:
- Awaiting feedback: Security Incidents awaiting your feedback and/or action
- Awaiting SOC: Security Incidents awaiting response from the SOC
- Closed: all closed Security Incidents
- Total: Total Security Incidents
Security Incident Fields
Find information related to all Security Incident fields (outlined red in Figure 1):
1. Reference
- Reference number of the Security Incident.
2. Severity
- All Security Incidents are categorized with a severity that describes the reported threat.
| Severity | Description |
|---|---|
| Critical | Security Incidents with severe impact that threatens to have a significant adverse impact on the affected systems. These issues have a high probability of spreading or propagating, pose a threat to confidential or otherwise sensitive data or system. Critical security incidents require immediate attention for remediation or mitigation. |
| High | Security incidents where if exploited, these threats could lead to compromise of the system and/or loss of information. Should be investigated in a timely fashion. |
| Medium | Minor security incidents with low risk of spreading or propagation. Should be tracked and followed-up but generally medium threat severity incidents require no immediate action. |
| Low | Observed security related event that could be an indicator of threat or interesting from other perspectives but no direct security incident or threat. |
- The Security Analyst will make an informed decision in assigning the threat severity taking into consideration the specific situation and past experience.
- The assigned severity level will provide you an easy means to quickly assess how important a threat is, and the level of priority which should be assigned in addressing it. This will allow you to re-prioritize your actions so that you can start mitigating any threats quickly.
3. State
- Each Security Incident has an assigned state which quickly allows you to determine who is responsible for follow up.
| State | Description |
|---|---|
| Awaiting Feedback | Security Incident has been created or updated and is awaiting your feedback / response |
| Awaiting SOC | Security Incident is currently awaiting feedback / input from the SOC. |
| Closed | The Security Incident is Closed |
4. Title
- A “one-liner” that describes the content of the reported Security Incident. This field is used when listing tickets and within notifications.
5. MITRE ATT&CK
- To make it easier to understand the threat and perform additional mitigations actions, we categorize a threat according to tactics in the MITRE ATT&CK IT and OT framework.
For more details about MITRE ATT&CK tactics:
- IT: Enterprise Matrix
- OT: ICS Matrix
Reflecting the MITRE tactics, provides the possibility to use MITRE techniques to do additional threat hunting and mitigation.
6. Revision
- If a threat changes, emerges or new relevant info is available, a new revision of the Security Incident will be created. The revision number is reflected in this field.
7. Created
- Date and time of creation of the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC).
8. Updated:
- Date and time of last update to the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC).
What now?
Click on a Security Incident to view more detail and work directly with our SOC within the Situation Room.
2.1.1 - The Situation Room
We adopted the term ‘Situation Room’, often used by military and political establishments as an intelligence management center to monitor and deal with crisis situations.
The SamurAI MDR Situation Room is where you will find detailed information for any given Security Incident reported to you and allows you to communicate with our SOC Analysts.
Enter The Situation Room
To enter the Situation Room, click a Security Incident reported to you from the Security Incident List.

Figure 1: Example Situation Room
The Situation Room is structured as follows, click on the links to learn more:
Security Incident Information

Figure 2: Example incident information
To the left of the window, high level information about the Security Incident will be displayed, some of which is also summarized under the all Security Incidents menu. For clarity we have also included the field information below:
1. Incident Reference # / Title
- Reference number of the Security Incident
- A “one-liner” that describes the content of the reported Security Incident.
2. Severity
- All Security Incidents are categorized with a severity that describes the reported threat.
| Severity | Description |
|---|---|
| Critical | Security Incidents with severe impact that threatens to have a significant adverse impact on the affected systems. These issues have a high probability of spreading or propagating, pose a threat to confidential or otherwise sensitive data or system. Critical security incidents require immediate attention for remediation or mitigation. |
| High | Security incidents where if exploited, these threats could lead to compromise of the system and/or loss of information. Should be investigated in a timely fashion. |
| Medium | Minor security incidents with low risk of spreading or propagation. Should be tracked and followed-up but generally medium threat severity incidents require no immediate action. |
| Low | Observed security related event that could be an indicator of threat or interesting from other perspectives but no direct security incident or threat. |
3. Status
- Each Security Incident has an assigned status which quickly allows you to determine who is responsible for follow up.
| State | Icon | Description |
|---|---|---|
| Awaiting Feedback | Security Incident has been created or updated and is awaiting your feedback / response | |
| Awaiting SOC | Security Incident is currently awaiting feedback / input from the SOC. | |
| Closed | The Security Incident is Closed. |
4. Created
- Date and time of creation of the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default.
5. Updated
- Date and time of update to Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default. This may indicate multiple revisions of the Security Incident.
6. MITRE Categories
- To make it easier to understand the threat and perform additional mitigation actions, we categorize a threat according to tactics in the MITRE ATT&CK IT and OT framework.
For more details about MITRE ATT&CK tactics:
- IT: Enterprise Matrix
- OT: ICS Matrix
Reflecting the MITRE tactics, provides the possibility to use MITRE techniques to conduct additional threat hunting, respond and mitigate threats.
Towards the top of the window additional information is displayed:

Figure 3: Additional information
7. Revision
- If a threat changes, emerges or new relevant information is available, a new revision of the Security Incident will be created and the revision number displayed. e.g Revision 2,3,4.
- You are notified of any new revisions (which is also displayed within the Communication Channel) with the latest revision being displayed as default.
- Selecting the drop down allows you to select the revision number which will update details and evidence appropriately.
8. PDF
- Allows you to download the Security Incident and all details in PDF format.
9. Close Incident
- Allows you to Close the Security Incident.
10. Status
- Icon depiction of the current Security Incident Status. See item (3).
Details
Security Incident details are included within this section as:
Summary
A short summary of the Security Incident.
Description
In this section, the SOC clearly describes the relevant threat and outlines why this poses a risk. The description includes steps and findings through the analysis process where the SOC has used enrichment data and performed Threat Hunting and correlation. The SOC will add Evidence data to support the findings.
The Incident Description can be short or extensive depending on the what is needed to accurately describe the reported threat and associated risk.
Recommendations
A set of actionable mitigation step(s) that can be performed by you to mitigate the threat and bring it to closure. This may include signatures that we recommend to block.
The Recommendations might not be the only way to mitigate the threat. Rather, they provide a suggested approach from the SOC. Ultimately, the choice of the most appropriate mitigation approach rests with the client. When performing mitigation, it is also necessary to understand risks associated with mitigation actions, as there could be impacts on availability and in some cases even data loss could occur. These kinds of impacts may either be known side-effects of mitigation or there may be potential risks associated with errors which could occur during mitigation.
Hosts
Specific hosts applicable to the Security Incident are listed in the table with details which may include IP Address, Hostname, User, Endpoint ID and any actions taken by the SOC e.g if the SOC has isolated an endpoint.
Communication Channel
The Communications Channel provides messaging functionality allowing you to communicate with SOC Analysts in real-time. The editor allows you to construct and format text as desired, your messages are displayed to the left of the Communications Channel whilst all SOC messages are displayed to the right.
Emoji support is also available.
- Windows: Press Windows + . (period) to open the emoji picker.
- macOS: Press Control + Command + Space to open the emoji and symbol picker.

Figure 4: Communications channel
Evidence
Evidence is provided with any given Security Incident to corroborate a SOC analyst investigation and ultimately the Security Incident.
Evidence may be included by the SOC analysts or by a user and will display a timestamp of when it was added building a timeline. Evidence may include:
- Alert data - vendor/product alerts and/or SamurAI platform alerts
- Log data- log data
- Files - e.g PCAP files if available
You can also upload supporting evidence for the security incident, click on Upload File and provide a description (optional) and select the file to upload. The maximum size limit for the file is 50MB.
Selecting the drop down  allows you to view or download the Evidence. For Log data you can pivot to Advanced Query by clicking the link to view the log data and complete further investigation as required.
allows you to view or download the Evidence. For Log data you can pivot to Advanced Query by clicking the link to view the log data and complete further investigation as required.
Indicators
If any Indicators of Compromise (IoC) have been identified applicable to the Security Incident, they will be listed in the table. Indicator types may include (but are not limited to):
- Domain
- IPv4 address
- IPv6 address
- IPv4 address with port
- IPv6 address with port
- MD5
- SHA1
- SHA256
- URL
At the SOC Analyst discretion, they may perform actions based on high confidence IoCs. This may include (based on the type of IoC):
- Add to Dynamic Block List with the intention for any technology subscribed to block the IoC.
- Perform an automated retroactive hunt leveraging the SamurAI Hunting Engine. This automated search is against the last 30 days of data stored within the SamurAI platform. Any findings may result in a new Security Incident.
- Perform a manual retroactive search in certain cases which fall outside of automated scope.
Change History
If there are multiple revisions of the Security Incident, a change history will be displayed providing full visibility into each change.
What Now?
Please refer to our Incident Management process as it is important you understand what is expected of you in the result of a Security Incident as well as our responsibilities.
2.2 - Threat Review
What is a Threat Review?
A Threat Review is a meeting between SamurAI Security Operation Center (SOC) Analysts your assigned Cybersecurity Advisor (if applicable) and your designates with the goal of ensuring your organization derives maximum value from the SamurAI Managed Detection and Response (MDR) service.
Threat Reviews include:
- review of any reported security incidents within the time period
- recommendations to improve detection and response
- follow-up and tracking to ensure reported threats are handled and mitigated
- dialogue around detection and emerging threats
How often are Threat Reviews conducted?
Threat Reviews are conducted quarterly with a standard SamurAI MDR subscription and are typically scheduled during onboarding.
For clients’ that prefer a dedicated senior-level resource and a monthly candence of Threat Reviews the SamurAI Cybersecurity Advisor is available as an add-on subscription.
Where can I find more information?
Review MDR Threat Reviews and/or SamurAI Cybersecurity Advisor Service Description.
Threat Reviews and the SamurAI Portal
Threat Review information is available within the SamurAI Portal after being published by the SOC. Publication of a new Threat Review will typically occur 24hrs before the scheduled meeting.
To access Threat Reviews, click on ![]() Threat Review from the main menu.
Threat Review from the main menu.
The Threat Review landing page displays all Threat Reviews to date for your SamurAI MDR subscription and also documented Action Points.

Figure 1: Example Threat Reviews
Threat Review Fields
Find information related to Threat Review fields:
1. Reference
- Reference number of the Threat Review
2. Status
Each Threat Review has a status:
- Published - a newly created Threat Review for the given time period
- Closed - Threat Review is closed after meeting with client designates
3. Title
- A given title for the Threat Review typically based on the time period.
4. Start Date
- Start date for all detail within the Threat Review.
5. End date
- End date for all detail within the Threat Review.
Action Points
Action Points are typically tasks that have been documented during a Threat Review. Actions points are tracked over the subcription period and once actioned updated as Completed.

Figure 2: Example Action Points
What now?
Click on a Threat Review listed within the landing page to view more detail. Review Threat Review Detail for additional information.
2.2.1 - Threat Review Detail
Information and detail of a Threat Review are presented within the SamurAI Portal. In this article we walk through elements of each Threat Review.
Summary
Summary information of the Threat Review including status, start and end date. These dates will align with you SamurAI MDR subscription (i.e quarterly or monthly) please review How often are Threat Reviews conducted?

Figure 1: Example Summary data
Metrics
For the given Threat Review period, various widgets will be displayed providing you insight to the service. This includes:
Monitoring, Detection & Response Summary
The funnel summarizes:
- telemetry ingested (events) by the SamurAI platform from your configured integrations
- the security detections (alerts) made by the SamurAI platform detection engines and third party vendors which are triaged and investigated by the SamurAI SOC
- the number of security incidents reported to your organization
The funnel infers the value of the service based on the data analyzed focusing on detecting and reporting threats to your organization.

Figure 2: Example Monitoring, Detection & Response summary for the period
Licence usage
Two charts display your utilized data quota (in Gigabytes GB) against your data subscription (an aggregated quota typically based on number of endpoints subscribed). Any overages or under utilization is discussed with you during the Threat Review meeting.

Figure 3: Example Licence usage for the period
Alerts
A donut chart showing the alerts per detection method over the Threat Review period. For a brief explanation of the detection engines please refer to Alerts

Figure 4: Example Alerts per detection method chart
Security Incidents
A chart depicting security incidents reported by severity within the Threat Review period.

Figure 5: Example Security incidents per severity chart
Security Incidents
New Security Incidents
Presented in the table are all Security Incidents reported during the Threat Review period.
Click on a Security Incident and you are redirected you to the Situation Room relevant to the Security Incident. Refer to The Situation Room for additional information.

Figure 6: Example New security incidents table
Highlighted Security Incidents
Any Security Incidents that the SOC determine require attention and discussion during the Threat Review meeting will be included here in table format.
General Tickets
Presented in the table are all general tickets which were created within the Threat Review period.
Click on a General Ticket and you are redirected to the ticket details. Refer to Getting Help for additional information.
New General tickets

Figure 7: Example New general tickets table
Highlighted general tickets
Any General Tickets that the SOC determine require attention and discussion during the Threat Review will be included here in table format.
Threat Intel
The SOC may include Threat Intelligence with references for the Threat Review reporting period.
Other
Any other topics outside of a standard Threat Review are displayed here, for example a client working with a dedicated Cybersecurity Advisor (CSA) with specific requests may be documented here.
Action Points
A list of current Action Points based on all Threat Review, for example recommendation that have been made which may require your action.

Figure 8: Example Action points table
2.3 - Dashboard
2.3.1 - Telemetry Dashboard
The Telemetry dashboard provides a simple self explanatory high level view of your Managed Detection and Response service telemetry metrics.
Summary Panels
Within the dashboard are various summary panels which can be updated based on a specified time period and includes:
- Total number of events ingested into the SamurAI platform
- Total log volume
- Number of integrations (this is current state and not affected by the specified time period)
- Unhealthy integrations (these integrations likely need action, please review the Telemetry Monitoring article for further information)

Figure 1: Example summary panel
Time period
You can update relevant panels to specific date and time ranges. We have included Quick time ranges or you can specify a date and time period.

Figure 2: Date and time selection
Detail Panels
Additional panels provide event data based on products you have integrated with the SamurAI platform.
Events per product

Figure 3: Example events per product bar graph
Events per product

Figure 4: Example events per product pie chart
Data ingested per product

Figure 5: Example data ingested per product table
If you wish to drill down into the events we recommend you use the Advanced Query feature. Review Advanced Query Introduction for more information.
2.3.2 - Alerts Dashboard
The alerts dashboard provides valuable insights into your organization’s security landscape, despite all alerts being handled by the SamurAI Security Operation Center (SOC) it provides visibility into the volume of alerts which potentially lead to validated threats and reported to you as a security incident. Additionally we provide transparency by categorizing the alerts by detection engine and highlighting top threat signatures, whilst you do not need to act upon these alerts, this information demonstrates the SamurAI MDR service’s scale and effectiveness.
Outlined below are examples and an explanation of each panel within the dashboard:
Monitoring, Detection and Response summary
The funnel outlines telemetry ingested (events) by the SamurAI platform from your configured integrations, the security detections (alerts) made by the SamurAI platform detection engines and third party vendors which are triaged and investigated by the SamurAI SOC, and the number of security incidents reported to your organization. The funnel infers the value of the service based on the data analyzed focusing on detecting and reporting threats to your organization.

Figure 1: Example summary
Number of alerts
The total number of alerts analyzed by the SamurAI platform and SOC analysts.

Figure 2: Example number of alerts
Number of unique signatures
The total number of unique alert signatures.

Figure 3: Example unique signatures
Alerts per detection method
Donut chart showing the alerts per detection method. For a brief explanation of the detection engines please refer to Alerts.

Figure 4: Example alerts per detection method chart
Alerts timeline per detection method
Bar graph showing alerts over the time period per detection method.

Figure 5: Example alerts timeline per detection method graph
Top 10 signatures
Top 10 alert signatures from all detection methods.

Figure 6: Example top 10 signatures
Top 10 signatures for Hunting Engine
Top 10 alert signatures for the SamurAI hunting engine.

Figure 7: Example top 10 signatures for hunting engine
Top 10 signatures for Real-time Engine
Top 10 alert signatures for the SamurAI real-time engine.

Figure 8: Example top 10 signatures for real-time engine
Top 10 signatures for vendor
Top 10 alert signatures from your vendor product integrations.

Figure 9: Example top 10 signatures for vendor
2.3.3 - Security Incident Dashboard
The Security Incidents dashboard provides a simple self explanatory high level view of your Managed Detection and Response service security incidents.
Current open security incidents per severity
For more information on severity definitions, refer to Security Incident Fields.

Figure 1: Example current open security incidents by severity
Current open security incidents by state
For more information on state definitions, refer to Security Incident Fields.

Figure 2: Example current open security incidents by state
Current open security incidents (days)
This graph helps you understand how long (in days) a security incident has remained open - this could be in ‘Awaiting feedback’ or ‘Awaiting SOC’ states. Ideally the goal is to remediate and close a security incident as quickly as possible to mitigate risk.

Figure 3: Example current open security incidents (days)
New security incidents per month by severity

Figure 4: Example new security incidents per month by severity)
Security incidents average closing time by severity (days)
This graph shows the average closing time (in days) of security incidents per severity. Ideally the goal should be to keep this average closing down to a minimum.

Figure 5: Example security incidents average closing time by severity (days))
Security incidents total opened/closed per month

Figure 6: Example Security incidents total opened/closed per month))
2.4 - Telemetry
2.4.1 - Telemetry Monitoring
The Telemetry Monitoring view provides you a clear concise view of any integrations that have a status of Warning and Critical.
Access Telemetry Monitoring
- Click Telemetry in the main menu
- Select Telemetry Monitoring

Figure 1: Telemetry monitoring menu and visual indicator
Summary Panel
Telemetry Monitoring provides a summary of all integrations and their current status.

Figure 2: Example summary information
Possible status and their associated descriptions are outlined in the table below:
| Status | Description |
|---|---|
| Pending | Telemetry components installing / provisioning or awaiting status |
| Unknown | The SamurAI platform is unable to determine a status or the Vendor/Product are unknown |
| OK | All components healthy |
| Warning | Warning status will be displayed if the SamurAI platform has not seen any events per the defined threshold. |
| Critical | Critical status will be displayed and an email notification will be sent to registered users (by default) if the SamurAI platform has not seen any events per the defined threshold |
Telemetry Monitoring Table
The table lists all integrations for which the SamurAI Platform has not received events according to defined thresholds for Critical and Warning.
 Figure 3: Example detail table
Figure 3: Example detail table
Clicking on the Integration will navigate you to the Integration Details. For integrations of type Log an events graph will be displayed which may help in troubleshooting.
Additional Table Information
HA Group
- Represents integrations configured in High Availability (HA) mode (e.g. Active/Passive pairs)
- The best member state determines the group’s overall status
- Notifications are sent only for HA groups — not for individual members
- Refer to High Availability and Integrations
Unsupported integrations
- Displayed as Product - unknown and Vendor - unknown
- The SamurAI platform does monitor these telemetry event sources in line with default or customized status thresholds
The Telemetry Monitoring view has the same functionality as the Integration View therefore refer to:
If you want additional information on Integration health, please review How do I know if my integration is functioning?
2.4.2 - Integrations
What is an Integration?
A data source integrated with the SamurAI platform. An integration allows us to collect and ingest telemetry data from multiple sources, including network, endpoint and cloud.
What integrations are available?
We have pre-built integrations to a comprehensive array of 3rd party products and services. Select Supported Integrations to view what is available.
For syslog sources, even if events do not match a supported Integration, we will still ingest events into our data lake as a Generic Log Source. You will still be able to process this data using Advanced Query, and include events from generic log sources within your queries.
How do I integrate data sources?
Select Create for steps to integrate data sources.
Integration Health
Once you have configured Integrations to bring your data into the SamurAI platform, you will also want to make sure that your data sources are healthy. For more details on how to maintain Integration health and troubleshoot problems, please read our article about Integration Health.
What’s Next?
Upon completion of your integrations and validation of health, the platform will start collecting and ingesting telemetry data. Dependent on your phase of MDR onboarding our team will be in contact with you.
2.4.2.1 - Supported Integrations
Integrations facilitate the ingestion of data sources from a wide range of third party vendors. Our Integrations are updated regularly as new and emerging technologies are released.
Each Integration typically requires a configuration guide outlining steps you must follow to integrate your data source to the SamurAI platform.
For details such as transport methods and logs collected please refer to each supporting vendor configuration guide by clicking the link in the table or browsing directly to Product Integration Guides.
All supported integrations are categorized according to our Detection Categorization. For further information refer to the following article: Telemetry Data Source Categorization.
Available configuration guides
In the pipeline
Outlined below are integrations we have in the pipeline however have no committed dates for support. Please note any integration may be influenced by changing business opportunities and client requirements. Please contact NTT for further information or if you require additional support.
| Vendor | Product |
|---|---|
| Cloudflare | Cloudflare |
| OpenBSD | Packet Filter |
| Skyhigh Security | On-Premises SWG |
| Netskope | Netskope SSE |
2.4.2.2 - Create
Create Integration
- From the SamurAI Portal click Telemetry and select Integrations from the main menu.
- Click Create integration.
- Select the product you wish to integrate with the SamurAI platform.
- Click Next. Dependent on how we collect telemetry, the product may be integrated via a Cloud Collector or Local Collector. Follow the steps based on the Collector type:
Cloud Collector
- If the integration is cloud-based you need to select the relevant Cloud Collector. Select the relevant Cloud Collector and click Next.
- If you are using a public cloud storage account you should already have completed the steps in Cloud Collector.
- If no cloud storage is utilized then a default cloud collector is available.
- Select Configuration Guide which will direct you to SamurAI documentation outlining how to configure your product and obtain required fields.
- Once you have configured your product, complete the required fields.
- Select Finish.
Local Collector
- Your Local Collector(s) will be listed. Select the Local Collector that you will integrate the product with.
- Click Next (typically this is the syslog destination host when configuring your device). If you do not have a Local Collector setup and deployed, follow the steps in our SamurAI Local Collector article.
- The Local Collector IP Address will be displayed, copy the IP address or take note of it.
- Click Configuration Guide which will direct you to SamurAI documentation outlining how to configure your product.
- Based on the product, Extended Data Collection may be displayed, if so jump to Extended Data Collection.
- Click Finish
Extended Data Collection
For many products we are able to collect extended data enhancing our threat detection capabilities and accuracy, for example Packet Capture (PCAP) data. This option will be displayed during configuration of an integration.
- If extended data collection is available for the product, you can choose to enable or disable via the toggle. If you choose to disable, Select Finish
- If you choose to enable extended data collection you must complete all the necessary fields. The parameters for each field are derived from following the associated product configuration guide. Once complete, Select Finish
2.4.2.3 - High Availability
If you have products configured in a High Availability configuration e.g. Active/Passive pair you have the option to configure HA Groups.
HA Groups are important for telemetry health monitoring and notifications. An example scenario is if you have an Active/Passive product configuration where the Active node consistently sends data to a local collector, however the Passive node sends intermittent data. In this scenario the Active node status would be reported as OK, however the Passive node status may appear as Critical despite there not being a telemetry ingestion problem.
HA Group telemetry monitoring is handled based on the ‘best’ state of all members e.g in the scenario above if a HA Group has two members and one member has an OK status, and the second member has Critical status the overall group state will be considered OK.
Create HA Group
- Click Telemetry and select Integrations from the main menu
- Click
 (more options) at the top right of the table and select Create HA Group
(more options) at the top right of the table and select Create HA Group - A Create HA Group window will be displayed
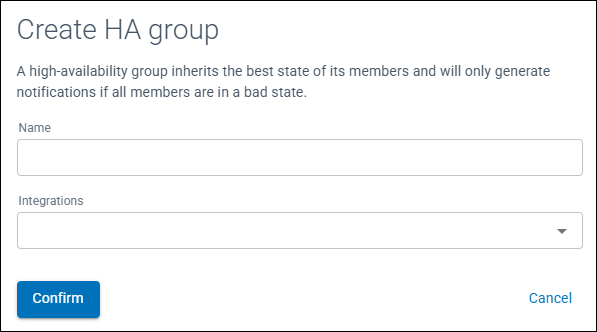
Figure 1: Create HA Group window
- Enter a Name for the HA Group
- From the drop down menu select the integrations to be members of the HA Group
- Click Confirm
Within the Integrations table, the field type HA Group will be displayed with the number of members highlighted.
Edit a HA Group
- Click Telemetry and select Integrations from the main menu
- Click on
 (more options) to the left of the HA Group and select Edit HA Group
(more options) to the left of the HA Group and select Edit HA Group - Add or remove the group members required
- Click Confirm
Delete HA Group
- Click Telemetry and select Integrations from the main menu
- Click on
 (more options) to the left of the HA Group and select Delete HA Group
(more options) to the left of the HA Group and select Delete HA Group - A confirmation window will be displayed, Click Confirm
The HA Group will be deleted and integrations listed within the table.
2.4.2.4 - Details and Status
View Integration
There are multiple methods of viewing your integrations.
To view integrations associated with a specific collector:
- From the SamurAI Portal click Telemetry and select Collectors from the main menu
- Select the relevant Collector
- All integrations associated with the Collector will be displayed with associated information
You can also view all integrations regardless of collector:
- Click Telemetry and select Integrations from the main menu
- An Integrations table will be displayed with all of your Integrations listed
Click on the specific integration to view configuration parameters. You can edit and update a description to help keep track of the integration.
For integrations of type Log an events graph will be displayed. This is a useful indicator of the number of events over a given period and may show spikes and drops in events.
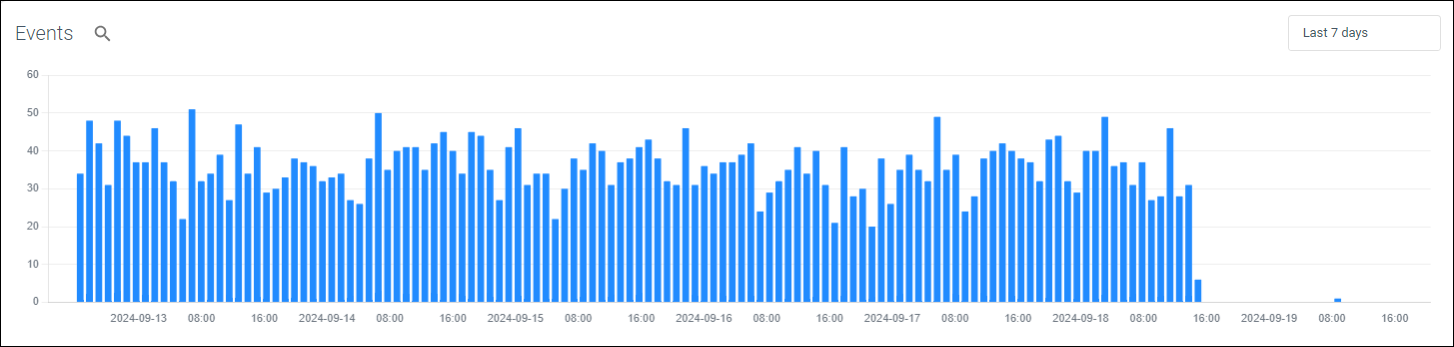
Figure 1: Example events graph
By clicking the time picker you can update the events graph to a specific date and time range. We default to the Last 7 days however have included Quick time ranges.
Figure 2: Data and time selector
From the events graph you can pivot directly into Advanced Query by selecting the magnifying glass icon ( ) to view the underlying event data.
) to view the underlying event data.
Views
You can save filters you set through views. This is useful if, for example, you have a large number of integrations and wish to view only specific products or types of integration.
Click Views to save/reset/delete your different filters. Once saved you can toggle between views.
Figure 3: Views drop down
Integration Status
Potential status displayed are included in the table below:
| Indicator | Status | Description |
|---|---|---|
| Pending | Telemetry components installing / provisioning or awaiting status | |
| Unknown | The SamurAI platform is unable to determine a status or the Vendor/Product are unknown | |
| OK | All components healthy | |
| Warning | Warning status will be displayed if the SamurAI platform has not seen any events per the defined threshold. Refer to Status Thresholds for additional information | |
| Critical | Critical status will be displayed and an email notification will be sent to registered users (by default) if the SamurAI platform has not seen any events per the defined threshold. Refer to Status Thresholds for additional information |
Status Thresholds
The SamurAI platform defines default Warning and Critical thresholds for each integrated product. These thresholds determine when an integration status is reported as Warning or Critical. You can adjust these values per product (e.g for all integrated Palo Alto NG Firewalls) or per integration (e.g for a single Palo Alto NG Firewall). Refer to Custom Thresholds for further information.
To view the default status threshold per product:
- Click on more options (
 ) to the right of the table as depicted:
) to the right of the table as depicted:
Figure 4: Status thresholds option
- Select Status Thresholds per product
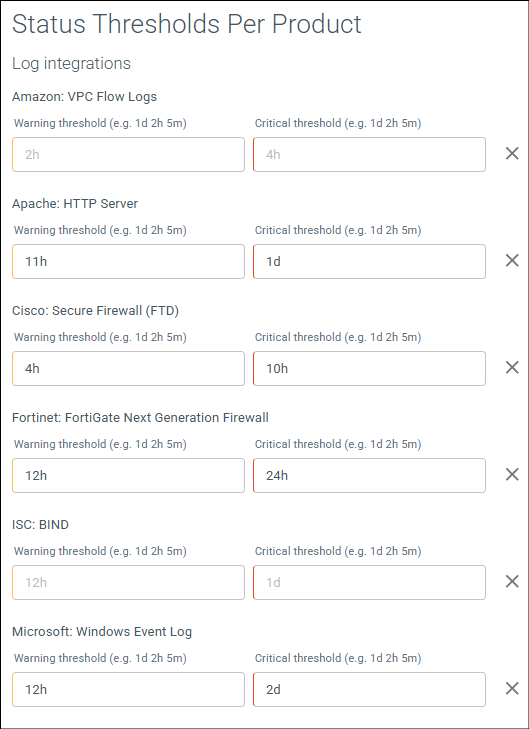
Figure 5: Example default status thresholds per product
Status threshold per product will be displayed, defined in single units or a combination as d (days), h (hours) and m (minutes).
In the example above (Figure 5) for all integrated Cisco: Secure Firewall (FTD) the default thresholds are:
- Warning: 4h. If the SamurAI platform does not receive or ingest any events after 4 hours, the integration status is updated to Warning (displayed within the Integrations Table and the Telemetry Monitoring Table).
- Critical: 10h. If the SamurAI platform does not receive or ingest any events after 10 hours, the integration status is updated to Critical (displayed within the Integrations Table and the Telemetry Monitoring Table, and an email notification is sent to registered users (by default) or as configured by each user.
Custom Thresholds
Custom thresholds can be set per Product (e.g for all integrated Palo Alto NG Firewalls) and/or per Integration (e.g for a single integrated Palo Alto NG Firewall). Set thresholds using a single or combination of time units. Use d for days, h for hours and m for minutes e.g 12h or 1d 2h 10m.
Adjust thresholds per Product
- Click on more options (
 ) to the right of the table
) to the right of the table - Select Status Thresholds per product
- Enter the Warning threshold in days, hours and/or minutes for the Product
- Enter the Critical threshold in days, hours and/or minutes for the Product
- Click Save
Adjust thresholds per Integration
- Click on more options (
 ) to the left of the integration
) to the left of the integration - Select Status Thresholds
- Enter the Warning threshold in days, hours and/or minutes for the integration
- Enter the Critical threshold in days, hours and/or minutes for the integration
- Click Save
Once saved:
- The integration will display an Info icon (
 )
) - Hovering over the icon will display Custom Status Threshold text with the threshold set per status
Integration Email Notifications
By default email notifications are enabled. The SamurAI platform sends email notifications to registered users when an integration is reported as Critical e.g. the SamurAI platform has not receieved or ingested any data from the integrated product according to the defined threshold, however this is fully customizable.
Email notifications can be set per Product (e.g for all Palo Alto NG Firewalls) and/or per Integration (e.g for a single Palo Alto NG Firewall). Registered users can also customize what email notifications they receive. Refer to User Notifications Settings.
Enable or disable email notification per Product
- Click on more options (
 ) to the right of the table
) to the right of the table - Select Notifications Per Product
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting
- Click Save

Figure 6: Example notification settings
Enable or disable email notification per Integration
- Click on more options (
 ) to the left of the integration
) to the left of the integration - Select Notifications
- A Notifications Settings window will be displayed
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting
- Click Save
Hide Integration
Hiding an integration will remove it from the integrations displayed and also from the Telemetry Monitoring view and disable notifications.
Only integrations of type Log can be hidden. Some reasons why you may want to hide an integration include:
- You may want to hide all of your unsupported/generic log source integrations.
- And you do not want to receive notifications if there is an issue with telemetry ingestion to the SamurAI platform.
To hide an integration:
- Find the relevant Log integration within the table
- Click on more options (
 ) select Hide integration
) select Hide integration - A Hide Log Integration window will be displayed, click Confirm
To view any hidden integrations:
- Click on more options (
 ) at the top right of the table and select Hidden log integrations
) at the top right of the table and select Hidden log integrations - A Hidden Log Integrations window will be displayed with hidden integrations
Unhide Integration
- Click more options (
 ) at the top right of the table and select Hidden log integrations
) at the top right of the table and select Hidden log integrations - A Hidden Log Integrations window will be displayed
- Find the relevant Hidden integration
- Click on more options (
 ) to the left of the integration and select Unhide integration
) to the left of the integration and select Unhide integration
2.4.2.5 - Delete
Delete Integration
If you wish to delete an integration associated with a specific Collector:
- From your SamurAI Portal Telemetry and select Collectors from the main menu
- Select the relevant collector from your list
- You will now see all integrations associated with the collector
- Select your integrations
- On the right hand side of the relevant integration, click on
 (more options) and select Delete Integration
(more options) and select Delete Integration - The following warning will appear: ‘Warning: This is a destructive action and cannot be reversed.’. To ensure you intended to delete the integration you will need to type in the highlighted ‘Integration’s Hostname’ and select Delete Integration
You can also delete from the Integrations menu item:
- Click Telemetry and select Integrations from the main menu
- Find and select your integrated product
- On the right hand side of the relevant integration, click on
 (more options) and select Delete Integration
(more options) and select Delete Integration
2.4.2.6 - Generic Log Sources
While we make an effort to support a wide variety of Integrations and different types of log sources, it is possible that there may be a log source that you would like to ingest into the SamurAI platform which we are not able to parse and analyze. This is especially true for events generated via syslog log sources.
The fact that we are not able to use a log source for detections doesn’t mean that it won’t still be useful to ingest into the SamurAI platform. We will ingest any event data, provided via syslog (sent to a SamurAI local collector), into our data lake and you will still be able to analyze that event data using Advanced Query. This allows you to include events from generic log sources when you are performing queries.
If a log source, ingested via syslog, does not match one of our supported integrations, we will ingest the log events, which will still contain, amongst others, the following fields:
- timestamp: the time at which the log message was ingested
- collector: the id of the collector which ingested the event
- host: the source host from which the event was received
- raw: the complete raw log message
You can then proceed to query these events using Advanced Query. For example, the following KQL query finds all the attempts to connect to a host using invalid user ids and then counts the attempts by source IPv4 or IPv6 address:
events | where host == "10.1.1.1" and i(raw contains "Invalid" or raw contains "failed") and raw !contains "connect" | project timestamp, user = extract("user ([a-zA-Z0-9\\-]+) from ", 1, raw), ipaddr = extract(".+ ([0-9a-f]+[\\:\\.][0-9a-f\\.\\:]+) ", 1, raw) | summarize num_attempts = count() by ipaddr| order by num_attempts
The output is ordered by the number of attempts from each IP address, producing a table like the following:
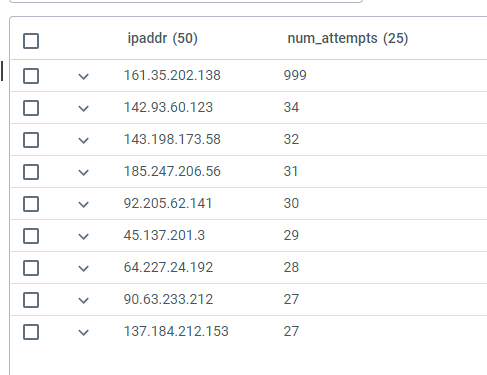
2.4.3 - Collectors
What is a SamurAI Collector?
SamurAI Collectors are used to receive and transport telemetry from your security controls, network devices or cloud services to the SamurAI platform.
There are two types of collectors:
1. Cloud Collector
- Deployed within the SamurAI platform and is used to gather telemetry from cloud services and/or security controls. Various use cases exist with differing requirements based on the Product/Service you are integrating with SamurAI:
- In some cases you simply need to complete the relevant integration and the cloud collector is automatically used.
- When we gather telemetry from public cloud storage (specifically Microsoft Azure storage accounts and Amazon Web Services (AWS) S3 buckets) you must first deploy a cloud collector within the SamurAI platform that is used to monitor your cloud storage for updated telemetry files.
- When we ingest telemetry using Splunk HTTP Event Collection (HEC) you must also first deploy a cloud collector within the SamurAI platform that is used to receieve telemetry data.
2. Local Collector
- Deployed within your environment and is used to gather telemetry from your security controls and network devices. We have packaged the local collector to support multiple formats and envionments.
What type of Collector do you require?
This is dependent on the products you want to integrate with SamurAI:
- For products deployed in your internal network, a Local Collector will be required to gather (pull & push) telemetry data and securely transfer it to the SamurAI platform.
- For cloud based products providing API endpoints, a Cloud Collector will be used to pull the telemetry data and securely transfer it to the SamurAI platform.
- For cloud based products utilizing streaming of telemetry data to cloud storage, a Cloud Collector is also required to retrieve the telemetry data and securely transfer it to the SamurAI platform.
- For products that leverage streaming of telemetry via Splunk HTTP Event Collection (HEC), a Cloud Collector is required to receieve telemetry data to the SamurAI platform.
Next steps:
- Review our Supported Integrations and associated Integration Guides to determine the collector type(s) required. Within each Integration Guide there is a table denoting use of a Local or Cloud Collector, alternatively this is displayed in the SamurAI Portal when working through an integration.
- You may also choose to jump directly to the SamurAI Portal and review integrations
- If you have determined you require a local collector then click on SamurAI Local Collector and follow the steps to create, configure and install.
- If you have determined you require a cloud collector then click on SamurAI Cloud Collector and follow the steps to create and configure.
2.4.3.1 - SamurAI Local Collector
If you have determined that you require a local collector then follow the steps below to learn what you need to get started, create, configure and download a local collector from the SamurAI Portal and ensure it is working as expected.
- Take a moment to understand what you need to get started
- Create, configure and download a Collector
- Install a Collector
- Validate Collector Status
- Collector Status Notifications
- What’s next?
- Deleting a Collector
What you need to get started
Access to the SamurAI Portal and your specific tenant.
A hypervisor to run the virtual machine, for example VMware vSphere, Microsoft Hyper-V, Amazon EC2 or Azure Virtual Machine
- View virtual machine requirements below.
Ensure to make any necessary updates to comply with the collectors connectivity requirements.
A static IP address for the collector and DNS server IP addresses unless you decide to use DHCP.
Access to your products to make necessary changes outlined within the relevant integration guide.
Minimum Virtual Machine Requirements
| Resource | Requirement |
|---|---|
| CPU | 2 vCPU |
| Disk | 500GB disk |
| Memory | 4 GB |
Connectivity required for the Collector
The collector requires connectivity to resources outlined within the table below, you may need to update your security controls e.g firewall to allow this connectivity.
| Function | Protocol | Port | Source | Destination | Details |
|---|---|---|---|---|---|
| Enrolment, Telemetry | TCP | 443 | Collector | *.*.security.ntt nttsecurity.io .nttsecurity.io .*.nttsecurity.io samurai-xdr-prod-westeurope-xgliuoit.azure-api.net | All regular backend communication, telemetry |
| Remote Management | TCP | 443 | Collector | ra.cto.nttsecurity.io deb.releases.teleport.dev apt.releases.teleport.dev | Used for remote administration of collector (this is not mandatory and used when troubleshooting) |
| NTP | UDP | 123 | Collector | Client infrastructure (NTP server(s)) if configured in SamurAI Portal OR 0.ubuntu.pool.ntp.org 1.ubuntu.pool.ntp.org 2.ubuntu.pool.ntp.org 3.ubuntu.pool.ntp.org | Time synchronization |
| DNS | UDP | 53 | Collector | Client infrastructure (DNS server(s)) or external DNS servers (based on your collector configuration) | Domain name resolution |
| Ubuntu updates | TCP | 80, 443 | Collector | *.ubuntu.com api.snapcraft.io | Ubuntu software repository |
| Container Management | TCP | 443 | Collector | docker.com *.docker.com (private container registry) docker.io (private container registry) *.docker.io (private container registry) | Private container registry |
| Amazon Cloud dependencies | TCP | 443 | Collector | *.cloudfront.net | Amazon CDN used by Collector API |
| Log storage | TCP | 443 | Collector | *.s3.*.amazonaws.com | Amazon Cloud storage (this is not mandatory and used when troubleshooting) |
| Telemetry data | (based on product - see Integration guide) | Client Product | Collector | Frequent data transfer (based on product) |
Create, Configure and Download a Collector
Login to the SamurAI Portal, click Telemetry and select Collectors from the main menu
Select Create Collector
Select Local collector
Complete the fields as required.
| Collector name | A nickname for the collector |
|---|---|
| Description (Optional) | A description of your collector, this could be the property name where installed |
| Location (Optional) | Useful if you have collectors in multiple locations |
| Hostname | A hostname for your collector |
| Proxy Server IP (Optional) | Optional HTTP proxy server (URL that contains a hostname or IP address with port e.g https://192.168.1.254:8080) |
| NTP Servers (Optional) | Input your own NTP server IP addresses |
| DHCP or Static | Determine whether the collector will use DHCP or specify your own static IP address and network information |
Select Create Collector once you have completed all relevant fields
Select the Collector you created by clicking the Name used in Step 2
Select Download
The files you need to download are based on your Hypervisor. The options available for download are:
- Configuration
- iso - configuration file for your collector, this file is always required for virtual machines
- Cloud init
- AWS - used to provide cloud-init data to AWS instance
- Azure - used to provide cloud-init data to Azure instance
- Virtual machine
- vmdk - disk image (not needed if using the ova)
- vhdx - virtual hard disk format used for Hyper-V
- ova - virtual machine that the collector will run (includes disk image) for VMware
- Configuration
- Download the iso configuration file and also the relevant file needed for your hypervisor.
Install a Collector
Based on your hypervisor follow the relevant section:
VMware vSphere
Follow the documentation from VMware:
- When asked to provide a virtual machine name, we suggest samurai-nttsh-collector
- Be sure to select the .ova file you downloaded when asked for the file to deploy your virtual machine from.
Once complete follow the VMware article to configure a datastore ISO file
- Be sure to select the .iso file you downloaded when asked to select file
The VM is now ready to be powered on.
Microsoft Hyper-V
Follow the documentation from Microsoft:
- When asked to provide a virtual machine name, we suggest samurai-nttsh-collector
- Use the Virtual Machine Requirements when configuring memory and network
- When asked to Connect Virtual Hard Disk ensure to use the .vhdx file you previously downloaded
- For Installation Options ensure you use the .iso file you previously downloaded
Once you have completed setup of your Collector you should ensure it is running and validate the status within the SamurAI Portal, upon initial setup this can take a little while.
Amazon EC2
Prerequisitve steps:
- Ensure you have the AWS cloud-init.yaml file you downloaded from Create, Configure and Download a Collector.. This file will be used later during EC2 instance deployment.
Follow the vendor documentation from Amazon to launch a EC2 instance:
Perform the following adjustments to the vendor documentation when launching the instance:
- During step 4.a, select Ubuntu as AMI.
- During step 4.b*,* select the latest Ubuntu AMI
- During step 5*,* select a suitable Instance Type based on estimated performance requirements while fulfilling the Minimum Virtual Machine Requirements.
- During step 6 & 7, Set Key pair & Network Settings as per your AWS policies. Ensuring the the Network settings still fulfills the Connectivity required for the Collector.
- Before step 8, modify the Configure storage section with the following settings:
- Adjust the Root Volume to be at least 64 GiB.
- Add a secondary volume with at least 500 GiB according to the Minimum Virtual Machine Requirements.
- Before step 8, expand the section Advanced details and paste in the content of the cloud-init.yaml file into the User data section. Ensure that the check box User data has already been base64 encoded is not enabled.
- Proceed with step 8 and finish the rest of the installation as per the vendor documentation.
Azure Virtual Machine
Prerequisite steps:
- Ensure you have the Azure cloud-init.yaml file you downloaded from Create, Configure and Download a Collector.. This file will be used later during the Virtual Machine instance deployment.
Follow the vendor documentation from Microsoft to launch a Virtual Machine instance:
Perform the following adjustments to the vendor documentation when launching the instance:
- Under the Basic tab, select Ubuntu Server 22.04 LTS as image
- Under the Basic tab, select a suitable Size based on estimated performance requirements while fulfilling the Minimum Virtual Machine Requirements.
- Under the Disk tab, add one data disk with at least 500 GiB according to the Minimum Virtual Machine Requirements.
- Under the Advanced tab, paste the contents of cloud-init.yaml in the Custom datafield.
Validate Collector Status
Click Telemetry and select Collectors from the main menu
Select the relevant Collector from the presented list
View Status
| Indicator | Status | Description |
|---|---|---|
| Pending | Collector components installing / provisioning or awaiting status | |
| Unknown | The SamurAI platform is unable to determine a status | |
| OK | Healthy | |
| Warning | Warning status will be displayed if the Collector is experiencing any issues e.g components are experiencing problems | |
| Critical | Critical status will be displayed and an email notification will be sent to registered users (by default) if the SamurAI platform cannot communicate with the Collector |
After you provision a Collector VM and start it, it will go through a process of installing updates and modules specified in the configuration ISO file which you downloaded. The time taken for this process is dependent on factors like the speed of the hardware you are running the Collector on and connectivity to the repositories that it downloads updates from. In some cases this process can take around 30 minutes.
If you have any problems, please submit a ticket via the SamurAI Portal.
Collector Email Notifications
By default email notifications are enabled. The SamurAI platform sends email notifications to registered users when a Collector is reported as Critical (e.g. the SamurAI platform cannot communicate to the Collector) however this is customizable by users for any Collector status.
Enable or Disable Email Notifications
- Click on More Options (
 ) to the right of the table
) to the right of the table - Select Notifications
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting
- Click Save
You can also achieve this per individual Collector by:
- Click on More Options (
 ) to the left of the Collector
) to the left of the Collector - Select Notifications
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting (send notification).
- Click Save
What’s next?
You should now have a collector running within your environment!
The next step is to start configuring integrations which will allow the SamurAI platform to start receiving your telemetry data.
Select Integrations Overview for more information on integrations and where to start.
If you require high availability for your collector, this can be achieved using the capabilities of your virtualization platform.
Deleting a Collector
If you need to delete a local collector you can do so by following the steps below:
- From your SamurAI Portal click Telemetry and select Collectors
- Select the relevant collector from your list
- On the right hand side of the relevant collector, click on More Options (
 ) and select Delete Collector
) and select Delete Collector - The following warning will appear: ‘Warning: This is a destructive action and cannot be reversed.’. To ensure you intended to delete the collector you will need to type DELETE in the field and select Delete Collector
Replacing a Collector
If for some reason a Local Collector VM is lost due to corruption or damage, such as in the case of a major disk storage failure, you may need to replace your Collector. If this happens, you will need to delete the old Collector in the SamurAI Portal, discard your old Collector VM image and then create a new Collector using the process described to Install a Collector.
- If you need to replace a Collector VM, you cannot re-download the installer ISO for an existing Collector and redeploy it. You must delete the old Collector and replace it with a new one.
- You can re-use the same IP address as your old Collector. This allows you to replace a Collector without re-configuring any log sources which were sending logs to the old Collector.
- When replacing a Collector, any Integrations which were automatically detected and attached to the original Collector will be automatically detected and attached to the new Collector.
- Once you have created the new Collector, you will need to add any Integrations which you were previously using and which you had to previously manually add to the old Collector.
2.4.3.2 - SamurAI Cloud Collector
Deployed within the SamurAI platform, Cloud Collectors are used to:
- Pull telemetry data via an API and securely transfer it to the SamurAI platform.
- Retrieve telemetry data from public cloud storage (Microsoft Azure storage accounts and Amazon Simple Storage Service - S3). The collector monitors for new or updated files in cloud storage and pulls the data into the SamurAI platform for ingestion.
- Receieve telemetry data for ingestion to the SamurAI platform (Splunk HTTP Event Collection - HEC).
The need for a Cloud Collector is based on the specific product being integrated with the SamurAI platform. This will be clearly indicated within the Product Integration Guide.
- For integrations where we leverage an API, you can simply follow the integration guide as a cloud collector will already be available.
- For integrations where we leverage collection of telemetry data from public cloud storage or receipt via Splunk HTTP Event Collector (HEC) there are steps you will need to follow as outlined in the section below Create Cloud Collector.
Create Cloud Collector
From the SamurAI Portal, click Telemetry and select Collectors from the main menu
Select Create Collector
Select Cloud collector
Complete the fields as required.
| Field | Description |
|---|---|
| Collector name | A name for the collector |
| Description (Optional) | A description of your collector |
| Provider | Select the correct Provider |
Select Create Collector
Follow the relevant section below based on your provider.
Microsoft Azure
- Click Deploy to Azure and you will be redirected to the Microsoft Azure login.
- An Azure Resource Manager (ARM) template will be launched, follow the steps and complete the necessary fields within the template:
Project Details
| Field | Description |
|---|---|
| Subscription | Select your Azure subscription |
| Resource Group | Create or select your Resource Group |
Instance Details
| Field | Description |
|---|---|
| Region | Select the Azure region to deploy the Collector into |
| Collector Name | (this is auto populated from the SamurAI Portal Collector name you defined) |
| Collector Id | (this is auto populated from SamurAI) |
| Passkey | (this is auto populated from SamurAI) |
Select Next
Select Review and Create
Upon creation your Collector status will be updated to Healthy.
You can now refer to the relevant Product Integration Guides.
Amazon Web Services (AWS)
- Click Launch Stack and you will be redirected to the AWS login.
Login to your AWS account with administrative permissions.
The SamurAI cloud formation template will be displayed.
If you have an existing S3 Bucket enter the name within the Parameters section under Enable SamurAI ingestion on existing S3 bucket. If you have no existing S3 bucket, leave this field blank and a new S3 bucket will be created.
If you are integrating Cisco Umbrella, be sure to update Cisco Umbrella under the Parameters section to Yes.
Click Create Stack.
Upon creation of the stack your Collector status will be updated to Healthy.
You can now refer to the relevant Product Integration Guides.
Additional required steps when using an existing bucket
- Add the following to the bucket policy, please update the json with the correct bucket name.
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::600502389717:user/samurai-xdr-s3-reader-user"
},
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::BUCKET_NAME",
"arn:aws:s3:::BUCKET_NAME/*"
]
}
Create an Event Notification in the bucket properties.
Enter an Event Name for the notification, leave the Prefix and Suffix boxes blank.
Select All object create events
Under Destination, select SNS Topic and select the SNS topic that was created by the Cloud Formation Template from the drop down and click Save Changes.
Splunk HTTP Event Collector
- If you selected this option you will be presented with the following information:
- API URL
- Token
Copy these entries as you will need them when completing your integration.
Select Close.
You can now refer to the relevant Product Integration Guides.
Validate Collector Status
Select Telemetry and Collectors from the main menu
Select the relevant Collector from the presented list
View Status
| Indicator | Status | Description |
|---|---|---|
| Pending | Collector components installing / provisioning or awaiting status | |
| Unknown | The SamurAI platform is unable to determine a status | |
| OK | Healthy | |
| Warning | Warning status will be displayed if the Collector is experiencing any issues e.g components are experiencing problems | |
| Critical | Critical status will be displayed and an email notification will be sent to registered users (by default) if the SamurAI platform cannot communicate with the Collector |
Collector Email Notifications
By default email notifications are enabled. The SamurAI platform sends email notifications to registered users when a Collector is reported as Critical (e.g. the SamurAI platform cannot communicate to the Collector) however this is customizable by users for any Collector status.
Enable or Disable Email Notifications
- Click on More Options (
 ) to the right of the table
) to the right of the table - Select Notifications
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting
- Click Save
You can also achieve this per individual Collector by:
- Click on More Options (
 ) to the left of the Collector
) to the left of the Collector - Select Notifications
- Toggle the setting to enable or disable by selecting the bell icon. Alternatively you can select the default setting (send notification).
- Click Save
What’s next?
You should now have a collector running.
The next step is to start configuring integrations which will allow the SamurAI platform to collect your telemetry data.
Select Integrations Overview for more information on integrations and where to start.
Deleting a Collector
If you need to delete a Cloud collector you can do so by following the steps below:
- From your SamurAI Portal click Telemetry and select Collectors from the main menu
- Select the relevant collector from your list
- On the right hand side of the relevant collector, click on More Options (
 ) and select Delete Collector
) and select Delete Collector - The following warning will appear: ‘Warning: This is a destructive action and cannot be reversed.’. To ensure you intended to delete the collector you will need to type DELETE in the window and select Delete Collector
2.4.4 - Network Traffic Analyzer (NTA)
What is the NTA?
The SamurAI Network Traffic Analyzer (NTA) is a virtual appliance designed to provide deep visibility into network activity and detect suspicious or malicious behaviour. It can be deployed in a virtual environment or as an AWS EC2 instance, enabling passive monitoring and analysis of east-west and north-south traffic for security threats and anomalies. The NTA compliments existing security measures, delivering deeper insight into traffic and potential risks. Our approach leverages core capabilities to maximize protection and visibility:
Advanced Analytics
- Utilizing machine learning and behavioral analysis, the SamurAI Real-Time Engine (deployed on the NTA) identifies anomalous network activities that could indicate security threats, even those that evade traditional detection methods.
Cyber Threat Intelligence Integration
- We apply our global threat intelligence feeds to enrich network data with context about known malicious actors, emerging threats, and attack patterns. This enhances the accuracy and speed of threat detection.
Network Layer Threat Hunting
- The ability to proactively hunt for threats at the network layer, our SamurAI SOC analysts can identify suspicious patterns and indicators of compromise that automated systems might miss.
Full Packet Capture (PCAP)
- With full packet capture capabilities, the SamurAI NTA allows for comprehensive forensic analysis. In the event of a security incident, SamurAI SOC analysts can reconstruct sessions and examine payloads to understand the full scope and impact of the breach.
What are example use cases for the NTA
- Clients with bespoke or unsupported systems e.g no current integration
- Clients who want to expand their monitoring capabilities leveraging NTTs global threat intelligence
- Clients who want to expand monitoring beyond telemetry data sources integrated into SamurAI MDR, or have systems that do not produce telemetry data with limited threat detection capabilities, refer to Telemetry Data Source Categorization to understand how SamurAI categorizes supported integrations
- Clients who wants to get a quick cyber security grip on new acquisitions
- Clients with distributed branch offices with heterogenous environments and no central log collection
What are the components of the NTA?
The NTA gains visibility of network traffic through traffic mirroring. The NTA monitors the traffic utilizing specific components and generates security detections (alerts) which are sent to the SamurAI platform and triaged, investigated and validated by SOC analysts potentially leading to a security incident reported to you. Refer to the high level diagram below:

Figure 1: The NTA internal components
Traditional IDS Meets Advanced Analytics
- The NTA includes a traditional Intrusion Detection System (IDS) component (Suricata), which provides baseline network monitoring. However, its true strength lies in its ability to decode network protocols, converting them into detailed activity logs.
Real-Time Detection with Advanced Analytics
- These activity logs are processed by the NTA resident SamurAI Real-Time Engine, which applies:
- Advanced Analytics to identify subtle anomalies.
- Threat Intelligence to detect known malicious patterns.
- This approach ensures a proactive, accurate understanding of network activity.
Full Traffic Recording (Stenographer)
- The NTA records all traffic flowing through its sensor.
- This enables comprehensive forensics and retrospective analysis, providing critical insights into historical activity.
Automatic Alert Data Collection
- When an alert is triggered, the NTA automatically captures related packet data and sends it upstream to the SamurAI platform for investigation by SOC Analysts.
- This allows for immediate analysis and a deeper understanding of a potential incident.
What data is analyzed by the NTA?
All network traffic you decide to mirror to the NTA is analyzed. The NTA operates passively monitoring the mirrored traffic without introducing latency or affecting production systems. Even when network traffic is encrypted (e.g HTTPS, SSL/TLS), the NTA can still extract and analyze unencrypted meta data such as IP addresses, port numbers, traffic patterns and correlate this metadata with Threat Intelligence such as known malicious IPs, domains or abnormal behaviors - the NTA can identify potential threats and suspicious activity maintaining effective threat detection without decrypting the payload.
If a client has the capability to decrypt traffic before mirroring to the NTA it is of course advantageous, however we recognize this may not be optimal or available in many cases.
All data resides local to the NTA. Any security detections (alerts) made by the NTA coupled with PCAP data is sent to the SamurAI platform for investigation by SOC Analysts.
What are the deployment options?
There are two options for deploying the SamurAI NTA, both options cover network traffic visibility but are deployed and configured differently.
Who is responsible for the NTA?
You, the client is responsible for installation and configuration of the NTA including the underlying hypervisor/virtual machine settings and/or AWS EC2 configuration and settings.
The SamurAI team is responsible for ensuring health and availability of the NTA which includes maintenance of the Operating System and installed software.
SamurAI will send email notifications to registered users should your NTA encounter any problems, once any issues have been resolved you will be notified again when a healthy status is reached.
If the SamurAI team determines that an NTA is oversubscribed we will liaise with you to determine the best plan forward - this could include requesting you to update assigned virtual resources.
Can I get assistance with deployment of an NTA
Yes, if you require help and guidance with NTA deployment and configuration we can help via the SamurAI Onboarding service. The service is typically utilized by new SamurAI MDR clients to support transition onto SamurAI Managed Detection and Response (MDR) but also for clients who wish to expand or review existing commitment including the NTA.
What’s Next?
Review the requirements to determine what is needed before deployment and configuration of an NTA.
2.4.4.1 - Requirements
What you need to get started
Access to the SamurAI Portal and your specific tenant.
A hypervisor to run the virtual machine, for example VMware ESXi, Microsoft Hyper-V or relevant access to AWS for deployment to an Amazon EC2 instance.
- View Recommended Specifications below.
Make any necessary updates to comply with the NTA Communications Requirements.
A static IP address for the NTA management interface and DNS server IP addresses unless you decide to use DHCP.
Necessary access to configure traffic mirroring to the NTA.
Supported Hypervisors
The NTA supports the follows hypervisors and versions:
| Hypervisor | Version |
|---|---|
| VMware ESXi | 7.x and above |
| Microsoft Hyper-V | 2016 and above |
| Proxmox Virtual Environment | 8.4.1 and above |
Amazon Web Services Support
For AWS deployment, the NTA requires use of AWS Nitro instances that support traffic mirroring, more information can be found at:
Recommended Specifications
There are two NTA sizes which are based on network throughput, therefore note the specifications based on your requirements.
| Medium | Large | |
|---|---|---|
| Throughput | 500 Mbit/s | 1000 Mbits/s |
| CPU | 8 Cores | 8 cores |
| Memory | 52 GB RAM (32 GB RAM for OS and 20GB RAM for ramdisk) | 104 GB RAM (64 GB RAM for OS and 40GB RAM for ramdisk) |
| Disks | System disk: 300GB Data disk 200GB | System disk: 300GB Data disk 200GB |
| Network Interfaces | Management:1 x 1 Gbit/s Network Monitoring:1 x 1 Gbit/s | Management:1 x 1 Gbit/s Network Monitoring:1 x 1 Gbit/s |
Communication Requirements
The NTA requires connectivity to resources outlined within the table below, you may need to update your security controls e.g firewall to allow this connectivity.
| Function | Protocol | Port | Source | Destination | Details |
|---|---|---|---|---|---|
| Enrolment, NTA backend | TCP | 443 | NTA | *.*.security.ntt nttsecurity.io .nttsecurity.io .*.nttsecurity.io samurai-xdr-prod-westeurope-xgliuoit.azure-api.net | All regular backend communication |
| Remote Management | TCP | 443 | NTA | ra.cto.nttsecurity.io deb.releases.teleport.dev apt.releases.teleport.dev | Remote administration of an NTA |
| NTP | UDP | 123 | NTA | Client infrastructure (NTP server(s)) if configured in SamurAI Portal OR 0.ubuntu.pool.ntp.org 1.ubuntu.pool.ntp.org 2.ubuntu.pool.ntp.org 3.ubuntu.pool.ntp.org | Time synchronization |
| DNS | UDP | 53 | NTA | Client infrastructure (DNS server(s)) or external DNS servers (based on your NTA configuration) | Domain name resolution |
| Ubuntu updates | TCP | 80, 443 | NTA | *.ubuntu.com api.snapcraft.io | Ubuntu software repository |
| Container Management | TCP | 443 | NTA | docker.com *.docker.com (private container registry) docker.io (private container registry) *.docker.io (private container registry) | Private container registry |
| Amazon Cloud dependencies | TCP | 443 | NTA | *.cloudfront.net | Amazon CDN used by NTA API |
What’s Next?
Now you have an understanding of the recommended specifications and communication requirements we recommend you proceed to SamurAI NTA Deployment
2.4.4.2 - Deployment
Deployment Considerations
Traffic Source
The NTA is a passive device and relies on client infrastructure to stream a copy of network traffic to the NTA’s monitoring interface. When deploying an NTA in a virtual environment or on AWS EC2, several key considerations should be addressed to ensure effective monitoring and minimal impact on performance:
Resource Allocation
- Ensure the NTA meets the recommended specifications. In some circumstances the resources may not be sufficient and we will work with you on any modifications we recommend based on your traffic throughput once the NTA is deployed and running.
Multi-NTA Deployments
- If your network throughput figures exceed what a single NTA can accomodate you have the option to deploy multiple NTA’s to ensure coverage.
Network Topology and Segmentation
- Map out the virtual network topology and identify where the NTA should be deployed for optimal coverage e.g east-west traffic which typically flows between VM’s connected in the same virtual switch or virtual network, or EC2 instances in the same VPC. Additionally north-south traffic which typically flows between internal and external networks such as web traffic.
Traffic Visibility
- A stream copy of data needs to be provided to the NTA monitoring interface.
Recommendations
Traffic visibility is dependant on your environment, to ensure the best use cases for threat detection in general we recommend:
- Client to internet traffic
- Client to client traffic
- Client to server traffic
Specific traffic which is typically not useful:
- Encrypted traffic e.g any traffic between servers that is encrypted and significant in numbers
- SAN / Backup traffic
Capturing traffic requires configuration of network mirroring or traffic monitoring as outlined below based on your deployment:
Virtual Environment
- Network mirroring on a virtual switch is a method used to capture and analyze traffic passing through a virtual machine (VM) or virtual networks. This is typically achieved by configuring a port mirror, where a copy of the network traffic from one or more source ports is sent to a designated mirror port i.e the NTA mirror interface.
- In a virtualized environment, network mirroring and promiscuous mode can be configured on a virtual switch (such as those in VMware vSphere, Microsoft Hyper-V or others) to facilitate traffic analysis without affecting the networks performance.

Figure 1: The NTA in a virtual environment
Amazon EC2
- For deployment on an EC2 instance, VPC Traffic Mirroring is utilized which allows you to copy traffic from an Elastic Network Interface (ENI).

Figure 2: The NTA running atop AWS
Create Configure and Download an NTA
Login to the SamurAI Portal, click Telemetry and select Network Traffic Analyzer from the main menu
Select Create
Complete the fields as required.
| Field | Description |
|---|---|
| NTA name | A name for the NTA |
| Description (Optional) | A description of your NTA |
| Location (Optional) | Useful if you have NTAs in multiple locations |
| Hostname | A hostname for your NTA |
| Proxy Server address (Optional) | Optional HTTP proxy server (URL that contains a hostname or IP address with port e.g https://192.168.1.254:8080) |
| NTP Servers (Optional) | Input your own NTP server IP addresses |
| Size | Select the appropriate Size based on throughput |
| DHCP or Static | Determine whether the NTA will use DHCP or specify static IP address and network information |
Select Create NTA once you have completed all relevant fields
Select the NTA you created by clicking the NTA Name used in Step 3
Select Download
The files you need to download are based on your deployment and hypervisor. The options available for download are:
- Configuration
- ISO - configuration file for the NTA, this file is always required for virtual machines
- Cloud init
- AWS - used to provide cloud-init data to an AWS EC2 instance
- Virtual machine
- vmdk - disk image (not needed if using the ova)
- vhdx - virtual hard disk format used for Hyper-V
- ova - virtual machine that the NTA will run (includes disk image) for VMware and/or Proxmox
- Configuration
- Download the appropriate files for your deployment.
NTA Installation
Based on your chosen deployment follow the relevant section:
VMware vSphere Installation
Follow the documentation from VMware:
- Provide a virtual machine name.
- Be sure to select the .ova file you downloaded when asked for the file to deploy your virtual machine from.
Once complete follow the VMware article to mount the config ISO file
- Be sure to select the .iso file you downloaded when asked to select file
- The management interface will by default be Network Device (net0)
- The monitoring interface will be by default Network Device (net1) - ensure it is connected to your monitoring network.
- The VM is now ready to be powered on.
- Jump to Deployment Status for next steps.
Proxmox VE Installation
Follow the documentation from Proxmox:
- Follow the steps to first setup a new storage for an import source.
- Refer to the OVA/OVF Import section to import the OVA file you downloaded from the SamurAI Portal.
- Import the NTA configuration ISO file to Proxmox
- Navigate to the Datacenter - Storage section
- Select the storage where you want to store the ISO file
- Click on ISO Images

- Click Upload
- Choose the NTA ISO file and upload it using default settings

- Configure the NTA virtual machine to use the NTA configuration file
- Select the NTA virtual machine and click on Hardware and then Add

- Select CD/DVD Drive

- Check Use CD/DVD disk image file (iso) and locate your NTA configuration file. Click Add

- The management interface will by default be Network Device (net0)
- The monitoring interface will be by default Network Device (net1) - ensure it is connected to your monitoring network
- The VM is now ready to be powered on.
- Jump to Deployment Status for next steps.
Microsoft Hyper-V Installation
Follow the documentation from Microsoft:
- Provide a virtual machine name
- Use the Virtual Machine Requirements when configuring memory and network
- When asked to Connect Virtual Hard Disk ensure to use the .vhdx file you previously downloaded
- For Installation Options ensure you use the .iso file you previously downloaded
- The management interface will by default be Eth0
- The monitoring interface will be by default Eth1 - ensure it is connected to your monitoring network
- The VM is now ready to be powered on.
- Jump to Deployment Status for next steps.
Amazon EC2 Installation
Prerequisitve steps:
- Ensure you have the AWS cloud-init.yaml file you downloaded from Create, Configure and Download an NTA.. This file will be used later during EC2 instance deployment.
Follow the vendor documentation from Amazon to launch a EC2 instance:
Follow the steps outlined in Launch an instance
Perform the following adjustments to the vendor documentation when launching the instance:
- During step 5.a, select Ubuntu as AMI.
- During step 5.b*,* select the latest Ubuntu 24.04 Server AMI
- During step 6*,* select a suitable Instance Type based on estimated performance requirements while fulfilling the Recommended Specifications.
- During step 7 & 7, Set Key pair & Network Settings as per your AWS policies. Ensuring the the Network settings still fulfills the Communications Requirements.
- Before step 9, modify the Configure storage section based on the appropriate NTA size disk requirements.
- Before step 9, expand the section Advanced details and paste in the content of the cloud-init.yaml file into the User data section. Ensure that the check box User data has already been base64 encoded is not enabled.
- Proceed with step 10 and finish the rest of the installation as per the vendor documentation.
- Jump to Deployment Status for next steps.
Deployment Status
Once you have deployed your NTA you can view the deployment steps and status within the SamurAI Portal.
Login to the SamurAI Portal
Click Telemetry and select Network Traffic Analyzer from the main menu
Click the relevant NTA from the presented list
Under General the Status will display as Provisioning.
Deployment Status will be displayed and along with phases and a timestamp. As the NTA builds the status will be listed and cycle green as completed. This includes:
| No. | Deployment Status Message | Description |
|---|---|---|
| 1. | Initial call to backend. Network connectivity ok | First message sent to NTA SamurAI backend, this indicates that the enrolment has started |
| 2. | Refreshing OS package lists | Refreshing operating system software repository information |
| 3. | Upgrading packages | Starting updating operating system |
| 4. | Finished upgrading packages | Operating sytem update completed |
| 5. | Base OS update completed | Post operating system update maintenance jobs completed |
| 6. | Initiating CTS Build X | NTA installer downloaded and started |
| 7. | Running verification to ensure minimal requirements | Installer started self check to verify minimum requirements and software settings |
| 8. | Completed verification to ensure minimal requirements | Self check completed |
| 9. | Request device_id | Requesting device identity |
| 10. | Request init | Started the registration process |
| 11. | Initiator successfully contacted backend | Contacting backend to retreive basic operating information |
| 12. | Downloading configuration | Downloaded configuration |
| 13. | Logged in to dockerhub | Authorized to Docker hub to access private containers |
| 14. | Downloading Docker containers | Containers was downloaded from Docker hub and are ready to be used |
| 15. | Storing device configuration to the backend | Sent device information to the backend |
| 16. | Starting Manager | Starting NTA manager software, more software/containers will be downloaded in the background |
- Once the NTA has completed deployment, Status will display as Not Healthy as individual components need to start. Once complete the Status will be updated to Healthy which may take approximately 5 minutes.
Configure Traffic Mirroring
Once you have deployed your NTA you will need to determine the Monitoring interface.
Login to the SamurAI Portal
Click Telemetry and select Network Traffic Analyzer from the main menu
Click the relevant NTA from the presented list
Select System Information and view Network which will display the Management and Monitoring interfaces. Take note of each MAC address and ensure it aligns with the relevant configuration for your hypervisor or AWS EC2 configuration.
You will now need to configure traffic mirroring to the monitoring interface of the NTA. Based on your chosen deployment. We advise you to refer to vendor documentation for traffic mirroring as environments may differ. We have provided some useful links based on your deployment model:
VMware VSphere
Microsoft Hyper-V
The following Microsoft documentation is based on Microsoft Defender for IoT, however is applicable to traffic mirroring configuration in general.
Amazon EC2
Delete an NTA
If you need to delete an NTA you can do so by following the steps below:
From the SamurAI Portal click Telemetry and select Network Traffic Analyzer from the main menu
Select the relevant NTA from your list
On the left hand side of the relevant NTA, click on
 (more options) and select Delete NTA
(more options) and select Delete NTAThe following warning will appear: ‘Warning: This is a destructive action and cannot be reversed.’. To ensure you intended to delete the NTA you will need to type DELETE in the field and select Delete NTA
What’s Next?
You have now deployed and configured your NTA. Refer to NTA Details.
2.4.4.3 - NTA Details
In this article all elements of the Network Traffic Analyzer are outlined to help you understand the panels available.
List all NTAs
Login to the SamurAI Portal
Click Telemetry and select Network Traffic Analyzer from the main menu
A list of all NTAs will be displayed. Various fields are displayed based on information you included when creating the NTA.
Click on an entry to drill into an NTA’s details.
General
The General panel of an NTA provides an overview of the NTA and status.
| Field | Description |
|---|---|
| Status | Status of the NTA. See NTA status for list of potential statuses |
| Description | A decription field for your NTA. You can edit this field at any time |
| Location | Populated from Location specified during creation of the NTA |
| Hostname | Hostname specified during creation of the NTA |
| Size | The size selected during creation of the NTA |
NTA Status
| Indicator | Status | Description |
|---|---|---|
| Pending | NTA components installing / provisioning or awaiting status | |
| Unknown | The SamurAI platform is unable to determine a status | |
| OK | Healthy | |
| Warning | Warning status will be displayed if the NTA is experiencing any issues e.g components are experiencing problems | |
| Critical | Critical status will be displayed and an email notification will be sent to registered users if the SamurAI platform cannot communicate with the NTA |
Current Status
The Current Status widget provides a visual representation of the CPU, Memory and Disk usage of the NTA. Each metric is displayed as a half-donut chart, offering a quick visual snapshot of system load.
| Metric | Description |
|---|---|
| CPU Utilization | Displays the percentage utilization across all CPU cores. |
| Memory Utilization | Displays the percentage of system memory consumed. |
| Disk Utilization / | Represents the percentage of storage space used for the system disk. |
| Disk Utilization /srv | Represents the percentage of storage space used for the data disk. Monitoring this metric ensures sufficient space for data/memory cache |
This widget may also include status messages of individual components of the NTA, this will assist with identifing any problems and should be included if you submit a ticket with the SamurAI SOC.
NTA Email Notifications
The SamurAI platform will send email notifications to registered users should your NTA status change to Critical. Once any issues have been resolved, you will also be notified again when rectified. Users have the option to enable or disable notifications.
Enable or Disable Email Notifications
- From the NTA Table view, click on More Options (
 ) to the right of the NTA View
) to the right of the NTA View - Select Notifications Settings
- Toggle the setting to enable or disable by selecting the relevant icon per listed NTA. Alternatively you can select the default setting (send notification).
- Click Save.
You can also achieve this per individual NTA by:
- From the NTA Table view, click on More Options (
 ) to the left of the NTA.
) to the left of the NTA. - Select Notifications
- Toggle the setting to enable or disable by selecting the relevant icon. Alternatively you can select the default setting (send notification).
- Click Save.
System Information
The System Informatiom panel displays important NTA system information and metrics including:
System
| Field | Description |
|---|---|
| Operating System | The NTA leverages Ubuntu, it is our repsonsibility to maintain the Operating System. |
| CPU | CPU information captured |
| Cores | No. of physical and logical cores of the NTA |
| Memory | Total memory of the NTA |
| Swap | Allocated disk space used as virtual memory |
Storage
| Field | Description |
|---|---|
| Mount | Directory where storage device or parition is attached to the file system |
| Device | Represents the virtual storage medium by path or Amazon EBS volume |
| Size | Capacity of storage device or partition |
| Usage | Amount of storage consumed in % |
Network Management
| Field | Description |
|---|---|
| Configuration | Static or DHCP |
| IPv4 | The assigned IP address. The Monitoring interface will not have an IP address |
| Proxy server | Proxy server configured during cofiguration creation |
| NTP servers | Network time protocol servers configured during configuration creation |
| Interface | Virtual adapter |
| Type | Management interface |
| MAC | Unique identifier assigned to the interface |
| Current Bandwidth | The data transfer rate of the network interface measured in Mbit/s |
Network Monitoring
| Field | Description |
|---|---|
| Interface | Virtual adapter |
| Type | Monitoring interface |
| MAC | Unique identifier assigned to the interface |
| Current Bandwidth | The data transfer rate of the network interface measured in Mbit/s |
Metrics
All metrics displayed are by default over the past 2 hours however you can adjust via the Time Picker
| Metric | Description |
|---|---|
| CPU Utilization | Displays the percentage utilization across all CPU cores. High usage may indicate heavy traffic analysis or potential system strain |
| Memory Utilization | Displays the percentage of system memory consumed. Persistent high usage could impact performance and may require optimization |
| Disk Utilization | Represents the percentage of storage space used across each disk mount. Monitoring this metric ensures sufficient space for traffic data and system operations |
| Bandwidth Utilization | Displays bandwidth utilization of the mirror interface in Mbit/s |
Alerts
The Alerts panel displays security detections made by the NTA.
You do not have to act on any alerts as the SamurAI SOC analysts triage, investigate and validate alerts as part of the Managed Detection & Response (MDR) service.
As alerts are validated by the SamurAI SOC analysts and investigated, they may potentially lead to a reported Security Incident and are marked accordingly. Our strategy includes visibility and transparency of the service we provide to you therefore this feature provides you that visibility showcasing the value of the NTA and service.
Alerts Summary
Alerts are summarized in a panel which can be updated based on a specified time period and includes:
- Security Incidents - the total number of security incidents reported to you that may correspond to one or more alerts.
- Alerts - the total number of alerts detected by the NTA.
- Real-time engine- the total number of alerts created by the NTA resident SamurAI real-time engine.
- Vendor - the total number of alerts created by the NTA resident Intrusion Detection System (IDS) - Suricata.
Filters
Various filters are available to determine the alerts to be displayed.

Figure 1: Time and Display filter
The total number of alerts within the alerts table in displayed to the left of the Time Period filter.
Time period
You can update all panels to specific date and time ranges. We default to the Last 24 hours however have included Quick time ranges.

Figure 2: Date and time selection
Display Filter
Enter any values you wish to filter and highlight within the display filter.

Figure 3: Display filter
Alert Column Filter
Adjust and show/hide any of the column values within the Alert Table.

Figure 4: Alert column filter
Alerts Table
All alerts related to the NTA are listed within the alert table, it is important to note is that the table is limited to 10,000 alerts therefore apply filters to narrow the results.
For description of each field within the Alert table refer to Alerts Table
2.4.5 - SamurAI Endpoint Agent
What is the SamurAI Endpoint Agent?
The SamurAI Endpoint Agent is a light weight, software component installed on an endpoint (such as a workstation or server) providing deep visibility and enabling SamurAI Managed Detection and Response across your endpoints. Capabilities include:
Telemetry Data Collection
- Standardized and targeted telemetry data collection independent of operating system (e.g the agent utilizes a custom Sysmon configuration, specifically tuned for the SamurAI Platform applied to Microsoft Windows to optimize event collection and analysis).
- Eliminates the need for 3rd party integrations to the SamurAI Platform (e.g winlogbeat agents installed on the Microsoft Windows OS).
- Eliminates the need for any endpoint configuration in telemetry collection.
Detection
- Leverages the SamurAI Real-Time Engine for detection of threats.
- We apply our global threat intelligence feeds to enrich data with context about known malicious actors, emerging threats, and attack patterns enhancing accuracy and speed of threat detection.
- Leverages the SamurAI Hunting Engine for automated and analyst driven threat hunting.
Investigate
- Provides a powerful query capability (osquery) with real-time visibility into endpoints (e.g query for installed browser extensions to help analysts detect potential persistance mechanisms used by threat actors and accelerate investigations).
- Event driven threat hunting to investigate, validate and contextualize a threat/incident.
Respond
- Provides incident response tooling and aids endpoint forensics.
What’s Next?
Review the SamurAI Endpoint Agent Support and Pre-requisites.
2.4.5.1 - Support and Pre-requisites
Listed below are supported Operating Systems (OS) and communication pre-requisites. If you do not see a specific OS version listed please reach out to us.
Supported Operating Systems
| Operating System | Supported Version |
|---|---|
| Microsoft Windows |
|
Communication Pre-Requisites
Ensure endpoints with the SamurAI Endpoint Agent installed have the following network connectivity:
| Source | Destination | Ports | Description |
|---|---|---|---|
| SamurAI Endpoint Agent | spiral-node-api.td.nttsecurity.io | TCP/443 |
|
What’s Next?
Now you have an understanding of support and pre-requisites, learn about Download and Installation.
2.4.5.2 - Download and Installation
Before you begin download and installation of the SamurAI Endpoint Agent you must first select how you wish to manage SamurAI Endpoint Agent Updates and decide settings for the SamurAI Endpoint Agent for Windows.
- From the SamurAI Portal select Telemetry and click SamurAI Endpoint Agent
Upon first navigation to this page, the following will be displayed:

Figure 1: SamurAI Endpoint Agent settings
Updates
Select how you want to manage SamurAI Endpoint Agent updates:
- Auto Managed : Auto updates of agents is enabled by default, this option will automatically update agents as new versions are released without any action needed on your part.
- Self Managed : Select this option should you wish to manage updates yourself. See Self Managed for more information.
SamurAI Endpoint Agent for Windows
- Determine whether to Accept Microsoft Sysinternals Software Licence Terms (Sysmon EULA).
If you accept the Sysmon EULA, you can select to Install Sysmon if missing
Click Apply SamurAI Endpoint Agent Settings
The SamurAI Endpoint Agent and Sysmon
For enhanced telemetry on Windows, the SamurAI Endpoint Agent optionally leverages Microsoft System Monitor (Sysmon), a vital component for collecting detailed process and system activity. Read more about Sysmon from Microsoft Documentation.
Sysmon is not bundled with the SamurAI Endpoint Agent therefore if you Accept Microsoft Sysinternals Software Licence Terms (Sysmon EULA) upon installation of the SamurAI Endpoint Agent, sysmon will be downloaded and installed or updated silently using standard Microsoft provided installation flags.
The SamurAI Endpoint Agent leverages a custom Sysmon configuration tuned and maintained by the SamurAI detection engineering team. This provides:
Noise reduction: a default Sysmon deployment generates an extremely high volume of data, our tuned configuration filters out unnecessary events which are irrelevant for SamurAI Managed Detection and Response.
High Fidelity detections: we selectively enable and enrich valuable event IDs (e.g process creation, network connections, registry modification etc) aligned with the MITRE ATT&CK framework.
Consistency across environments: ensures standardized event coverage across deployments.
Ongoing Tuning: we regularly update the configuration to reflect emerging attacker techniques, new ATT&CK mappings and lessons learned.
What’s Next
You can now proceed to Agent Download
2.4.5.2.1 - Download
To download the SamurAI Endpoint Agent follow the steps below:
Login go the SamurAI Portal
Click Telemetry and select SamurAI Endpoint Agent from the main menu
Click Installers
Select the relevant installer based on your operating system and click Download
Verify Download
Microsoft Windows
To ensure your download has not been corrupted or tampered with, you can validate it’s checksum using the built-in Windows tool ‘certutil’.
Run the following command and view the checksum to ensure it matches the installer within the SamurAI Portal:
c:\certutil -hashfile spiral-windows-amd64.msi sha256
example:
c:\certutil -hashfile spiral-windows-amd64.msi sha256
SHA256 hash of spiral-windows-amd64.msi:
85193aa8c4e7a1eaba1da36251bc6ea78e0e62b2
CertUtil: -hashfile command completed successfully.
What’s Next?
Based on your Operating System jump to the relevant SamurAI Endpoint Agent installation guide:
2.4.5.2.2 - Microsoft Windows
Manual Installation
Locate the Windows MSI installer file that you previously downloaded and double-click, a small progress window will appear which does not require any interaction.
Additional commands are available using the command line as outlined below. All commands can be used in combination as required.
Proxy Support
If your organization leverages a proxy then use the following command during install:
Example:
msiexec.exe /i "spiral-windows-amd64.msi" PROXY=http://<ip>:<port>
This will create a key in the Windows registry: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\NTT\Spiral with a parameter Proxy with the proxy from the command line.
This can be added/changed/removed at a later time, if so the SamurAI Endpoint Agent services must be restarted.
Quiet Mode Installation
Use the the following command for quiet mode installation (i.e no progress window is displayed):
msiexec.exe /i "spiral-windows-amd64.msi" /qn
Verbose Installation Logs
If you wish to view installation logs you can use the following command to save logs to a file for review:
Example:
msiexec.exe /i "spiral-windows-amd64.msi" /L*vx output.txt
Validate installation
After the installation has completed, there will be a Spiral entry under installed programs.

Figure 1: Windows apps & features
The installation folder is C:\Program Files\Spiral with full control permissions to SYSTEM and Administrators.
This should apply to all subfolders and files with one exception osquery.db which will have an additional read access to Everyone/World.

Figure 2: SamurAI Endpoint Agent Windows install path and files
There will also be a service named Spiral running.

Figure 3: Task manager service
The Spiral process will also be visible.

Figure 4: Task manager process
Additionally osquery processes will be running.

Figure 5: osquery processes
The following files are created by the installer:
C:\Program Files\Spiral\bin\spiral.exe: The Spiral launcher (more details what it does and functions further down)
C:\Program Files\Spiral\bin\osqueryd.exe: The Osqueryd binary that will be launched by spiral.exe (more details further down)
C:\Program Files\Spiral\config.yaml: The configuration for Spiral launcher
C:\Program Files\Spiral\secret: The embedded tenant/enrollment secret
C:\Program Files\Spiral\ca.pem: Spiral CA bundle used to communicate with the SamurAI platform. Will download new if missing or if outdated. Used by both spiral.exe and osqueryd.exe.
The following files are created by either the Spiral or Osquery process:
C:\Program Files\Spiral\server.crt: Exported server certificate chain from Spiral Node API (typically excluding Root CA).
C:\Program Files\Spiral\sysmon.xml: The sysmon configuration downloaded from Spiral Node API.
C:\Program Files\Spiral\data\osquery.db: RocksDB data folder used by Osquery for state keeping. Osquery sets this with read access to Everyone/World at intervals.
C:\Program Files\Spiral\data\extensions.load: Purposely left empty
C:\Program Files\Spiral\data\osquery.flags: Osquery startup flags (generated by Spiral), extended configuration is fetched by Osquery over HTTPS.
C:\Program Files\Spiral\data\osquery.log: Stdout/stderr log output from osqueryd.exe
C:\Program Files\Spiral\data\osquery.pid: Osquery PID
C:\Program Files\Spiral\data\osquery.uuid: UUID for this specific node
C:\Program Files\Spiral\data\spiral.log: Stdout/stderr log output from spiral.exe
C:\Program Files\Spiral\data\shell: A folder created if running spiral.exe with "shell" command which is an interactive mode to run Osquery commands.
Dependant on your selection for SamurAI Endpoint Agent for Windows the agent may:
- Download Sysmon from Microsoft official servers.
- Install or update Sysmon silently using standard Microsoft provided installation flags.
- Modify Sysmon with the configuration.
Review Deployed SamurAI Endpoint Agents
Review and Manage within the SamurAI Portal.
2.4.5.3 - Management
View Nodes
To view all deployed agents:
Login go the SamurAI Portal
Click Telemetry and select SamurAI Endpoint Agent from the main menu.
Dashboard
The dashboard panel displays summary information:
- Nodes: the total deployed and seen by the SamurAI platform
- Online: the total currently online (have communicated with the SamurAI platform within five minutes)
- Offline: the total number offline (have not communicated with the SamurAI platform for five minutes)
- Platforms: the total number of platforms i.e Windows / MacOS / Linux
Nodes Table
A table displays all deployed agents with node specific information:
| Field | Description |
|---|---|
| ID | Universally Unique Identifier (UUID) of the node |
| Status Description | Status of the agent. Potential status displayed: Online or Offline |
| Name | Hostname of the endpoint |
| Platform | Platform and architecture - icon depicting OS and processor e.g AMD64 |
| OS Name | The underlying operating system |
| OS Version | The operating system version |
| Agent Version | The SamurAI Endpoint Agent version installed |
| Sysmon Version | The System Monitor (sysmon) version installed |
| Last external IP | The external IP address of the agent as seen by the SamurAI platform |
| Last Seen | Date and timestamp of when the agent last checked-in to the SamurAI platform |
| Inactivity Threshold | An indicator displaying time until the agent will be deemed inactive and purged from view |
Inactive Node(s)
Nodes communicate with the SamurAI platform every minute and are marked offline if no communication is received after five minutes.
Offline nodes will be visible for 90 days, after this threshold it is deemed to be inactive and purged from the SamurAI platform backend and the current view.
You can view inactive and deleted nodes within the Node History.
Delete Node(s)
You can delete nodes from the table:
- Select the nodes you wish to Delete
- Click Actions and select Delete selected nodes
- To ensure you intended to delete the agents you will need to type DELETE in the field and select Delete
- The deleted node record will appear under Node History.
Node History
The Node History log displays a table of Deleted Nodes and Purged (deemed inactive) with node specific information:
| Field | Description |
|---|---|
| ID | Universally Unique Identifier (UUID) of the node |
| Action | The action taken against the node. This could include Purged based on the inactivity threshold or Deleted |
| Name | Hostname of the endpoint |
| Last Status | The Last known Status of the node (typically offline) |
| OS Name | The underlying operating system |
| User | The user that deleted the node. This could also include System which denotes the SamurAI platform when the node is inactive and purged |
| Last Enrolled | Date and timestamp of when the node was originally enrolled |
| Action Applied | Displays when the Action was applied to the node |
2.4.5.3.1 - Settings and Updates
Settings
You can change the Update and Sysmon EULA selections by clicking Settings from the SamurAI Endpoint Agent view.
- Auto Managed : Auto updates of agents is enabled by default, select this option if you want the agent updates to occur automatically without any action needed on your part.
- Self Managed : Select this option should you wish to manage agent updates yourself.
Updates
Self Managed
If Self Managed is selected a new option entitled Update Tasks is displayed.
Update Tasks
Selecting Update Tasks allows you to configure tasks for updating your deployed agents.
- Click on Create Update Task
Enter a Name for the task e.g Windows 10 Pro Update
Toggle whether you wish to Start immediately. If you do not start the task immediately you have the option to update the status at a later date/time. See Update the Task.
Select whether you wish to update:
- SamurAI Agent version (the latest version will always be displayed)
- Sysmon version
Rate Limit is enabled by default to 5 nodes per 1 minute. Read more about Rate Limiting
Once complete, select Review Selection and review your tasks
Click on Create Update Task
Rate Limiting
Rate limiting allows you to roll out updates to nodes gradually instead of updating all at once. This controlled approach reduces risk of disruption, avoids overloading networks and ensures that if an unexpected issue occurs, only a small number of nodes are affected.
Rate limiting allows you to configure the number of nodes to update per time duration (which can be set per minute/hour/day).
When rate limiting is recommended:
- Large fleets (typically 500+ nodes)
- Networks with remote sites, VPN’s or limited bandwidth
- Critical workloads where uptime and stability are essential
- Major agent version upgrades or significant configuration changes
When rate limiting may not be necessary:
- Small fleets with a few hundred nodes
- Minor, low-risk updates
Rate limit upper limits are set as:
- 25 nodes per 1 minute, 50 nodes per 2 minutes etc
- 1500 nodes per 1 hours, 3000 nodes per 2 hours etc
- 36000 nodes per 1 day, 72000 nodes per 2 days etc
View Update Tasks
- From the SSamurAI Endpoint Agent view, click Update Tasks.
A table displays all Update Tasks with specific information:
| Field | Description |
|---|---|
| Status | Status of the Update Task (hover over for text, potential status displayed Paused/Running/Completed/Failed |
| Status Description | Status Description (potential status displayed Paused/Running/Completed/Failed |
| Name | Name provided for the task |
| Sysmon Version | Updated Sysmon version (if applicable) |
| Agent Version | Updated SamurAI Endpoint Agent version |
| Target Node Count | The number of nodes within the update task |
| Completed Node Count | The number of completed node updates |
| Failed Node Count | The number of failed node updates |
| Created | Date/Timestamp of update task creation |
| Updated | Date/Timestamp of updates to the update task |
Select an Update Task from the list to display status of individual node updates.
A summary will be displayed including:
- Update task status
- Number completed
- Number failed
- Target
- Rate Limit
Additional details for each node are also included:
| Field | Description |
|---|---|
| Name | Hostname of the node to be updated |
| Node Update Task Status | The status of the node update, potential status are New/Pending/Completed/Failed |
| Message | A short description of progress |
| Start Date | Date/Timestamp of agent update |
| End Date | Date/Timestamp of agent update end |
| Agent before | SamurAI Endpoint Agent version before the update |
| Agent after | SamurAI Endpoint Agent version after the update |
| Sysmon before | Sysmon version before update |
| Sysmon after | Sysmon version after update |
Update the Task
You can update the State of an Update Task to either Paused or Running.
For example, if you previously set an Update Task NOT to Start Immediately you can set the state to Running to begin the update:
From the Update Tasks list select the relevant Update Task
Select More Options (
).
Click Update the Task
Select the State to Paused to pause the update task or to Running to begin or resume the update task.
2.4.5.4 - Uninstall
Follow the steps to uninstall the SamurAI Endpoint Agent based on your Operating System:
Microsoft Windows
Go to Add or remove programs
Find Spiral Agent
Click Uninstall
When uninstalled, program files and registry entries are removed from the endpoint/node, however some files may remain:
- All files not added by the installer itself such as the Data folder in C:\Program Files\Spiral\Data
- Files server.crt and sysmon.xml in C:\Program Files\Spiral remain after uninstall.
It is safe to delete C:\Program Files\Spiral after the uninstall has completed.
2.4.5.5 - FAQ
General
Is the SamurAI Endpoint Agent available to all clients?
Is the SamurAI Endpoint Agent an Endpoint Detection & Response (EDR) product?
I already have an EDR (e.g Crowdstrike, Microsoft Defender), do I need the SamurAI Endpoint Agent?
Can I use the SamurAI Endpoint Agent in conjunction with my current EDR?
Are there any known limitations or problems with running the SamurAI Endpoint Agent in addition to my deployed agents?
What type of data does the SamurAI Endpoint Agent collect from the host?
What is the average log data volume per day for the SamurAI Endpoint Agent?
Support
What Operating Systems are supported?
Can the agent also be used and installed on server systems (e.g Windows Server 202x)
Can the SamurAI Endpoint Agent be installed on virtual systems? e.g within a virtualization platform where multiple virtual machines (VMs) share the same underlying hardware?)
Installation and Setup
What network connectivity is required?
What endpoints should I install the SamurAI Endpoint Agent on?
Are there any restrictions on installing on a user’s PC/endpoint?
Is it possible to install the SamurAI Endpoint Agent remotely?
Management
How often are SamurAI Endpoint Agents updates available?
How do I update deployed SamurAI Endpoint Agents?
Why is the term Node(s) used in the SamurAI Portal?
Why is the name Spiral used in folder paths and services names?
2.5 - Analysis
2.5.1 - Advanced Query
Advanced Query provides a powerful interface that enables you to query your event data ingested into the SamurAI platform. For instance, you can query for matching events which were logged or triggered in the past in order to fully understand the context.
After a threat has been responded to, Advanced Query can also play an important role in the forensic investigation of the threat, in order to determine both its extent and the sequence of events which occurred.
Advanced Query provides a very flexible interface which is based on Microsoft’s Kusto Query Language (KQL). This means that you can perform tasks ranging from simplistic queries all the way through to complex and powerful threat hunts in search of evasive threats.
The Advanced Query interface provides you with a graphical view showing the distribution of query matches over time. This allows you to easily spot deviations from the norm, and to identify the time when important events occurred.

Some examples of the functionality provided by Advanced Query include:
- Ability to use the KQL query language to cover simplistic searches across your data to running complex queries in support of Threat Hunting activities.
- Ability to query the SamurAI data lake for events over the entirety of your full retention period.
- Ability to provide a time-based visualization of the results matching your query enabling you to spot deviations from normal activity.
- Ability to easily filter in/filter out values.
- Ability to easily drill in and out using a graph of the overview, enabling you to quickly pivot across anything from small result sets, to ones containing millions of data points.
- Ability to query over a user-defined time period.
- Ability to easily search/filter the results and export the selected results.
Some example use cases, which can be covered by Advanced Query include:
- Verifying activity of an endpoint over a specified time period
- Tracking lateral movement of a threat actor
- Finding other endpoints which may have been affected by a breach
- Tracing the sequence of events in a breach
- Find all activity related to a specific attacker
- Confirming that new log sources are generating data and verify these are configured correctly.
The Advanced Query user interface is divided into a number of panes which provide:
- A time-picker allowing the user to easily select a time-period to apply a query.
- An interactive KQL query editor.
- A filters panel, reflecting all the Fields available in the current result. This allows you to quickly filter in/out, search across the filter values and visually see the split between various values. This also allows you to quickly narrow down a query.
- A Results panel, showing all matching Alert and Event data, both in parsed and raw format. This allows you to easily search and filter cross the viewed result and export results of relevance.
- A User Tips panel, showing some quick Tips to assist the user in getting started in writing their first KQL queries.
To learn all about the feature within the SamurAI Portal please review Advanced Query Functionality.
2.5.1.1 - Advanced Query Functionality
Advanced Query allows you to query all of your telemetry data ingested into the SamurAI platform using Microsoft’s Kusto Query Language (KQL). You can use KQL to perform simple exploration of your data through to sophisticated threat hunting in search of security anomalies and evasive cyber security threats.
In this article we provide an overview of each element of the interface within the SamurAI Portal and its’s usage to enable you to maximize your query results.
Navigate to the Advanced Query Interface
- Login to the SamurAI Portal
- Click Analysis and select Advanced Query located on the main menu

Figure 1: Advanced Query interface
Advanced Query Panels
Query Panel
The Query panel is where you write KQL queries. As you construct a query the interface auto-completes suggesting operators or schema.

Figure 2: Query panel auto-complete example
Result Limit
You can choose to display 2000 or 10000 results based on your query by leveraging the drop down.

Figure 3: Result Limit

Figure 4: Advanced query Tips
Once you have completed writing your query click Run Query

Figure 5: Run Query
Time Period
Any query you run is based on a time period. Select a relevant time period when constructing a query to display results based on this time period.
If you use a timestamp operator within a query, the Time Period will be overridden and be viewed as ’Set in Query’.

Figure 6: Time period
Query History
To view your historical queries click (![]() ). This displays the latest 50 queries executed by you with time of execution and an option to add the query to a library. To save the query to a library, click (
). This displays the latest 50 queries executed by you with time of execution and an option to add the query to a library. To save the query to a library, click (![]() ) .For more information on saving a query jump to Save New Query.
) .For more information on saving a query jump to Save New Query.

Figure 7: Query history
Query Library
A library is where queries are saved for future use. There are different types of query libraries:
- Standard library - useful queries provided and populated by NTT.
- Organization library - queries saved within folders are available to any of your organization’s users with access to the SamurAI Portal.
- My library - queries saved within folders are only available to you.

Figure 8: Query library
Within ‘Organization library’ and ‘My library’ you can create folders to categorize and save your queries.
Save New Query
Click Add to save a query and select the Folder to save it in (you can also create a new folder here). You can optionally add a Description and MITRE ATT&CK category from the prepopulated list. Once complete click Save.

Figure 9: New query
Edit/Duplicate/Delete Queries
Click more options () if you need to edit or duplicate existing queries to refine them or alternatively delete.

Figure 10: Edit, duplicate and delete options
Fields Panel
The Fields panel displays all fields available based on the query. By default we query the events table which displays all fields available from your telemetry, this is divided into Favorite Fields and Other Fields.
Each Field displays a count which represents the hits within the entirety of the query result.

Figure 11: Fields and count
By selecting a Field you can expand on the values within that field. For example, the graphic below highlights the ‘dest_ip’ field which displays all values with a Count and percentage of total

Figure 12: Field selection showing values
SamurAI has default Favorite Fields, however you can update your Favorite Fields by selecting the Field and either select or deselect as a favorite by clicking  .
.
To simplify query building you have the ability to select one or more values when you expand the field using the “+ - " symbols, this appends the value to include (==) or exclude (!=) from the query.

Figure 13: Add value to query
Results Overview Panel
Query results are presented in a graphical overview, this may allow you to visually identify patterns or deviations in the results. The graph takes into consideration selected time-period, number of results matching the query and is presented with date/timestamp and total for each bar in the graph. Hovering over any bar in the graph will display the date/timestamp and total results.

Figure 14: Graphical result overview
The graph is also interactive, by clicking on any bar in the graph or by left click selection and highlighting multiple bars, the Fields and Results Panel are adjusted to display data in the selected time-period. You can also zoom in to specific results by selecting Zoom to Selection (![]() )
)

Figure 15: Result selection
Additionally you can Zoom out (![]() ) from any result set to view a larger time-period in relation to the active result. The Zoom out increment is based on the time period between the first result and last result and added to the ‘from’ and ’to’ time.
) from any result set to view a larger time-period in relation to the active result. The Zoom out increment is based on the time period between the first result and last result and added to the ‘from’ and ’to’ time.
For example: First result at 13:00 and Last result at 14:00, is a 1 hour time difference. If you Zoom out this adjusts the time period 1 hour, therefore , 13:00, updates to 12:00 and 14:00 adjusts to15:00. Increasing the viewed time-period from 1 hour, to 3 hours.
By default a column chart type is displayed, however you also have the options to select from multiple chart types options, based on the chart type.

Figure 16: Chart types
Results Panel
The results panel displays an Events view (with timestamp and raw data) or Table view (with all events displayed in rows and each field in columns). The results panel will display up to 2000 or 10000 results dependant on your selection under Result Limit.

Figure 17: Results panel
Results Panel Options
By selecting more options () displayed on the top right of the the result panel you can:
- Show favorite fields
- Show empty fields
- Autosize visible columns
- Clear all filters
- Clear all sorting
- Export to CSV - export the results displayed to CSV. This functionality takes into consideration result selections and active filters making it very easy to export specific results.

Figure 18: Results panel options
Expand the Result
You can view all event data in a vertical view by selecting expand () in both Event and Table views.
Filter the Result
You can create filters against any of the results by selecting ( ) and choosing a filter option and parameter.
) and choosing a filter option and parameter.

Figure 19: Filter options
You can also easily filter results from the Filter located at the top right of the Results Panel.
Filter / Copy based on value
By selecting more options () on any given field result you can copy to clipboard (
 ) or Add or Exclude filter to your query.
) or Add or Exclude filter to your query.

Figure 20: More options
What’s Next?
If you are new to KQL please refer to Constructing an Advanced Query or for comprehensive documentation refer to Microsoft KQL documentation.
2.5.1.2 - Constructing an Advanced Query
The Advanced Query feature within the SamurAI Portal uses Microsoft’s Kusto Query Language (KQL). In this article we discuss the basics of KQL, the logic of a query and provide some examples to get you started.
What is KQL?
In short, KQL is as it states, a Query Language.
The “K” in KQL (Kusto) is named after Jacques Cousteau, the infamous ocean explorer! Just like Jacques’s exploration into the depths of the oceans, finding previously unknown volcanic basins, KQL provides you the ability to explore the expanse of your telemetry data.
Why and when use KQL?
Of course, you are not going to find any volcanic basins or new species of dolphin in your data, however in the cybersecurity context it will allow you to find actionable information. Use of KQL will allow you to investigate your data to answer simple questions such as ‘is my log source generating data’ through to tracing the sequence of events in a breach. You may be familiar with the term Threat Hunting, effectively searching for malicious, suspicious or nefarious activity - whether that be proactive via determining a hypothesis through to hunts based on Indicators of Compromise (IOCs) and Indicators of Attack (IOAs). In essence, using KQL helps you answer the following questions:
- Does X exist
- Where does X exist?
- Why does X exist?
- How to respond?
KQL Logic
A typical query is structured to search, locate information and produce results.
The structure may include:
- What? table to query
- Pipe (|) for command separation
- Filter
- Order data
- Modify Columns in results
Lets walk through some simple examples to understand the logic.
Find events between two hosts
events | where src_ip == "10.170.236.50" and dest_ip == "10.179.236.106"
- The first step in this query outlines what to query, in this example it is the “events” table. By default SamurAI always queries the “events” table.
- The pipe ( | ) command is always used for command separation.
- We then use a ‘where’ operator to filter within the query for the source ip address (src_ip) of “10.170.236.50” and a destination IP address (dst_ip) of “10.179.236.106”
When looking at the results of a query, you will be presented with associated Fields based on the query which allows you to narrow down your search. KQL query statements work like a funnel, starting with a large data set and passing it through multiple operators until it is filtered, summarized or rearranged as required.
By selecting a Favorite Field or Other Field you can start to narrow down your results to your requirements. Alternatively you may choose to include the fields within the query itself or use the Project operator to include specific column fields within your result.
Refer to Advanced Query Functionality to understand more on Favorite Fields and Other Fields.
Search for events with source IP 10.170.236.50 and display a table with a few selected columns
events | where src_ip == "10.170.236.50" | order by timestamp|project timestamp, action, src_ip, src_port, dest_ip, dest_port
- Query the ’events’ table
- Filter events using the where operator for source IP address “10.170.236.50”
- Use the order operator to order results by timestamp
- Use the project operator to include the column fields “timestamp, action, src_ip, src_port, dest_ip, dest_port”
The simple examples above make use of common operators, use the KQL quick reference guide for more info on operators which includes a comprehensive list with definitions.
Complex Examples
Lets now walk through some more complex examples.
Frequency of Events
A common requirement is to find the frequency of occurrence of an event. For instance, in this example we are reviewing Amazon VPC Flow logs and finding which destination IP addresses are receiving the most connections to port numbers below 1024.
events| where product == "Secure Firewall (FTD)" and toint(dest_port) <1024| summarize connections = count() by dest_ip |order by connections
What is also worth noting in this example is that we first need to convert the destination port number to an integer type (as it is a text field) before checking if it is a low-numbered port (less than 1024). For more information on the data types used in the data lake, you can refer to the article on event field data types.
This query produces output which looks something like this:

The result helps us to see which IP addresses are accepting the most connections to privileged ports.
Querying raw logs
Advanced Query isn’t only able to query logs from sources which originate from supported integrations. The fact that logs from any kind of syslog source can be ingested into the SamurAI platform makes it possible to query the raw content of these logs using Advanced Query.
In the example below, we are taking authentication logs from a host, and querying for failed authentication attempts. We are able to use the extend operator and extract function to create our own fields from the log lines, parsing them using regular expressions.
events| where host == "10.1.1.1" and (raw contains "Invalid" or raw contains "fail") and raw !contains "connect"| extend message = substring(raw,16)| extend src_host = extract("([A-Za-z0-9\\-]+).+",1, message)|extend msg_info = extract("\\[[0-9]+\\]\\:(.+)",1, message)| extend app_src = extract("[A-Za-z0-9\\-]+([a-zA-Z0-9\\-]+).+",1, message)| extend user = extract("([A-Za-z0-9\\-]+) from",1, msg_info)| extend src_ip = extract("from([0-9a-f\\.\\:]+)",1, msg_info)| project timestamp, host, src_host, app_src, user, src_ip, msg_info| summarize attempts = count()by src_ip| order by attempts
Once we have extracted the fields we want, we can then go on to perform more operations. In this case we are summarizing the logs by counting the failed authentication attempts by source IP address, and ordering the list so that the IP address with the most failed attempts is listed first. In this case, this helps us to find potential brute force attackers who are trying to guess passwords through brute force tactics.
Tips!
Be Specific when constructing queries!
Used correctly, Advanced Query can perform sophisticated queries matching against a data set measured in terabytes within seconds! However poorly constructed queries can cause problems, cause dreaded browser slowdowns, or even trigger a query time-out when exceeding the maximum allowed query wait time. The more specific you are with your query, the quicker you are able to will get to the Result.
Lets look at an example:
- Try not run a query with no criteria (for example simply ‘events’) against a long timer period. Whilst this might be tempting to view all events, this will match ALL events in your SamurAI tenant, delivering a sub optimal experience - results for such a query could potentially be measured in Gigabytes or at times Terabytes!
Instead, try to be as specific as possible:
- If you are querying activity for a specific source host, add a where statement specifically asking for results from a specific source:
events where src == "172.21.33.99"
Example:
- matching results: 9 100 000 events
- Approx time to completion: Partial results in 45 seconds.
If you are researching activity related to a specific source type, extend the query to specifically ask for results matching a type:
events where src == "172.21.33.99" and type == "WEBPROXY"
Example:
- matching results: 3 700 000 events
- Approx time to completion: Full Results in 40 seconds.
If you are looking for specific fields, extend the query to specifically project specific fields:
events | where src == "172.21.33.99" and type == "WEBPROXY" | project timestamp, src, url
- Example:
- matching results: 3 700 000 events
- Approx time to completion: Full Results in 7 seconds
What Now?
As you may have realized from reading this article, Advanced Query is a powerful tool - only limited by your own understanding of KQL and in determining what questions or hypothesis against your data you may have. We recommend you start by writing a few simple queries and review the Microsoft documentation. If you need a reminder of usage in the SamurAI Portal, be sure to review Advanced Query Functionality.
2.5.1.3 - Event field data types
When using Advanced Query to analyze Events stored in the data lake, it is sometimes necessary to be aware of the data types of the fields of the records being processed.
For instance if you want to perform a numeric comparison on the value of a field, you need to ensure that it has a numerical data type (such as an integer) or otherwise type-cast it first. For instance, in the following example, we are testing for privileged port numbers (below 1024), but the dest_port field is a string:
events| where product == "VPC Flow Logs" and toint(dest_port) < 1024
Here we are using the toint() statement to convert the dest_port field to an integer before making a numerical comparison.
This raises the question of how to determine the data types of fields. You can use the getschema statement to display the data types of fields. The following query will display the types of the fields of the entire schema:
events | getschema
This example produces output something like this:

To find the type of a specific field, you can use the search bar above the output:

This example selects all the fields whose names contain the substring “port”.
If you know the name of the field whose type you want to query, you can use the project statement to filter out only that field:

2.5.2 - Alerts
What is an alert?
An alert is a security detection made by the SamurAI platform or third party vendor where SamurAI is ingesting telemetry.
How are alerts triggered?
Alerts are triggered by detection engines based on single or multiple events. The SamurAI Portal displays alerts categorized according to the underlying detection engine. These categories include:
SamurAI platform
- Real-time engine - Proprietary NTT developed detection engine that leverages behaviour modeling, machine learning, and the latest threat research to automatically identify suspected threats during real-time analysis of ingested telemetry into the SamurAI platform.
- Hunting engine - Intelligence-driven detection engine based on the Sigma project but customized by NTT with additional detection capabilities. The SamurAI hunting engine performs automated threat hunting to idenfiy and alert on possible adversary activity.
Vendor
- Alerts generated by and collected from third-party vendor technologies which are integrated with the SamurAI platform (e.g Endpoint Detection & Response (EDR) and Firewall technologies)
What alerts are displayed within the SamurAI Portal?
We display the same alerts as our SamurAI Security Operation Centre (SOC) analysts view.
Do I need to review and act on alerts?
No. The SamurAI SOC analysts triage, investigate and validate alerts as part of your Managed Detection & Response (MDR) service. As alerts are validated by the SamurAI SOC analysts and investigated, they may potentially lead to a reported Security Incident and are marked accordingly. Our strategy includes visibility and transparency of the service we provide to you therefore this feature provides you that visibility showcasing the value of the service. Refer to the Alert Dashboard which provides some key alert metrics over a given time period.
Next Steps
To further understand Alerts within the SamurAI Portal we recommend you review the Alerts View article.
2.5.2.1 - Alerts View
In this article, all elements of the Alert View are outlined to help you understand the alerts displayed.
Navigate to Alert View
- Login to the SamurAI Portal
- Click Analysis and select Alerts on the main menu

Figure 1: Alert view example
Alerts Summary
Alerts are summarized in a panel which can be updated based on a specified time period and includes:
- Security Incidents - the total number of security incidents reported to you that may correspond to one or more alerts.
- Alerts - the total number of alerts detected by the SamurAI platform and third party vendor integrated with the SamurAI platform.
- Real-time engine - the total number of alerts detected by the SamurAI real-time engine
- Hunting engine - the total number of alerts detected by the SamurAI hunting engine
- Vendor - the total number of alerts collected from third-party vendor products integrated with the SamurAI platform

Figure 2: Alerts summary example
Filters
Various filters are available to determine the alerts to be displayed.

Figure 3: Time and Display filter
The total number of alerts within the alerts table in displayed to the left of the Time Period filter.
Time period
You can update all panels to specific date and time ranges. We default to the Last 24 hours however have included Quick time ranges.

Figure 4: Date and time selection
Display Filter
Enter any values you wish to filter and highlight within the display filter.

Figure 5: Display filter
Alert Column Filter
Adjust and show/hide any of the column values within the Alert Table.

Figure 6: Alert column filter
Alerts Table
All alerts are listed within the alert table, important to note is that the table is limited to 10,000 alerts therefore apply filters to narrow the results.
What are the Alert table fields?
Review the table below outlining each field displayed:
| Alert field | Description |
|---|---|
| Timestamp | Local date and time of when the alert was generated displayed in the format [yyyy:mm:dd] [hh:mm:ss], hover over will display Universal Time Coordinated (UTC) and local timezone offset |
| Incident | If the alert is associated with a reported security incident (one or more alerts may be associated with a single security incident) a link to the security incident is displayed |
| Action | Action relates to the parsed action in the underlying event(s) |
| Signature | Signature name from the detecting engine - this could be from an integrated telemetry source (vendor) or from a SamurAI platform detection engine |
| Source | Initiating source, this could be represented as hostname(s), IP address, user or URL |
| Source Port | The initiating source port |
| Destination | The destination, this could be represented as hostname(s), IP address, user or URL |
| Destination Port | Destination port number |
| Protocol | Network protocol e.g TCP / UDP |
| User | User from the underlying event(s) |
| MITRE | The MITRE ATT&CK tactic mapping - this could include one or more tactics. For further information refer to ATT&CK Matrix for Enterprise |
| Detection | The detection engine triggering the alert. Refer to How are alerts triggered? |
| ID | Alert ID (not displayed by default) |
2.6 - Reports
Reporting provides you valuable insight into your service and includes metrics which help you understand your organizations security posture and the value of SamurAI MDR.
A standard template entitled Executive Overview is currently available which has been designed to address common needs and highlights different facets of the service.
Create a Report
To create a PDF report from the standard template:
- Login to the SamurAI Portal
- Select Reports from the main menu
- Select Create Report
- Enter a Title for the report (if a title is not provided it will default to the template name)
- Select the Language for the report
- Select a Report start date (this will be from 00:00:00 UTC of start date)
- Select a Report end date (if the current date is selected, the current time will be used. If the current date is not selected the end of day 23:59:59 is used)
- Select Create Report
Report Status
As a report is generated, the status flag can get the following states:
| Status | Description |
|---|---|
| Queued | Queued and generation of the report will begin |
| Running | Report generation is running |
| Failed | Report generation has failed |
| Completed | Report is complete and available for download |
Viewing a Report
You can view a report once generation has completed by downloading in PDF format, simply click on download ( ).
).
The report will be saved in the following format: ‘Title’_‘start-date’_-_’end-date’.pdf.
Reporting Functionality
Column Filtering (
 )
)- Select Columns to toggle on or off any of the column fields to optimize your view of all report
Filtering (
 )
)- Filter your report list view by any of the fields
Export Report List (
 )
)- You can export your report list to a CSV file
Refresh (
 )
)- Refresh your page view
The Executive Overview Template
The executive overview template was designed to provide insight into the MDR service over a reporting time period you can specify. The report itself is intuitive and self explanatory however below is an outline and description of each report section:
Service Activity
This section of the report focuses on activity related to security incidents, general tickets submitted by your organization via the SamurAI Portal and integration data within the specified reporting period of the report. This includes:
The number of new and closed Security incidents reported to your organization over the reporting period selected.
The number of new and closed General tickets submitted by your organization over the reporting period selected.
New security incidents by severity
- If new security incidents were reported to you within your selected reporting period then a graph will be displayed depicting the number of open security incidents by severity.
- Review Security Incidents for additional information on security incident reporting and severities and MDR Incident Management for our incident management process.
Closed security incidents by severity
- If security incidents were closed during your selected reporting period then a graph will be displayed depicting the number of closed security incidents by severity.
New security incidents by MITRE ATT&CK category
- If new security incidents were reported to you within your selected reporting period then a table will be displayed outlining the number of security incidents reported ranked by MITRE ATT&CK category.
Security incidents
- A table providing additional information of each security incident within the reporting period ranked by creation date.
Security Monitoring Funnel
- The funnel graphic depicts the total number of events from your telemetry sources ingested into SamurAI, the alerts that were analyzed and validated security incidents reported to your organization. This funnel infers the value of the service based on the data analyzed focusing on detecting and reporting threats to your organization.
Data Usage
- This graphic is helpful for you to understand your subscription quota against actual usage.
Data ingested per product
- Graph depiction of data usage per integrated telemetry data source within the reporting period.
Data Ingested
- Further detail on data ingested per integrated telemetry data source within the reporting period.
Alerts Analyzed per vendor
- Graph depiction of alerts analyzed per vendor within the reporting period. The graph shows both vendor alerts and detection made by the SamurAI platform (shown as NTT).
Alerts Analyzed
- A table providing alert counts per vendor within the reporting period. The table shows both vendor alerts and detections made by the SamurAI platform based on the ingested data.
New general tickets by priority
- If your organization submitted any general tickets during your selected reporting period then a graph will be displayed depicting the number of general tickets by priority.
Closed general tickets by priority
- If your organization’s general tickets were closed during your selected reporting period then a graph will be displayed depicting the number of general tickets by priority
New general tickets by category
- If new general tickets were submitted by your organization within your selected reporting period then a table will be displayed outlining the number of general tickets ranked by category.
General Tickets
- A table providing additional information of each general ticket submitted by your organization within the reporting period ranked by creation date.
Current Status
This section of the report focuses on all reported security incidents and also general tickets submitted by your organization as of your reporting end date. This includes:
All open Security Incidents as of reporting end date
All open general tickets submitted by your organization as of the reporting end date
Open security incidents severity
- A graph depicting all open security incidents reported to you by severity as of the reporting end date.
Open security incidents by status
- A graph depicting all open security incidents reported to you by status as of the reporting end date.
Open security incidents by age
- A graph depicting all open security incidents reported to you by ages in days as of the reporting end date.
Open security incidents
- A table providing additional information of all security incidents reported to you as of the reporting end date ranked by age in days.
Open general tickets by priority
- A graph depicting all open general tickets submitted by your organization ranked by priority as of the reporting end date.
Open general tickets by status
- A graph depicting all open general tickets submitted by your organization ranked by status as of the reporting end date.
Open general tickets by age
- A graph depicting all open general tickets submitted by your organization ranked by age days as of the reporting end date.
Open general tickets
- A table providing additional information of all general tickets submitted by your organization as of the reporting end date ranked by age in days.
Trending
This section of the report focuses on historical trends related to open and closed security incidents and general tickets submitted by your organization over the last 13 months from the end date of the reporting period. The start date is when data became available over the 13 month period.
Opened and closed security incidents
- A graph highlighting opened and closed security incidents by month illustrating historical trends over the last 13 months from the reporting end date.
Opened and closed security incidents cumulative
- A cumulative graph highlighting opened and closed security incidents by month illustrating historical trends over the last 13 months from the reporting end date.
Average time to close security incidents
- A graph highlighting the average number of days to close a security incident over the last 13 months from the reporting end date.
Opened and closed general tickets
- A graph highlighting opened and closed general tickets submitted by your organization by month illustrating historical trends over the last 13 months from the reporting end date.
Opened and closed general tickets cumulative
- A cumulative graph highlighting opened and closed general tickets submitted by your organization by month illustrating historical trends over the last 13 months from the reporting end date.
Average time to close general tickets
- A graph highlighting the average number of days to close a ticket submitted by your organization over the last 13 months from the reporting end date.
Data usage
- A graph highlighting data usage over the last 13 months from the reporting end date.
2.7 - Admin
2.7.1 - User Management
To view all users of your SamurAI tenant select Admin > User Management from the main menu.
User Management displays information for each user including when they were created, account status and last login.
You also have the ability to export you user list to a CSV file by selecting Export.
Invite Users
To add new users you can send an invite from the SamurAI Portal, this will send an email allowing the user to register their account.
- Login to the SamurAI Portal and select Admin - User Management
- Select Invite Users and add the email address of the user. You can add multiple email addresses as needed.
- An email will be sent from no-reply@security.ntt to each user requesting them to Register Account and complete Account Details.
- Further registration information can be found in Getting Started with SamurAI MDR
User Status
The table below outlines the potential user status:
| User Status | Description |
|---|---|
| Invited | user has been invited to register account |
| Active | user has registered and is active |
2.7.2 - User Settings
Select your user account at the top right of the SamurAI Portal to access your settings.
Figure 1: User Settings
Notification Settings
You can manage which email notifications you receive from the SamurAI Platform by adjusting your personal notification settings. These settings apply only to your account and do not affect other users.
To ensure your notification preferences work correctly, notifications must remain enabled for each individual Collector, Integration, and Network Traffic Analyzer. For details, see the relevant sections:
Notification Behavior by Catgeory
- Collectors, Integrations and Network Traffic Analyzers: Notifications are triggered by status changes (e.g OK, Warning, Critical, Pending, Unknown)
- Security Incidents and General Tickets: Notifications are triggered by actions (e.g created, updated, closed, comment added)
Default Notification Settings
| Notification Category | Default Setting |
|---|---|
| Collector | Critical Status |
| Integration | Critical Status |
| Network Traffic Analyzer | Critical Status |
| Security Incidents | Created, updated, closed, comment added |
| General Tickets | Created, updated, closed, comment added |
How to Update Your Email Notification Settings
- Open the SamurAI Portal and select your user profile in the top right corner
- Click Notification Settings
- Choose a notification category and use the dropdown menu to select the state or action for which you want to receive email notifications.
Appearance
Choose between a light or dark appearance for the application by toggling between the two modes.
Language
Toggle between the supported languages - English, Swedish or Japanese.
Time Zone
By default, the portal uses your browser’s time zone (detected from your device’s operating system) for timestamps displayed. You can override this by selecting a different time zone in your profile settings.
Tenant
Tenants that you belong to are listed. If you have multiple tenants simply select the tenant you wish to view.
News Feed
The news feed is populated by the SamurAI Security Operation Center (SOC) analysts and may include:
- any issues or maintenance affecting service
- news such as how we are handling new and emerging threats
- links to blog posts on interesting security research
- updates on new releases
The news feed is viewed by clicking on the news icon ( ), with the latest title and an indication of any unread news displayed. The latest 15 news items are displayed and more can be fetched by clicking on more at the bottom of the list.
), with the latest title and an indication of any unread news displayed. The latest 15 news items are displayed and more can be fetched by clicking on more at the bottom of the list.
Important news items will be highlighted and include a warning icon beside the title in the feed.
2.8 - Product Integration Guides
2.8.1 - Amazon CloudTrail
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Amazon Web Services (AWS) to send CloudTrail logs to S3 storage for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that an AWS cloud collector has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed cloud collector, the information can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information:
- Account number
- Bucket name
- Region
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling CloudTrail Logs
Follow the AWS documentation guide:
When following the vendor documentation, please perform the following adjustments:
- Enable for all accounts in my organization: Recommended to enable.
- Storage Location: Use existing S3 Bucket.
- Trail log bucket name: Select the S3 bucket which you setup during creation of the cloud collector.
- Prefix: Leave empty
- Log file SSE-KMS encryption: If enabled, extend the KMS Policy with:
{
"Sid": "Allow NTTHS Samurai account to use this KMS key",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::600502389717:root"
},
"Action": [
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}
- Event Type: At minimum Management events
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.2 - Amazon Elastic Load Balancer (ELB)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Amazon Web Services (AWS) to send Elastic Load Balancer (ELB) logs to S3 storage for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that an AWS cloud collector has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed cloud collector, the information can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information:
- Account number
- Bucket name
- Region
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Elastic Load Balancer Logging
Follow the official AWS documentation guide:
Attach a policy to your S3 bucket:
- Navigate to Step 2: Attach a policy to your S3 bucket.
- At this stage, you should have already created an S3 bucket or selected an existing one.
- Ensure that the policy you attach grants the necessary permissions for ELB to write logs to the bucket.
Configure access logs:
- Proceed to Step 3: Configure access logs.
- Specify the correct S3 bucket name and prefix.
- Make sure to use the appropriate S3 URI corresponding to the bucket created or selected previously.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.3 - Amazon Virtual Private Cloud Flow Logs
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Amazon Web Services (AWS) to send Virtual Private Cloud (VPC) flow logs to S3 storage for ingestion to Samurai via a cloud collector
Prerequisites
Ensure that an AWS cloud collector has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed cloud collector, the information can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Account number
- Bucket name
- Region
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Amazon Virtual Private Cloud Flow Logs
Follow the AWS documentation guide:
When following the vendor documentation, please perform the following adjustments:
- Filter: All
- Interval: 1 minute
- S3 Bucket ARN: Select the S3 bucket which you setup during creation of the cloud collector
- Log record format: Select AWS default format.
- Hive-compatible S3 prefixes: Unchecked
- Partition logs by time: Recommended to select Every 1 hour (60 mins)
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.4 - Amazon Web Application Firewall (WAF)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Amazon Web Services (AWS) to send Web Application Firewall (WAF) logs to S3 storage for ingestion to Samurai via a cloud collector.
Prerequisites
You will need to deploy an AWS cloud collector via the SamurAI Portal. Follow the steps outlined in:
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Amazon Web Application Firewall Logging
Follow the official AWS documentation guide:
Sending protection pack (web ACL) traffic logs to an Amazon Simple Storage Service bucket
When completing the steps ensure to select the S3 bucket created in the previous section with the bucket name prefix aws-waf-logs-
Ensure permissions required to publish logs to Amazon S3 is also completed as applicable
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.5 - Apache HTTP Server
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Apache HTTP Server hosted on a Linux host to send access and error logs to a Samurai Local Collector deployed on your network by configuring rsyslog.
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| Apache HTTP Server | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Configure Apache HTTP Server
Ensure that Apache HTTP Server is configured to log to syslog
Add or modify the ErrorLog and CustomLog directives in your Apache configuration file, normally located at /etc/apache2/apache2.conf:
ErrorLog "|/usr/bin/logger -p local6.error -t apache_error"CustomLog "|/usr/bin/logger -p local6.info -t apache_access" combined
Restart the Apache service to apply the configuration:
sudo systemctl restart apache2
Configure log forwarding with rsyslog
Follow the below steps to configure rsyslog to forward Error and Access events.
Rsyslog prerequisites
Ensure the following statement is included in the main rsyslog configuration file, normally located at /etc/rsyslog.conf:
$IncludeConfig /etc/rsyslog.d/*.conf
If no IncludeConfig statement exist for the /etc/rsyslog.d/ directory, append it to the end of rsyslog.conf.
Create /etc/rsyslog.d/ntt_apache.conf
Create /etc/rsyslog.d/ntt_apache.conf and insert the below configuration block, enter the Local Collector IP in the Target field.
template(name="apache-log" type="string" string="<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% apache_log %STRUCTURED-DATA% %msg%\n")if $programname == 'apache_error' then { action( queue.type="LinkedList" queue.size="10000" type="omfwd" template="apache-log" Target="<Local Collector IP>" Port="514" Protocol="tcp" )}if $programname == 'apache_access' then {action(queue.type="LinkedList" queue.size="10000" type="omfwd" template="apache-log" Target="<Local Collector IP>" Port="514" Protocol="tcp")}
Validate and restart service
Confirm that rsyslog can parse the configuration without any errors by running:
rsyslogd -N1
Then restart the rsyslog service:
sudo systemctl restart rsyslog
The log messages will now be forwarded to the Samurai Local Collector.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.6 - Aruba Networks ClearPass
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Aruba Networks ClearPass to send logs to a Samurai Local Collector deployed in your network.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Aruba Networks ClearPass | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Syslog Configuration
Follow the below steps in ClearPass Policy Manager to enable syslog output to the local collector.
Add a Syslog Target using the following parameters:
Parameter Value Host Address IP of the Samurai Local Collector Protocol TCP Server Port 514 Create Syslog Export Filters for each event type using the following parameters:
Parameter Value Export Template Audit Records, Insight Logs and Session Logs Export Event Format Type CEF Syslog Servers Syslog target created in the above step
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.7 - Azure Virtual Networks
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Virtual Network flow logs to a Storage account for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- On the left navigation pane, click Telemetry and select Collectors.
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling NSG flow logs
Follow the vendor documentation guide to enable VNet flow logs.
When following the vendor documentation, please perform the following adjustments:
- Ensure when configuring the Storage Account setting that it’s referencing the storage account that was setup during the creation of the cloud collector.
- Ensure the retention period aligns with your storage policies however we recommend at minimum 7 days.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.8 - BeyondTrust Endpoint Privilege Management (EPM)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure BeyondTrust EPM Cloud to send events to a Samurai Cloud Collector.
Prerequisites
Ensure that a Samurai Cloud Collector of type Splunk HTTP Event Collector (HEC) has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed Samurai HEC Cloud Collector you will need (displayed only upon creation):
- API URL
- Token
From the BeyondTrust Privilege Management Console
Follow the BeyondTrust SIEM settings documentation:
When following the vendor documentation, please use the following:
- Enter the details of your Splunk configuration:
- Hostname: The Samurai Cloud Collector API URL
- Index: (This is ignored by Samurai so enter a dummy value)
- Token: The Samurai Cloud Collector token
- Data format:
- CIM - Common Information Model
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.9 - Blackberry CylancePROTECT
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure CylancePROTECT to send logs to a Samurai Local Collector deployed on your network. CylancePROTECT requires access to the Local Collector via syslog on port 514/TCP.
To complete this Integration you will need to:
1) From the Cylance Console
Cylance syslog configuration
Follow the steps outlined within the Blackberry documentation:
Use the following parameters when completing the steps:
| Blackberry Documentation Step | Field Name | Parameter |
|---|---|---|
| 3 | Event Types | All types related to CylancePROTECT |
| 5 | SIEM | Other |
| 6 | Protocol | TCP (TLS/SSL unchecked) |
| 8 | IP/Domain | Samurai Local Collector IP address |
| 9 | Port | 514 |
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.10 - Check Point Harmony SASE
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Check Point Harmony SASE to send events to a Samurai Cloud Collector.
Prerequisites
Ensure that a Samurai Cloud Collector of type Splunk HTTP Event Collector (HEC) has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed Samurai HEC Cloud Collector you will need (displayed only upon creation):
- API URL
- Token
From the Check Point Harmony SASE Management Console
Follow the Check Point documentation:
When following the documentation, please use the following:
- Enter these:
- Splunk HEC Host: The Samurai Cloud Collector API URL
- HEC Port: 443
- Protocol: HTTPS
- Verify SSL Certificate: Enabled
- HEC URI: (value is automatically populated)
- Authentication Token: The SamurAI Cloud Collector token
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.11 - Check Point Next-Generation Firewall
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Ensure Connectivity Requirements are in place
2) From Check Point Management Console:
- Configure Syslog Settings
- Create an NTT Account
- Defining Trusted Clients
- Enable Packet Capture for IPS Protections
- Enable Packet Capture for IPS Core Protections
3) From the SamurAI Portal:
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| Check Point Management Center | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
| Samurai Local Collector | Check Point Management Center | TCP/443 (https) | Application Programming Interface (API) access |
Configure Syslog Settings
Once you have validated or updated your Check Point version follow the steps outlined in the Check Point documentation section Advanced Deployment:
Use the following parameters when completing the Advanced Deployment :
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTT-LOGEXPORT |
| target-server | IP address of your Samurai Local Collector |
| target-port | 514 |
| protocol | tcp |
| format | default |
| read-mode | semi-unified |
| export-attachment-ids | true |
cp_log_export add name NTT-LOGEXPORT target-server <SAMURAI Local Collector IP> target-port 514 protocol tcp format default read-mode semi-unified export-attachment-ids true
Create an NTT Account
When you Complete the Check Point Next-Generation Firewall Integration in the SamurAI Portal you can choose to use a username/password or API key for authentication. Note the authentication method when following the steps below.
Follow the Check Point documentation to create an NTT Account with password authentication:
Follow the Check Point documentation to create an NTT Account with API key authentication:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTTUser |
| Authentication method | Select either Check Point Password OR API Key |
| Password | If Authentication method is Password - Set the password in accordance with your policy, you will need this to complete the integration in the SamurAI Portal. |
| Permission Profile | Read Only All (Check Point Documentation) |
Defining Trusted Clients
In order to allow the NTT Account to access the Security Management Server via either username/password or API key it may be needed to configure Trusted Clients in the Check Point Management Console.
Follow the Check Point documentation when defining trusted clients:
General recommendation is to limit access to IPv4 Address and specifying the IP address of the Samurai Local Collector.
Enable Packet Capture for IPS Protections
Follow the Check Point documentation to enable packet capture for specific profiles:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Logging / Track | Log |
| Capture Packets | Enabled (check box) |
Enable Packet Capture for IPS Core Protections
Follow the Check Point documentation to enable packet packet for IPS Core Protections:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Logging / Track | Log |
| Capture Packets | Enabled (check box) |
| Protection Scope | Apply to all HTTP traffic |
Complete the Check Point Next-Generation Firewall Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Check Point Next-Generation Firewall
You will be presented with the Local Collector IP Address on the left of the screen
To configure Extended Telemetry Collection ensure it is enabled via the toggle
Enter the following information:
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description - optional but if completed will appear in the SamurAI Portal for you to easily reference)
- Devicename - an arbitrary name to identify the Check Point device
- IP - IP address of host - this can include multiple separated by a comma (,)
- API-key (optional) - if this is not specified will default to Username/Password
- Domain (optional) - if the user is created in a specific domain, specify the domain
- Username (optional) - enter a username if not using an API-Key
- Password - specify password to use
- Port - if you have changed the default port enter the port number, if not, we default to 443
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.12 - Cisco Identity Services Engine (ISE)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco Identity Services Engine to send logs to a Samurai Local Collector deployed in your network.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Cisco ISE | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure Syslog
Follow the steps outlined in Remote Logging Target Settings using the following parameters:
| Field Name | Parameter |
|---|---|
| Target Type | TCP Syslog |
| IP Address | IP address of your Samurai Local Collector |
| Port | 514 |
| Maximum Length | 8192 |
| Comply to RFC 3164 | Enabled |
With the following logging categories enabled:
| Logging Category |
|---|
| AAA Audit |
| Failed attempts |
| Passed Authentications |
| Administrative and Operational Audit |
| Posture and Client Provisioning Audit |
| MDM |
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.13 - Cisco IOS Routers and Switches
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco IOS to send logs to a Samurai Local Collector deployed on your network. Your Cisco IOS device(s) require access to the Local Collector via syslog on port 514/UDP.
To complete this Integration you will need to:
1) From your Cisco IOS device
Configure Log
Use these instructions to configure Cisco IOS.
- Log into the Cisco IOS device and specify the following commands:
1. en
2. conf t
3. no logging on
4. archive
5. log config
6. logging enable
7. logging size 1000
8. notify syslog contenttype plaintext
9. hidekeys
10. exit
11. exit
12. logging host [Local Collector IP Address] where [Local Collector IP Address] is the IP address of the Samurai Local Collector deployed on your network.
13. logging trap 6
14. login on-failure log every 1
15. login on-success log every 1
16. logging origin-id hostname
17. logging source-interface [Interface Name] where [Interface Name] is the name of the interface that has access to the Samurai Local Collector.
18. no service sequence-numbers
19. no service timestamps
20. service timestamps log datetime localtime show-timezone
21. no logging message-counter syslog
22. no logging console
23. no logging monitor
24. logging buffered 16384 informational
25. logging on
26. end
27. wr mem
Test the logging configuration
- Execute the following commands to generate a %SYS-5-CONFIG_I log.
conf t
end
Configure ACL log
To configure logging of specific ACLs, add the option log to the end of the ACL to be monitored. For example:
access-list 101 deny tcp any host 192.168.35.0/24 25 log
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.14 - Cisco Meraki MX Security Appliances
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco Meraki Security Appliances to send logs to a Samurai Local Collector deployed on your network. Cisco appliances require access to the Local Collector via syslog on port 514/UDP.
To complete this Integration you will need to:
1) From the Meraki Dashboard:
Meraki syslog configuration
Log in to the Meraki Dashboard and complete the following steps:
- Click Network-wide.
- Click General.
- Click Add a syslog server.
- In the Server IP field, enter the IP address of the Collector appliance deployed on your network.
- Specify the Port as 514.
- Select all the available Roles.
- Click Save.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.15 - Cisco Secure Endpoint
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Within the Cisco Secure Endpoint web interface
2) From Cisco Secure Malware Analytics
3) From the SamurAI Portal:
Determine API Endpoint
The URL for API access Secure Endpoint depends on the region the instance is located, at the time of writing the following are available:
- api.amp.cisco.com
- api.apjc.amp.cisco.com
- api.consumer.amp.cisco.com
- api.eu.amp.cisco.com
The URL for API access to Secure Malware Analytics depends on the region the instance is located, at the time of writing the following are available:
Generate API Credentials
Use the steps below to generate API credentials to allow a Samurai cloud collector to gather telemetry from Secure Endpoint:
Log in to your Cisco Secure Endpoint Instance.
Click Accounts > API Credentials
Click + New API Credential
Add a new API key with the following information:
In the Application name field, enter an appropriate name
From the Scope list, ensure Read & Write is selected
Click Create
The API credentials are displayed
Make a note of the 3rd Party API Client ID and API Key values
Generate Secure Malware Analytics API Credentials
Use these steps to generate API credentials to allow Samurai to gather telemetry from Secure Malware Analytics:
Log in to your Cisco Secure Malware Analytics Instance.
In the top-right click on your account name,then My Account
If no API key has been generated previously, click Generate API Key
Make a note of the API Key
Complete the Cisco Secure Endpoint Integration
You will need:
- Devicename (arbitrary name)
- API Endpoint (from Determine API Endpoint)
- API Client ID (from Generate API Credentials)
- API Key (from Generate API Credentials)
- Secure Malware Analytics API Key (from Generate Secure Malware Analytics API Credentials)
Login to the SamurAI Portal
Click Telemetry and select Integrations
Select Create
Locate and click Cisco Secure Endpoint
Click Next (we leverage a Samurai Cloud Collector)
Enter a Name of Integration
Enter a Description (Optional)
Enter your Devicename
Enter your API Endpoint
Enter your API Client ID
Enter your API Key
Enter your Secure Malware Analytics Endpoint
Enter your Secure Malware Analytics API Key
Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.16 - Cisco Secure Firewall (ASA Appliances)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco Secure Firewall (ASA Appliances) to send logs to a Samurai Local Collector deployed on your network. Your Cisco appliances require access to the Local Collector via syslog on port 514/UDP.
To complete this Integration you will need to:
1) From your Cisco Firewall:
Configure syslog
Perform the following steps to configure syslog:
Log in to the Cisco ASA
From the command line specify the following commands to setup logging:
en
conf t
logging enable
logging timestamp
logging device-id
logging standby
logging trap debugging
logging queue 1024
logging host [interface name] [Local Collector IP Address]
where:
[interface name] is the name of the interface closest/routable to the Local Collector, and
[Local Collector IP Address ] is the IP address of the Samurai Local Collector deployed on your
network .
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.17 - Cisco Secure Firewall (Firepower Threat Defense)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco Secure Firewall Threat Defense (FTD) (previously entitled Firepower Threat Defense) to send syslog to a Samurai Local Collector.
1) Ensure Connectivity Requirements are in place
2) From Cisco Secure Firewall Management Center console:
- Send Security Event Syslog Messages from FTD Devices
- Enabling External Access to the Database
- Database User Creation
3) From the SamurAI Portal
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| FTD | Samurai Local Collector | UCP/514 (syslog) | For log transmission |
| Samurai Local Collector | FMC | TCP/1500 & TCP/2000 | Database access |
Send Security Event Syslog Messages from FTD Devices
Follow the steps outlined within the Cisco documentation:
Cisco Documentation Step 1:
Use the following parameters:
| Cisco Documentation Step | Field Name | Parameter |
|---|---|---|
| 1d | IP Address | Samurai Local Collector IP address (verify or add the address) |
| 1d | Protocol | UDP |
| 1d | Port | 514 |
| 1d | Security Zones or Named Interface | Select the interface/zone on which the Samurai Local Collector is reachable |
| 1e | Time Stamp Format | RFC 5424 (yy-MM-ddTHH:mm:ssZ) |
| 1e | Enable Syslog Device ID | Enabled (Host Name) |
| 1f | Send syslogs in EMBLEM format | Unchecked |
Cisco Documentation Step 2:
Use the following parameters:
| Field Name | Field Name | Parameter |
|---|---|---|
| 2f | IPS Settings | Send Syslog Messages for IPS Events (Selected) |
| 2f | File and Malware Settings | Send Syslog messages for File and Malware events (Selected) |
Cisco Documentation Step 3:
Complete the steps outlined.
Cisco Documentation Step 4:
Use the following parameters:
| Field Name | Field Name | Parameter |
|---|---|---|
| 4d | Logging | Log at End of Connection (Selected) |
Cisco Documentation Step 5:
Complete the steps outlined.
Enabling External Access to the Database
Follow the steps outlined within the Cisco documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Allow External Database Access | Enabled |
| Server Hostname | If this is blank, enter the IP address of the Cisco Firepower Management Center that is being configured. |
| Add Hosts > IP Address | IP address of your Samurai Local Collector |
Database User Creation
Follow the steps outlined within the Cisco documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| User Name | Whatever you want |
| Authentication > Use External Authentication Method | Unchecked |
| Password | Whatever you want, but need to comply with Password Policy |
| Options | Only check Check Password Strength. Other than that, unchecked. |
| Default User Roles | Only check External Database User. Other than that, unchecked. |
Complete the Cisco Secure Firewall (Firepower Threat Defense) Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Click Create
- Find and select Cisco Secure Firewall (Firepower Threat Defense)
- Select the relevant Local Collector and click Next
- You will be presented with the Local Collector IP Address
- Click Next
- Complete the fields required including the Database Username and Password you created in Database user creation
- Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.18 - Cisco Umbrella
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Cisco Umbrella to send logs to S3 storage for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that an AWS cloud collector has been deployed via the SamurAI Portal.
If you are planning to reuse an already deployed AWS cloud collector, the information can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information:
- Account number
- Bucket name
- Region
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enable Logging in the Cisco Umbrella Console
Follow the Enable Logging section (Steps 1-3) in the Cisco Umbrella documentation:
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.19 - Citrix Netscaler (Formely Netscaler ADC)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Citrix Netscaler to send logs to a Samurai Local Collector deployed on your network. Citrix Netscaler requires access to the Local Collector via syslog on port 514/UDP.
To complete this Integration you will need to:
1) From your Citrix Netscaler Appliance :
Follow the steps outlined within the Citrix documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Auditing Type | SYSLOG |
| Name | Whatever you want, however we suggest NTT_syslog_action |
| ServerIP | IP address of your Samurai Collector |
| serverPort | 514 |
| logLevel | EMERGENCY,ALERT,CRITICAL,ERROR,WARNING,NOTICE,INFORMATIONAL |
| dateFormat | MMDDYYYY |
| transport | UDP |
Table 1: Audit-log Action
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_syslog_policy |
| rule | Use the Audit-log action you created above. |
Table 2: Audit-log Policy
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.20 - Claroty Continuous Threat Detection (CTD)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Claroty CTD to send logs to a Samurai Local Collector deployed on your network. Claroty CTD requires access to the Local Collector via syslog on port 514/TCP.
Prerequisites
The following integration will configure Rules for Baseline, Event and Alert Logs. A user account is also created for read-only API access to gather additional telemetry.
To complete this Integration you will need to:
1) From the Claroty Web management user interface
2) From the SamurAI Portal
Configure Save CAPs and Detect Known Threats
- Log in to Claroty’s web configuration dashboard.
- Click the Configuration tab.
- In the Networks area:
- Select the checkbox to enable Save Caps
- Select the checkbox to enable Detect Known Threats
Configuration of Rules
Baseline Rule
Log in to Claroty’s web configuration dashboard.
On the main menu on the left, click Configuration
Select Integrations > SIEM Syslog
Complete the following steps to add a rule to send baseline logs:
In the SIEM Syslog screen click on the “+” button
In the From list, click the relevant site(s)
The Add new Syslog screen will appear
Update the following fields:
- Uncheck the LOCAL checkbox
- From the MESSAGE CONTENTS list, click Baselines
- From the MESSAGE FORMAT list, click CEF
- Protocol - select all from the available list
- Communication Type - select all available options
- Access Type - select all available options
- Server - enter in the IP address of your Samurai Local Collector
- Port - enter 514
- Protocol - TCP
Click Save
Events Rule
Log in to Claroty’s web configuration dashboard.
On the main menu on the left, click Configuration
Select Integrations > SIEM Syslog
Complete the following steps to add a rule to send Events logs:
In the SIEM Syslog screen click on the “+” button
In the From list, click the relevant site(s)
The Add new Syslog screen will appear
Update the following fields:
- Uncheck the LOCAL checkbox
- From the MESSAGE CONTENTS list, click Events
- From the MESSAGE FORMAT list, click CEF
- Below Select Filters for the corresponding alerts configure:
- Category - select all available selections
- Protocol - select all from the available list
- Server - enter in the IP address of your Samurai Local Collector
- Port - enter 514
- Protocol - TCP
Click Save
Alert Rule
Log in to Claroty’s web configuration dashboard.
On the main menu on the left, click Configuration
Select Integrations > SIEM Syslog
Complete the following steps to add a rule to send Alerts logs:
In the SIEM Syslog screen click on the “+” button
In the From list, click the relevant site(s)
The Add new Syslog screen will appear
Update the following fields:
- Uncheck the LOCAL checkbox
- From the MESSAGE CONTENTS list, click Alerts
- From the MESSAGE FORMAT list, click CEF
- Category - select all available selections
- Protocol - select all from the available list
- Server - enter in the IP address of your Samurai Local Collector
- Port - enter 514
- Protocol - TCP
Click Save
Create an account for API access
- Log in to Claroty’s web configuration dashboard.
- On the main menu select Configuration and Users
- In the User Management configuration screen, Click Add new users
- Enter a Username
- Enter a Full Name
- Enter a Password
- Repeat the Password
- Click Add
Create a Group with permissions for the API access account
- Log in to Claroty’s web configuration dashboard.
- On the main menu select Configuration and Groups
- In the Group Management configuration screen, Click Add new groups
- Enter a Group Name
- Select the user created in Create an account for API access from the Add User dropdown list
- In the Systems Permissions area, Click Add permission
- Select specific sites to which the permissions applies, or All Sites
- From the All dropdown list, select relevant option
- Set the appropriate permission level to Read
- Click Save
Complete the Claroty Continuous Threat Detection (CTD) Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Claroty Continuous Threat Detection (CTD)
Select the relevant Local Collector and click Next
You will be presented with the Local Collector IP Address on the left of the screen
To configure Extended Telemetry Collection ensure it is enabled via the toggle
Enter the following information:
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description - optional but if completed will appear in the SamurAI Portal for you to easily reference)
- Devicename - an arbitrary name to identify the Claroty CTD device
- IP Address - the IP address of Claroty CTD
- Username - enter the username you created in Create an account for API access
- Password - enter the password you created in Create an account for API access
- Port (Optional)- if you have changed the default port enter the port number, if not, we default to 5000
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.21 - Claroty xDome
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Claroty xDome to send logs to a Samurai Local Collector deployed in your network.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Claroty xDome Collection Server | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure Claroty Syslog
Follow the steps outlined in About Claroty Syslog (Claroty login is required) using the following parameters:
| Field Name | Parameter |
|---|---|
| Destination IP | IP address of your Samurai Local Collector |
| Transport Protocol | TCP |
| Destination Port | 514 |
| Message Format | JSON |
| Syslog Protocol Standard | RFC 5424 |
| Installation Server | Select your xDome collection server |
| Export Comm. Events | ON. Select All Event Types and All Devices |
| Export Alerts | ON. Select All Alert Types |
| Export Vulnerabilities | ON. Select All |
Table 2: Claroty Syslog Configuration
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.22 - Clavister NetWall
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure a Clavister NetWall firewall to send syslog events to a Samurai Local Collector deployed in your network.
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| Clavister NetWall | Samurai Local Collector | TCP/514 or UDP/514 | For log transmission |
Configure Clavister Netwall
Follow the vendor documentation to add a new syslog receiver:
Perform the steps under section Example 2.29. Enabling Syslog RFC-5424 Compliance with Hostname.
Adjust Syslog service to TCP
Optionaly, in the cOS Core web interface:
- Navigate to: Objects -> Serivces
- Click on Syslog
- Modify Type and set the protocol to TCP
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.23 - Click Studios Passwordstate
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Passwordstate | Samurai Local Collector | TCP/514 | For log transmission |
Configure syslog
Follow the documentation for syslog server configuration in section 4.9 of the Passwordstate Security Administrators Manual, using the following parameters:
- Syslog Server: IP address of the Samurai Local Collector
- Port Number: 514
- Protocol: TCP
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.24 - Crowdstrike Falcon Insight
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) From the Crowdstrike Falcon Console:
2) From the SamurAI Portal:
3) Complete and send authorization form
Create a new API client
For additional information you can refer to the Crowdstrike documentation
To create a new API client follow the steps below:
Log in to the Crowdstrike Falcon Console
Click the Support and resources icon in the left menu pane.
Under Resources and tools select API Clients and Keys. The API Clients and Keys page is displayed.
Click Create API client. The Create API client page appears.
Perform the following steps:
5.1 Specify NTT API Client in the CLIENT NAME field.
5.2 Specify API client for NTT in the DESCRIPTION field.
5.3 Under API SCOPES, perform the following steps:
5.4 Select the Read checkbox for:
- Detections
- Event Streams
- Host groups
- Hosts
- Prevention policies
- Threatgraph
- User Management
5.5 Select the Write checkbox for:
- Hosts
Click Create to save the API client and generate the client ID and secret.
Copy and record the values:
- CLIENT ID
- SECRET
- Take note of your Cloud location which is dervived from the Base URL as per the table below, you will need to specify the cloud location under Complete the Crowdstrike Falcon Insight Integration.
The table below outlines the Cloud location and Base URL:
| Cloud Location | Base URL |
|---|---|
| US-1 | https://api.crowdstrike.com |
| US-2 | https://api.us-2.crowdstrike.com |
| EU-1 | https://api.eu-1.crowdstrike.com |
| US-GOV-1 | https://api.laggar.gcw.crowdstrike.com |
Complete the Crowdstrike Falcon Insight Integration
You will need:
- OAuth Client ID: (from Step 7 under Create a new API client)
- OAuth Secret: (from Step 7 under Create a new API client)
- Cloud location: (from Step 8 under Create a new API client)
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Select Create
Locate and click Crowdstrike Falcon Insight
Click Next (we leverage a Samurai Cloud Collector)
Enter a Name of Integration
Enter a Description (Optional)
Enter your OAuth Client ID
Enter your OAuth Secret
Select your Cloud Location (US-1 is default).
Click Finish
Complete and send authorization form
The Samurai SOC requires access to your Crowdstrike instance in order to:
- Perform deeper investigations
- Access data not present in the APIs
- Perform remote isolation tasks
To ensure the Samurai SOC has access please complete this form Authorization Form for Access to Crowdstrike Falcon Host by MSP Personnel.
Once you have completed, email the form to mssp@crowdstrike.com.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.25 - CyberArk Privileged Access Security (PAS)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure CyberArk PAS to send logs to a Samurai Local Collector deployed on your network. Your CyberArk PAS Vault deployment requires access to the Local Collector via syslog on port 514/UDP.
To complete this Integration you will need to:
1) From CyberArk Vault
Configure Vault to forward syslog messages
Follow the steps below, you may also wish to refer to CyberArk documentation.
Download ntt.xsl.
Log in to the (primary) CyberArk PAS Vault server as the administrator user
Navigate to the <CyberArk install folder>\Server\Syslog directory.
- By default, the subdirectory is: C:\Program Files (x86)\PrivateArk\Server\Syslog
Copy the ntt.xsl file into the directory.
Navigate to the <CyberArk install folder>\Server\ directory.
- By default, the subdirector is: C:\Program Files (x86)\PrivateArk\Server\
Copy the existing DBParm.ini file to DBParm.ini.bak file within the same directory (in case you need to rollback)
Edit the DBParm.ini file and make the following configuration changes:
For example:
SyslogServerIP=1.1.1.1,2.2.2.2
SyslogServerPort=514,6514
In the above example, server 1.1.1.1 would match with port 514, while server 2.2.2.2 would match with port 6514.
- For SyslogServerIP, enter the IP address of the Samurai Local Collector deployed on your network.
- For SyslogServerPort, enter 514
- For SyslogServerProtocol, enter TCP
- For SyslogTranslatorFile, enter Syslog\ntt.xsl
This is the file mentioned in step 1 & 4 - For SyslogMessageCodeFilter, enter 0-999.
- For UseLegacySyslogFormat, enter No.
The changes to DBParm.ini should look like the following example:
[SYSLOG]SyslogServerIP=1.1.1.1SyslogServerPort=514SyslogServerProtocol=TCPSyslogTranslatorFile=Syslog\ntt.xslSyslogMessageCodeFilter=0-999UseLegacySyslogFormat=No
Save the file
Restart the Vault server
- If applicable. perform the procedure on all Primary and Satellite Vaults.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.26 - Digital Arts i-Filter
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Digital Arts i-Filter to send events to a Samurai Local Collector deployed in your environment.
Product Version Requirements
i-Filter must at least the following version:
- i-Filter for Linux v.10
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| i-Filter | Samurai local collector | TCP/514 | For log transmission |
i-Filter Access Log Settings
Follow the steps outlined within each section below:
Access Log Settings
Login to the i-Filter management console
Go to System / Log / Access Log Settings
Configure the parameters below:
- Set Format Setting to Detailed Mode
- Specify Format as indicated in the table below.
| Output Order | Field Name | Field Content |
|---|---|---|
| 1 | output_log_date | Access log output date and time |
| 2 | process_id | Process number |
| 3 | product | Product |
| 4 | vendor | Vendor |
| 5 | ifilter_version | i-Filter version |
| 6 | realy_proxyip | Upper proxy server IP address |
| 7 | public_ip Source | IP address |
| 8 | src_ip | Client |
| 9 | hostname | Computer name |
| 10 | access_date | Access start date and time |
| 11 | status | HTTP response code |
| 12 | bytes_in | HTTP response size |
| 13 | bytes_out | HTTP request size |
| 14 | filter_action | Filter action |
| 15 | r_id | Rule object ID |
| 16 | virus_name | Virus name |
| 17 | ssl_parameter | SSL parameter encryption presence |
| 18 | post_info | File information at the time of POST |
| 19 | http_method | HTTP method |
| 20 | http_version | HTTP version |
| 21 | http_referer | HTTP referrer |
| 22 | http_user_agent | HTTP user agent |
| 23 | http_content_type_raw | HTTP content type |
| 24 | dest_ip | Destination IP address |
| 25 | dest_port | Destination port number |
| 26 | src_port | Source port number |
| 27 | client_port | Client port number |
| 28 | dest_host | Destination host name |
| 29 | user | Authentication user name (non-encoded) |
| 30 | group_name | Group name (non-encoded) |
| 31 | url | URL (non-encoded) |
| 32 | ss_time | Session time |
| 33 | au_status | Authentication status |
| 34 | filter_reason | Filter reason (non-encoded) |
| 35 | url_category_list | URL category list name (non-encoded) |
| 36 | web_service_name | Web service name (non-encoded) |
| 37 | http_response | HTTP response code (upper) |
| 38 | checksum | Checksum |
Log Output Settings
The log format must be set as follows. In this document it is displayed with line breaks but in reality it is a single line:
output_log_date="%ltl",process_id="%pid",product="ifilter",vendor="DigitalArts",ifilter_version="%vr"
,realy_proxyip="%pp",public_ip="%sip",src_ip="%>a",hostname="%>A",access_date="%tl",status="%hst",
bytes_in="%<st",bytes_out="%>st",filter_action="%bk",r_id="%rid",virus_name="%vi",ssl_parameter="%en"
,post_info="%pl",http_method="%rm",http_version="%rv",http_referer="%hrf",http_user_agent="%hua",
http_content_type_raw="%mt",dest_ip="%dip",dest_port="%dpt",src_port="%spt",client_port="%cpt",
dest_host="%hnm",user="%Dul",group_name="%Dgn",url="%Dru",ss_time="%Tss",au_status="%Aus",
filter_reason="%DFR",url_category_list="%DCT",web_service_name="%DWID",http_response="%hrst",checksum="%ccs"
Access Log Transfer Settings
From the i-Filter management console
Go to System / Log / Access Log Transfer Settings
Configure the parameters below:
- Enable the Access Log Transfer Function
- Set the Maximum Size per Line to 64 KB
Access Log Transfer Server Settings
From the i-Filter management console
Go to System / Log / Access Log Transfer Server Settings
Configure the parameters below:
- Enable the Effective Setting
- Specify the target set in Access Log Tansfer Settings for Access Log Settings
- Set the Address to the IP address of the Samurai Local Collector deployed on your network
- Set the Port Number to 514
- Set the Transfer Protocol to TCP
- Set the Transfer Format to syslog format
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.27 - ESET PROTECT
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure ESET PROTECT On-Prem to send logs to a Samurai Local Collector deployed in your network.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| ESET PROTECT | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Syslog Configuration
Follow the steps described in Export logs to Syslog using the following parameters:
| Parameter | Value |
|---|---|
| Host | IP of the Samurai Local Collector |
| Port | 514 |
| Format | Syslog |
| Transport | TCP |
| Exported logs format | JSON |
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.28 - F5 Application Security Module (ASM)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure F5 Application Security Module to send logs to a Samurai Local Collector deployed in your network.
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| BIG-IP ASM | Samurai Local Collector | TCP/514 | For log transmission |
To send ASM logs to a Samurai Local Collector
Follow the steps outlined in the F5 documentation:
Follow each section outlined below. If you have already created a logging profile navigate to the next section:
- Creating a logging profile
- Setting up remote logging
- Associating a logging profile with a security policy
Perform the below settings adjustments as you work through the steps. In case a setting property is not referenced below, simply use the default value.
- Application Security: Application Security Checkbox (Enabled)
When enabled, additional Application Security fields will be displayed. Use the parameters outlined below when completing the additional fields:
- Remote Storage: Checkbox enabled
- Logging Format: Key-Value Pairs
- Protocol: TCP
- Server Addresses: IP address of your Samurai local collector
- Server Addresses Port: 514
- Storage Filter Request Type: All Requests
Ensure you associate the logging profile with the relevant security policy by following the steps in the F5 documentation.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.29 - F5 BIG-IP LTM
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| BIG-IP LTM | Samurai Local Collector | TCP/514 | For log transmission |
Follow steps in F5 documentation
Perform the steps outlined in the vendor documentation to configure and implement a Request Logging profile:
Perform the below settings adjustments under the relevant section. In case a setting property is not referenced below, simply use the default value.
Creating a pool with request logging to manage HTTP traffic
- IP address of logging server: Insert the IP address of the Samurai Local Collector.
- Service Port: 514
Creating a request logging profile
- HSL Protocol: TCP
- Custom Request Settings:
BIGIP_LTM_WEB $BIGIP_HOSTNAME $VIRTUAL_NAME $NCSA_COMBINED
Configuring a request logging profile for responses
- HSL Protocol: TCP
- Custom Request Settings:
BIGIP_LTM_WEB $BIGIP_HOSTNAME $VIRTUAL_NAME $NCSA_COMBINED
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.30 - Fortinet FortiAnalyzer
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Ensure Connectivity Requirements are in place
2) From the FortiAnalyzer
3) From your Fortigate devices (if using Fortigate devices)
4) From your FortiWeb devices (if using Fortiweb devices)
5) From the SamurAI Portal:
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| FortiAnalyzer | Samurai Local Collector | UDP/514 (syslog) | For log transmission |
| Samurai Local Collector | FortiAnalyzer | TCP/443 (https) default or your definition | Optional (based on optional configuration in this article) |
Create a reduced restricted profile
Follow the steps outlined in the Fortinet documentation:
Use the following parameters when completing the steps:
| Profile system settings | Value |
|---|---|
| Profile Name | Whatever you want, however we suggest ntt_restricted_user |
| Options | Set all options to None except Log View / FortiView which should be set to Read-Only |
Configure log forwarding
Follow the steps outlined in the Fortinet documentation:
Use the following required parameters when completing the steps:
| Log forward setting | Value |
|---|---|
| Name | Whatever you want, however we suggest NTT_collector |
| Status | On |
| Remote Server Type | Syslog |
| Server Address | IP address of your collector |
| Server Port | 514 |
| Compression | Off |
| Reliable Connection | Off |
| Sending Frequency | Real-time |
| Device Filters | Click Select Device, then select the devices whose logs will be forwarded (Note: you may have to come back to this if you are not sending logs from your Fortigate devices yet!) |
| Log filters | Off |
| Enable exclusions | Off |
| Enable Masking | Off |
Create a new administrator
Follow the steps outlined in the Fortinet documentation:
Use the following parameters when completing the steps:
| Administrator account | Value |
|---|---|
| User Name | Whatever you want, however we suggest ntt_user |
| Description / Comments | Whatever you want |
| Admin Type | LOCAL |
| Password | Enter a secure password, you will need this later for the integration |
| Admin Profile | Select the profile from the the previous step, we recommended ntt_restricted_user |
| Administrative Domain | Select based on your setup or use the default option, All ADOMS |
| JSON API Access | Read |
| Trusted Hosts (optional) | You can optionally restrict this account to the IP address of your Collector |
Enable FortiGate to send logs and PCAP to FortiAnalyzer
All FortiGate devices in scope must be connected to the FortiAnalyzer to send logs and PCAP.
Follow the steps outlined in the Fortinet documentation:
Use the following required parameters when completing the steps:
| Remote Logging and Archiving | Value |
|---|---|
| Send logs to FortiAnalyzer/FortiManager | Enable |
| Server | IP address for your FortiAnalyzer |
| Upload option | Real Time |
Disk backed log buffer is recommended on Fortigates with an SSD disk.
Follow the steps outlined in the Fortinet documentation:
Configure FortiAnalyzer policies for FortiWeb
Follow the steps in the section entitled ‘Configuring FortiAnalyzer policies’ outlined in the Fortinet FortiWeb documentation:
Complete the Fortinet FortiAnalyzer Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Fortinet FortiAnalyzer
Select the relevant Local Collector and click Next
Enter the following information
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description - optional but if completed will appear in the SamurAI Portal for you to easily reference)
- The Username and Password you created in Create a new administrator
- Select Enable PCAP (only applicable to FortiGate devices) which was enabled in Enable FortiGate to send logs and PCAP to FortiAnalyzer
- Hostname/IP - enter FortiAnalyzer hostname or IP address
- Port (Optional) - if you have changed the default port enter the port number, if not, we default to 443
- adom (optional) - if not specified we default to “root”
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.31 - Fortinet FortiEDR Cloud
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure a cloud based Fortinet FortiEDR Central Manager for telemetry data ingestion to the Samurai platform.
Follow the steps below:
1. From the FortiEDR Central Manager (Cloud)
2. From the SamurAI Portal
Create a user with a REST API role
Follow the Fortinet documentation:
When completing the steps use the following parameters:
| Attribute | Parameter |
|---|---|
| Role | Read-Only |
| Advanced | Rest-API (Checked) |
| Two-Factor Authentication | Ensure it is disabled |
Additional information required
You will also need to provide additional information to complete the integration. This includes:
- Deployment URL: This is the URL utilized to access the Cloud based FortiEDR Central Manager .
- Organization: This is the Organization name used when logging into the FortiEDR Central Manager
Complete the Fortinet FortiEDR Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Fortinet FortiEDR (cloud)
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Deployment URL
- Enter your Organization
- Enter your Username
- Enter your Password
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.32 - Fortinet FortiEDR On-Premise
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure an On-Premise deployed Fortinet FortiEDR Central Manager for telemetry data ingestion to the Samurai platform.
Follow the steps below:
1) Ensure Connectivity Requirements are in place
2. From the FortiEDR Central Manager (On-Premise)
3. From the SamurAI Portal
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Samurai Local Collector | FortiEDR Central Manager (On-Premise) | TCP/443 (https) | Application Programming Interface (API) access |
Create a user with a REST API role
Follow the Fortinet documentation:
When completing the steps use the following parameters:
| Attribute | Parameter |
|---|---|
| Role | Read-Only |
| Advanced | Rest-API (Checked) |
| Two-Factor Authentication | Ensure it is disabled |
Additional information required
You will also need to provide additional information to complete the integration. This includes:
- Deployment URL: This is the URL utilized to access the On-Premise deployed FortiEDR Central Manager
- Example: https://IP address or Hostname (if hostname it must resolve to the IP address)
- Organization: This is the Organization name used when logging into the FortiEDR Central Manager (On-Premise)
Complete the Fortinet FortiEDR On-premise Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Fortinet FortiEDR (on-prem)
- Click Next
- Select the relevant Local Collector and click Next
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Local Deployment URL - example https://IP or hostname (if hostname is used, it must be resolveable and accessible from the local collector)
- Enter your Organization
- Enter your Username
- Enter your Password
- Select the Fallback timezone - this is the timezone to assume if no epoch field exists in the data. UTC and CET (for CET/CEST) supported.
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.33 - Fortinet FortiGate Next-Generation Firewall
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
1) Ensure Connectivity Requirements are in place
2) From FortiGate Next-Generation Firewall console:
- Configure Syslog Forwarding Settings
- Configure Log Settings for Each Security Features
- Configure IPS Packet Logging
- Configure the Storage Settings
- Configure API Access Permission and Create API Key
3) If you have configured the options above, from the SamurAI Portal:
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| FortiGate NGFW | Samurai Local Collector | UDP/514 (syslog) | For log transmission |
| Samurai Local Collector | FortiGate NGFW | TCP/443 (https) default or your definition | Application Programming Interface (API) access |
Configure Syslog Forwarding Settings
Execute the CLI commands outlined in the FortiGate Next Generation Firewall documentation.
config log syslogd4 setting
set status enable
set server [IP address of your Samurai Collector]
set mode udp
set port 514
unset source-ip
set format default
end
config log syslogd4 filter
set filter [see table 1]
set filter-type include
end
The following table shows the value indicating the send log for each security function.
| Security Features | Value indicating the send log (One line each; no separator) |
|---|---|
| IPS/IDS Features | “ips-level(information)” |
| IPS/IDS and AntiVirus Features | “ips-level(information)virus-level(information)” |
| IPS/IDS and AntiVirus Features and Web Filter Features | “ips-level(information)virus-level(information)webfilter-level(information)” |
Table 1: Security Features Logs To Be Sent
Configure Log Settings for Each Security Features
Execute the CLI commands outlined in the FortiGate Next Generation Firewall documentation.
config firewall policy
edit [Policy ID]
...
set logtraffic [utm or all]
set logtraffic-start disable
...
next
end
config antivirus profile edit [Profile Name] ... set extended-log enable ... nextend
config webfilter profile
edit [Profile Name]
...
set log-all-url disable
set web-content-log enable
set web-filter-activex-log enable
set web-filter-command-block-log enable
set web-filter-cookie-log enable
set web-filter-applet-log enable
set web-filter-jscript-log enable
set web-filter-js-log enable
set web-filter-vbs-log enable
set web-filter-unknown-log enable
set web-filter-refere-log enable
set web-filter-cookie-removal-log enable
set web-url-log enable
set web-invalid-domain-log enable
set web-ftgd-err-log enable
set web-ftgd-quota-usage enable
set extended-log enable
set web-extended-all-action-log enable
next
end
config ips sensor
edit [Sensor Name]
...
set extended-log enable
config entries
edit [ID]
set location all
set severity info low
set protocol all
set os all
set application all
set status [enable or default]
(please refer to the table below)
set log enable
set log-packet disable
set log-attack-context disable
set action [pass or block or reset or default]
(please refer to the table below)
...
next
edit [ID]
set location all
set severity medium high critical
set protocol allset os all
set application all
set status [enable or default]
(please refer to the table 2)
set log enable
set log-packet enable
set log-attack-context disable
set action [pass or block or reset or default]
(please refer to the table 2)
...
Tip: Ensure evaluation order of IPS sensor entries so that the above settings apply properly.
| Action | Status |
|---|---|
| pass or block or reset | enable |
| default | default |
Table 2: Matching Actions to Status
Configure IPS Packet Logging
Execute the CLI command outlined in the FortiGate Next Generation Firewall documentation.
config ips settings set packet-log-history 5 set packet-log-post-attack 10 set ips-packet-quota 0end
Configure the Storage Settings
After checking [HD logging space] with the following command, determine the size of [log-quota] with the following calculation:
[log-quota] = [Total HD logging space] / 2
[log-quota] should be rounded down to the nearest thousand. In the following example, the [log-quota] is 88000.
diagnose sys logdisk usage
Total HD usage: 236286 MB/333 MB
Total HD logging space: 177214 MB
HD logging space usage for vdom "root": 106 MB/177214 MB
Execute the CLI command outlined in the FortiGate Next Generation Firewall documentation.
config log disk setting
set status enable
set ips-archive enable
set max-policy-packet-capture-size 100
set log-quota [calculated value above,for example here, 88000]
set maximum-log-age 5
set full-first-warning-threshold 75
set full-second-warning-threshold 90
set full-final-warning-threshold 95
set max-log-file-size 20
set roll-schedule daily
set diskfull overwrite
...
Configure API Access Permission and Create API Key
Follow the steps outlined in the FortiGate Next Generation Firewall documentation.
Use the following parameters when completing the deployment:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: api_admin |
| Data Access | Read |
Table 3: Administrator Profile
Use the following parameters when completing the deployment:
| Field Name | Parameter |
|---|---|
| Username | Whatever you want, however we suggest: api_user |
| Administrator Profile | Add your administrator profile created above (we suggested api_admin) |
| Trusted Hosts | IP Address of your Samurai Local Collector |
Table 4: REST API Admin
Complete the Fortinet FortiGate Next-Generation Firewall Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Fortinet FortiGate Next-Generation Firewall
Select the relevant Local Collector and click Next
You will be presented with the Local Collector IP Address on the left of the screen
To configure Extended Telemetry Collection ensure it is enabled via the toggle
Enter the following information:
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description - optional but if completed will appear in the SamurAI Portal for you to easily reference)
- Devicename - an arbitrary name to identify the Fortinet device
- API-Key - you generated under Create new Rest API Admin
- Select Enable PCAP
- Hostname/IP - hostname or IP address of Fortinet device to collect alerts from
- Port - if you have changed the default port enter the port number, if not, we default to 443
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.34 - Fortinet FortiWeb
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Fortinet FortiWeb to send logs to a Samurai Local Collector deployed on your network. FortiWeb requires access to the Local Collector via syslog on port 514/UDP.
If you have deployed a FortiAnalyzer, please refer to the Fortinet FortiAnalyzer integration guide.
1) From FortiWeb console:
Configure syslog policy
Follow the steps outlined in the section entitled ‘Configuring Syslog settings’ located within the Fortinet documentation:
Use the parameters defined in the table below for each field:
| Field Name | Parameter |
|---|---|
| Policy Name | Whatever you like, however we recommend ntt_syslog_policy |
| IP Address (remote syslog server) | IP address of your Local Samurai Collector |
| Port | 514 |
| Format | Default |
| Enable TLS | disabled |
Table 1 - Syslog settings
Configure trigger policy
Follow the steps outlined in the section entitled ‘Configuring triggers’ within the Fortinet documentation:
Use the parameters defined in the table below for each field:
| Field Name | Parameter |
|---|---|
| Name | Whatever you like, however we recommend ntt_syslog_trigger |
| Syslog Policy | We recommended ntt_syslog_policy |
Table 2 - Trigger policy
Configure log destination
Follow the steps outlined in the section entitled ‘Configure log destinations’ within the Fortinet documentation:
Use the parameter defined in the table below for each field:
| Field Name | Parameter |
|---|---|
| Global Log Setting | Enable Syslog |
| Syslog Policy | We recommended ntt_syslog_policy |
| Log Level | Information |
| Facility | leave as default (reserved for local use 7) |
Table 3 - Log destination
Enable log types
Follow the steps outlined within the Fortinet documentation:
Use the parameter defined in the table below for each field:
| Field Name | Parameter |
|---|---|
| Other Log Settings | Enable the following: Enable Attack Log Enable Traffic Log Enable Event Log (Optional) |
| System Alert Thresholds | Keep default values for all (CPU Utilization, Memory Utilization, Log Disk Utilization) |
| Trigger Policy | We recommended ntt_syslog_trigger |
Table 4 - Log types
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.35 - GestioIP IPAM
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure GestioIP asset information retrieval from a Samurai Local Collector deployed in your network.
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| Samurai Local Collector | GestioIP IPAM | TCP/443 (HTTPS) | API access |
Create GestioIP User
Follow the steps outlined in section 8.1.1.1 GestioIP Documentation to create a local user or section 8.1.2.2 if using LDAP. If using the authorization feature of GestioIP, ensure that the created user is added to the Read Only default group.
Complete the GestioIP IPAM Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click GestioIP IPAM
- Select a Samurai Local Collector
- Enter the URL to your GestioIP instance
- Enter User and Password as created in Creating GestioIP User
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.36 - Google Workspace
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to perform steps in both Google Workspace and the SamurAI Portal.
The Google Workspace integration leverages two APIs which are part of the Admin SDK API
Follow the steps below:
1. From Google Workspace
- Enable the Admin SDK API
- Create a service account
- Create credentials for the service account
- Delegate domain-wide authority to the service account
2. From the SamurAI Portal
Enable the Admin SDK API
Follow the Google API Console Help documentation:
Ensure you login to the Google Console as a super administrator and use the following parameters when completing the steps:
| Documentation Step | Field Name | Parameter |
|---|---|---|
| 2 | Project Name | Anything you want but we recommend “SamuraiAPI” |
| 2 | Organization | The name of your organization |
| 2 | Location | Anything you want |
| 4 | API Library | Select and enable against the project created in Step 2: “Admin SDK API” “Google Workspace Alert Center API” |
Create a service account
Follow the steps outlined within the Google documentation:
Use the following parameters when completing the steps:
| Documentation Step | Field Name | Parameter |
|---|---|---|
| 3 | Service Account Name | Anything you want but we recommend “SamuraiAPI” |
| 3 | Service Account ID | Anything you want but we recommend “SamuraiAPI” |
| 3 | Service Account Description | Anything you want but we recommend “SamuraiAPI” |
Create credentials for the service account
Follow the steps outlined within the Google documentation:
| Documentation Step | Field Name | Parameter |
|---|---|---|
| 2 | Project | Select the project created in Enable the Admin SDK API |
| 2 | Service Account | Select the service account you created in Create a service account |
| 4 | Key Type | Ensure “JSON” is selected. |
Delegate domain-wide authority to the service account
Follow the steps outlined within the Google documentation:
Use the following parameters when completing the steps:
| Documentation Step | Field Name | Parameter |
|---|---|---|
| 2 | Service Accounrt | Ensure you select the service account created in Create a service account |
| 5e | OAuth scopes | https://www.googleapis.com/auth/admin.reports.audit.readonly |
| https://www.googleapis.com/auth/admin.reports.usage.readonly | ||
| https://www.googleapis.com/auth/apps.alerts |
Complete the Google Workspace integration
You will need:
- JSON file you downloaded in Create credentials for the service account
- The admin account email used in Delegate domain-wide authority to the service account
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Google Workspace
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Service Account JSON (copy and paste from the json file you downloaded)
- Enter your Domain-Wide delegation account (the admin account email used for domain-wide delegation)
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.37 - Heimdal Security
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) From the Heimdal Security Dashboard
2) From the SamurAI Portal
Create a Heimdal Dashboard Account
Follow the steps outlined in the Heimdal Security documentation:
This account will only be used for API access from the Samurai platform therefore ensure you utilize appropriate credentials that you will manage. We recommend populating only the minimum fields required and not enabling reports and alerts whilst ensuring the account is activated under Miscellaneous Settings.
Create a Personal API Key
Follow the steps outlined in the Heimdal Security documentation:
Take note of the Customer ID and select Copy key as you will need this to Complete the Heimdal Security Integration
Complete the Heimdal Security Integration
You will need:
- CustomerID: (captured during the steps Create a Personal API Key)
- API Key: (captured during the steps Create a Personal API Key)
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Click Create
- Find and select Heimdal Security
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter the CustomerID
- Enter the API Key
- Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.38 - Infoblox DDI
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure an on-premise Infoblox DDI device to send logs to a Samurai Local Collector deployed in your network.
To complete this Integration you will need to:
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Infoblox DDI | Samurai Local Collector | TCP/514 | For log transmission |
Perform Grid Configuration
Perform the steps outlined in the vendor documentation to add an external syslog server:
Perform the below settings adjustments. In case a setting property is not referenced below, simply use the default value:
- Address: Insert the IP address of the Samurai Local Collector.
- Transport: Select TCP.
- Node ID: Select Host Name.
- Severity: Select Info.
- Logging Category: Select Send selected categories and then enable all logging categories.
Perform Data Management Configuration
Perform the steps outlined in the vendor documentation to configure DNS logging categories:
Perform the below settings adjustments. In case a setting property is not referenced below, simply use the default value:
- Logging Category: Select all the available categories.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.39 - Linux Authentication
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Linux hosts to send authentication logs to a Samurai Local Collector deployed on your network by configuring rsyslog.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Linux Host | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure log forwarding with rsyslog
Follow the below steps to configure rsyslog to forward authentication events.
Rsyslog prerequisites
Ensure the following statement is included in the main rsyslog configuration file, normally located at /etc/rsyslog.conf:
$IncludeConfig /etc/rsyslog.d/*.conf
If no IncludeConfig statement exist for the /etc/rsyslog.d/ directory, append it to the end of rsyslog.conf.
Create /etc/rsyslog.d/ntt_auth.conf
Create /etc/rsyslog.d/ntt_auth.conf and insert the below configuration block, enter the Local Collector IP in the Target field.
template(
name = "linux-auth"
type = "string"
string = "<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% linux_auth %STRUCTURED-DATA% %msg%"
)
if ($syslogfacility-text == "auth" or $syslogfacility-text == "authpriv") then {
action(
queue.type="LinkedList"
queue.size="10000"
type="omfwd"
template="linux-auth"
Target="<Local Collector IP>"
Port="514" Protocol="tcp")
}
Validate and restart service
Confirm that rsyslog can parse the configuration without any errors by running:
rsyslogd -N1
Then restart the rsyslog service:
sudo systemctl restart rsyslog
The authentication messages will now be forwarded to the Samurai Local Collector.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.40 - Microsoft Azure Activity Logs
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Microsoft Azure to send Activity Logs to a Storage account for ingestion to Samurai via a cloud collector.
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Azure Activity logs
Follow the vendor documentation guide to enable Microsoft Azure Activity logs.
When following the vendor documentation, please perform the following adjustments:
Select the following log categories
- Administrative
- Policy
Ensure when configuring the Storage Account setting that it’s referencing the storage account that was setup during the creation of the cloud collector.
Ensure the retention period aligns with your storage policies however we recommend at minimum 7 days.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.41 - Microsoft Azure Application Gateway
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes all steps required to configure Microsoft Azure Application Gateway to send logs to a Storage account for ingestion to Samurai via a cloud collector.
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Configure logging for Application Gateway
Follow the vendor documentation guide to enable Azure Application Gateway logs through the Azure Portal:
When following the vendor documentation, please perform the following adjustments:
Select the following log categories
- ApplicationGatewayAccessLogs
- ApplicationGatewayFirewallLogs
Ensure when configuring the Storage Account setting that it’s referencing the storage account that was setup during the creation of the cloud collector.
Ensure the retention period aligns with your storage policies however we recommend at minimum 7 days.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.42 - Microsoft Azure Firewall
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure a Microsoft Azure Firewall to send logs to a Storage account for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Azure Firewall logs
Follow the vendor documentation guide to enable Microsoft Azure Firewall logs.
When following the vendor documentation, please perform the following adjustments:
Select the following log categories
- Network Rule
- Application Rule
- Nat Rule
- Threat Intelligence
- IDPS Signature
- DNS query
Ensure when configuring the Storage Account setting that it’s referencing the storage account that was setup during the creation of the cloud collector.
Ensure the retention period aligns with your storage policies however we recommend at minimum 7 days.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.43 - Microsoft Azure Key Vault
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Microsoft Azure to send Azure Key Vault logs to a Storage account for ingestion to Samurai via a cloud collector.
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Azure Key Vault logs
Follow the vendor documentation guide to enable Azure Key Vault logging:
When following the documentation, please perform the following adjustments:
Select the following log categories
- Audit
- allLogs
Ensure when configuring the Destination Details to select Archive to storage account. When selecting the Storage Account ensure it references the storage account that was setup during the creation of the cloud collector.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.44 - Microsoft Defender Advanced Hunting
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Microsoft Defender to send Advanced Hunting Logs to a Storage account for ingestion to Samurai via a cloud collector.
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Defender Advanced Hunting Logs
Follow the vendor documentation guide to enable Advanced Hunting Logs data streaming to blob storage.
Stream Microsoft Defender XDR events to your storage account
Ensure when configuring the Storage Account setting that it’s referencing the resource ID for the storage account that was setup during the creation of the cloud collector.
Recommended event types to stream for endpoint related data are
- DeviceEvents
- DeviceFileEvents
- DeviceImageLoadEvents
- DeviceLogonEvents
- DeviceNetworkEvents
- DeviceProcessEvents
- DeviceRegistryEvents
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.45 - Microsoft DHCP Server
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Use this document to install and configure the Filebeat agent to send Microsoft DHCP Server logs to Samurai using the Samurai Local Collector deployed in your network.
To complete this Integration you will need to:
- Ensure correct network connectivity
- Download & Install Filebeat
- Configure & Enable DHCP Server Audit Logging
- Configure & Start Filebeat
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Microsoft DHCP Server Host | Samurai Local Collector | TCP/5044 | For log transmission |
Download & Install Filebeat
Perform the steps outlined in Step 1: Install Filebeat as per the vendor documentation.
Configure & Enable DHCP Server Audit Logging
Configure via Powershell
To view the DHCP Audit logging config, run the command Get-DhcpServerAuditLog.
PS C:\> Get-DhcpServerAuditLogPath : C:\Windows\system32\dhcpEnable : TrueMaxMBFileSize : 70DiskCheckInterval : 50MinMBDiskSpace : 20Verify that the flag Enabled is set to True.
In case logging is not enabled, run the commend Set-DhcpServerAuditLog. Example command with arguments is presented below.
PS C:\> Set-DhcpServerAuditLog -Enable $True -Path C:\dhcpThe DHCP server needs to be restarted after logging has been enabled, run the following command to restart the service.
PS C:\> Restart-Service DHCPServer
Note down the file path that has been configured, this will be used later in the section Configure & Start Filebeat.
Configure & Start Filebeat
- Access the Filebeat installation folder and open and edit the file filebeat.yml.
- Modify the below template by replacing the section IP_OF_LOCAL_COLLECTOR with the IP address of the Samurai Local Collector.
- Modify the paths section of the template to use the path that was configured for the DHCP Server Audit log file location from Configure & Enable DHCP Server Audit Logging.
# ============================== Filebeat inputs ===============================
filebeat.inputs:
- type: filestream
id: win_dhcp
enabled: true
paths:
- 'C:\Windows\System32\dhcp\Dhcp*'
include_lines: ['^\d+,(\d+\/){2}\d+,.*$']
tags: [win_dhcp_server]
#------------------------------ Logstash Output -------------------------------
output.logstash:
hosts: ["IP_OF_LOCAL_COLLECTOR:5044"]
- Replace the default configuration of filebeat.yml with the modified template and save the file.
- Perform the steps outlined in Step 5: Start Filebeat as per the vendor documentation to start the service.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.46 - Microsoft DNS Server
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Use this document to install and configure the Filebeat agent to send Microsoft DNS Server logs to Samurai using the Samurai Local Collector deployed in your network.
To complete this Integration you will need to:
- Ensure correct network connectivity
- Download & Install Filebeat
- Configure & Enable Microsoft DNS Server Debug Logging
- Configure & Start Filebeat
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Microsoft DNS Server Host | Samurai Local Collector | TCP/5044 | For log transmission |
Download & Install Filebeat
Perform the steps outlined in Step 1: Install Filebeat as per the vendor documentation.
Configure & Enable Microsoft DNS Server Debug Logging
Follow the steps outlined in To select and enable debug logging options on the DNS server as per the vendor documentation.
Configure Packet direction & Packet Contents*.*
- Keep default configuration or follow the minimum requirement below.
- Minimum requirement is to enable logging for Outgoing Response.

Figure 1 – Example of default configuration once “Log packets for debugging” has been enabled.
Configure an appropriate log location and name of the log file as well as a suitable Maximum Size (bytes) according to your system needs.
Note down the file path that has been configured, this will be used later in the section Configure & Start Filebeat.
Configure & Start Filebeat
- Access the Filebeat installation folder and open and edit the file filebeat.yml.
- Modify the below template by replacing the section IP_OF_LOCAL_COLLECTOR with the IP address of the Samurai Local Collector.
- Modify the paths section of the template to use the path that was configured for the DNS Server debug log file location from Configure & Enable Microsoft DNS Server Debug Logging.
# ============================== Filebeat inputs ===============================
filebeat.inputs:
- type: filestream
id: win_dns_server
enabled: true
paths:
- 'C:\dns_logs\*'
include_lines: ['^\d{1,4}.\d{1,2}.\d{1,4}\s.*?$']
tags: [win_dns_server]
# ------------------------------ Logstash Output -------------------------------
output.logstash:
hosts: ["IP_OF_LOCAL_COLLECTOR:5044"]
- Replace the default configuration of filebeat.yml with the modified template and save the file.
- Perform the steps outlined in Step 5: Start Filebeat as per the vendor documentation to start the service.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.47 - Microsoft Entra ID
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure a Microsoft Entra ID to send logs to a Storage account for ingestion to Samurai via a cloud collector.
Prerequisites
Ensure that a cloud collector has been deployed via the SamurAI Portal.
Take note of the name of the storage account created and which subscription it resides in. This will be used later when setting up the telemetry sources.
If you are planning to reuse an already deployed cloud collector, the information about the created storage account and subscription can be found via:
- Navigate to the SamurAI Portal.
- Click Telemetry and select Collectors from the main menu
- Click on the name of the desired collector.
- Note down information about the:
- Subscription
- Storage account name
Alternatively, you can utilize the integration setup wizard via the SamurAI Portal for the desired telemetry source listed on Product Integration Guide page which shall provide you the same information required to setup your telemetry source.
Enabling Entra ID activity logs
Follow the vendor documentation guide to archive Microsoft Entra logs to an Azure storage account:
When following the vendor documentation, please perform the following adjustments:
Select the following log categories
- AuditLogs
- SignInLogs
- NonInteractiveUserSignInLogs
- ServicePrincipalSignInLogs
- ManagedIdentitiySignInLogs
- ProvisioningLogs
- ADFSSignInLogs
- UserRiskEvents
- ServicePrincipalRiskEvents
- MicrosoftGraphActivityLogs
- MicrosoftServicePrincipalSignInLogs
- AzureADGraphActivityLogs
Please note NonInteractiveUserSignInLogs may cause high log volume
Ensure when configuring the Storage Account setting that it’s referencing the storage account that was setup during the creation of the cloud collector.
Ensure the retention period aligns with your storage policies however we recommend at minimum 7 days.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.48 - Microsoft Graph (Security)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Supported Microsoft Security products
The Microsoft Graph Security API supports collection of alerts for multiple Microsoft Security products. An updated list can be found in the Microsoft documentation. Support for the following products has been validated by Samurai MDR:
- Microsoft Entra ID Protection
- Microsoft 365 Defender
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Microsoft Defender for Cloud
Prerequisites
The user must have Global administrative access to the Microsoft 365 Defender and Microsoft Azure Portal.
Recommended Advanced Settings for Defender for Endpoint
If you are a customer with the Incident Response (IR) Retainer, in order to ensure an optimal service delivery and a quick turnaround from activation to remediation by the NTT Incident Response team the below features are recommended to be enabled in Defender for Endpoint:
- Live response
- Live response for servers
- Live response unsigned script execution
Follow the Microsoft documentation - Configure advanced features in Defender for Endpoint to enable the features.
To complete this Integration you will need to perform actions in both the Azure Portal and SamurAI Portal:
1. Azure Portal
2. From the SamurAI Portal
- Complete the Microsoft Graph (Security) Integration
Application Registration
- Follow the steps outlined within section entitled Register an application in the Microsoft Graph API documentation using the following parameters.
Field Name Parameter Supported account type Accounts in this organizational directory only Redirect URL Leave blank
- Follow the steps outlined within section entitled Add a client secret in the Microsoft Graph API documentation.
- Follow the steps outlined within section entitled Configure permissions for Microsoft Graph in the Microsoft Graph API documentation. Select the following permissions.
SecurityAlert.Read.All
Enable the Samurai MDR SOC access to Microsoft 365 Defender
The steps outlined below are required for the Samurai SOC to perform remote isolation and further analysis through the Microsoft 365 Defender portal. You may also wish to refer to the Microsoft documentation - Granting managed security service provider (MSSP) access
Prerequisites
Ensure role-based access control (RBAC) is enabled in your Microsoft Defender Security Center.
To enable RBAC in Microsoft Defender Security Center, navigate to Settings > Permissions > Roles and Turn on roles from a user account with Global Administrator or Security Administrator rights.
This feature also requires an Entra ID P2 plan for the Privileged Identity Management feature.
Create an Entra ID Group and assign role
To create an Entra ID group for NTT, perform the following steps:
Log in to Entra ID admin center
Navigate to Groups > All groups > New group
Select Security from the Group type list
Ensure that Microsoft Entra roles can be assigned to the group is set to Yes
After creating the group, follow the steps in Assign Microsoft Entra roles to groups to assign the Security Reader role to the newly created group.
Add NTT as Connected Organization
Perform the following steps to add NTT as a connected organization:
- Navigate to Identity Governance
- Click Connected organizations
- Click Add connected organization
- On the Basics tab*,* specify a Name and Description
- On the Directory + domain tab, perform the following steps:
- Click Add directory + domain
- In the Select directories + domains field, search for security.ntt

Create a Resource Catalog
In the Entra ID portal under Identity Governance perform the following steps:
- Navigate to the Catalogs tab
- Click New catalog
- Specify a Name and Descriptions, keep other values default
- Click Create
Create an Access Package
An access package enables you to do a one-time set up of resources and policies that automatically administers access for the life of the access package.
To create a new access package, perform the following steps:
Navigate to Identity Governance
Click Access packages
Click New access package
Specify a Name and Description*,* select the Catalog created in the previous step
In the Resource roles tab, add the group created in previously and set Role to Member
In the Requests tab, ensure the following options are set (leave other settings as default):
Set Users who can request access to For users not in your directory
Under Select connected organizations, select NTT
Set Require approval to Yes
Under First Approver, add at least one fallback approver
Set Enable new requests to Yes
In the Lifecycle tab, set Access Reviews to No
After creating the access package provide the My Access portal link to NTT.
Define your Sponsors
Sponsors are the people responsible for approving requests made by NTT staff. You may define internal and/or external sponsors.
Internal sponsors are select individuals from within your organization who can approve requests from NTT. External sponsors are select individuals from within NTT who can approve these on your behalf.
NTT recommends selecting external sponsors and obtaining a list of names during the MDR Onboarding. These names include managers and team leads who support the service.
Setting up sponsors is a time-consuming process as it requires approving access requests from NTT staff. Therefore, NTT recommends you define external sponsors to enable NTT to manage this process.
Initial NTT users will need to be approved by the selected Fallback approvers, after which they can be added as external sponsors.
To add external sponsors, select the Connected Organization and then Sponsors.

Complete the Microsoft Graph (Security) Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Microsoft Graph (Security)
- Click Next (we leverage a Samurai Cloud Collector)
- Enter Tenant ID, Application ID and Client Secret as created in Application Registration
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.49 - Microsoft IIS
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Use this document to install and configure the Filebeat agent to send Microsoft IIS logs to Samurai using the Samurai Local Collector deployed in your network.
To complete this Integration you will need to:
- Ensure correct network connectivity
- Download & Install Filebeat
- Configure & Enable Microsoft IIS Logging
- Configure & Start Filebeat
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Microsoft IIS Host | Samurai Local Collector | TCP/5044 | For log transmission |
Download & Install Filebeat
Perform the steps outlined in Step 1: Install Filebeat as per the vendor documentation.
Configure & Enable Microsoft IIS Logging
Follow the steps outlined below as per the vendor documentation for either per-site or per-server configuration that is best suited to your setup.
During step 4 in the vendor documentation, select W3C logging format.

Under “Select Fields…”, select all available fields:

Configure a suitable log file path for the logging files according to your system requirements.
During step 6 in the vendor documentation, configure Log File Rolloversettings and **Maximum file size (in bytes)**according to your system needs and requirements.
Note down the file path that has been configured, this will be used later in the section Configure & Start Filebeat.
Configure & Start Filebeat
- Access the Filebeat installation folder and open and edit the file filebeat.yml.
- Modify the below template by replacing the section IP_OF_LOCAL_COLLECTOR with the IP address of the Samurai Local Collector.
- Modify the paths section of the template to use the path that was configured for the ISS Web Server log file location from Configure & Enable Microsoft IIS Logging.
# ============================== Filebeat inputs ===============================
filebeat.inputs:
- type: filestream
id: microsoft_iis
enabled: true
paths:
- 'c:\inetpub\logs\LogFiles\*\*.log'
include_lines: ['^[^#].*?$']
tags: [microsoft_iis]
# ------------------------------ Logstash Output -------------------------------
output.logstash:
hosts: ["IP_OF_LOCAL_COLLECTOR:5044"]
- Replace the default configuration of filebeat.yml with the modified template and save the file.
- Perform the steps outlined in Step 5: Start Filebeat as per the vendor documentation to start the service.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.50 - Microsoft Office 365
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Within Microsoft 365:
- Ensure Microsoft Office 365 auditing is enabled
- Ensure Azure Exchange mailbox auditing is enabled (if monitoring Azure Exchange)
- Register application with Azure Active Directory
- Generate application secret key
- Specify permissions for the app
2) From the SamurAI Portal:
Ensure Microsoft 365 auditing is enabled
Follow the steps outlined within the Office365 documentation to ensure audit logging is enabled:
Verify that Azure Exchange Mailbox Auditing is Enabled
Azure Exchange Mailbox Auditing is enabled by default however verify this by following the Office365 documentation:
Register application with Azure Active Directory
Follow the steps outlined within the Office365 documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name of app | Whatever you want, however we suggest NTT_app |
| Supported Account Types | Select Accounts in this organizational directory only (single tenant) |
| Redirect URI | Not required |
Table 1: App registration
Generate Application Secret Key
Follow the steps within the Office365 documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Description | Whatever you want, however we suggest NTT_app |
| Expires | The expiration period will depend on your company’s security policies. It will be your responsibility to create a new key should it expire and update the Integration when you Complete the Office 365 Integration |
| Redirect URI | Not required |
Table 2: Secret key
Specify permissions for the app
Follow the steps within the Office365 documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Request API permissions | Application permissions |
| Permissions | ActivityFeed.Read ActivityFeed.ReadDlp ServiceHealth.Read |
Table 3: App permissions
Complete the Microsoft Office 365 Integration
You will need:
- Application (client) ID and Directory (tenant) ID created during Register application with Azure Active Directory
- Client Secret created during Generate Application Secret Key
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Microsoft Office 365
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Application (client) ID
- Enter your Directory (tenant) ID
- Enter your Secret Key (client Secret)
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.51 - Microsoft Windows Event Log
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Use this document to install and configure the Winlogbeat agent to send Microsoft Windows Event Logs to Samurai using the Samurai Local Collector deployed in your network.
To complete this Integration you will need to:
Ensure correct network connectivity
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Windows Host | Samurai Local Collector | TCP/5044 | For log transmission |
Download & Install Winlogbeat
Perform the steps outlined in Step 1: Install Winlogbeat as per the vendor documentation.
Configure & Start Winlogbeat
- Access the Winlogbeat installation folder and open and edit the file winlogbeat.yml.
- Modify the below template by replacing the section IP_OF_LOCAL_COLLECTOR with the IP address of the Samurai Local Collector.
# ======================== Winlogbeat specific options =========================
winlogbeat.event_logs:
- name: Application
- name: System
- name: Security
- name: Microsoft-Windows-Sysmon/Operational
# ------------------------------ Logstash Output -------------------------------
output.logstash:
hosts: ["IP_OF_LOCAL_COLLECTOR:5044"]
- Replace the default configuration of winlogbeat.yml with the modified template and save the file.
- Perform the steps outlined in Step 5: Start Winlogbeat as per the vendor documentation to start the service.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.52 - Nozomi Networks Guardian
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Guardian | Samurai Local Collector | TCP/514 (Syslog) | For log transmission |
| Samurai Local Collector | Guardian | TCP/443 (Default HTTPS) | Alerts and related evidence |
Configure syslog to the Samurai Local Collector
Ensure that the Syslog Capture Feature is enabled:
Follow the steps outlined within the Nozomi documentation to send logs to your Samurai Local Collector. We reference the CMC documentation:
Use the following parameters when completing the steps:
- Configuration: Syslog Forwarder
- To URI: TCP://LOCALCOLLECTOR:514
Extended Telemetry Collection Prerequisites
Perform the following steps to allow Extended Telemetry Collection.
Configure User Group
Follow the steps outlined within the Nozomi Networks documentation:
Use the following parameters when completing the steps:
- Allowed sections: Enable Queries and Exports
Configure User
Follow the steps outlined within the Nozomi Networks documentation:
Use the following parameters when completing the steps:
- Source: Local
- Group: Select the group created under Configure User Group
- Must update password: Uncheck
Complete the Nozomi Guardian Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Click Create
- Find and select Nozomi Guardian
- Select the relevant Local Collector and click Next
- You will be presented with the Local Collector IP Address on the left of the screen
- To configure Extended Telemetry Collection ensure it is enabled via the toggle
- Enter the following information
- Name for the Integration - The name will appear in the SamurAI Portal for you to easily reference
- Description - Optional but if completed will appear in the SamurAI Portal for you to easily reference
- Username - Enter the username created in Configure User
- Password - Enter the password created in Configure User
- Hostname / IP - Enter the Hostname or IP address of the Guardian
- Custom port - Optional if you have changed the port for access
- Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.53 - Okta Workforce Identity Cloud
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Pre-requisites
- An Okta account with administrative privileges
- Your Okta Instance
From the Okta admin console
Create an OAuth service app integration
Follow the Okta documentation to:
Generate a public/private key pair
Follow the Okta documentation to:
Use the following settings when completing:
- Client Authentication - Public / Private Key
- Public Key Configuration - Save Keys in Okta
- Select PEM to ensure the private keys appear in PEM format
Grant allowed scopes
Follow the Okta documentation to:
Grant the following scope:
- okta.logs.read
Assign read-only administrator
Follow the Okta documentation to:
Complete the Okta Workforce Identity Cloud Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Okta Workforce Identity Cloud
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your ClientID created under Create an OAuth 2.0 service app integration
- Enter your Instance this refers to your Okta domain
- Enter your PEM data by pasting your Private Key in PEM format created under Generate a public/private key pair
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.54 - Palo Alto Networks Cortex XDR Pro
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) From your Cortex XDR Gateway:
2) From the SamurAI Portal:
Configure an API Key to allow us to collect telemetry
Follow Steps 1-3 outlined within the Palo Alto Networks documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Security Level | Standard |
| Enable Expiration Date | not required (do not select) |
| Roles | Viewer |
Be sure to save a copy of the following information as it required to complete the integration:
- API key (as noted in the documentation you will not be able to view it again!)
- API KeyID
- FQDN (for the Base URL e.g https://api-{fqdn}
Complete the Palo Alto Cortex XDR Pro Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Palo Alto Networks Cortex XDR Pro
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Device Name
- Enter the URL, API KeyID and API Key created in Configure an API Key to allow us to collect telemetry
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.55 - Palo Alto Networks: Next-Generation Firewall
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Ensure Connectivity Requirements are in place
2) From your Palo Alto Networks Next Generation Firewall:
- Configure syslog to your Samurai Local Collector
- Create Log Forwarding Profiles
- Create URL Filtering Profile
- Create Filtering Profile Group
- Create Security Policy Rule
- Enable Packet Capture Profiles
- Enable API Access
- Obtain Wildfire API Key (if applicable)
4) From the SamurAI Portal:
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| PAN NGFW | Samurai Local Collector | UDP/514 (syslog) | For log transmission |
| Samurai Local Collector | PAN NGFW | TCP/443 (https) | Packet captures |
| Samurai Local Collector | *.wildfire.paloaltonetworks.com(WildFire Public Cloud) | TCP/443 (https) | For WildFire reports (if applicable) |
Configure syslog to your Samurai Local Collector
Follow the steps outlined within the Palo Alto Networks documentation to configure your firewall to send logs to your Samurai Local Collector:
If you do not have Panorama deployed:
If you have Panorama deployed please refer to Palo Alto Networks: Panorama (Be aware of steps based on your Panorama deployment mode)
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Server Profile Name | Whatever you want, however we suggest NTT_Syslog_Profile |
| Syslog Server | IP address of your Samurai Collector |
| Transport | UDP |
| Port | 514 (Default) |
| Format | BSD (Default) |
| Facility | keep as default |
| Custom Log Format | keep as default for every log type |
Create Log Forwarding Profiles
Follow the steps outlined within the Palo Alto Networks documentation:
You will need to configure Log forwarding profiles for each log type as per the table below:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_Log_Fwd_Profile |
| Name for each Log Type | Whatever you want, however we suggest NTT_<log type>_Fwd_Profile. Where <log type> denotes each log type available |
| Log Type | All (you need to include all log types eg. traffic, threat, wildfire etc) |
| Filter | All logs |
| Forward Method | Select the syslog Server Profile you configured in Configure syslog to Samurai Local Collector (we suggested *NTT_Syslog_Profile) |
Create URL Filtering Profile
Follow the steps outlined within the Palo Alto Networks documentation:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_URL_Profile |
| Site Access for Each Category | Alert. If your company policy requires Block for certain categories, set it that way. |
| User Credential Submission for Each Category | Alert. If your company policy requires Block for certain categories, set it that way. |
| Settings | Ensure Log container page only is not selected |
| HTTP Header Logging | Enable: User-Agent, Referer, X-Forwarded-For |
Create Filtering Profile Group
Follow the steps outlined within the Palo Alto Networks documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Security Profile Group name | Whatever you want, however we suggest NTT_Security_Profile |
| Filtering Profiles | All as applicable eg. Anti-virus, Anti-Spyware, Vulnerability Protection, and URL Filtering created in Create URL Filtering Profile and Enable Packet Capture Profiles |
Create Security Policy Rule
Follow the steps outlined within the Palo Alto Networks documentation:
Use the following parameters in the Actions tab when completing the steps:
| Field Name | Parameter |
|---|---|
| Profile Setting | Select the Group Profile you provided in Create Filtering Profile Group (we suggested NTT_Security_Profile) |
| Log at Session Start | Enabled |
| Log at Session End | Enabled |
| Log Forwarding | Select the Log Forwarding Profile you provided in Create Log Forwarding Profile (we suggested NTT_Log_Fwd_Profile) |
Enable Packet Capture Profiles
Follow the steps outlined within the Palo Alto Networks documentation:
You will need to enable Packet Capture for for each profile as tables below:
Anti Virus Profile
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_AV_Profile |
| Anti-Virus | Enable Packet-Capture |
Anti-Spyware Profile
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_Spyware_Profile |
| Severity Critical Severity High Severity Medium | Select extended-capture |
Vulnerability Protection Profile
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_IDS_Profile |
| Severity Critical Severity High Severity Medium | Select extended-capture |
Enable API Access
Follow the steps outlined within the Palo Alto Networks documentation:
Creating a new Admin Role Profile to be used specifically by the Samurai platform.
Under XML API ensure to disable all permissions except the following:
- Log
- Operation Requests
- Export
Once complete you now need to get the API key to be used in the SamurAI Portal. Follow the Palo Alto documentation:
When following the steps be sure to use the username and password you created in the previous step. Once successful make a note of the <Key> string as you will need this later when you Complete the Palo Alto Networks NG Firewall Integration
Obtain your Wildfire API Key
If you leverage Wildfire, follow the steps outlined in the Palo Alto documentation to obtain your Wildfire API key:
Complete the Palo Alto Networks Next-Generation Firewall Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Click Create
- Find and select Palo Alto Networks Next-Generation Firewall
- Select the relevant Local Collector and click Next
- You will be presented with the Local Collector IP Address on the left of the screen
- To configure Extended Data Collection ensure it is enabled via the toggle
- Enter the following information
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description - optional but if completed will appear in the SamurAI Portal for you to easily reference)
- API-Key - you captured in Enable API Access
- Wildfire API-Key (optional) - to enable Wildfire telemetry collection include the key you captured in Obtain your Wildfire API key
- Hostname/IP - hostname or IP address of Palo Alto device to collect alerts from
- Vsys (optional) - if you leverage virtual systems add the vsys names e.g vsys1, vsys2. If you do not add vsys the default vsys1 is used
- Threat severity ignore list (optional) - to optionally ignore specific severity threats, specify from the drop down list. By default we ignore informational and low severity threats to reduce noise.
- Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.56 - Palo Alto Networks: Panorama
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Ensure Connectivity Requirements are in place
2) From your Palo Alto Networks Panorama:
- Configure syslog to your Samurai Local Collector
- Enable API Access
- Obtain your Wildfire API key (if applicable)
4) From the SamurAI Portal:
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Panorama | Samurai Local Collector | UDP/514 (syslog) | For log transmission |
| Samurai Local Collector | Panorama | TCP/443 (https) | For Packet Captures |
Configure syslog to your Samurai Local Collector
Follow the steps outlined within the Palo Alto Networks documentation to configure your Panorama to send logs to your Samurai Local Collector:
Use the following parameters when completing the steps:
| Documentation Step | Field Name | Parameter |
|---|---|---|
| 4.2 | Server Profile Name | Whatever you want, however we suggest NTT_Syslog_Profile |
| 4.2 | Syslog Server | IP address of your Samurai Collector |
| 4.2 | Transport | UDP |
| 4.2 | Port | 514 (Default) |
| 4.2 | Format | BSD (Default) |
| 4.2 | Facility | keep as default |
| 4.4 | Custom Log Format | keep as default for every log type |
If you will not be using the Panorama Management interface you will need to configure an alternative ethernet interface to forward syslog by following the documentation from Step 5.
Enable API Access
Follow the steps outlined within the Palo Alto Networks documentation:
Creating a new Admin Role Profile to be used specifically by Samurai.
Under XML API ensure to disable all permissions except the following:
- Log
- Operation Requests
- Export
Once complete you now need to get the API key to be used in the SamurAI Portal. Follow the Palo Alto documentation:
When following the steps be sure to use the username and password you created in the previous step. Once successful make a note of the <Key> string as you will need this later when you Complete the Palo Alto Networks Panorama Integration
Obtain your Wildfire API key
If you leverage Wildfire, follow the steps outlined in the Palo Alto documentation to obtain your Wildfire API key:
Complete the Palo Alto Networks Panorama Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Palo Alto Networks Next-Generation Firewall Panorama
Select the relevant Local Collector and click Next
You will be presented with the Local Collector IP Address on the left of the screen
To configure Extended Telemetry Collection ensure it is enabled via the toggle
Enter the following information
- Name for the Integration - the name will appear in the application for you to easily reference
- Description - optional but if completed will appear in the application for you to easily reference)
- Manager name- this name is used as the source for alerts for this integration
- API-Key you captured in Enable API Access
- Wildfire API-key - to enable Wildfire telemetry collection include the key you captured in Obtain your Wildfire API key
- Hostname/IP - hostname or IP address of Palo Alto device to collect alerts from
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.57 - PowerDNS Recursor
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure PowerDNS Recursor logs to a Samurai Local Collector deployed on your network by configuring rsyslog.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| PowerDNS Host | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure PowerDNS
Ensure that Structured Logging is enabled and Quiet is disabled in the PowerDNS Recursor configuration file, normally located at /etc/powerdns/recursor.conf:
structured-logging=yes
quiet=no
Configure log forwarding with rsyslog
Follow the below steps to configure rsyslog to forward authentication events.
Rsyslog prerequisites
Ensure the following statement is included in the main rsyslog configuration file, normally located at /etc/rsyslog.conf:
$IncludeConfig /etc/rsyslog.d/*.conf
If no IncludeConfig statement exist for the /etc/rsyslog.d/ directory, append it to the end of rsyslog.conf.
Create /etc/rsyslog.d/ntt_powerdns.conf
Create /etc/rsyslog.d/ntt_powerdns.conf and insert the below configuration block, enter the Local Collector IP in the Target field.
template(
name = "powerdns-recursor"
type = "string"
string = "<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% powerdns_recursor %STRUCTURED-DATA% %msg%"
)
if ($programname == "pdns-recursor") then {
action(
queue.type="LinkedList"
queue.size="10000"
type="omfwd"
template="powerdns-recursor"
Target="<Local Collector IP>"
Port="514"
Protocol="tcp"
)
}
Validate and restart service
Confirm that rsyslog can parse the configuration without any errors by running:
rsyslogd -N1
Then restart the rsyslog service:
sudo systemctl restart rsyslog
The log messages will now be forwarded to the Samurai Local Collector.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.58 - Proofpoint Targeted Attack Protection (TAP)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
The guide outlined the steps required to configure Proofpoint Targeted Attack Protection (TAP) to facilitate log ingestion into the Samurai platform.
To complete this Integration you will need to:
2) From your TAP dashboard:
3) From the SamurAI Portal:
Generate TAP Service Credentials
- Follows the steps outlined within section entitled Generate TAP Service Credentials in the Proofpoint TAP documentation.
Complete the Proofpoint Targeted Attack Protection (TAP)
Login to your Samurai tenant
Click Telemetry and select Integrations from the main menu
Select Create
Locate and click Proofpoint Targeted Attack Protection
Click Next (we leverage a Samurai Cloud Collector)
Enter a Name of Integration
Enter a Description (Optional)
8. Enter a Devicename
Enter your Service Principle
Enter your Secret
Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.59 - Samba AD
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Samba AD to send authentication logs to a Samurai Local Collector deployed on your network by configuring rsyslog.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Samba AD host | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure Samba AD logging
Ensure that Authentication Audit Logging in JSON format is configured in the smb.conf file.
[global]
log level = 1 auth_json_audit:3
Configure log forwarding with rsyslog
Follow the below steps to configure rsyslog to forward authentication events.
Rsyslog prerequisites
Ensure the following statement is included in the main rsyslog configuration file, normally located at /etc/rsyslog.conf:
$IncludeConfig /etc/rsyslog.d/*.conf
If no IncludeConfig statement exist for the /etc/rsyslog.d/ directory, append it to the end of rsyslog.conf.
Create /etc/rsyslog.d/ntt_smb_auth.conf
Create /etc/rsyslog.d/ntt_smb_auth.conf and insert the below configuration block, enter the Local Collector IP in the Target field.
template(
name = "samba-auth"
type = "string"
string = "<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% samba_auth %STRUCTURED-DATA% %msg%"
)
if ($programname == "samba_auth") then {
action(
queue.type="LinkedList"
queue.size="10000"
type="omfwd"
template="samba-auth"
Target="<Local Collector IP>"
Port="514"
Protocol="tcp")
}
Validate and restart service
Confirm that rsyslog can parse the configuration without any errors by running:
rsyslogd -N1
Then restart the rsyslog service:
sudo systemctl restart rsyslog
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.60 - Sophos Central
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Supported Products
Sophos Central can integrate with many Sophos and Third-Party products. The following products are supported through the Sophos Central integration:
- Sophos Intercept X
To complete this Integration you will need to:
1) Within Sophos Central Admin
2) From the SamurAI Portal:
Create an API Token
Follow steps outlined within the Sophos documentation:
Be sure to save a copy of the following information as it required to complete the integration:
- Client ID
- Client Secret (as noted in the documentation you will not be able to view it again!)
Complete the Sophos Central Integration
You will need:
- Client ID: (from Create an API Token)
- Client Secret: (from Create an API Token)
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Sophos Central
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Devicename
- Enter your Client ID
- Enter your Client Secret
- Enter your Tenant ID (optional) - if not included we will identify from your credentials
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.61 - Squid Cache
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Squid Cache hosts to send logs to a Samurai Local Collector deployed on your network by configuring rsyslog.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Squid Cache | Samurai Local Collector | TCP/514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Configure Squid
Ensure that access_log is configured to log in format combined to syslog in the squid.conf file.
access_log syslog:local0.info combined
Configure log forwarding with rsyslog
Follow the below steps to configure rsyslog to forward authentication events.
Rsyslog prerequisites
Ensure the following statement is included in the main rsyslog configuration file, normally located at /etc/rsyslog.conf:
$IncludeConfig /etc/rsyslog.d/*.conf
If no IncludeConfig statement exist for the /etc/rsyslog.d/ directory, append it to the end of rsyslog.conf.
Create /etc/rsyslog.d/ntt_squid.conf
Create /etc/rsyslog.d/ntt_squid.conf and insert the below configuration block, enter the Local Collector IP in the Target field.
template(
name = "squid-access"
type = "string"
string = "<%PRI%>1 %TIMESTAMP:::date-rfc3339% %HOSTNAME% %APP-NAME% %PROCID% squid_access %STRUCTURED-DATA% %msg%"
)
if ($programname == "squid") then {
action(
queue.type="LinkedList"
queue.size="10000"
type="omfwd"
template="squid-access"
Target="<Local Collector IP>"
Port="514"
Protocol="tcp")
}
Validate and restart service
Confirm that rsyslog can parse the configuration without any errors by running:
rsyslogd -N1
Then restart the rsyslog service:
sudo systemctl restart rsyslog
The authentication messages will now be forwarded to the Samurai Local Collector.
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.62 - Trellix Endpoint Security (ENS)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Trellix Endpoint Security (ENS) to send logs through a Trellix ePolicy Orchestrator (On-prem) to a Samurai Local Collector deployed in your network.
Connectivity Requirements
You must ensure the following connectivity requirements are available:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Trellix ePolicy Orchestrator | Samurai Local Collector | TCP/6514 (syslog) | For log transmission |
Table 1: Connectivity requirements
Syslog Configuration
Follow the Trellix Register syslog servers documentation using the following parameters:
| Parameter | Value |
|---|---|
| Server name | IP of the Samurai Local Collector |
| TCP port number | 6514 |
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.63 - Trellix Endpoint Security (HX)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Ensure Connectivity Requirements are in place
2) From the Trellix HX Console:
- Create Users
- Acquisition Setting
- Enable Auto Triage
- Data Acquisition Script Setting
- Configuration for Log Collection
- Polling Configuration
3) From the SamurAI Portal:
Connectivity Requirements
| Source | Destination | Port | Description |
|---|---|---|---|
| SamurAI Local Collector | Trellix Endpoint Security Server | TCP/443 | API access |
| Trellix Endpoint Security Server | SamurAI Local Collector | UDP/514 or TCP/514 | Log forwarding |
Create Users
Perform the following steps:
- Login to the Endpoint Security Web UI with admin access
- Navigate to Admin > Appliance Settings
- Click User Accounts and specify the following information to create a new user account for NTT:
| Account | Parameter |
|---|---|
| User Name | you choose however we recommend: api_analyst_ntt |
| Role | api_admin |
| Password | [Set secure password] |
Verify the logins using the above accounts as you will need this information to Complete the Trellix Endpoint Security (HX) Integration
Acquisition Setting
Configure the Acquisition setting to enable triage file retrieval:
- Login to the Endpoint Security Web UI with admin access
- Navigate to Admin > Policies
- In the Edit Policy page under Configurations, click Audits - version number
- Turn on Enable the File and Data Audits on the host.
- Click Save.
Enable Auto Triage
Configure the auto triage setting to make triage files available in the HX instance:
- Login to the Endpoint Security Web UI with admin access
- Navigate to Admin > Triage Settings
- On the Automatic Triages settings page, toggle the Triage Settings switch to ON
- Click Save.
Data Acquisition Script Setting
Configure the Data Acquisition setting to enable event log retrieval:
- Login to the Endpoint Security Web UI with admin access
- Navigate to Admin > Data Acquisition Scripts
- Click Standard Investigative Details.
- On the Script Description page, click ACTIONS and select Edit
- Click Event Logs and then enable Security logs in the Windows event logs section.
- Click Save.
Configuration for Log Collection
Configure a syslog server (the SamurAI Local Collector) using the CLI.
# show logging
Local logging level: notice
Override for class cef: none
Remote syslog default level: notice.
- Go to CLI Configuration mode and enter the following commands to configure syslog:
hostname > enable
hostname # configure terminal
hostname (config) # logging [IP Address of your Local Collector] trap none
hostname (config) # logging [IP Address of your Local Collector] trap overrride class cef
priority info
hostname # logging [IP Address of your Local Collector] protocol tcp
hostname (config) # (config) # write memory
- Configure RFC-3339 Time Format
hostname > enable
hostname # configure terminal
hostname (config) # logging fields timestamp format rfc-3339
hostname (config) # (config) # write memory
Polling Configuration
This configuration is not mandatory but recommended to configure certain parameters in order to fully align with our service.
Perform the following steps:
- Login to the Endpoint Security Web UI with admin access
- Navigate to Admin > Policies
- From the Policies page, click Agent Default policy to edit the policy
- From the Edit Policy page, select Polling and overwrite the parameters highlighted in the table below
| Parameters | Time |
|---|---|
| ① Polling agents | 1 minute |
| ② Fastpoll agents | 30 seconds |
| ③ Request sysinfo | 10 minutes |
| ④ Poll for agent config | 15 minutes |
- Click Save to apply the configuration
Complete the Trellix Endpoint Security (HX) Integration
Login to the SamurAI Portal
Click Telemetry and select Integrations from the main menu
Click Create
Find and select Trellix Endpoint Security (HX)
Select the intended SamurAI Local Collector
You will be presented with the Local Collector IP Address on the left of the screen
To configure Extended Telemetry Collection ensure it is enabled via the toggle
Enter the following information:
- Name for the Integration - the name will appear in the SamurAI Portal for you to easily reference
- Description (optional) - if completed will appear in the SamurAI Portal for you to easily reference)
- Devicename - an arbitrary name to identify FireEye HX
- Username - enter a username (created under Create Users)
- Password - specify password to use (created under Create Users)
- Hostname / IP - IP address or hostname of the manager
- Custom Port (optional)- if you have changed the default port enter the port number, if not, we default to 443
Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.64 - Trend Micro Vision One
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) From the Trend Micro Vision One console
2) From the SamurAI Portal
Create an API Key
Follow the steps outlined in the Trend Micro documentation:
When completing the steps be sure to:
- Ensure the API key has Role: Analyst
- You generate and copy the Authentication Token for use when you Complete the Trend Micro Vision One Integration
Determine your Trend Vision One region
Review the Trend Micro documentation to determine your region:
Complete the Trend Micro Vision One Integration
You will need:
- Authentication Token: (you obtained from Create an API Key)
- Regional Domain: (this corresponds to the region from Determine your Trend Vision One region)
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Click Create
- Click Next (we leverage a Samurai Cloud Collector)
- Find and select Trend Micro Vision One
- Enter the Authentication Token within the Access token field
- Select the Regional Domain
- Click on Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.65 - Veeam Backup & Replication
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure Veeam Backup & Replication to send syslog events to a Samurai Local Collector deployed in your network.
Connectivity Requirements
| Source | Destination | Ports | Description |
|---|---|---|---|
| Veeam Backup & Replication | Samurai Local Collector | TCP/514 | For log transmission |
Veeam Configuration
Follow the vendor documentation to add a new syslog server:
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.66 - VMware Carbon Black Cloud Enterprise EDR
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
To complete this Integration you will need to:
1) Within the VMware Carbon Black Cloud web interface
2) From the SamurAI Portal:
Determine Environment
The URL for API access appears in the address bar in a browser as follows:
https://defense-<Cloud Instance ID>.conferdeploy.net
Determine Org Key for API Access
To determine your Org Key for API Access:
- Login to your Carbon Black Cloud instance
- Select Settings > API Access
- The ORG KEY is shown on the screen.
API Access
Use these steps to configure a custom API access level:
- Log in to your Carbon Black Cloud Instance with an account that has the Super Admin role.
- Click Settings > API Access
- Go to the Access Level-tab
- Click Add Access Level
- In the Name field, enter Samurai-Access
- Enter a description
- Select the following permissions
- org.alerts Read
- org.watchlists Read
- device Read
- org.search.events Create, Read
- Click Save
Use these steps to enable API configuration to allow Samurai to gather telemetry:
Click Settings > API Access
Click +Add API Key
Add a new API key with the following information:
- In the Name field, enter Samurai-MDR
- From the Access Level type list, select Custom
- From Custom Access Level list, select Samurai-Access
- Click Save
The API credentials are displayed
Use the copy button to copy the Samurai-MDR API ID and API Secret Key. Paste the information to a file clearly indicating name, API ID, and API secret key.
Complete the VMware Carbon Black Cloud Enterprise EDR Integration
You will need:
- Environment: (the URL from Determine Environment e.g https://defense-<ENV>.conferdeploy.net)
- Organization Key: (from Determine Org Key for API Access)
- API ID: (from API Access)
- API Secret: (from API Access)
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Carbon Black Enterprise EDR
- Click Next (we leverage a Samurai Cloud Collector)
- Enter a Name of Integration
- Enter a Description (Optional)
- Enter your Environment
- Enter your Organization Key
- Enter your API ID
- Enter your API Secret
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.67 - WatchGuard Firebox
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
This guide describes the steps required to configure WatchGuard Firebox to send logs to a Samurai Local Collector deployed on your network. The Firebox requires access to the Local Collector via syslog on port 514/UDP.
1) From your WatchGuard Firebox:
Adding Syslog Servers
Follow the steps outlined in the following section of the WatchGuard documentation.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| IP Address | IP address of your Samurai MDR Local Collector |
| Port | 514 |
| Log Format | IBM LEEF |
| Description | Whatever you want. |
| The serial number of the device | Enabled |
| The syslog header | Enabled |
| Syslog facility | Required log message types: Traffic, Alarm Optional log message types: Event, Diagnostic, Performance |
Table 1: Adding Syslog Servers
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.68 - Zscaler Internet Access (ZIA)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Connectivity Requirements
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Zscaler NSS Server | Samurai Local Collector | TCP/514 | For log transmission |
Adding NSS Server
Follow the steps outlined in the ZIA documentation. If you use an existing one, skip this section.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTT Monitoring |
| Type | NSS for Web / NSS for Firewall |
Adding NSS Feeds for Web Logs
Follow the steps outlined in the ZIA documentation.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Feed Name | Whatever you want, however we suggest: NTT-Web |
| NSS Type | Select your NSS Server created in Adding NSS Server or the existing server |
| SIEM Destination Type | IP Address |
| SIEM IP Address | IP address of your Samurai Local Collector |
| Log Type | Web Log |
| Feed Output Type | Custom |
| Feed Output Format | \{ "sourcetype" : "zscalernss-web", "event" : \{"datetime":"%d{yy}-%02d{mth}-%02d{dd} %02d{hh}:%02d{mm}:%02d{ss}","reason":"%s{reason}","event_id":"%d{recordid}","protocol":"%s{proto}","action":"%s{action}","transactionsize":"%d{totalsize}","responsesize":"%d{respsize}","requestsize":"%d{reqsize}","urlcategory":"%s{urlcat}","serverip":"%s{sip}","clienttranstime":"%d{ctime}","requestmethod":"%s{reqmethod}","refererURL":"%s{ereferer}","useragent":"%s{eua}","product":"NSS","location":"%s{elocation}","ClientIP":"%s{cip}","status":"%s{respcode}","user":"%s{elogin}","url":"%s{eurl}","vendor":"Zscaler","hostname":"%s{ehost}","clientpublicIP":"%s{cintip}","threatcategory":"%s{malwarecat}","threatname":"%s{threatname}","filetype":"%s{filetype}","appname":"%s{appname}","pagerisk":"%d{riskscore}","department":"%s{edepartment}","urlsupercategory":"%s{urlsupercat}","appclass":"%s{appclass}","dlpengine":"%s{dlpeng}","urlclass":"%s{urlclass}","threatclass":"%s{malwareclass}","dlpdictionaries":"%s{dlpdict}","fileclass":"%s{fileclass}","bwthrottle":"%s{bwthrottle}","servertranstime":"%d{stime}","contenttype":"%s{contenttype}","unscannabletype":"%s{unscannabletype}","deviceowner":"%s{deviceowner}","devicehostname":"%s{devicehostname}","upload_filetype":"%s{upload_filetype}","upload_filename":"%s{upload_filename}"\}\} |
| Timezone | GMT |
| Duplicate Logs | Disabled |
Adding NSS Feeds for Firewall Logs
Follow the steps outlined in the ZIA documentation.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Feed Name | Whatever you want, however we suggest: NTT-FW |
| NSS Type | NSS for Firewall |
| NSS Server | Select your NSS Server created in Adding NSS Server or the existing server |
| SIEM Destination Type | IP Address |
| SIEM IP Address | IP address of your Samurai Local Collector |
| SIEM TCP Port | 514 |
| Log Type | Firewall Logs |
| Feed Output Type | JSON |
| Timezone | GMT |
| Duplicate Logs | Disabled |
Adding NSS Feeds for DNS Logs
Follow the steps outlined in the ZIA documentation.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Feed Name | Whatever you want, however we suggest: NTT-DNS |
| NSS Type | NSS for Firewall |
| NSS Server | Select your NSS Server created in Adding NSS Server or the existing server |
| SIEM Destination Type | IP Address |
| SIEM IP Address | IP address of your Samurai Local Collector |
| SIEM TCP Port | 514 |
| Log Type | DNS Logs |
| Feed Output Type | JSON |
| Timezone | GMT |
| Duplicate Logs | Disabled |
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.8.69 - Zscaler Private Access (ZPA)
| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Connectivity Requirements
You must ensure the following connectivity requirements are fulfilled:
| Source | Destination | Ports | Description |
|---|---|---|---|
| Zscaler App Connector | Samurai Local Collector | TCP/514 | For log transmission |
Log Receiver Configuration
Follow the steps outlined in the ZPA documentation.
Use the following parameters when completing the steps within the documentation under section 1. Log Receiver:
| Field Name | Parameter |
|---|---|
| Name | Specify a unique name, such as User Activity |
| Description | Specify a relevant description |
| Domain or IP Address | IP address of your Samurai Local Collector |
| TCP Port | 514 |
| TLS Encryption | Disabled |
| App Connector Groups | Select the group(s) related to the on-prem App Connector(s) that will forward data to the Samurai Local Collector |
Use the following parameters when completing the steps within the documentation under section 2. Log Stream:
| Field Name | Parameter |
|---|---|
| Log Type | User Activity |
| Log Template | JSON |
| Policy | Select |
Create Additional Log Receivers
A log receiver is required for each log type. Complete the Log Receiver Configuration steps outlined above for each log type listed below. Where User Activity is referenced in the previous section, replace it with the log types listed below:
- Browser Access
- Audit Logs
For integrations that utilize a Local Collector where we ingest syslog only, you do not need to follow specific steps in the SamurAI MDR portal as we auto detect the vendor and product. The only reason you need to use the SamurAI MDR portal is if you need to determine the Local Collector IP address. Of course you will still need to ensure the integration is functioning! See Integrations for more information on checking status.
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.
2.9 - Assistant
The Assistant is an AI-powered documentation assistant to quickly find information from official documentation directly within the SamurAI Portal.
It enables SamurAI Portal users to ask natural language questions and get accurate, contextual answers drawn solely from SamurAI documentation.
The Assistant is designed to make it faster and easier to find setup instructions, feature explanations, and guidance without leaving the SamurAI Portal.
Key Benefits
- Instant answers - quickly get relevant information from SamurAI documentation
- Natural language support - ask questions as you would a person
- Time saving - No need to manually search or navigate multiple documentation pages
How it works
- The Assisant is trained exclusively on this documentation site
- It does not access or have access to client data or personal information
- It uses AI natural language understanding to summarize or direct you to the most relevant documentation pages
- It is automatically updated to include revised or new documentation
- It operates securely within the SamurAI Portal - no external AI services are used
Example Questions
- How do I validate the status of my local collector?
- What is Advanced Query and its purpose?
- What is the Samurai platform?
Access the Assistant
Login go the SamurAI Portal
Click on Assistant in the main menu.
Limitations
- As with any LLM-based system, the Assistant may occasionally produce inaccurate or incomplete responses. Users should validate outputs, as AI can make mistakes.
- Questions are limited to 250 characters to encourage concise queries and prevent long-form text input.
- The Assistant does not retain memory of previous questions or interactions. Each query is treated independently, meaning it cannot reference or build upon earlier conversations. For continuity, users should include relevant context in each new question.
3 - Knowledgebase
3.1 - SamurAI MDR
3.1.1 - What are the Integration Table fields?
The Integration Table lists all of your integrated products to the SamurAI platform. The table has a number of fields which are described below:
| Field Name | Description | Additional Info |
|---|---|---|
| Status | Color indication of integration status | Pending Unknown OK Warning Critical |
| Status Description | Description of the status | Pending: Telemetry components installing / provisioning or awaiting status Unknown: The SamurAI platform is unable to determine a status OK: All components healthy Warning: The SamurAI platform has not seen any events per the defined threshold Critical: The SamurAI platform has not seen any events per the defined threshold |
| Info | Useful information displayed when hovering over icon |
|
| ID | Universally Unique Identifier (UUID) for integration | UUID utilized by the SamurAI Platform |
| Vendor | Vendor name of the product | unknown indicates the vendor is not currently supported by SamurAI |
| Product | Product name | unknown indicates the product is not currently supported by SamurAI |
| Type | Integration type used to gather or ingest telemetry. | Potential entries displayed include:
|
| HA Group | High Availability (HA) group of integrations. | Review High Availability and Integrations for more information. |
| Name | Integration name | The name provided during integration configuration or could denote the hostname if sending syslog to a Local Collector |
| IP Address | IP address of the host | |
| Collector | Collector name associated with the integration | The Collector used to ingest telemetry to the SamurAI platform |
| Description | Optional description provided during integration configuration | This description can be edited at any time within Integration Details |
| Last Event Seen | The last event seen from the telemetry source | Format is [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default or as configured. |
| Created | Date and time of integration creation | Format is [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default or as configured. |
3.1.2 - Best Practices for Custom Status Thresholds
Custom status thresholds allow you to fine-tune telemetry monitoring. This article provides practical guidance for setting thresholds that balance responsiveness with noise reduction.
Why it matters
- Low thresholds may result in status ‘flapping’ and not reflect accurate status
- High thresholds may result in delayed detection of telemetry ingestion/collection issues.
The goal is to align thresholds with integration behaviour, business impact, and maintenance patterns.
Best Practices
1. Start Conservative, Then Optimize
- Review and leverage default thresholds to begin with and if not satisfactory then look to customize for your operational needs.
- Monitor notification frequency and adjust to reduce false positives while maintaining reliability.
2. Understand the Integration’s Normal Behavior
- Review historical data through the events graph or via Advanced Query to determine typical ingest times or intervals.
- Avoid setting thresholds too aggressively to ensure notifcation of minor, non-critical fluctations in system behaviour.
3. Balance Sensitivity and Noise
- Warning Threshold: Set this to catch early signs of delay without triggering too often.
- Critical Threshold: Make this significantly higher than the warning threshold to indicate a real issue.
4. Consider Business Impact
- For mission-critical integrations use tighter thresholds.
- For non-critical allow more flexibility to avoid unnecessary notifications.
5. Account for Maintenance Windows
- If integrations have scheduled downtime or maintenance, adjust thresholds or disable notifications during those periods.
Common Pitfalls
- Ignoring seasonal patterns: Traffic spikes or quiet periods can skew thresholds.
- One-size-fits-all settings: Different integrations need different thresholds.
- Not revisiting thresholds: Review quarterly or after major changes.
3.1.3 - Boost Scoring
Boost Scoring is a technique used by the SamurAI platform which improves the ability to find Advanced Persistent Threats (APTs) by using a methodology which helps to link seemingly unrelated events allowing the platform to determine where a set of events becomes notable enough to warrant investigation as a threat.
This is done by using the ability to identify suspicious activities using the combined insights offered by multiple enrolled sources, irrespective of technology type or vendor. This enables detection using activities and events that normally would not be of a significant interest by themselves. When seen in combination however they represent individual aspects of a threat. Boost scoring provides a method to link these events and strengthen their relevance when they are combined.
By grouping activities and events on a user and entity basis and Mitre tactic basis, Boost scoring enables identification of suspicious behaviors which are identified via combined insights. The Boost score increases over time providing more accurate confidence and threat severity scoring for each group over time.

Figure 1: Boost scoring
By keeping the Group state for a long period of time (typically over 60 days) SamurAI is able to detect evasive threats that have stayed dormant for a longer period of time after the initial breach by linking additional events which can be linked to the initial breach attempt.
Once a Boost score reaches a predetermined level it will be used to generate an alert which is presented to SOC analysts. This helps to suppress single indicators from raising alerts, and rather permits the gathering of evidence until a confidence threshold is reached where the raising of an alert is justified.
This technique enables detection of dormant threats and slow-moving attacks (a traditional evasion technique). Suspicious activities are assessed in their entirety regardless of threat severity, time or log source.
Simply put, Boost scoring helps to find the balance between too many alerts (false positives) and too few alerts (false negatives) and in that process selecting the activity which is of real importance in identifying the activity of threat actors.
3.1.4 - How do I know if my integration is functioning?
It is important to understand that the integrations you have configured are working correctly and sending telemetry to the SamurAI platform.
Integration Health
You can easily get an overview of which of your integrations are not healthy (e.g the integration status is not reported as OK) by viewing the Integrations Table or Telemetry Monitoring. Telemetry Monitoring provides you a concise overview of any integrations which are considered unhealthy, or in other words, integrations where the SamurAI platform has not seen events/data over specific time periods:

Figure 1: Example telemetry monitoring view
The fact that an integration is unhealthy doesn’t necessarily mean that there is a fault. For example, your integration may send telemetry intermittently. The SamurAI platform takes this into consideration through default status thresholds, however as environments may differ you may consider updating the Status Threholds to meet your requirements.
Telemetry Monitoring Notifications
By default the SamurAI platform will send email notifications to registered users if an integration is reported as Critical.
Notification settings can be fully customized to meet your requirements, refer to Notification Settings for more information.
Managing Integration Health
There are a few factors which could result in telemetry not being properly ingested. This article takes you through the main factors which could impact whether an integration is working or not, who is responsible for them, and how to address them.
In order for data to be ingested into the platform, the following main areas need to be functioning properly:
- Platform is available: We are responsible for making sure that the SamurAI platform is available.
- Data source configuration: Often the first place to check is that the source is correctly configured to send data. If your data source uses a Cloud Collector, you will also need to check that the Cloud Collector is functioning and healthy. Make sure that you have followed all of the configuration steps outlined in the configuration guide for the Integration.
- Connectivity: Any data sources using Local Collectors are dependent on:
- required ports from the device to the Local Collector as outlined within the configuration guide
- internet connectivity between your premises and the SamurAI platform. Check that your internet connection is available and that firewalls are configured to allow traffic.
- the Local Collector article provides a detailed explanation of all of the ports that a Local Collector needs to have open in order to function correctly.
- Local Collector: If your data source uses a Local Collector, you will need to ensure that the Local Collector is available. You will also need to ensure that the virtualization platform that hosts the Local Collector is healthy. For more information see the section on Local Collectors below.
- Cloud Collector: If your data source uses a Cloud Collector, the health of your integration is also dependent on the Cloud Collector being operational. If your cloud collector monitors a cloud storage account, ensure that your integrated sources are sending and storing data to the storage account. If your data source is correctly configured but it remains unhealthy e.g reported status is Pending and/or Unknown, it is our responsibility to ensure the Cloud Collector is operational for you.
Local Collectors
If your integration is utilizing a Local Collector, first ensure it’s running as expected. If there is a problem with your Local Collector you should receive an email notification when the status is reported as Critical (by default) or per your configured user notification settings.
When you drill down into a Local Collector in the SamurAI Portal, you are provided a view which shows you the health of the Collector, together with all of the Integrations that are configured to use that Collector:

Figure 2: Example local collector view
For integrations that utilize a Cloud Collector you can jump directly to checking the Integration status.
Integration Status
Once you have confirmed that the Local Collector is Healthy (communicating with the SamurAI platform), check the Integration status. From the Collectors menu (applicable to both Local Collectors and Cloud Collector) you can view associated integrations to view their state of health. Alternatively, navigate to the Integrations page. Refer to Integrations Details and Status.
In both cases you will see a column called ‘Last Event Seen’. This column provides a timestamp of the last received event with the time format as [yyyy:mm:dd], [hh:mm:ss]) and in your timezone set per Time Zone.
The SamurAI platform monitors for ‘Last Event Seen’ within specific timeframes that relate directly to the status. There are default status thresholds, but they can also be fully customized, therefore if you are troubleshooting problems, check for any custom thresholds. Refer to Status Thresholds for more information.
If for some reason, the Integration is not healthy (e.g. not Green), then run through the Integration guide for your specific device and confirm there are no other controls blocking the traffic to the Local Collector or Cloud Collector.
If your Integration is of type Local or Cloud and is not healthy, then review the integration configuration to ensure it is correct and also ensure you followed the appropriate Integration guide for your device.
If you still have issues and please submit a ticket via the SamurAI Portal
Querying the detail
If you would like to go into more detail about the events from your log sources, you can make use of Advanced Query to analyze the events stored in the SamurAI platform. This will help you to answer questions like:
Is my log source generating logs intermittently?
By querying your log source over a period of time, the graphical representation of events will quickly show you time periods when your log source was not generating logs:

Figure 3: Example query
When did my log source last generate an event and what was that event?
You can easily find the last time when a log source generated an event. This will be the same as the “Last Event Seen” field for the Integration. For instance, the following query shows the last log generated in the last 7 days:

Figure 4: Example query
Is my log source configured to generate correctly formatted logs?
Sometimes a configuration error on your log source might result in your log source generating incorrectly formatted logs. By examining the raw log content you can check that your logs are correctly formatted. This will assist in correcting any configuration errors which may have resulted in incorrectly formatted logs being sent.
Is my log source sending the logs I need?
By checking the types of events generated, you can verify that you have configured the log source to send the logs you require, and that it is generating them. For instance, in this example, we are verifying that a device is generating DNS logs as expected:

Figure 5: Example query
3.1.5 - SamurAI Glossary of Terms
The definitions provided below are used within SamurAI documentation, all legal terms can be found under Legal.
Agent
A software component installed on an endpoint. The SamurAI Endpoint ‘Agent’ is a native software agent of the SamurAI Platform that enables telemetry collection and query execution in the delivery of the SamurAI Managed Detection and Response service.
Advanced Analytics
Detection capabilities, including machine learning, big data, and complex event processing analysis, that are used by the SamurAI platform.
Alert
Security detection made by the SamurAI platform or third party vendor where we are ingesting telemetry.
Boost Scoring
Boost Scoring is a technique used by the SamurAI platform which improves the ability to find Advanced Persistent Threats (APTs) by using a methodology which helps to link seemingly unrelated events.
Collector
A Collector is responsible for ingesting telemetry (or logs) into the SamurAI platform. There are two types of Collector, Local Collectors and Cloud Collectors.
A Local Collector is a virtual appliance which is deployed in your environment. Typically you will use the Local Collector as the destination for syslog messages produced by your devices.
A Cloud Collector provides the ability to ingest telemetry from cloud platforms and services, and is hosted centrally as part of the SamurAI platform. For specific integrations we leverage a cloud collector to monitor public cloud storage and pull data to the SamurAI platform.
Correlation
The ability for our systems to find a common linkage in Logs or Events (via source or destination IP address, Common Vulnerabilities and Exposures identifier, or other attributes) and combine them within one Event to add context to an Alert.
Endpoint
A physical or virtual device (e.g workstation, laptop, server) that connects to a computer network.
Enrichment
The process of adding contextual information (such as geolocation, evidence from packet captures or other data) to log information, either programmatically, or by a Security Analyst.
Event
All of the individual data points (Telemetry) ingested via Collectors into the SamurAI platform are known as Events. Through the use of Advanced Analytics, our systems are able to generate Alerts from Events which indicate the presence of threat actor activity. All events are stored in our data lake, and can be queried using Advanced Query.
Global Threat Intelligence Center (GTIC)
The organization within NTT’s Security Holdings responsible for, threat research, vulnerability tracking and the development, aggregation and curation of threat intelligence.
Integration
Integrations provide the mechanism to ingest telemetry (in other words logs and data) into the SamurAI platform.
Managed Detection and Response (MDR)
SamurAI Managed Detection and Response is a service which delivers cybersecurity insights, advanced threat detection, response, and protection capabilities via the ingestion of varied telemetry sources including cloud, network, compute and mobility sources. Supported telemetry combined with our proprietary Advanced Analytics, analyst threat hunting, and AI-based threat detection capabilities translate to faster, more accurate detections and most importantly reduced business risk.
MITRE ATT&CK Framework
MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
Threats detected by the SamurAI platform are mapped against MITRE ATT&CK to assist in better understanding the nature of the activity detected, possible countermeasures and the urgency of response.
Network Traffic Analyzer (NTA)
A native component of the SamurAI Platform. It is a passively deployed sensor that monitors mirrored network traffic to provide real-time, agentless visibility into network activity. The NTA is designed to detect suspicious or malicious behavior across both perimeter and internal segments of a network in conjunction with the SamurAI Managed Detection and Response (MDR) service.
Node
A registered instance of the SamurAI Endpoint Agent with the SamurAI platform.
SamurAI Endpoint Agent
A native software agent of the SamurAI Platform. It is installed on an endpoint enabling telemetry collection and query execution in the delivery of the SamurAI Managed Detection and Response service.
SamurAI plaform
SamurAI is a vendor-agnostic, cloud native, scalable, API-driven, advanced threat detection, and response platform.
SamurAI Hunting Engine
Intelligence-driven detection engine based on the Sigma project but customized by NTT with additional detection capabilities. The SamurAI hunting engine performs automated threat hunting to idenfiy and alert on possible adversary activity.
SamurAI Real-time Engine
Proprietary NTT developed detection engine that leverages behaviour modeling, machine learning, and the latest threat research to automatically identify suspected threats during real-time analysis of ingested telemetry into SamurAI.
Security Incident
A notable threat to a client environment detected and validated via automation or by Security Analysts. Security Incidents may require a response to mitigate or eliminate the identified threat. Information related to Security Incidents are available via the SamurAI Portal and downloadable in PDF format as required.
Severity
Severity is the term used to describe the potential magnitude of impact of a detected threat which is presented as a Security Incident. Severity is presented as Unknown, Low, Medium, High or Critical.
Telemetry
In the context of SamurAI, Telemetry refers to the data, usually in the form of logs, collected from different security solutions and other sources which is then ingested into the SamurAI platform. This includes but is not limited to network, firewall , DNS, email, endpoint, server, and cloud workloads.
Each telemetry source contains different types of activity data. The SamurAI platform is able to collect a wide variety telemetry in order to detect and hunt for unknown threats and assist in forensic analysis.
Tenant
A tenant is the entity used to represent an organization using SamurAI. Individual users can be invited to one or more tenants.
3.1.6 - Telemetry Data Source Categorization
SamurAI telemetry support is categorized using the following three levels. These categories describe the estimated value that a specific telemetry data source is expected to add to the Managed Detection & Response (MDR) service, whilst providing clarity and expectations of threat detection capabilities.
1. Foundation
- Vendors and technologies with excellent threat detection, validation and hunting capabilities and where evidence collection is performed (such as IDS/IPS).
2. Detection
- Vendors and technologies with good threat detection capabilities and where evidence collection is performed (such as Sandbox). Although best offered in combination with Foundation sources, Detection level sources are sufficiently high value to be monitored in isolation.
3. Enrichment
- Vendor and technologies with no / limited threat detection / validation capabilities in isolation. Used mainly for correlation, Threat Hunting and Enrichment purposes in combination with Foundation/Detection sources.
Some examples:
- An IDS/IPS telemetry source where full API integration is available and evidence (e.g Packet Capture - PCAP) is collected for analysis would be used for threat detection purposes. However the same technology type without such an integration (e.g syslog only) would only provide data with no actual detail in support of qualifying threats, and would therefore primarily be used for Enrichment purposes in relation to events from sources of a higher support level.
- A DHCP log would add no actual detection capability, but it can be used to identify the actual physical host in a network using dynamic net assignment.
For technologies consisting of a combination of data source types, our policy is that the highest level of support that a source reaches also determines the overall support category of the technology.
For example, a Unified Threat Management (UTM) data source consisting of multiple types (e.g. Firewall, URL, IDS/IPS, Sandbox) would when evidence collection is supported (e.g. PCAP, Sandbox Execution reports) be categorized as a Foundation source as the IDS/IPS with PCAP collection is considered to be at such a level.
A UTM consisting of the same source types, without evidence collection, would be categorized as Detection support as the highest level source would be at Detection level (e.g. URL/FW).
All supported telemetry data sources with the assigned category can be found under Supported Integrations.
3.2 - Support
3.2.1 - Getting Help
Contacting Support
You can contact us by submitting a ticket from the SamurAI Portal. We will get back to you in accordance with our Support Policy.
General Tickets
Submit a ticket from the SamurAI Portal:
- Ensure you are signed in to the SamurAI Portal
- From the main menu at the top left click General Tickets
- Select Create Ticket
- Add a Title and Description that describes your issue or request.
- Click Create ticket
Emoji support is also available.
- Windows: Press Windows + . (period) to open the emoji picker.
- macOS: Press Control + Command + Space to open the emoji and symbol picker.
Tracking Tickets
- Ensure you are signed in to the SamurAI Portal
- From the main menu at the top left click General Tickets
General Ticket Status
- Awaiting SOC: Ticket is currently awaiting feedback / input from the SOC
- Awaiting Feedback: Ticket has been created or updated and is awaiting your feedback / response
- Closed: The Ticket is Closed.
Security Incidents
Review the following articles on Security Incidents and The Situation Room for further information on Security Incidents.
Tracking Security Incidents from the SamurAI Portal:
- Ensure you are signed in to the SamurAI Portal
- From the main menu at the top left click Security Incidents.
Security Incident Status
- Awaiting Feedback: Security Incident has been created or updated and is awaiting your feedback / response
- Awaiting SOC: Security Incident is currently awaiting feedback / input from the SOC
- Closed: The Security Incident is Closed.
How do I access documentation for the SamurAI Portal?
You must already know, if you are reading this!!
- From the SamurAI Portal select Documentation on the main menu
4 - Services
4.1 - Managed Detection and Response (MDR)
4.1.1 - Managed Detection & Response (MDR) Service Description
1. Introduction
NTT’s SamurAI Managed Detection and Response (MDR) service builds on the capabilities of the SamurAI platform which delivers cybersecurity insights, advanced threat detection, response, and protection capabilities via the ingestion of varied telemetry sources including cloud, network, endpoint, identity and compute. Supported telemetry combined with our proprietary advanced analytics, threat hunting, and AI-based threat detection capabilities translate to faster, more accurate detections and most importantly reduced business risk.
SamurAI MDR offers the sophisticated threat detection capabilities of the SamurAI platform along with, 24/7 threat monitoring, automated and analyst-driven threat hunting, and comprehensive Cyber Threat Intelligence (CTI) delivered by NTT’s Global Threat Intelligence Center. By combining the advanced analytics capability of the SamurAI platform with the expertise of skilled Cyber Security Analysts in NTT’s Security Operation Center (SOC), threats are identified and separated from a large number of false positives typically generated by security technologies.
SamurAI MDR is a service that utilises security alerts along with relevant contextual information identified by the SamurAI platform. This information is analysed by a skilled Cyber Security Analyst, who engages in threat hunting and validation activities to verify the threat, its impact, and to identify additional information associated with a potential breach. Once the threat is validated, the Cyber Security Analyst creates a detailed Security Incident Report for the Client. The Security Incident Report includes a detailed description of the security incident combined with scenario-specific actionable response recommendations. This significantly assists in reducing the time taken for informed responsive measures, thereby, lowering associated risks.
2. Service Elements
SamurAI MDR provides the Client with a service overlay which provides advanced detection and response capabilities delivered by skilled Cyber Security Analysts in NTT’s SOC, leveraging the SamurAI platform. The SamurAI MDR service provides a set of components which provide the Client with:
- Onboarding guidance
- Access to SOC Analysts
- Cyber Threat Intelligence
- Threat Detection and Investigation
- Threat Hunting
- Security Incident Reports
- Threat Response
- Service Management Portal and Reporting
- Incident Response
- Service Assurance through regular Threat Reviews
3. Onboarding
Onboarding of the service commences with the activation of the Client’s SamurAI tenant. Activation of the Client’s tenant will provide the Client with a link to online documentation and the access and instructions required in order to integrate with the SamurAI platform. This includes:
- Deploying Local Collector appliances
- Deploying Network Traffic Analyzer(s) (NTAs)
- Deploying SamurAI Endpoint Agent(s)
- Connecting telemetry sources (including logs, enrichment and other data sources) and;
- Configuring integrations to client applications such as Endpoint Detection and Response, network security controls and other cloud-based platforms
Within two business days of activation, NTT will host a SamurAI MDR introductory conference call with the Client. This meeting will explain the onboarding process and will include an overview of the SamurAI Portal and configuration steps to be completed by the Client. Follow-up progress calls may be scheduled to ensure setup progress and status. Within fourteen days of activation a SamurAI MDR orientation conference call will be held with the Client which upon completion, Service Delivery will begin. This meeting will outline what to expect from the service including how SOC analysts will interact with the Client, overview of Security Incident Reports and how to utilize the SamurAI MDR.
For more details please visit the SamurAI MDR Onboarding Guide.
4. Service Features
SamurAI MDR provides the following service features:
4.1 Threat Detection
The SamurAI platform detects threats and suspicious behavior using the SamurAI Real-Time Engine and the SamurAI Hunting Engine. The SamurAI Engine(s) makes use of a combination of traditional threat detection techniques, advanced analytics, machine learning and Cyber Threat Intelligence to detect sophisticated threats. To ensure service quality, NTT continuously makes detection-tuning decisions based on the validity and relevance of alerts and security incidents.
4.2 Cyber Threat Intelligence
SamurAI MDR integrates Cyber Threat Intelligence (CTI) from a diverse set of sources, including Open Source Intelligence (OSINT), commercial feeds, restricted sharing communities, and proprietary insights from NTT’s Tier-1 Global IP Network. This multi-source approach ensures that alerts are enriched with actionable context, enabling faster and more accurate threat detection.
CTI updates are continuously refined through real-time investigations of security incidents, ensuring that threat intelligence remains current and relevant. This dynamic enrichment process enhances the fidelity of detections and supports proactive defense against emerging threats
4.3 24/7 Security Analyst Interaction
SamurAI MDR includes detailed security investigation of alerts detected via SamurAI by Cyber Security Analysts in NTT’s SOC. Investigation includes threat analysis and threat hunting activities across the Client’s telemetry environment to provide validation and assessment of the malicious nature of a threat and its potential impact.
Cyber Security Analysts use the MITRE ATT&CK framework as a reference model in presenting the nature of a threat and assigning appropriate severity to identified security incidents.
SamurAI MDR also validates threats through vendor integration and evidence collection for selected security technologies, such as packet capture data (PCAP) and malware execution reports.
4.4 Investigations
When the SamurAI platform generates an alert indicating a potential threat, an NTT SOC Cyber Security Analyst will begin an investigation. The investigation includes validating the presence of a threat via client telemetry and evidence data, cyber threat intelligence, and other data and information sources within the SamurAI platform. Using this information and automation capabilities of the SamurAI platform, the analyst then determines the nature and extent of any compromise which may have occurred. Depending on the nature of the potential threat, activities conducted during the process of the investigation may include:
- Threat analysis
- Threat hunting across the Client’s telemetry data which has been ingested into the SamurAI platform
- Assessment of the malicious nature of a threat and its potential impact
- Contextualisation of validated threats based on factors such as industry vertical and geopolitical context
- Categorisation according to industry best practice frameworks including MITRE ATT&CK
- Forensic analysis of telemetry data stored in the SamurAI platform
- Malware analysis; and
- Recommendation to the Client of a suggested response covering suggested next steps
4.5 Security Incident Reports
If, as a result of an investigation, a threat is identified, the Cyber Security Analyst creates a Security Incident Report detailing the cybersecurity incident, including plain-language observations and incident mitigation and/or remediation recommendations.
Client notifications can be provided by phone or email based on severity:
- Critical severity; Phone / E-mail notifications
- Low, Medium, High severity; E-mail notifications
Clients requiring phone notifications must provide NTT with a prioritized list of Client contacts.
4.6 Threat Hunting
Utilizing Client telemetry and evidence data, NTT perform automated scheduled and event driven threat hunting to detect activities such as post exploitation behaviors, malicious activity, lateral movement or the tactics and techniques and procedures (“TTPs”) of threat actors. Cyber Security Analysts also conduct retroactive threat hunting based on newly released threat research to identity and mitigate threats associated with recent discoveries. When a threat is detected, a cyber security analyst will create a security incident and notify the Client.
4.7 Threat Response
NTT can perform actions on the Client’s behalf when an investigation results in the detection of a threat.
NTT will take actions to isolate compromised/malicious host Endpoints following Cyber Security Analyst incident validation. Remote isolation actions are performed using the isolation capabilities of the Client’s Endpoint Detection and Response (EDR) technology.
4.8 SamurAI Portal
Managed Detection and Response Clients have access to the SamurAI Portal, details of the functionality can be found in SamurAI online documentation that includes:
- Self service features such as:
- telemetry integration
- local and cloud collector configuration and monitoring
- SamurAI Network Traffic Analyzer (NTA) configuration and monitoring
- SamurAI Endpoint Agent download and monitoring
- Interact with us online by logging incidents and requests
- View reported security incidents
- Track, view and submit comments within incident and request tickets; and
- View service dashboards, metrics and reports.
4.9 Threat Reviews
Through a program of scheduled quarterly meetings, Threat Reviews will be conducted with the Client to derive maximum value from SamurAI MDR.
Topics covered in the quarterly meetings include:
- Review service health
- Review security incidents and how they provide insights into the Client’s security posture and attack surface; and
- Advising the Client regarding configuration of SamurAI to better meet the Client’s needs
For clients that require a dedicated resource and monthly threat reviews, the SamurAI Cybersecurity Advisor subscription is available as a chargeable add-on.
5. Supplements & Add-ons
5.1 The SamurAI Endpoint Agent
The SamurAI Endpoint Agent is a lightweight software component installed on Client endpoints and included with the SamurAI Managed Detection and Response (MDR) service. It is natively integrated with the SamurAI platform enabling foundational visibility in support of detection, investigation and response workflows.
Key Characteristics:
- Purpose-built for deployment across diverse endpoint environments with minimal resource impact
- Operates alongside existing endpoint security solutions ensuring compatibility with current security infrastructure
- Focused telemetry collection that aides SamurAI’s detection engines to identify threats and supports forensic analysis during investigations
By integrating directly with the SamurAI platform, the SamurAI Endpoint Agent enables NTT SOC Cyber Security analysts to perform real-time and scheduled queries, validate threats, and conduct investigations efficiently. This capability improves visibility into endpoint activity and supports proactive identification of suspicious behaviors and emerging threats across the client environment.
5.2 SamurAI Network Traffic Analyzer (NTA)
Included within the SamurAI MDR service at no additional charge, the SamurAI NTA is a Network Traffic Analyzer that identifies threats by analyzing traffic on Client network segments.
The NTA has embedded multiple components that leverage traditional threat detection techniques, advanced analytics, machine learning and Cyber Threat Intelligence to detect sophisticated threats.
Upon identifying suspicious activities, or threats, the NTA provides the NTT SOC Cyber Security Analysts with Evidence data (Full packet capture [PCAP]), allowing for deep network investigations. This additional evidence data increases the Cyber Security Analyst’s ability to analyse, validate and escalate cyber security threats.
Operating System/Software Management
NTT maintains the supported Operating System and installed Software on NTA devices. Such maintenance is performed remotely and at the sole discretion of NTT as relevant security hot fixes are made available, or as part of standard OS software management.
Capacity improvement recommendations
Where NTT monitoring determines that an NTA is oversubscribed, NTT shall liaise with the Client to determine the best plan and path forward. Examples include but are not limited to the following:
- Request the Client to change the network architecture
- Request the Client to update assigned virtual resources, or licenses to facilitate greater capacity
5.3 Incident Response
The Incident Response add-on is a retainer which the Client may choose to utilize if the Client requires the NTT SOC to perform additional threat investigation activities. Clients can continue to leverage the services of the NTT SOC in instances where the severity of an incident justifies additional effort to perform tasks such as threat hunting, malware analysis or forensic analysis of data in the SamurAI platform.
This add-on provides the Client with the facility of additional post root-cause analysis to assist with containment of a threat.
The Incident Response retainer includes 40 hours per year. If the Client requires additional Incident Response beyond 40 hours, additional retainers of 40 hours can be purchased.
Incident Response effectiveness is enhanced with an installed and supported endpoint agent. If the client does not have a supported agent, NTT will work with the client to provision endpoint agents to support the investigation. For more information please read the detailed description of the Incident Response add-on.
5.4 Dynamic Blocklist
Included within the SamurAI MDR service at no additional charge, Dynamic Blocklist provides a real-time feed of curated Indicators of Compromise (IoC). The Client can configure supported devices, such as next generation firewalls and internet proxies, to receive the dynamic list to proactively block threats. IoCs are added to the Dynamic Blocklist on an ongoing basis. Additional details can be found in the Dynamic Blocklist overview.
6. Data Retention
The SamurAI MDR service contract includes 12 months of telemetry data retention. Retention is performed only for clients with an active contract. Data will be deleted from all NTT data stores according to the retention window designated based on the contract period. If a contract expires, the client will no longer have access to their data via the SamurAI Portal or service features.
7. Client Responsibilities
Client is required to perform the following obligations below:
- assign a primary Point of Contact (POC) to work with NTT. Client will ensure that NTT’s records of all Client POCs are kept up to date and are accurate
- ensure that all telemetry sources have connectivity required in order to interact with the SamurAI platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data as well as the ability to monitor and control any agents or virtual appliances installed in Client’s environment for the purpose of providing the service
- ensure that endpoints falling under the scope of SamurAI MDR have a supported endpoint agent installed in order to facilitate the gathering of telemetry and evidence data as well as providing the ability to perform remote isolation
- provide knowledgeable technical staff and/or third-party resources to perform any configurations or software installations required in order for Client to consume the service. This includes, but is not limited to:
- Configuration of connectivity
- Installation of Local Collector virtual appliances
- Installation of Network Traffic Analyzer (NTA) appliances
- Installation of SamurAI Endpoint Agents
- Provision of IP addressing required for any virtual appliances required in Client’s network; and
- Configurations of cloud services required in order for the SamurAI platform to receive telemetry from these services
- perform all aspects of Service Onboarding, including the configuration of telemetry sources and configuration of Collectors to provide telemetry feeds to the SamurAI platform. Client will ensure that all source devices are compliant with the SamurAI platform configuration requirements and are running supported software and/or hardware versions
- ensure that it does not utilise any technologies or configurations which block traffic, rotate logs or in any other way impede delivery of the service
- procure all maintenance, support and licensing agreements with third-party vendors for all telemetry sources
- comply with all the relevant data privacy, regulatory, and administrative laws, policies and procedures related to monitoring user traffic and communications
- bring a threat, identified in a security incident report, to closure
Failure to provide any of the service requirement information on a timely basis can result in delays in Service Onboarding and Service Delivery by NTT and NTT shall not be liable for any consequences of such delays.
8. Service Level Agreements
The Service Level Agreements (SLAs) listed in this section will become active once Onboarding of the Client is considered complete.
8.1 Availability
The Availability SLA is determined by the ability of the Client to access the SamurAI Platform. This is measured by the ability of the Client to log into the SamurAI Portal.
NTT will use reasonable commercial means to ensure an availability of the SamurAI Portal of at least 99.9%. If the availability of the platform drops below this level, the Client may claim a Service Level Credit as set out in the table below:
| Application Availability | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| 99.9% - 100.0% | 0% |
| 95.0% - 99.9% | 1% |
| Less than 95% | 10% |
8.2 Validated Security Incident Notification
NTT will analyze alerts and related available data sources on a 24/7 basis for signs of malicious activity which has bypassed preventative security controls.
If malicious activity is confirmed, NTT will determine the severity of the threat. For Security Incidents with a severity of high or critical NTT will provide an Incident Report within 30 minutes of determining the severity.
For Security Incidents with a severity of low or medium, NTT will endeavor to provide an Incident Report within 120 minutes of determining the severity.
If the creation of a security incident report in relation to an incident with a severity of high or critical takes longer than 30 minutes, the Client may claim a Service Level Credit as set out in the table below:
| Time taken to create a security incident report | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| Less than 30 minutes | 0% |
| 31 to 300 minutes | 1% |
| Over 300 minutes | 5% |
A Client may make a maximum of 1 claim against this service level per calendar day and per security incident.
8.3 Receiving Service Credits
To receive a Service Credit, the Client must open a ticket via the SamurAI Portal within 30 days of the incident for which the Client is claiming a Service Level Credit.
4.1.2 - MDR Security Incident Management
Overview
The MDR Security Incident Management process is designed to address reported threats that pose a risk to a client’s environment and to ensure appropriate handling. When the Security Operations Center (SOC) create a Security Incident, it will remain open until the client reports back that the threat had been handled, risk mitigated and closure request submitted.
The more information included in a Security Incident, the easier it will be for a client’s security staff to understand and mitigate the threat, therefore the SOC create a detailed Security Incident viewable within the SamurAI Portal and downloadable in PDF format as required. The SOC also recommend you provide feedback of your incident handling as this could improve future security incidents from the SOC and your own handling of them.
Below is a description of how the SOC performs Security Incident Management when relevant threats are detected and how the Security Incident life-cycle is managed.

Security Incident life-cycle
The Security Incident Management process starts with a security detection (alert) made by the SamurAI platform (Real-time engine or Hunting engine) or third party technology integrated with the SamurAI platform. In all cases, the alert is presented to the the Analyst in the SamurAI platform. Another possible trigger for the Security Incident management process could relate to a known high risk global Security Incident or threat, for example Log4shell or SolarWinds. In this instance, the Analyst conducts Retroactive Hunting in available telemetry data to search for indicators of compromise (IOCs) and determine if a client has been affected by the newly discovered global threat.
Once the Analyst receives an alert, they will start to analyze the threat through an investigation process that includes reviewing AI/ML correlations and threat hunting across all telemetry data and older Security Incidents. In some cases, the Analyst will also try to recreate the threat in the SOC malware lab.
The analysis phase can be time-consuming, but the purpose is to find attack vectors to first verify how the attack has affected the client and how the threat can be mitigated. The more detail known about a threat, the easier it will be to mitigate. However, if the SOC observes that the threat is actively damaging client systems or leaking client data, an initial and expedited Security Incident will be created to inform the client so that client assets can be protected. The SOC will then update the initial Security Incident with all needed threat details.
Security Incident Management
When a new Security Incident is created it will be made available within the SamurAI Portal and an automated email notification is sent to predefined email addresses (collected during the MDR onboarding phase). The email will contain key information such as severity, title, reference ID and a link to the Security Incident within the SamurAI Portal. The initial Security Incident Status is set to Awaiting feedback. If the Security Incident severity is critical, the SOC will also call the client.
When creating the Security Incident, the SOC may perform remote isolation of infected client endpoints using the client’s Endpoint Detection and Response (EDR) platform. The SOC will also include a recommendation whether the client should engage your Incident Response Team (either you have an internal team, NTT is providing or a 3rd party). If further remediation is required the client can also engage the NTT Incident Response Team.
Once the client is informed by a notification email (or telephone call if severity is critical), the Security Incident will enter the handling phase.
The SOC will also include recommendation (actions) for the client to perform. Additional questions can be asked by the client in the Security Incident Situation Room communication channel (Click to read more) Type feedback or comments/questions, in the communications channel and click ‘Send message’.

Once the client clicks ‘Send message’, the Security Incident status is updated to Awaiting SOC, meaning the next action is on the SOC. The SOC will respond to your question or feedback. You may still add feedback and questions even if the status is Awaiting SOC and next actions will remain with the SOC.
It is important to ensure that any critical or high severity Security Incidents progress towards closure, therefore you are advised to keep the SOC updated and respond in a timely manner when the status is Awaiting feedback.
As long as the SOC is working on a response to your questions, the Security Incident status will remain as Awaiting SOC. When the SOC responds, the status will be updated to Awaiting feedback. If the SOC detects that a new or existing threat re-emerges or there is new vital information, the Security Incident will be updated, a new revision created and a notification emailed to you.
Closure
When the risk has been mitigated or the client has accepted the risk (e.g. managing the threat), the client can request the Security Incident to be closed via the Security Incident Situation Room. This decision is based on the client’s assessment that sufficient action to mitigate the risk has been taken and is now comfortable with closure of the Security Incident. In the event the SOC receive feedback to close the request during an open investigation, confirmation of the request will be included in the ticket details.
Non-closure
If the SOC does not receive a closure request from the client, the security incident will be kept active and in an Awaiting feedback status. The SOC will present and go through all of the non-closed security incidents during the regular Threat Review Meetings. This to ensure client handling of all reported threats and risks, If the SOC has received no feedback, this could mean that the threat is still present and active, despite being reported months ago.
4.1.3 - MDR Threat Reviews
The Managed Detection and Response (MDR) service will detect, respond and report relevant threats that pose a risk to a client, but it is the client’s responsibility to bring the risk to closure. To help the client with this, a program of quarterly threat reviews is included with the MDR service.
For clients that require a dedicated resource and monthly threat reviews, the SamurAI Cybersecurity Advisor add-on subscription is available for an additional fee.
The key focus of threat reviews is to help MDR clients get the most value from the service, reduce business risk based on security incidents reported, and ensure security incidents are handled appropriately.
Through regular threat reviews, a client will:
- be trained and educated to understand threats and risks reported by the MDR service,
- be provided recommendations to improve detection and response, and
- receive follow-up to ensure that reported threats and risks are handled and mitigated.
The threat review program is initiated at the time of onboarding. During the orientation call the quarterly meetings will be scheduled for the remainder of the contract period. Please review Onboarding Managed Detection and Response (MDR) for further details.
The threat review meetings are scheduled during business hours within central European time (CET) and conducted by an MDR analyst who is or has been part of 24/7 MDR service delivery. This resource is not a dedicated resource per client but is a shared responsibility for analysts within our Security Operations Center (SOC). With access to the SOC workbench and a client’s SamurAI tenant our analysts have detailed knowledge of potential threats and risks, and skills to perform searches and hunts.
The MDR service will detect and respond to relevant threats that pose a risk. These threats are reported via Security Incident Reports. It is the client’s responsibility to handle and bring the risk to closure. All actions related to the handling of the security incident will be performed through the 24/7 MDR service and not during threat reviews. We understand that threats and risks can often be difficult to understand, our recommendations can often mitigate risk, however our aim during threat reviews is to enable clients to fully understand the risk so they can stay proactive, mitigate root cause, and avoid future security incidents. Hence during a threat review meeting we will present reported security incidents to a client and their stakeholders outlining the threats reported and risks posed.
We will also maintain and update a detection and response improvement list through the entire lifecycle of the MDR service. The improvement list focuses on suggestions that will improve detection of threats e.g. new systems that should be onboarded into the MDR service, or could also include actions that either the client, the SOC or NTT Security Holdings need to take in relation to improving threat detection and response. The ultimate benefit of this process to the client is an improved security posture.
Threat reviews will also follow up on any actions performed by a client after a Security Incident was reported. This will help to confirm that the client was able to take suitable actions based on the threat identified. Depending on the client’s security posture and risk profile, the client may either take mitigation actions that remove the threat or decide to accept risk. Clients should provide feedback on the reported Security Incident and the actions taken as it enables the 24/7 MDR service to verify if the threat was removed or if still present after any actions. During Threat Review meetings we will work through these actions with the client so that the client handling time for any subsequent Security Incident will decrease, reducing risk exposure time.
If a client has any general questions or requests related to the MDR service and/or how to detect and respond to threats not related to a reported Security Incident, a ticket can be raised via the SamurAI Portal, and be handled by the Threat Review team.
4.1.4 - Onboarding Managed Detection and Response (MDR)
Overview
Welcome to NTT Security and the SamurAI Managed Detection and Response (MDR) Service.
We have made onboarding simple and shall support you through each phase.
MDR Security Operations Center (SOC)
The SOC provide guidance and expertise during onboarding and service delivery, however it is important to understand the role and responsibilities of you and our team.
The SOC will be your main contact during onboarding and will schedule introduction and orientation calls with you to ensure your journey to MDR is problem free. You as a Client will still need to perform your responsible actions outlined in the rest of this document and specifically for onboarding MDR telemetry sources, unless you have purchased SamurAI Onboarding.
After your orientation meeting, MDR Service delivery begins. The SOC will schedule and conduct regular threat review meetings as outlined within the MDR Service Description to ensure you derive maximum value from the service.
Suggested Resources
During onboarding you will likely need to call upon various teams within your organization, we understand you may not have all of the appropriate roles but suggest the following:
| Role/Function | Responsibility |
|---|---|
| Chief Information Security Officer (CISO) | Awareness of the service and how it functions to drive handling of security incidents reported |
| Security Operations Engineer | Management and administration of the SamurAI Portal |
| System Administrator | Deployment of Collector(s) |
| Network Engineer | Configuration of supported integrations, configuration of access control rules as required by Collector and integration |
| Security Manager | Integration of SamurAI MDR into your organization’s security practice and operating processes |
| Project Manager | Initiating, planning, executing, controlling and closing work of your teams to achieve onboarding |
Onboarding Phases
The image and table below outline the main phases of onboarding including responsibilities, resources and deliverables.
| Phase | NTTSH responsibilities | Client responsibilities | NTTSH Resource/Deliverable |
|---|---|---|---|
| Activation |
|
|
|
| Introduction Meeting (within 2 days SamurAI Portal activation) | |||
|
|
| |
| Setup |
|
|
|
| MDR Service Delivery | Orientation Meeting (within 14 days of introduction meeting) | ||
|
|
| |
| Threat Review (Quarterly during MDR Service Delivery) | |||
|
|
| |
| Incident Response (IR) retainer (option) | |||
|
|
|
Your Responsibilities
Below are your primary responsibilities during onboarding. Additional responsibilities may arise as needed to support aspects of the implementation that are unique to your specific environment(s):
- Create user accounts for additional users of the SamurAI Portal, maintain all user accounts, ensuring that contact information for each user is complete and accurate.
- Deploy SamurAI Collector(s) and successfully configure required integrations.
- Configure and manage all resources required to support the deployment of Collector(s) - virtual / physical.
- Configure and maintain supported on-premises log sources and cloud integrations in line with SamurAI MDR requirements.
- Ensure that all telemetry sources have connectivity required in order to interact with the SamurAI platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data as well as the ability to monitor and control any agents or virtual appliances installed in your environment for the purpose of providing the service.
- Respond to NTTSH communications in a timely manner and ensure attendance of the necessary resources for all meetings to ensure timely completion of onboarding and during service lifecycle.
- Bring a threat, identified in a security incident report, to closure.
Your overall responsibilities for the service can be found in the MDR Service Description.
4.2 - Additional Subscriptions
4.2.1 - Dynamic Blocklist
Dynamic Blocklist (DBL) is a feature included with SamurAI MDR. The list is a feed of high fidelity indicators of compromise (IOC) which when subscribed to by a supporting device, provides the ability to block traffic to the identified threat actor. Typical devices which can make use of DBL include Secure Web Gateways (SWG) and Next Generation Firewalls (NGFW).
The DBL contains IP addresses, domain names and Uniform Resource Locators (URLs) of servers hosting malware, exploits, botnet Command and Control (C&C) servers and other known malicious activity.
Feeds are updated hourly and as emerging threats are discovered. Devices which are subscribed to the DBL will receive updated IoCs at the next “push” or “pull” event, depending on the manufacturer.
Our high fidelity IoCs contained in the Dynamic Blocklist originate from sources including:
- NTT’s proprietary Threat Intelligence data sources
- IoCs based on security incident investigations from all clients subscribed to NTT’s threat detection services
- Threat Intelligence obtained via partner intelligence relationships
- Open Source Intelligence feeds which have been analyzed and vetted by NTT
- NTT analysis tools which detect malicious websites (especially phishing and fraud) and extract intelligence of phishing reports from social media.
Onboarding
During the MDR onboarding or during service, the client can choose to enable DBL.
If the client elects to enable DBL and has Supported Devices:
- The client must submit a DBL Request via the SamurAI Portal
- Include the relevant information required within the request as outlined within the DBL Configuration Guide
- Once access has been enabled, the client will be notified via the ticket with relevant configuration information.
- The client may then proceed with configuration of their devices as per the relevant DBL Configuration Guide
Supported Devices
NTT provides configuration guides to assist the Client in configuring Dynamic Blocklist on supported devices. The following device types are currently supported:
- McAfee WebGateway (Skyhigh Secure Web Gateway)
- Palo Alto Networks NGFW
- ZScaler Internet Access (ZIA) - Proxy
- Squid proxy
- Cisco Firepower
Depending on the capabilities of individual device types, DBL will be configured using one of two possible methods:
- “pull”: In a “pull” configuration the device is set up to connect to NTT’s servers and fetch the threat feed. The frequency of retrieval is dependent on the device configuration.
- “push”: In a “push” configuration the device is set up to receive connections from NTT’s servers in order to receive the threat feed. The frequency with which the threat feed is pushed to the client device is usually determined by the configuration of the client device.
If the client is interested in using DBL with a device that is currently not supported, this can be discussed with NTT during onboarding.
Connectivity Requirements
In addition to configuring the devices for DBL, the client will also need to ensure that Internet connectivity is in place:
- for devices using a “pull” configuration, outbound TCP connections to the DBL server, typically on port 443.
- for devices using a “push” configuration, inbound TCP connections are possible from DBL servers to the client device.
NTT will provide the client with the DBL server IP addresses and/or URLs and other relevant details of the via the ‘DBL On-boarding request’ ticket.
4.2.1.1 - Dynamic Block List Configuration Guides
4.2.1.1.1 - Cisco Firepower DBL Configuration Guide
Submit a ticket
To continue with this configuration guide you must first submit a ticket via the SamurAI Portal. Add the following information within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for Cisco Firepower device(s) |
| Description | Add hostname and IP address (internet facing) of your Cisco Firepower devices. For example: mycfw1.acme.org, 19.16*.2*.2 If enrolling multiple devices please add each device on individual line* |
Submit the ticket and you will hear back from us with additional information (e.g DBL URL) to continue with the configuration below.
Connection Requirements
You will need to ensure your Firepower device(s) can reach a specific URL to obtain the DBL. This information will be provided to you once subscribed.
| Parameter | Note |
|---|---|
| Connection Port | TCP / 443 |
| DBL URL | NTT will provide a unique URL to you to download the DBL URL list |
Table 1: Connections requirements
To complete this integration you have to:
- Have submitted a ticket via the SamurAI Portal and have been provided the necessary DBL endpoint URL/IP address.
From your Cisco Firepower Management Console (FMC):
- Create a feed that captures the DBL URLs
- Set Security Intelligence Settings for DBL URL
- Confirm Blocking
- Create a feed that captures the DBL IP list
- Set Security Intelligence Settings for DBL IP
Create a feed that captures the DBL URLs
Login to your FMC
Click Objects – Object Management

- Click Security Intelligence – URL Lists and Feeds in the left pane.

- Click Add URL Lists and Feeds

- Enter the following information in Security Intelligence for URL List/Feed and click Save
| Parameter | Entry |
|---|---|
| Name | whatever you want, in our example we have used ABTI_for_URL |
| Feed URL | Feed URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| MD5 URL | MD5 URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| Update Frequency | (Optional) - If you set the Update Frequency to less than 30 minutes, the MD5 URL is required |

Set Security Intelligence Settings
Set the feed you created in Create a feed that captures the DBL URLsto Security Intelligence.
- Click Policies – Access Control

- Select the Policy for which you want to set the Feed
(For example: Select sample-fp-policy as depicted below)

If you do not have a Policy, create one from New Policy and follow the procedure
Select Security Intelligence

- Select URLs

- Select the Feed you created in Create a feed that captures the DBL URLs(our example was ABTI_for_URL)

- Under Available Zones, select Any and click Add to Block List

- Click Save

- Click Deploy

Confirm Blocking
Verify that the test URL is blocked.
- From a browser that leverages the Cisco Firepower inspection path, access the following test URL:
- Verify that it is blocked. If blocking does not occur check through the configuration again. Our example block screen looks like this:

Create a feed that captures the DBL IP list
- Click Objects – Object Management

- Click Security Intelligence – Network Lists and Feeds in the left pane

Click Add Network Lists and Feeds
Enter the following information in Security Intelligence for URL List/Feed and click Save
| Parameter | Entry |
|---|---|
| Name | whatever you want, in our example we have used ABTI_for_IP |
| Feed URL | Feed URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| MD5 URL | MD5 URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| Update Frequency | (Optional) - If you set the Update Frequency to less than 30 minutes, the MD5 URL is required |

Set Security Intelligence Settings for DBL IP
- Click Policies – Access Control**

- Select the Policy for which you want to set the Feed
(For example: Select sample-fp-policy as depicted below)

If you do not have a Policy, create one from New Policy and follow the procedure
Select Security Intelligence

- Select Networks

- Select the Feed you created in Create a feed that captures the DBL IP list (our example was ABTI_for_IP)

- Under Available Zones, select Any and click Add to Block List

- Click Save

- Click Deploy

Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the SamurAI Portal and we shall get it updated.
4.2.1.1.2 - McAfee Web Gateway (Skyhigh Secure Web Gateway) DBL Configuration Guide
Submit a ticket
To continue with this configuration guide you must first submit a ticket via the SamurAI Portal. Add the following information within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for McAfee Gateway device(s) |
| Description | Add hostname and IP address (internet facing) of your McAfee Gateway(s). For example: mysecureproxy1.acme.org, 19.16*.2*.2 If enrolling multiple gateways please add the information on individual lines.* |
Submit the ticket and you will hear back from us with additional information (e.g DBL URL’s) to continue with the configuration below.
Connection Requirements
You will need to ensure your Secure Web Gateway can reach a specific URL to obtain the DBL. This information will be provided to you once subscribed.
| Parameter | Note |
|---|---|
| Connection Port | TCP / 443 |
| URL DBL | NTT will provide a unique URL to you to download the DBL URL list |
| IP DBL | NTT will provide a unique URL to you to download the DBL IP list |
Table 1: Connections requirements
From your Secure Web Gateway:
Configure the External Lists Module
Follow the steps outlined within the Skyhigh Security documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_DBL |
| Data Source Type | Web Service |
| Web service’s URL | URL will be provided to you upon enablement of the add-on |
| Advanced Parameters - Maximum number of entries to fetch | 100000 |
| Advanced Parameters - Maximum size of data fetch in kb | 100000 |
Table 2: External Lists Module
Tip: To find out more information about External Lists refer to Skyhigh Security documentation About External Lists
Create a Rule
Follow the steps outlined within the Skyhigh Security documentation:
You need to configure a rule that denies access if the URL requested by the client matches the external list previously created.
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Rule Name | Whatever you want, however we suggest ‘Block URLS that match the NTT DBL’ |
| Enable Rule | Selected |
| Rule Criteria/Apply this rule | If the following criteria is matched |
| Rule Criteria Type | URL/Host criteria |
| Filter | URL |
| Selected Operator | is in list |
| Compare with | ExtLists, StringList (String, String, String) |
| Settings | Select your external list created in Configure the External Lists Module |
| Parameters Property “Exlists.String” | 1. Placeholder ${0} Data (String) |
| Action | Block |
| Settings | URL Blocked |
Table 3: Rule creation
Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the SamurAI Portal and we shall get it updated.
4.2.1.1.3 - Palo Alto Networks DBL Configuration Guide
Submit a ticket
To continue with this configuration guide you must first submit a ticket via the SamurAI Portal. Add the following information within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for Palo Alto Networks device(s) |
| Description | Add hostname and IP address (internet facing) of your Palo Alto Networks NGFW(s). For example: mysecureproxy1.acme.org, 19.16*.2*.2 If enrolling multiple gateways please add each gateway on individual lines.* |
Submit the ticket and you will hear back from us with additional information (e.g DBL URL) to continue with the configuration below.
Connection Requirements
You will need to ensure your Palo Alto Networks device(s) can reach a specific URL to obtain the DBL. This information will be provided to you once subscribed.
| Parameter | Note |
|---|---|
| Connection Port | TCP / 443 |
| DBL URL | NTT will provide a unique URL to you to download the DBL URL list |
Table 1: Connections requirements
To complete this configuration you will need to:
From your Palo Alto Networks device:
- Configure an External Dynamic List (EDL)
- Configure a URL Filtering Profile
- Configure security policy rule
Configure an External Dynamic List (EDL)
Follow the steps outlined within the Palo Alto Networks documentation:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest NTT_DBL |
| Type | URL List |
| Source | DBL URL will be provided to you upon enablement of the add-on |
| Certificate Profile | None |
| Check for updates | hourly |
Table 2: EDL Configuration
Tips:
- Select your specific PAN OS version when reviewing Palo Alto Networks documentation (we have linked version 10.2)
- To find out more information about EDL’s refer to Palo Alto Networks documentation External Dynamic Lists
- Once completed, follow the Palo Alto Networks documentation linked to y’Test Source URL’ to ensure the DBL can be accessed
Configure a URL Filtering Profile
Follow the steps outlined within the Palo Alto Networks documentation:
Use the following parameters for the EDL created in Configure an External Dynamic List when completing the steps:
| Field Name | Parameter |
|---|---|
| Profile Name | We suggested NTT_DBL |
| Site Access | Block |
| User Credential Submission | Block |
Table 3: URL filtering profile
Configure security policy rule
Follow the steps outlined within the Palo Alto Networks documentation:
Use the following parameters in the Actions tab when completing the steps:
| Field Name | Parameter |
|---|---|
| Profile Setting Type | Profiles |
| URL Filtering Profile | we suggested NTT_DBL |
| Log at Session Start | Disabled |
| Log at Session End | Enabled |
Table 4: Security policy rule
Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the SamurAI Portal and we shall get it updated.
4.2.1.1.4 - Squid DBL Configuration Guide
Refer to Squid Documentation as needed: http://www.squid-cache.org/
Submit a ticket
To continue with this configuration guide you must first submit a ticket via the SamurAI Portal. Add the following information within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for Squid device(s) |
| Description | Add hostname and IP address (internet facing) details of your Squid proxy(s). For example: mysecureproxy1.acme.org, 19.16*.2*.2. If enrolling multiple gateways please add each gateway on individual lines.* |
Submit the ticket and you will hear back from us with additional information (e.g DBL URL) to continue with the configuration below.
Connection Requirements
You will need to ensure your Squid proxy can reach a specific URL to obtain the DBL. This information will be provided to you once subscribed.
| Parameter | Note |
|---|---|
| Connection Port | TCP / 443 |
| URL DBL | NTT will provide a unique URL to you to download the DBL URL list |
| IP DBL | NTT will provide a unique URL to you to download the DBL IP list |
Table 1: Connections requirements
From your Squid Proxy:
Import the DBL
- Store the DBL list retrieval script as below:
/usr/local/squidList/getSquidACL.sh
- Back up the script file:
# cp /usr/local/squidList/getSquidACL.sh /usr/local/squidList/getSquidACL.sh.org
- Open the script file using your favorite editor. In the examples we use “vi” for editing
# vi /usr/local/squidList/getSquidACL.sh
- Set the DBL URL to import URL list.
(Example)DBL_URL="http://<IP address>/dbl/block_plain.txt"
- Set the DBL URL to import IP list.
(Example)DBL_IP="http://<IP address>/dbl/block_ip_plain.txt"
- Rewrite the reboot command to any command which used in production environment.
(Example)restart =/etc/rc.d/init.d/squid restart
- Set the place to output the URL list
(Example)DBL_URL_OUTPUT="/etc/squid/block_plain.txt"
- Set the place to output the IP list
(Example)DBL_IP_OUTPUT="/etc/squid/block_ip_plain.txt"
9.Save and close ”vi”
# :wq
- Give the execute permission to the script.
# chmod 775 /usr/local/squidList/getSquidACL.sh
ACL Configuration
- Edit the “squid.conf” file
# vi /etc/squid/squid.conf
- Add ACL setting for the list that set in steps 7 and 8 of the previous section.
(Example)acl blocklist_regex url_regex“/etc/squid/block_plain.txt”acl blockip dst “/etc/squid/block_ip_plain.txt”http_access deny blocklist_regexhttp_access deny blockip
- Save and close
# :wq
Confirm configuration and auto run
- Run the DBL retrieval script manually with the following command:
# /usr/local/squidList/getSquidACL.sh
After execution, check your standard Squid logs. If you receive an error, check the status of your network because it is highly likely that the DBL destination URL is not communicating.
- If there are no errors, set the execute command on Cron. (Following setting is run every 10 minutes.)
*/10 * * * * /usr/local/squidList/getSquidACL.sh
Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the SamurAI Portal and we shall get it updated.
4.2.1.1.5 - Zscaler Internet Access DBL Configuration Guide
Follow the steps below and then submit a ticket via the SamurAI Portal.
Access Requirements
Threat data will be pushed using the Zscaler native API with standard HTTPS TCP/443 to your Zscaler cloud instance.
From Zscaler Internet Access Portal:
Once completed you will need to provide specific information to NTT via a ticket in the SamurAI Portal.
Create a dedicated user with a specific role for NTT
Follow the steps outlined in Zscaler documentation to create an admin role:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTT_DBL |
| Enable Permissions for Executive Insights | disabled |
| Log Limit (Days) | 60 days |
| Dashboard Access | View Only |
| Reporting Access | Full |
| Insights Access | View Only |
| Policy Access | Full |
| Administrators Access | None |
| User Names | Obfuscated |
| Device Information | Obfuscated |
| Functional Scope | All options disabled (Advanced Settings, Data Loss Prevention, Security, SSL Policy, Virtual Service Edge Configuration, Firewall, DNAT, DNS & IPS, NSS Configuration, Partner Integration, Remote Assistance Management) |
| Access Control (Web and Mobile) | Enabled (Policy and Resource Management, Custom URL Category Management, Override Existing Categories, Tenant Profile Management) |
| Traffic Forwarding | Disabled |
| Authentication Configuration | Disabled |
Table 1: Admin role
Follow the steps outlined in Zscaler documentation to create a user and assign the role:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Login ID | Whatever you want, however we suggest: NTT_DBL |
| Name | Whatever you want, however we suggest: NTT Dynamic Block List |
| Role | The role previous created, we suggested*: NTT_DBL* |
| Status | Enable |
| Scope | As per your organization |
| Executive Insights App Access | Disabled |
| Comments | What you want |
| Security Updates | Disabled |
| Service Updates | Disabled |
| Product Updates | Disabled |
| Password Based Login | Enable (enter password) |
Table 2: Admin user
You will need to share these credentials when raising a ticket with us.
Provide your API base URL and API key
Review the Zscaler documentation to find your Base URL and API Key:
You can also read more information about the Zscaler API at:
You will need this information when raising a ticket with us.
Create a dedicated URL category for the DBL:
Follow the Zscaler documentation:
You need to create two URL categories. Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTT_Block |
| URL Super Category | User-Defined |
| Administrator Operational Scope | Any |
| Custom URLs | example.com (this entry will be removed in the first DBL list retrieval as one value is mandatory for creation) |
Table 3: Custom URL category 1
| Field Name | Parameter |
|---|---|
| Name | Whatever you want, however we suggest: NTT_Notify |
| URL Super Category | User-Defined |
| Administrator Operational Scope | Any |
| Custom URLs | example.com (this entry will be removed in the first DBL list retrieval as one value is mandatory for creation) |
Table 4: Custom URL category 2
Configure URL and Cloud App control
Follow the steps outlined in Zscaler documentation:
Use the following applicable parameters when completing the steps (set other parameters according to your specific configuration):
| Field Name | Parameter |
|---|---|
| Rule Order | 1 (Recommended) |
| Rule Name | Whatever you want, however we suggest: NTT DBL |
| URL Category | Select the previously created categories, we suggested NTT_Block & NTT_Notify |
| Protocol | DNS Over HTTPS, FTP Over HTTP, HTTP, HTTPS, HTTP Proxy, SSL, Tunnel and Tunnel SSL |
| Action | Block |
Table 5: URL filtering policy
Configure Monthly Reporting
To enable improvements of DBL we recommend that you schedule monthly reports that are automatically emailed to us.
Follow the steps in the Zscaler documentation, Refer to Copying a Standard Report:
Select the Blocked Web Traffic Overview under Standard Reports - Web Activity to copy
| Field Name | Parameter |
|---|---|
| Report Name | Anything you want, however we recommend ‘NTT_DBL_MonthlyReport’ |
| Time Frame | Previous Month |
Table 6: Copy Report
Follow the steps in Zscaler documentation to Schedule the Report:
Use the following parameters when completing the steps:
| Field Name | Parameter |
|---|---|
| Schedule Name | Whatever you want, however we suggest: NTT_MonthlyReport_Schedule |
| Report | Report previously created, we recommended ‘NTT_DBL_MonthlyReport’ |
| Recipients | dbl-support@security.ntt |
| Status | Enabled |
| Frequency | Monthly |
| Time zone | Asia/Tokyo |
Table 7: Scheduled Report
Submit a ticket
Now that you have completed all of the steps above you must now submit a ticket via the SamurAI Portal. Add the following information (created from the steps above) within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for Zscaler Internet Access |
| Description |
|
Submit the ticket and you will hear back from us when onboarding is complete.
Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the SamurAI Portal and we shall get it updated.
4.3 - Consulting and Supplemental Services
4.3.1 - Data Discovery Service Description
1. Introduction
The SamurAI Data-discovery service is a service package designed to enhance client visibility on internal IT-architecture, data flows and security posture. Through a series of workshops, interviews and reports with concrete next-step recommendations, NTT experts will help the client identify the data that’s most important to their business goals, review projects that may affect said data and recommend next-steps based on best-practices.
This service is intended for new NTT SamurAI MDR clients however it can be used for clients who wish to expand or review an existing commitment.
2. Data-discovery service
2.1 Service features
The Data-discovery service is delivered in two phases. If extended support is required to fulfill the engagement scope, the service can be expanded accordingly. For more info see section 2.2 Service Package.
Phase One:
The initial phase includes an internal workshop to walk-through the client IT-environment, security posture, project roadmap, planned initiatives and any other potential future organizational/infrastructure changes.
NTT Consultants will support the client in identifying the data that´s most important to the client business and operation. The phase will be concluded with the delivery of concrete next-step recommendations tailored to the client desired future security posture, roadmap and samurai enrollment strategy in the form of a report.
Phase Two:
The second phase is initiated six months post the initial phase, during which the client and NTT Consultants review the report from the first phase, progress on next-step action plan, new projects and changes to the IT-environment.
The second phase will be concluded with the delivery of an updated version of the initial report.
2.1.1 First Phase Deliverables
- Initial workshop report containing:
- Identified critical data elements and associated security controls.
- Identified potential impact of internal projects and initiatives on critical data infrastructure.
- If applicable, discuss security impact of potential organizational changes.
- Recommendations based on best practices given the information provided by the customer.
2.1.2 Second Phase Deliverables
- Six-month update report:
- Impact of eventual changes in the environment.
- New projects and IT-environment updates.
- Recommendations based on best practices given the information provided by the customer.
2.2 Service package
The Data discovery service, as defined above, is a fixed fee engagement. Additional service packages can be purchased to extend delivery.
Initial workshop and associated activities will not exceed 60 hours. Six-month follow-up and associated activities will not exceed 40 hours.
Delivery of the report associated with each portion of the service will constitute the closure of that portion.
4.3.2 - Incident Response Retainer Service Description
1. Introduction
With the rise of cyber-attacks in a fluid threat landscape an organization must quickly respond and be prepared to act on all threats. The ability to quickly respond to a security incident is crucial for limiting the impact of the attack, minimizing reputational damages and legal consequences.
In many cases, the damage from a cyber related incident is increased due to delays and mistakes in incident handling. Incident response is a highly specialized field that requires staffing by specialists who are engaged full-time in this area. It is likely to not be as successful when staffed by employees who only perform incident response tasks on an ad hoc basis. As a result, many organizations do not employ their own internal incident response team, but rather contract with external providers such as NTT.
NTT provides Incident Response (IR) Retainer services to assist organizations to effectively respond and rapidly remediate in the event of an incident. The NTT IR Team is experienced in handling incidents across various business verticals and provides a valuable resource to clients. The retainer service is offered as an add-on to NTT’s SamurAI MDR service and also as a standalone offering for either emergency incident response needs, or proactive risk mitigation.
2. SamurAI Incident Response
2.1 Service Features
The SamurAI Incident Response (IR) Retainer provides incident management, containment, and root cause analysis support to assist with mitigation of incidents. The NTT IR team consists of experienced Security Analysts in the NTT Security Operations Centre (SOC) and Incident Response consultancy experts, and is delivered through the SamurAI platform.
The Incident response offering provides a set of components which can provide the Client with:
- On call 24/7/365 response to incidents
- Incident lead and incident management
- Root cause analysis, containment, and eradication
- Rapid remote deployment of IR tools
- Integration with NTT’s Global Threat Intelligence Center (GTIC)
- Close collaboration with client teams
- Decades of experience in Security Monitoring and IR subjects
- Support during extended incidents
- Malware and threat behavior analysis
- Advanced Network Analysis Tools
These service components are not an exhaustive list and are provided as required during the engagement.
The IR retainer is based on an annual entitlement of 40 hours, which can be increased by the client through the purchase of additional retainer blocks of hours.
2.1.1 Incident lead and incident management
The NTT IR team will support the client by providing both hands-on and high-level incident lead and incident management, steering both NTT, client, and other involved 3rd party resources towards a common goal by assigning and prioritizing tasks, organizing meetings, risk evaluation and prioritization, damage evaluation, as well as providing stakeholder updates.
The NTT IR team will work together with the client to align reporting cadence, timelines, and updates in accordance with client requirements.
2.1.2 Root cause analysis, containment and eradication
The NTT IR team will support the incident investigation to understand the who, what, when, where, why and how of an attack. This includes:
- Review and analysis of client provided log, network, and endpoint telemetry.
- Assess the flow and history of incidents in the client’s environment to evaluate potentially related issues, campaigns, and persistence.
- Threat Intelligence, Open-Source Intelligence (OSINT), and closed source correlation.
- Providing insight and best practice guidelines on how to limit potential damage of an incident.
- Providing client’s security staff guidance on how to handle and execute the eradication process. This will be positioned from a governance approach and will guide the client’s internal security staff.
- Evaluating the possible recovery options and provide guidance to client security staff to restore affected systems from a backup or re-image the systems from a clean gold image, if applicable.
2.1.3 Rapid remote deployment of IR tools
Where the client does not have Endpoint Detection and Response (EDR) agents or a similar capability in place, NTT will work with the client to deploy EDR tools. The EDR tooling can be integrated with SamurAI and will be available to the client during the incident response engagement.
On completion of the incident response engagement, the client will have the option to purchase the EDR tooling and retain this tooling in the client environment. If the client decides not to purchase EDR tooling used by NTT for the purpose of incident response, it must be removed at the end of the incident response engagement.
2.1.4 Integration with NTT’s Global Threat Intelligence Center (GTIC)
Through the NTT Incident response service, clients benefit from extensive Threat Intelligence both curated and produced by Threat Intelligence researchers in NTT’s Global Threat Intelligence Centre (GTIC) via SamurAI.
2.1.5 Highly collaborative with client teams
The management of an investigation is just as important as the technical and investigative skills brought to bear during an incident. NTT IR team will work closely with the client team to provide detailed and structured status reports to communicate findings that will aid in making informed business decisions.
The frequency of status reports and interaction between NTT resources and client team will be adjusted to reflect the current requirements during the incident lifecycle.
2.1.6 Malware and threat behavior analysis
Malware is a name used for various malicious software variants, such as viruses, ransomware, spyware, etc. and is designed to infiltrate and damage computer environments and its data without knowledge of the user. Understanding malware and its behavior, is critical to an organization’s ability to respond to incidents, derive threat intelligence and boost defenses. NTT offers the knowledge and experience on how to identify key aspects and characteristics of various malware types and to understand the extent of the potential damage.
All identified Indicators of Compromise (IoCs) related to the malware or threat are shared with the client’s security team as part of the engagement.
2.1.7 Advanced network analysis tool
At times NTT IR team may recommend the deployment of advanced networking analysis tools to assist with the identification and mitigation of an incident. NTT IR team will discuss this in detail prior to authorization of its use.
These tools can be used to support the detection of behaviors that make endpoints act maliciously or outside of their normal mode of operation. They can help determine what changes occurred during a malware outbreak so that proper remediation can be planned. The tools can also track lateral movement of malware and determine how widespread it is across the entire network.
2.2 Retainer information
The SamurAI Incident Response offering is provided as a retainer and includes 40 hours per year. If the Client requires additional Incident Response beyond 40 hours per year, additional retainers of 40 hours can be purchased.
Retainer hours are consumed in 4-hour increments.
3. Onboarding
As part of NTT´s proactive engagement to enhance the Incident response teams ability to respond promptly and efficiently, NTT will meet with the client to establish knowledge about the client’s current setup, introduce the workflow of incident response engagements, how the client can initialize incident engagements and open up for questions from both parties.
The following details will be collected during the introduction call:
- Client points of contact
- Contacts allowed to activate IR-service
- EDR coverage in environment
The collected details will create a foundation for successful incident handling and a more seamless collaboration. Once the onboarding meeting has taken place and the basic requirements, such as accesses and points of contact, are in place the Incident Response Retainer can be started.
No onboarding meeting is provided when an Incident Response Retainer has been procured and activated for emergency incident response assistance. For emergency IR cases, onboarding will be done in parallel to the incident scoping call done as outlined in section 4.2.
The graphic below outlines the onboarding process:

4. Service activation
4.1 Incident response activation
MDR Client
If the cause for activation is an incident escalation from the MDR Service SOC, the customer should activate the IR-retainer directly via a request in the associated incident ticket within the SamurAI Portal.
The IR retainer may also be activated via a phone call to the Incident response on-call number which is provided during onboarding. The IR retainer can only be activated by an authorized list of individuals mandated by the client. This information is captured during the onboarding process but is naturally subject to change. Any changes to the authorization list must be communicated to the NTT IR team.
Standalone Client
The IR retainer is activated via a phone call to the Incident response on-call number which is provided during onboarding. The IR retainer can only be activated by an authorized list of individuals mandated by the client. This information is captured during the onboarding process but is naturally subject to change. Any changes to the authorization list must be communicated to the NTT IR team.
Emergency Client
The IR retainer is procured and activated via a phone call to the 24/7 Emergency Incident response on-call number.
4.2 Incident scoping call
Depending on the incident severity, magnitude, urgency and known context, the NTT IR team will initiate the engagement with a scoping call. During the call, NTT and the Client’s security team will work together as one team, to gain an understanding of the current situation and how to best proceed.
NTT will meet with the POC and designated Incident Response Team members to discuss the How, What, When and Where questions. Typical questions will include - How was the issue detected? Is there any evidence, data or logs related to the incident in SamurAI? What other telemetry is available outside of SamurAI? What steps have been taken? What does the environment look like, where are the egress and ingress points located?
Other discussion topics may include the gathering of additional evidence, such as providing audit log records or a network diagram showing what other devices on the network that the suspicious system has access to. The more telemetry available, the faster questions can be answered during an investigation. It is very critical for the client to document all actions taken on the suspected systems at the start of an incident. If incorrect or unknown steps are taken to clean up an infected system, block lateral movement or remediate other issues it may hinder or complicate response actions or root cause analysis at a later stage.
4.3 Engagement objectives
The NTT IR team will work together with the client POC at the time of the retainer activation to identify the immediate engagement objectives. As the incident lifecycle progresses and new evidence or information is discovered, the engagement objectives may be updated. The objectives may be to identify data loss, attack vectors or to recover from the incident and provide recommendations on actions to take to prevent the incident from repeating. NTT IR team can perform incident management, by providing remote support and coordinate with security staff to assist with incident mitigation, containment, eradication, recovery, and reporting.
The end delivery to the client will be a written report of our findings which includes:
- Executive Summary
- Overview
- Timeline of Activity
- Summary of Findings
- Recommendations
4.4 Engagement lifecycle
The figure below describes the process followed by the NTT Incident Response Team during engagements.

5. Service Provisions and Requirements
In order to ensure successful delivery of the Services, NTT and Client shall provide the following, as applicable.
- NTT personnel will maintain and track hours utilized against the retainer.
- Depending on the scope requested by the client, NTT will assign a Lead Incident manager to work with client’s main Point of Contact (POC) throughout the life of the engagement.
- NTT will assign an IR Manager to be available to client as an out-of-band resource for issue escalation.
- NTT will provide the client with ongoing status reports, as mutually defined in the project kick-off.
- If not otherwise stated above, upon completion of the Incident response engagement, NTT will provide client with a detailed report in PDF format, describing the actions performed, results and recommendations.
- Client will assign a main Point of Contact (POC) to work with NTT and will provide knowledgeable technical and administrative staff to assist NTT.
- As required, client will provide NTT with access to their network to perform Incident response services. If required client will also provide NTT with a list of areas considered “off limits”.
- Client understands NTT is not responsible for loss of business incurred by Client (or third parties associated with client), due to the performance of Services.
- As applicable, client will provide NTT with electronic copies of any applicable policies (e.g., Security Policy, Acceptable Use, Policy, Incident Response Plan, Escalation Trees, etc.), procedures, previous audits or assessments, network diagrams, configurations, evidence, and any other relevant materials (Engagement Information) associated with the Services outlined in this Service Description.
- Client explicitly understands Services may employ methods which could violate client’s policies. NTT will agree, together with the client on any actions which may violate said policies prior to taking the action.
- Client fully agrees that providing Engagement Information to NTT is not a violation of client’s policies and fully agrees not to instigate any type of prosecution against NTT, or NTT employees or third-party service providers, for the receipt and storage of such Engagement Information.
- If the in-scope environment for Services provided in this Service Description is hosted by a third-party provider, client agrees to notify the third-party provider in advance of the initiation of services and client accepts the responsibility for complying with any provisions set forth by the third-party provider.
- Should this Service Description be executed in a context where regulatory compliance, auditing, testing or assessment or other similar compliance advisory consulting services, for example under the PCI Data Security Standard or HIPAA Privacy, Security or Breach Notification Rules apply, client understands that NTT Incident response services do not constitute any guarantee or assurance that security of client’s systems, meets regulatory requirements. Furthermore, NTT is not responsible for updating its reports and assessments or inquiring as to the occurrence or absence of such in light of subsequent changes to client’s systems, networks and assets after the date of NTT´s final report absent a signed Statement of Work, or an amendment to a Statement of Work, expressly requiring the same.
- Client understands that failure to fulfil Service Requirements or provide required documentation/evidence on a timely basis can result in delay of Services or loss of contracted hours.
- If regulatory changes (e.g., changes by a regulatory agency, legislative body, or court of competent jurisdiction) require NTT to modify the Services described herein, client agrees in good faith to work with NTT to amend the scope of work accordingly.
- Upon initial client contact, NTT will respond within 2 hours.
- Client must enroll NTT IR personnel to its SamurAI tenant as required.
- Client understands that NTT Incident Response services do not constitute any guarantee or assurance that security of client’s systems, networks and assets cannot be breached or are not at risk.
4.3.3 - SamurAI Cybersecurity Advisor Service Description
1. Introduction
The SamurAI Cybersecurity Advisor (CSA) service add-on provides a dedicated technical senior-level resource to help SamurAI Managed Detection & Response (MDR) clients get the most value from the service, and reduce business risk.
Services provided by the CSA include:
- Monthly threat reviews
- Tracking of a detection and response recommendation improvement list
- Dialogues around detection & emerging threats
- Acting as a link between clients and the SamurAI MDR service
2. SamurAI Cybersecurity Advisor service
2.1 Monthly Threat Reviews
The SamurAI MDR service will detect, respond and report relevant threats that pose a risk to a client, but it is the client’s responsibility to bring the risk to closure. To help the client with this, a program of monthly threat reviews is included with the CSA service.
The monthly threat reviews are the main interaction point between clients and the CSA.
Through regular CSA-led threat reviews, clients will:
- be trained and educated to understand threats and risks reported by the SamurAI MDR service,
- be provided recommendations to improve detection and response, and
- receive follow-up to ensure that reported threats and risks are handled and mitigated.
The threat review program is initiated at the time of onboarding. During the onboarding orientation call the monthly meetings will be scheduled for the remainder of the contract period.
2.2 Detection and Response Recommendation Improvement List
The CSA will maintain and update a detection and response improvement list through the entire lifecycle of the SamurAI MDR service. The improvement list focuses on suggestions that will improve detection of threats e.g. new systems recommended to be onboarded by the client into the SamurAI MDR service, or could also include actions that either the client, the SOC or NTT Security Holdings need to take in relation to improving threat detection and response. The ultimate benefit of this process to the client is an improved security posture.
2.3 Detection & Emerging Threats
The CSA will stay informed of threat detection improvements made by NTT and follow the changing threat landscape. During the monthly threat review meetings, the CSA will lead a dialogue with the client to ensure the correct telemetry exists within the clients given SamurAI MDR configuration to take full benefit of any new detections created for emerging threats, and provide actionable recommendations where needed.
2.4 Act as a link between clients and the SamurAI MDR service
The CSA is a technical senior-level resource with extensive experience working within Managed Detection & Response. Complimenting the CSA’s extensive experience with the SamurAI MDR service, the CSA also has access to NTT threat intelligence, the specialist MDR SOC workbench, and the client’s MDR tenant.
This access provides the CSA the ability to perform searches and threat hunts as required within the scope of the service offered, while also having well-established contact routes with the different NTT Teams involved in the SamurAI MDR delivery.
2.5 Scope information
The SamurAI Cybersecurity Advisor Service add-on, as defined above, is a fixed fee engagement. The engagement will not exceed 192 hours yearly, and additional service packages can be purchased to extend delivery. Used hours per single month may not exceed 40 hours unless approved in dialogue with NTT.
The CSA service is delivered during business hours of central European time (CET).
4.3.4 - SamurAI Onboarding Service Description
1. Introduction
The SamurAI Onboarding service add-on is designed to support the client journey during the transition onto the SamurAI Managed Detection and Response (MDR) service. NTT personnel will through an initial workshop and subsequent interaction answer any questions and provide all the necessary documentation and information required to enroll to SamurAI MDR.
This service is intended for new NTT SamurAI MDR clients however it can be used for clients who wish to expand or review an existing commitment.
2. SamurAI Onboarding service
2.1 Service Features
Core service activities:
- Initial workshop to define devices and/or services in scope of enrollment to SamurAI
- Supply and walk through of SamurAI documentation and general information
- Service onboarding support
- Dependant on requirements this may include:
- Collector configuration and setup
- Integration configuration
- SamurAI Network Traffic Analyzer deployment and configuration
- Dependant on requirements this may include:
- Service verification post-onboarding
- General support and inquiries regarding device and 3rd party service support
Core service deliverables:
- Onboarding plan
- Onboarding guides relevant for the customers environment
- Portal training session.
- Initial kick-off session, not to exceed 1 full day
- Support during the transition
2.2 Scope information
- The SamurAI Onboarding service add-on, as defined above, is a fixed fee engagement. The engagement will not exceed 60 hours and additional service packages can be purchased to extend delivery.
4.3.5 - Table-Top Exercise Service Description
1. Introduction
When dealing with incidents, crisis, or disasters, one of the most imperative steps in the plan is to be properly prepared. Preparation plays a major part of incident handling as it enables organizations to improve efficiency of decision making in the heat of the moment during an attack, which leads to quicker recovery, minimizing impact and costs. It is also key for incident handlers to be able to act confidently and reduce the risk of making mistakes when carrying out their work throughout an incident.
One way to prepare for an incident and evaluate the documentation, processes and preparedness of the client’s participants is to carry out a Table-Top exercise with the goal of working through the scenario, with an open discussion in a collaborative low-stress environment.
The output of the exercise is to develop the incident response capabilities. After the Table-Top exercise the participants will have gained an understanding for what their strengths and weaknesses are in terms of handling an incident properly, be able to update their documentation, revise their processes and train their personnel to enhance their incident response capabilities.
2. Table-Top Exercise
2.1 Visual Overview

2.2 Objectives
The exercise is conducted with the goal of improving client incident response readiness by evaluating processes, routines and documentation.
On a high level the objective is achieved through having the client’s participants test the incident response process in a “safe” environment without stress and through giving a detailed report which highlights points of improvements in the process.
Aim to have an answer to questions such as:
- Are there pre-defined roles and responsibilities and is the coverage sufficient for the incident scenario?
- Did the staff assigned to the roles have all permissions and privileges to handle the incident in a satisfactory fashion?
- Are the points of escalation and contacts documented and defined?
- When to isolate hosts on a network
2.3 Plan & Prepare
NTT will set up an initial meeting with the client to decide on suitable exercise scenarios based on the client’s wishes and NTT experts’ 20+ years of Threat Intelligence experience. The goal is to have a scenario tailored to be relevant to the client’s environment and needs, while revolving around handling incidents such as:
- Threat actors’ intrusions to deploy ransomware or steal intellectual property
- Nation-state attacks
- Insider-threats
- Successful phishing attempts
- User executing malware on corporate device
Where technical emphasis can be put on specific areas, for example:
- Workstations
- Domain-controllers
- Email-servers
- ICS/OT
- Office 365
- Cloud infrastructure
After the scoping call NTT will produce the material necessary for the scenario walkthrough.
2.4 Exercise Session
The Table-Top exercise is designed to fundamentally test the processes and routines that together are the basis for the incident response capability.
NTT experts will lead the client’s participants through the scenario, enable conversations to identify potential gaps in processes and documentation, helping to achieve an understanding of their respective strengths and weaknesses in the context of incident response. Taking the incident step by step, our consultant will walk you through the events as they unfold depending on your own incident response actions and detection capabilities.
The client’s participants will get time to discuss amongst themselves without NTT interaction to find their own genuine course of action if this were to be outside of a simulation. During the time of the scenario taking place, NTT experts will document and map out the decision making, points of escalation and threat hunting processes of the client’s participants.
2.5 Report
The reporting covers the scenario setup and walkthrough, in detail, to bring visibility to the incident response process in action during the specific engagement scenario, complete with an incident response checklist.
Analyzing the events, processes and decisions with the expertise of NTT personnel with the result of getting actionable points of improvement for the process and routines.
Moreover, comparing the incident response capability and process in the scenarios to established industry frameworks that are relevant for the scenario ensuring a benchmark to compare to global industry standards, for example, NIST 800-61 or MITRE ATT&CK.
The report can also be used to have a detailed look into how the process and routine of incident response can play out in a real-world scenario.
2.6 Scope information & Requirements
2.6.1 Requirements
NTT will require participants in the scenario session that own relevant functions within the incident response process, moreover the participants will have mandate to help choose relevant scenarios for the client’s purposes.
NTT will require an overview of the IT environment, e.g., what OS is running on endpoints, servers, geographical split of sites, high value assets, documented incident response process routine, relevant documentation and lastly, what are some of your currently known pain points that you wish to address and improve.
2.6.2 Scope Information
A standard Table-Top exercise is a fixed fee engagement that will not exceed 80 hours. An estimation of the distribution of effort is as follows for each step of the engagement:
| Activity | Estimation (days) |
|---|---|
| Preparations ahead of Tabletop | Six (6) |
| Tabletop exercise | One (1) |
| Produce a Single (1) deliverable report at the completion of the engagement | Three (3) |
| Total | Ten (10) |
For client’s that require a Table-Top exercise that goes beyond a standard scope of service (eg. extensive custom scenario use-cases, groups of participants, longer expected duration), a custom engagement can be scoped by the NTT team to accommodate as required.
Table-Top exercises are delivered remotely during business hours of central European time (CET).
4.4 - Superseded Documents
4.4.1 - Superseded Managed Detection & Response Service Descriptions
4.4.1.1 - Managed Detection & Response (MDR) Service Description (v2.0 2025-05-01)
This document has been superseded. For the latest version please click HERE.
1. Introduction
NTT’s Managed Detection and Response service builds on the capabilities of the Samurai platform to provide a Managed Detection and Response service which delivers cybersecurity insights, advanced threat detection, response, and protection capabilities via the ingestion of varied telemetry sources including cloud, network, compute and mobility sources. Supported telemetry combined with our proprietary Advanced Analytics, analyst threat hunting, and AI-based threat detection capabilities translate to faster, more accurate detections and most importantly reduced business risk.
NTT’s Managed Detection and Response service offers the sophisticated threat detection capabilities of the Samurai platform along with, 24/7 threat monitoring, analyst-driven threat hunting, and comprehensive threat intelligence delivered by NTT’s Global Threat Intelligence Center. By combining the advanced analytics capability of the Samurai platform with the expertise of the skilled analysts in the NTT SOC, threats are identified and separated from a large number of false positives typically generated by security technologies.
Managed Detection and Response is a service that utilises security alerts along with relevant contextual information identified by the Samurai platform. This information is analysed by a skilled Security Analyst, who engages in threat hunting and validation activities to verify the threat, its impact, and to identify additional information associated with a potential breach. Once the threat is validated, the Security Analyst creates a detailed Security Incident Report for the Client. The Security Incident Report includes a detailed description of the security incident combined with scenario-specific actionable response recommendations. This significantly assists in reducing the time taken for informed responsive measures, thereby, lowering associated risks.
2. Service Elements
Samurai Managed Detection and Response provides the Client with a service overlay which provides advanced detection and response capabilities delivered by skilled Security Analysts in the NTT Security Operations Center, leveraging the Samurai platform. The Samurai Managed Detection and Response service provides a set of components which provide the Client with:
- Onboarding guidance
- Access to SOC Analysts
- Threat Intelligence
- Threat Detection and Investigation
- Threat Hunting
- Security Incident Reports
- Threat Response
- Service Management Portal and Service Reporting
- Incident Response
- Service Assurance through regular Threat Reviews
3. Onboarding
Onboarding of the Managed Detection and Response service commences with the activation of the Client’s Samurai tenant. Activation of the Client’s tenant will provide the Client with a link to online documentation and the access and instructions required in order to integrate with the Samurai platform. This includes:
- Deploying Local Collector appliances;
- Connecting telemetry sources (including logs, enrichment and other data sources); and;
- Configuring integrations to client applications such as Endpoint Detection and Response, network security controls and other cloud-based platforms.
Within two business days of activation, NTT will host a Managed Detection and Response introductory conference call with the Client. This meeting will explain the onboarding process and will include an overview of the SamurAI Portal and configuration steps to be completed by the Client. Follow-up progress calls may be scheduled to ensure setup progress and status.
Within fourteen days of activation a Samurai MDR orientation conference call will be held with the Client which upon completion, Service Delivery will begin. This meeting will outline what to expect from the service including how SOC analysts will interact with the Client, overview of Security Incident Reports and how to utilize the Samurai MDR.
For more details please visit the Samurai MDR Onboarding Guide.
4. Service Features
Samurai Managed Detection and Response provides the following service features:
4.1 Threat Detection
The Samurai platform detects threats and suspicious behavior using the Samurai AI Engine. The AI Engine makes use of a combination of traditional threat detection techniques, Advanced Analytics, machine learning and Threat Intelligence to detect sophisticated threats. To ensure service quality, NTT continuously makes detection-tuning decisions based on the validity and relevance of alerts and security incidents.
4.2 Threat Intelligence
The Global Threat Intelligence Center delivers Threat Intelligence, which enhances the Managed Detection and Response service. Additionally, the Managed Detection and Response service includes continuous Threat Intelligence updates driven by investigations of security incidents.
4.3 Dynamic Blocklist
The Dynamic Blocklist feature provides a real-time feed of curated Indicators of Compromise. The Client can configure supported devices, such as next generation firewalls and internet proxies, to receive the dynamic list to proactively block threats. IoCs are added to the Dynamic Blocklist on an ongoing basis. The Dynamic Blocklist option is available at no additional charge. Additional details can be found in the Dynamic Blocklist overview.
4.4 24/7 Security Analyst Interaction
The Managed Detection and Response service includes detailed security investigation of alerts detected via Samurai by Security Analysts in NTT’s SOC. Investigation includes threat analysis and threat hunting activities across the Client’s telemetry environment to provide validation and assessment of the malicious nature of a threat and its potential impact.
Security Analysts use the MITRE ATT&CK framework as a reference model in presenting the nature of a threat and assigning appropriate severity to identified security incidents.
The Managed Detection and Response service also provides validation of threats through vendor integration and evidence collection for selected security technologies, such as packet capture data (PCAP) and malware execution reports.
4.5 Investigations
When the Samurai platform generates an alert indicating a potential threat, a SOC Analyst will begin an investigation. The investigation includes validating the presence of a threat via client telemetry and evidence data, threat intelligence, and other data and information sources within the Samurai platform. Using this information and automation capabilities of the Samurai platform, the analyst then determines the nature and extent of any compromise which may have occurred. Depending on the nature of the potential threat, activities conducted during the process of the investigation may include:
- Threat analysis.
- Threat hunting across the Client’s telemetry data which has been ingested into the Samurai platform.
- Assessment of the malicious nature of a threat and its potential impact.
- Contextualisation of validated threats based on factors such as industry vertical and geopolitical context.
- Categorisation according to industry best practice frameworks including MITRE ATT&CK.
- Forensic analysis of telemetry data stored in the Samurai platform.
- Malware analysis; and
- Recommendation to the Client of a suggested response covering suggested next steps.
4.6 Security Incident Reports
If, as a result of an investigation, a threat is identified, the Security Analyst creates a Security Incident Report detailing the cybersecurity incident, including plain-language observations and incident mitigation and/or remediation recommendations.
Client notifications can be provided by phone or email based on severity:
- Critical severity; Phone / E-mail notifications.
- Low, Medium, High severity; E-mail notifications.
Clients requiring Phone notifications must provide NTT with a prioritized list of Client contacts.
4.7 Threat Hunting
Utilizing Client telemetry and evidence data, NTT will perform Threat Hunting to detect activities such as persistence mechanisms, application usage, network activity or the tactics and techniques and procedures (“TTPs”) of threat actors. When a threat is detected, a security analyst will create a security incident and notify the Client.
4.8 Threat Response
NTT can perform actions on the Client’s behalf when an investigation results in the detection of a threat.
NTT will take actions to isolate compromised/malicious host Endpoints following Security Analyst incident validation. Remote isolation actions are performed using the isolation capabilities of the Client’s Endpoint Detection and Response (EDR) technology.
4.9 SamurAI Portal
Managed Detection and Response Clients have access to the SamurAI Portal, including self service features such as telemetry integration and collector configuration. Details of the functionality can be found in Samurai online documentation.
In addition to the SamurAI Portal, Samurai Managed Detection and Response provides the client with access to the Samurai Help Center, which provides online access to:
- interact with us online by logging incidents and requests;
- view security incident reports;
- track, view and submit comments within incident and request tickets; and
- browse / search our knowledge base which contains online documentation for the Samurai MDR service and application.
Additional information regarding support can be found in our Support Policy.
4.10 Incident Response
The Incident Response add-on is a retainer which the Client may choose to utilize if the Client requires the NTT SOC to perform additional threat investigation activities. Clients can continue to leverage the services of the NTT SOC in instances where the severity of an incident justifies additional effort to perform tasks such as threat hunting, malware analysis or forensic analysis of data in the Samurai platform.
This add-on provides the Client with the facility of additional post root-cause analysis to assist with containment of a threat.
The Incident Response retainer includes 40 hours per year. If the Client requires additional Incident Response beyond 40 hours, additional retainers of 40 hours can be purchased.
Incident Response effectiveness is enhanced with an installed and supported endpoint agent. If the client does not have a supported agent, NTT will work with the client to provision endpoint agents to support the investigation. For more information please read the detailed description of the Incident Response add-on.
4.11 Threat Reviews
Through a program of scheduled quarterly meetings, Threat Reviews will be conducted with the Client to derive maximum value from Samurai MDR.
Topics covered in the quarterly meetings include:
- Review service health.
- Review security incidents and how they provide insights into the Client’s security posture and attack surface; and
- Advising the Client regarding configuration of Samurai to better meet the Client’s needs.
For clients that require a dedicated resource and monthly threat reviews, the Samurai Cybersecurity Advisor subscription is available as a chargeable add-on.
5. Client Responsibilities
Client is required to perform the following obligations below:
assign a primary Point of Contact (POC) to work with NTT. Client will ensure that NTT’s records of all Client POCs are kept up to date and are accurate.
ensure that all telemetry sources have connectivity required in order to interact with the Samurai platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data and the ability as well as the ability to monitor and control any agents or virtual appliances installed in Client’s environment for the purpose of providing the service.
ensure that endpoints falling under the scope of Samurai MDR have a supported endpoint agent installed in order to facilitate the gathering of telemetry and evidence data as well as providing the ability to perform remote isolation.
provide knowledgeable technical staff and/or third-party resources to perform any configurations or software installations required in order for Client to consume the service. This includes, but is not limited to:
- Configuration of connectivity.
- Installation of Local Collector virtual appliances.
- Provision of IP addressing required for any virtual appliances required in Client’s network; and
- Configurations of cloud services required in order for the Samurai platformto receive telemetry from these services.
perform all aspects of Service Onboarding, including the configuration of telemetry sources and configuration of Collectors to provide telemetry feeds to the Samurai platform. Client will ensure that all source devices are compliant with the Samurai platform configuration requirements and are running supported software and/or hardware versions.
ensure that it does not utilise any technologies or configurations which block traffic, rotate logs or in any other way impede delivery of the service.
procure all maintenance, support and licensing agreements with third-party vendors for all telemetry sources.
comply with all the relevant data privacy, regulatory, and administrative laws, policies and procedures related to monitoring user traffic and communications.
bring a threat, identified in a security incident report, to closure.
Failure to provide any of the service requirement information on a timely basis can result in delays in Service Onboarding and Service Delivery by NTT and NTT shall not be liable for any consequences of such delays.
6. Service Level Agreements
The Service Level Agreements (SLAs) listed in this section will become active once Onboarding of the Client is considered complete.
6.1 Availability
The Availability SLA is determined by the ability of the Client to access the Samurai MDR platform. This is measured by the ability of the Client to log into the SamurAI Portal.
NTT will use reasonable commercial means to ensure an availability of the SamurAI Portal of at least 99.9%. If the availability of the platform drops below this level, the Client may claim a Service Level Credit as set out in the table below:
| Application Availability | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| 99.9% - 100.0% | 0% |
| 95.0% - 99.9% | 1% |
| Less than 95% | 10% |
6.2 Validated Security Incident Notification
NTT will analyze alerts and related available data sources on a 24/7 basis for signs of malicious activity which has bypassed preventative security controls.
If malicious activity is confirmed, NTT will determine the severity of the threat. For Security Incidents with a severity of high or critical NTT will provide an Incident Report within 30 minutes of determining the severity.
For Security Incidents with a severity of low or medium, NTT will endeavor to provide an Incident Report within 120 minutes of determining the severity.
If the creation of a security incident report in relation to an incident with a severity of high or critical takes longer than 30 minutes, the Client may claim a Service Level Credit as set out in the table below:
| Time taken to create a security incident report | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| Less than 30 minutes | 0% |
| 31 to 300 minutes | 1% |
| Over 300 minutes | 5% |
A Client may make a maximum of 1 claim against this service level per calendar day and per security incident.
6.3 Receiving Service Credits
To receive a Service Credit, the Client must open a ticket via the SamurAI Portal within 30 days of the incident for which the Client is claiming a Service Level Credit.
4.4.1.2 - Managed Detection & Response (MDR) Service Description (v1.0 2023-09-11)
This document has been superseded. For the latest version please click HERE.
1. Introduction
NTT’s Managed Detection and Response service builds on the capabilities of Samurai XDR to provide a Managed Detection and Response service which delivers cybersecurity insights, advanced threat detection, response, and protection capabilities via the ingestion of varied telemetry sources including cloud, network, compute and mobility sources. Supported telemetry combined with our proprietary Advanced Analytics, analyst threat hunting, and AI-based threat detection capabilities translate to faster, more accurate detections and most importantly reduced business risk.
NTT’s Managed Detection and Response service offers the sophisticated threat detection capabilities of the Samurai XDR platform along with, 24/7 threat monitoring, analyst-driven threat hunting, and comprehensive threat intelligence delivered by NTT’s Global Threat Intelligence Center. By combining the advanced analytics capability of the Samurai XDR platform with the expertise of the skilled analysts in the NTT SOC, threats are identified and separated from a large number of false positives typically generated by security technologies.
Managed Detection and Response is a service that utilises security alerts along with relevant contextual information identified by the Samurai XDR platform. This information is analysed by a skilled Security Analyst, who engages in threat hunting and validation activities to verify the threat, its impact, and to identify additional information associated with a potential breach. Once the threat is validated, the Security Analyst creates a detailed Security Incident Report for the Client. The Security Incident Report includes a detailed description of the security incident combined with scenario-specific actionable response recommendations. This significantly assists in reducing the time taken for informed responsive measures, thereby, lowering associated risks.
2. Service Elements
Samurai Managed Detection and Response provides the Client with a service overlay which provides advanced detection and response capabilities delivered by skilled Security Analysts in the NTT Security Operations Center, leveraging the Samurai XDR platform. The Samurai Managed Detection and Response service provides a set of components which provide the Client with:
- Onboarding guidance
- Access to SOC Analysts
- Threat Intelligence
- Threat Detection and Investigation
- Threat Hunting
- Security Incident Reports
- Threat Response
- Service Management Portal and Service Reporting
- Incident Response
- Service Assurance through regular Threat Reviews
3. Onboarding
Onboarding of the Managed Detection and Response service commences with the activation of the Client’s Samurai XDR tenant. Activation of the Client’s tenant will provide the Client with instant access to Help Center online documentation and the access and instructions required in order to configure the Samurai XDR platform. This includes:
- Deploying Local Collector appliances;
- Connecting telemetry sources (including logs, enrichment and other data sources); and;
- Configuring integrations to client applications such as Endpoint Detection and Response, IT Service Management, and other cloud-based platforms.
Within two business days of activation, NTT will host a Managed Detection and Response introductory conference call with the Client. This meeting will explain the onboarding process and will include an overview of the Samurai XDR application and configuration steps to be completed by the Client. Follow-up progress calls may be scheduled to ensure setup progress and status.
Within fourteen days of activation a Samurai MDR orientation conference call will be held with the Client which upon completion, Service Delivery will begin. This meeting will outline what to expect from the service including how SOC analysts will interact with the Client, overview of Security Incident Reports and how to utilize the Samurai MDR.
For more details please visit the Samurai MDR Onboarding Guide.
4. Service Features
Samurai Managed Detection and Response provides the following service features:
4.1 Threat Detection
The Samurai XDR platform detects threats and suspicious behavior using the Samurai XDR AI Engine. The AI Engine makes use of a combination of traditional threat detection techniques, Advanced Analytics, machine learning and Threat Intelligence to detect sophisticated threats. To ensure service quality, NTT continuously makes detection-tuning decisions based on the validity and relevance of alerts and security incidents.
4.2 Threat Intelligence
The Global Threat Intelligence Center delivers Threat Intelligence, which enhances the Managed Detection and Response service. Additionally, the Managed Detection and Response service includes continuous Threat Intelligence updates driven by investigations of security incidents.
4.3 Dynamic Blocklist
The Dynamic Blocklist feature provides a real-time feed of curated Indicators of Compromise. The Client can configure supported devices, such as next generation firewalls and internet proxies, to receive the dynamic list to proactively block threats. IoCs are added to the Dynamic Blocklist on an ongoing basis. The Dynamic Blocklist option is available at no additional charge. Additional details can be found in the Dynamic Blocklist overview.
4.4 24/7 Security Analyst Interaction
The Managed Detection and Response service includes detailed security investigation of alerts detected via Samurai XDR by Security Analysts in NTT’s SOC. Investigation includes threat analysis and alert-driven threat hunting activities across the Client’s telemetry environment to provide validation and assessment of the malicious nature of a threat and its potential impact.
Security Analysts use the MITRE ATT&CK framework as a reference model in presenting the nature of a threat and assigning appropriate severity to identified security incidents.
The Managed Detection and Response service also provides validation of threats through vendor integration and evidence collection for selected security technologies, such as packet capture data (PCAP) and malware execution reports.
4.5 Investigations
When the Samurai XDR platform generates an alert indicating a potential threat, a SOC Analyst will begin an investigation. The investigation includes validating the presence of a threat via client telemetry and evidence data, threat intelligence, and other data and information sources within the Samurai XDR platform. Using this information and automation capabilities of the Samurai XDR platform, the analyst then determines the nature and extent of any compromise which may have occurred. Depending on the nature of the potential threat, activities conducted during the process of the investigation may include:
- Threat analysis.
- Alert-driven threat hunting across the Client’s telemetry data which has been ingested into Samurai XDR.
- Assessment of the malicious nature of a threat and its potential impact.
- Contextualisation of validated threats based on factors such as industry vertical and geopolitical context.
- Categorisation according to industry best practice frameworks including MITRE ATT&CK.
- Forensic analysis of telemetry data stored in Samurai XDR.
- Malware analysis; and
- Recommendation to the Client of a suggested response covering suggested next steps.
4.6 Security Incident Reports
If, as a result of an investigation, a threat is identified, the Security Analyst creates a Security Incident Report detailing the cybersecurity incident, including plain-language observations and incident mitigation and/or remediation recommendations.
Client notifications can be provided by phone or email based on severity:
- Critical severity; Phone / E-mail notifications.
- Low, Medium, High severity; E-mail notifications.
Clients requiring Phone notifications must provide NTT with a prioritized list of Client contacts.
4.7 Threat Hunting
Utilizing Client telemetry and evidence data, NTT will perform Threat Hunting to detect activities such as persistence mechanisms, application usage, network activity or the tactics and techniques and procedures (“TTPs”) of threat actors. When a threat is detected, a security analyst will create a security incident and notify the Client.
4.8 Threat Response
NTT will perform actions within the Samurai XDR platform on the Client’s behalf when an investigation results in the detection of a threat.
NTT will take actions to isolate compromised/malicious host Endpoints following Security Analyst incident validation. Remote isolation actions are performed using the isolation capabilities of the Client’s Endpoint Detection and Response (EDR) technology.
4.9 Samurai XDR Application and Help Center
Managed Detection and Response Clients have access to the Samurai XDR application, including self service features such as telemetry integration and collector configuration. Details of the functionality provided by the Samurai XDR platform can be found in the Samurai Help Center - online documentation.
In addition to the Samurai XDR application, Samurai Managed Detection and Response provides the client with access to the Samurai Help Center, which provides online access to:
- interact with us online by logging incidents and requests;
- view security incident reports;
- track, view and submit comments within incident and request tickets; and
- browse / search our knowledge base which contains online documentation for Samurai XDR and Managed Detection and Response.
Additional information regarding support for Samurai XDR and Samurai MDR can be found in our Support Policy.
4.10 Incident Response
The Incident Response add-on is a retainer which the Client may choose to utilize if the Client requires the NTT SOC to perform additional threat investigation activities. Clients can continue to leverage the services of the NTT SOC in instances where the severity of an incident justifies additional effort to perform tasks such as threat hunting, malware analysis or forensic analysis of data in Samurai XDR be performed.
This add-on provides the Client with the facility of additional post root-cause analysis to assist with containment of a threat.
The Incident Response retainer includes 40 hours per year. If the Client requires additional Incident Response beyond 40 hours, additional retainers of 40 hours can be purchased.
Incident Response effectiveness is enhanced with an installed and supported endpoint agent. If the client does not have a supported agent, NTT will work with the client to provision endpoint agents to support the investigation. For more information please read the detailed description of the Incident Response add-on.
4.11 Threat Reviews
Through a program of scheduled quarterly meetings, Threat Reviews will be conducted with the Client to derive maximum value from Samurai MDR.
Topics covered in the quarterly meetings include:
- Review service health.
- Review security incidents and how they provide insights into the Client’s security posture and attack surface; and
- Advising the Client regarding configuration of Samurai XDR to better meet the Client’s needs.
For clients that require a dedicated resource and monthly threat reviews, the Samurai Cybersecurity Advisor subscription is available as a chargeable add-on.
5. Client Responsibilities
Client is required to perform the following obligations below:
assign a primary Point of Contact (POC) to work with NTT. Client will ensure that NTT’s records of all Client POCs are kept up to date and are accurate.
ensure that all telemetry sources have connectivity required in order to interact with the Samurai XDR platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data and the ability as well as the ability to monitor and control any agents or virtual appliances installed in Client’s environment for the purpose of providing the service.
ensure that endpoints falling under the scope of Samurai MDR have a supported endpoint agent installed in order to facilitate the gathering of telemetry and evidence data as well as providing the ability to perform remote isolation.
provide knowledgeable technical staff and/or third-party resources to perform any configurations or software installations required in order for Client to consume the service. This includes, but is not limited to:
- Configuration of connectivity.
- Installation of Local Collector virtual appliances.
- Provision of IP addressing required for any virtual appliances required in Client’s network; and
- Configurations of cloud services required in order for Samurai XDR to receive telemetry from these services.
perform all aspects of Service Onboarding, including the configuration of telemetry sources and configuration of Collectors to provide telemetry feeds to the Samurai XDR platform. Client will ensure that all source devices are compliant with the Samurai XDR platform configuration requirements and are running supported software and/or hardware versions.
ensure that it does not utilise any technologies or configurations which block traffic, rotate logs or in any other way impede delivery of the service.
procure all maintenance, support and licensing agreements with third-party vendors for all telemetry sources.
comply with all the relevant data privacy, regulatory, and administrative laws, policies and procedures related to monitoring user traffic and communications.
bring a threat, identified in a security incident report, to closure.
Failure to provide any of the service requirement information on a timely basis can result in delays in Service Onboarding and Service Delivery by NTT and NTT shall not be liable for any consequences of such delays.
6. Service Level Agreements
The Service Level Agreements (SLAs) listed in this section will become active once Onboarding of the Client is considered complete.
6.1 Availability
The Availability SLA is determined by the ability of the Client to access the Samurai XDR platform. This is measured by the ability of the Client to log into the Samurai XDR app.
NTT will use reasonable commercial means to ensure an availability of the Samurai XDR app of at least 99.9%. If the availability of the platform drops below this level, the Client may claim a Service Level Credit as set out in the table below:
| Application Availability | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| 99.9% - 100.0% | 0% |
| 95.0% - 99.9% | 1% |
| Less than 95% | 10% |
6.2 Validated Security Incident Notification
NTT will analyze alerts and related available data sources on a 24/7 basis for signs of malicious activity which has bypassed preventative security controls.
If malicious activity is confirmed, NTT will determine the severity of the threat. For Security Incidents with a severity of high or critical NTT will provide an Incident Report within 30 minutes of determining the severity.
For Security Incidents with a severity of low or medium, NTT will endeavour to provide an Incident Report within 120 minutes of determining the severity.
If the creation of a security incident report in relation to an incident with a severity of high or critical takes longer than 30 minutes, the Client may claim a Service Level Credit as set out in the table below:
| Time taken to create a security incident report | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| Less than 30 minutes | 0% |
| 31 to 300 minutes | 1% |
| Over 300 minutes | 5% |
A Client may make a maximum of 1 claim against this service level per calendar day and per security incident.
6.3 Receiving Service Credits
To receive a Service Credit, the Client must open a ticket in the Samurai XDR app within 30 days of the incident for which the Client is claiming a Service Level Credit.
4.4.1.3 - Managed Detection & Response (MDR) Service Description (v3.0 2025-10-11)
This document has been superseded. For the latest version please click HERE.
1. Introduction
NTT’s Managed Detection and Response (MDR) service builds on the capabilities of the Samurai platform which delivers cybersecurity insights, advanced threat detection, response, and protection capabilities via the ingestion of varied telemetry sources including cloud, network, endpoint, identity and compute. Supported telemetry combined with our proprietary advanced analytics, threat hunting, and AI-based threat detection capabilities translate to faster, more accurate detections and most importantly reduced business risk.
NTT’s Managed Detection and Response service offers the sophisticated threat detection capabilities of the Samurai platform along with, 24/7 threat monitoring, automated and analyst-driven threat hunting, and comprehensive Cyber Threat Intelligence (CTI) delivered by NTT’s Global Threat Intelligence Center. By combining the advanced analytics capability of the Samurai platform with the expertise of skilled cyber security analysts in the NTT Security Operation Center (SOC), threats are identified and separated from a large number of false positives typically generated by security technologies.
Samurai Managed Detection and Response is a service that utilises security alerts along with relevant contextual information identified by the Samurai platform. This information is analysed by a skilled Cyber Security Analyst, who engages in threat hunting and validation activities to verify the threat, its impact, and to identify additional information associated with a potential breach. Once the threat is validated, the Cyber Security Analyst creates a detailed Security Incident Report for the Client. The Security Incident Report includes a detailed description of the security incident combined with scenario-specific actionable response recommendations. This significantly assists in reducing the time taken for informed responsive measures, thereby, lowering associated risks.
2. Service Elements
Samurai Managed Detection and Response provides the Client with a service overlay which provides advanced detection and response capabilities delivered by skilled Cyber Security Analysts in the NTT Security Operations Center, leveraging the Samurai platform. The Samurai Managed Detection and Response service provides a set of components which provide the Client with:
- Onboarding guidance
- Access to SOC Analysts
- Cyber Threat Intelligence
- Threat Detection and Investigation
- Threat Hunting
- Security Incident Reports
- Threat Response
- Service Management Portal and Reporting
- Incident Response
- Service Assurance through regular Threat Reviews
3. Onboarding
Onboarding of the Managed Detection and Response service commences with the activation of the Client’s Samurai tenant. Activation of the Client’s tenant will provide the Client with a link to online documentation and the access and instructions required in order to integrate with the Samurai platform. This includes:
- Deploying Local Collector appliances;
- Deploying Network Traffic Analyzer(s) (NTAs);
- Connecting telemetry sources (including logs, enrichment and other data sources); and;
- Configuring integrations to client applications such as Endpoint Detection and Response, network security controls and other cloud-based platforms.
Within two business days of activation, NTT will host a Managed Detection and Response introductory conference call with the Client. This meeting will explain the onboarding process and will include an overview of the SamurAI Portal and configuration steps to be completed by the Client. Follow-up progress calls may be scheduled to ensure setup progress and status.
Within fourteen days of activation a Samurai MDR orientation conference call will be held with the Client which upon completion, Service Delivery will begin. This meeting will outline what to expect from the service including how SOC analysts will interact with the Client, overview of Security Incident Reports and how to utilize the Samurai MDR.
For more details please visit the Samurai MDR Onboarding Guide.
4. Service Features
Samurai Managed Detection and Response provides the following service features:
4.1 Threat Detection
The Samurai platform detects threats and suspicious behavior using the Samurai Real-Time Engine and the Samurai Hunting Engine. The Samurai Engine(s) makes use of a combination of traditional threat detection techniques, advanced analytics, machine learning and Cyber Threat Intelligence to detect sophisticated threats. To ensure service quality, NTT continuously makes detection-tuning decisions based on the validity and relevance of alerts and security incidents.
4.2 Cyber Threat Intelligence
The Global Threat Intelligence Center delivers Cyber Threat Intelligence, which enhances the Managed Detection and Response service. Additionally, the Managed Detection and Response service includes continuous Cyber Threat Intelligence updates driven by investigations of security incidents.
4.3 24/7 Security Analyst Interaction
The Managed Detection and Response service includes detailed security investigation of alerts detected via Samurai by Cyber Security Analysts in NTT’s SOC. Investigation includes threat analysis and threat hunting activities across the Client’s telemetry environment to provide validation and assessment of the malicious nature of a threat and its potential impact.
Cyber Security Analysts use the MITRE ATT&CK framework as a reference model in presenting the nature of a threat and assigning appropriate severity to identified security incidents.
The Managed Detection and Response service also provides validation of threats through vendor integration and evidence collection for selected security technologies, such as packet capture data (PCAP) and malware execution reports.
4.4 Investigations
When the Samurai platform generates an alert indicating a potential threat, an NTT SOC Cyber Security Analyst will begin an investigation. The investigation includes validating the presence of a threat via client telemetry and evidence data, cyber threat intelligence, and other data and information sources within the Samurai platform. Using this information and automation capabilities of the Samurai platform, the analyst then determines the nature and extent of any compromise which may have occurred. Depending on the nature of the potential threat, activities conducted during the process of the investigation may include:
- Threat analysis.
- Threat hunting across the Client’s telemetry data which has been ingested into the Samurai platform.
- Assessment of the malicious nature of a threat and its potential impact.
- Contextualisation of validated threats based on factors such as industry vertical and geopolitical context.
- Categorisation according to industry best practice frameworks including MITRE ATT&CK.
- Forensic analysis of telemetry data stored in the Samurai platform.
- Malware analysis; and
- Recommendation to the Client of a suggested response covering suggested next steps.
4.5 Security Incident Reports
If, as a result of an investigation, a threat is identified, the Cyber Security Analyst creates a Security Incident Report detailing the cybersecurity incident, including plain-language observations and incident mitigation and/or remediation recommendations.
Client notifications can be provided by phone or email based on severity:
- Critical severity; Phone / E-mail notifications.
- Low, Medium, High severity; E-mail notifications.
Clients requiring phone notifications must provide NTT with a prioritized list of Client contacts.
4.6 Threat Hunting
Utilizing Client telemetry and evidence data, NTT will perform Threat Hunting to detect activities such as persistence mechanisms, application usage, network activity or the tactics and techniques and procedures (“TTPs”) of threat actors. When a threat is detected, a cyber security analyst will create a security incident and notify the Client.
4.7 Threat Response
NTT can perform actions on the Client’s behalf when an investigation results in the detection of a threat.
NTT will take actions to isolate compromised/malicious host Endpoints following Security Analyst incident validation. Remote isolation actions are performed using the isolation capabilities of the Client’s Endpoint Detection and Response (EDR) technology.
4.8 SamurAI Portal
Managed Detection and Response Clients have access to the SamurAI Portal, details of the functionality can be found in Samurai online documentation that includes:
- self service features such as telemetry integration and collector configuration;
- interact with us online by logging incidents and requests;
- view security incident reports;
- track, view and submit comments within incident and request tickets; and
- view service dashboards, metrics and reports.
4.9 Threat Reviews
Through a program of scheduled quarterly meetings, Threat Reviews will be conducted with the Client to derive maximum value from Samurai MDR.
Topics covered in the quarterly meetings include:
- Review service health.
- Review security incidents and how they provide insights into the Client’s security posture and attack surface; and
- Advising the Client regarding configuration of Samurai to better meet the Client’s needs.
For clients that require a dedicated resource and monthly threat reviews, the Samurai Cybersecurity Advisor subscription is available as a chargeable add-on.
5. Supplements & Add-ons
5.1 Dynamic Blocklist
Included within the Samurai MDR service at no additional charge, Dynamic Blocklist provides a real-time feed of curated Indicators of Compromise (IoC). The Client can configure supported devices, such as next generation firewalls and internet proxies, to receive the dynamic list to proactively block threats. IoCs are added to the Dynamic Blocklist on an ongoing basis. Additional details can be found in the Dynamic Blocklist overview.
5.2 Samurai Network Traffic Analyzer (NTA)
Included within the Samurai MDR service at no additional charge, the SamurAI NTA is a Network Traffic Analyzer that identifies threats by analyzing traffic on Client network segments.
The NTA has embedded multiple components that leverage traditional threat detection techniques, advanced analytics, machine learning and Cyber Threat Intelligence to detect sophisticated threats.
Upon identifying suspicious activities, or threats, the NTA provides the NTT SOC Cyber Security Analysts with Evidence data (Full packet capture [PCAP]), allowing for deep network investigations. This additional evidence data increases the Cyber Security Analyst’s ability to analyse, validate and escalate cyber security threats.
Operating System/Software Management
NTT maintains the supported Operating System and installed Software on NTA devices. Such maintenance is performed remotely and at the sole discretion of NTT as relevant security hot fixes are made available, or as part of standard OS software management.
Capacity improvement recommendations
Where NTT monitoring determines that an NTA is oversubscribed, NTT shall liaise with the Client to determine the best plan and path forward. Examples include but are not limited to the following:
- Request the Client to change the network architecture
- Request the Client to update assigned virtual resources, or licenses to facilitate greater capacity
5.3 Incident Response
The Incident Response add-on is a retainer which the Client may choose to utilize if the Client requires the NTT SOC to perform additional threat investigation activities. Clients can continue to leverage the services of the NTT SOC in instances where the severity of an incident justifies additional effort to perform tasks such as threat hunting, malware analysis or forensic analysis of data in the Samurai platform.
This add-on provides the Client with the facility of additional post root-cause analysis to assist with containment of a threat.
The Incident Response retainer includes 40 hours per year. If the Client requires additional Incident Response beyond 40 hours, additional retainers of 40 hours can be purchased.
Incident Response effectiveness is enhanced with an installed and supported endpoint agent. If the client does not have a supported agent, NTT will work with the client to provision endpoint agents to support the investigation. For more information please read the detailed description of the Incident Response add-on.
6. Data Retention
The Samurai MDR service contract includes 12 months of telemetry data retention. Retention is performed only for clients with an active contract. Data will be deleted from all NTT data stores according to the retention window designated based on the contract period. If a contract expires, the client will no longer have access to their data via the SamurAI Portal or service features.
7. Client Responsibilities
Client is required to perform the following obligations below:
assign a primary Point of Contact (POC) to work with NTT. Client will ensure that NTT’s records of all Client POCs are kept up to date and are accurate.
ensure that all telemetry sources have connectivity required in order to interact with the Samurai platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data and the ability as well as the ability to monitor and control any agents or virtual appliances installed in Client’s environment for the purpose of providing the service.
ensure that endpoints falling under the scope of Samurai MDR have a supported endpoint agent installed in order to facilitate the gathering of telemetry and evidence data as well as providing the ability to perform remote isolation.
provide knowledgeable technical staff and/or third-party resources to perform any configurations or software installations required in order for Client to consume the service. This includes, but is not limited to:
- Configuration of connectivity.
- Installation of Local Collector virtual appliances.
- Installation of Network Traffic Analyzer (NTA) appliances.
- Provision of IP addressing required for any virtual appliances required in Client’s network; and
- Configurations of cloud services required in order for the Samurai platform to receive telemetry from these services.
perform all aspects of Service Onboarding, including the configuration of telemetry sources and configuration of Collectors to provide telemetry feeds to the Samurai platform. Client will ensure that all source devices are compliant with the Samurai platform configuration requirements and are running supported software and/or hardware versions.
ensure that it does not utilise any technologies or configurations which block traffic, rotate logs or in any other way impede delivery of the service.
procure all maintenance, support and licensing agreements with third-party vendors for all telemetry sources.
comply with all the relevant data privacy, regulatory, and administrative laws, policies and procedures related to monitoring user traffic and communications.
bring a threat, identified in a security incident report, to closure.
Failure to provide any of the service requirement information on a timely basis can result in delays in Service Onboarding and Service Delivery by NTT and NTT shall not be liable for any consequences of such delays.
8. Service Level Agreements
The Service Level Agreements (SLAs) listed in this section will become active once Onboarding of the Client is considered complete.
8.1 Availability
The Availability SLA is determined by the ability of the Client to access the Samurai MDR platform. This is measured by the ability of the Client to log into the SamurAI Portal.
NTT will use reasonable commercial means to ensure an availability of the SamurAI Portal of at least 99.9%. If the availability of the platform drops below this level, the Client may claim a Service Level Credit as set out in the table below:
| Application Availability | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| 99.9% - 100.0% | 0% |
| 95.0% - 99.9% | 1% |
| Less than 95% | 10% |
8.2 Validated Security Incident Notification
NTT will analyze alerts and related available data sources on a 24/7 basis for signs of malicious activity which has bypassed preventative security controls.
If malicious activity is confirmed, NTT will determine the severity of the threat. For Security Incidents with a severity of high or critical NTT will provide an Incident Report within 30 minutes of determining the severity.
For Security Incidents with a severity of low or medium, NTT will endeavor to provide an Incident Report within 120 minutes of determining the severity.
If the creation of a security incident report in relation to an incident with a severity of high or critical takes longer than 30 minutes, the Client may claim a Service Level Credit as set out in the table below:
| Time taken to create a security incident report | Credit as a percentage of monthly Managed Detection and Response fee |
|---|---|
| Less than 30 minutes | 0% |
| 31 to 300 minutes | 1% |
| Over 300 minutes | 5% |
A Client may make a maximum of 1 claim against this service level per calendar day and per security incident.
8.3 Receiving Service Credits
To receive a Service Credit, the Client must open a ticket via the SamurAI Portal within 30 days of the incident for which the Client is claiming a Service Level Credit.
4.4.2 - Superseded Onboarding Managed Detection & Response
4.4.2.1 - Onboarding Managed Detection and Response (MDR) (v1.0 2023-09-11)
This document has been superseded. For the latest version please click HERE.
Overview
Welcome to NTT Security Holdings (NTTSH) and the Managed Detection and Response (MDR) Service Powered by Samurai XDR.
We have made onboarding simple and shall support you through each phase.
MDR Security Operations Center (SOC)
The SOC provide guidance and expertise during onboarding and service delivery, however it is important to understand the role and responsibilities of you and our team.
The SOC will be your main contact during onboarding and will schedule introduction and orientation calls with you to ensure your journey to MDR is problem free. You as a Client will still need to perform your responsible actions outlined in the rest of this document and specifically for onboarding MDR telemetry sources, unless you have purchased enhanced onboarding consulting services.
After your orientation meeting, MDR Service delivery begins. The SOC will schedule and conduct regular threat review meetings as outlined within the MDR Service Description to ensure you derive maximum value from the service.
Suggested Resources
During onboarding you will likely need to call upon various teams within your organization, we understand you may not have all of the appropriate roles but suggest the following:
| Rol****e/Function | Responsibility |
|---|---|
| Chief Information Security Officer (CISO) | Awareness of the service and how it functions to drive handling of security incidents reported |
| Security Operations Engineer | Management and administration of the Samurai XDR Application |
| System Administrator | Deployment of Collector(s) |
| Network Engineer | Configuration of supported integrations, configuration of access control rules as required by Collector and integration |
| Security Manager | Integration of Samurai MDR into your organization’s security practice and operating processes |
| Project Manager | Initiating, planning, executing, controlling and closing work of your teams to achieve onboarding |
Onboarding Phases
The image and table below outline the main phases of onboarding including responsibilities, resources and deliverables.
| Phase | NTTSH responsibilities | Client responsibilities | NTTSH Resource/Deliverable |
|---|---|---|---|
| Activation | * Send an activation email with instructions for accessing the Samurai XDR application (Contract term and client billing commences upon login) | * Activate Samurai XDR application | * Sales contact * Access to Samurai XDR application |
| Introduction Meeting (within 2 days Samurai XDR application activation) | |||
| * Schedule and conduct introductory meeting which includes: * Welcome and introduction to the MDR service * Overview of the Samurai XDR platform * Overview of setup/configuration steps and resources * Gather pertinent information (notification contacts) * Answer any questions/queries | * Attend scheduled introductory meeting * Review online documentation * Add additional Samurai XDR application users as required * Determine notification contact points and call list (this should be provided 7 days after intro call) | * SOC * Samurai XDR application | |
| Setup | * Respond and assist with any issues raised | * Configure and deploy collectors * Configure integrations * Configure telemetry sources * Raise any issues via ticket | * Samurai XDR application |
| MDR Service Delivery | Orientation Meeting (within 14 days of introduction meeting) | ||
| * Schedule and conduct MDR orientation conference call to include: * What to expect – how SOC analysts interact with you * Overview of Security Incident Reports * Support/Help resources * Schedule Threat Review meetings | * Complete necessary Setup * Attend scheduled orientation call | * SOC * 24/7 monitoring and investigation of threats detected via Samurai XDR by Security Analysts * Security Incident Report(s) as a result of our SOC Analyst investigation(s) with recommendations * Security Incident notification options selected by you * Access to Samurai XDR application to conduct your own threat investigations and threat hunts (outside MDR service delivery) if desired * Regular Threat Review meetings * Access to Incident Response retainer (if purchased) | |
| Threat Review (Quarterly during MDR Service Delivery) | |||
| * Schedule regular Threat Review meetings which include: * Security Incident Management * Notable incidents during period * Review and ensure progress on any open Security Incidents * MDR scope reviews * Metrics (volume) * Implemented log sources * Improvements * Detection and response improvement recommendations | * Attend scheduled Threat Review meetings | * SOC | |
| Incident Response (IR) retainer (option) | |||
| * Response to IR - analysts engagement e.g hunting, malware analysis | * Invoke IR as needed via ticket | * IR response |
Your Responsibilities
Below are your primary responsibilities during onboarding. Additional responsibilities may arise as needed to support aspects of the implementation that are unique to your specific environment(s):
- Create user accounts for additional users of the Samurai XDR application, maintain all user accounts, ensuring that contact information for each user is complete and accurate.
- Deploy the Samurai XDR Collector(s) and successfully configure required integrations.
- Configure and manage all resources required to support the deployment of Collector(s) - virtual / physical.
- Configure and maintain supported on-premises log sources and cloud integrations in line with Samurai XDR requirements.
- Ensure that all telemetry sources have connectivity required in order to interact with the Samurai XDR platform. This includes, but is not limited to, the ability to receive telemetry source feeds and evidence data as well as the ability to monitor and control any agents or virtual appliances installed in your environment for the purpose of providing the service.
- Respond to NTTSH communications in a timely manner and ensure attendance of the necessary resources for all meetings to ensure timely completion of onboarding and during service lifecycle.
- Bring a threat, identified in a security incident report, to closure.
Your overall responsibilities for the service can be found in the MDR Service Description.
5 - Reference
5.1 - What's New in Samurai MDR!
5.1.1 - SamurAI MDR Release Notes
12 Feb 2026
SamurAI Portal
General Improvements / Bug Fixes
- Following feedback on integration status threshold time units, we have made updates to set and view thresholds in d (days), h (hours) and m (minutes).
Related documentation:
10 Feb 2026
SamurAI Portal
We have enhanced the SamurAI Platform’s monitoring capabilities, introducing improvements across Collectors, Network Traffic Analyzers (NTA’s), Integrations and Notification handling.
Status Categories
We have updated our status model by replacing the previous time‑based statuses (e.g. no events in last 12 hours, no events in last 24 hours, healthy, provisioning, unknown) with a new standardized set of statuses: Critical, Warning, OK, Pending, and Unknown.
This change aligns with our new flexible threshold framework, which no longer relies on fixed 12 and 24 hour intervals.
Documentation for Collectors, Integrations and NTA’s has been updated accordingly.
Integration Thresholds
The SamurAI Portal now provides configurable Warning and Critical thresholds. These thresholds can be defined globally at the product level (ensuring consistent behavior across all integrations of the same product) or individually at the integration level, allowing overrides to meet specific operational requirements.
Related documentation:
High Availability
We now support telemetry monitoring for systems deployed in High Availability (HA) configurations through HA Groups, ensuring resilient processing of telemetry across paired systems.
Learn more:
Notifications
We have simplified the management of email notifications, allowing you to enable or disable them across all levels, including Collector, Integration, NTA, Security Incident, Ticket and User layers.
Relevant documentation:
User Notifications
Users can now manage their own notification preferences, choosing which events trigger email notifications and under what conditions.
Updated documentation:
General Improvements / Bug Fixes
- Email notifications for are now aggregated (when applicable) and sent as a single message instead of generating individual notifications per integration.
Samurai Documentation
Supported Integrations
Find a link to the newly supported telemetry sources and integration guides:
12 November 2025
SamurAI Portal
The SamurAI Endpoint Agent
We are excited to announce the release of the SamurAI Endpoint Agent, a light weight software component installed on an endpoint to provide deep visibility and enabling SamurAI Managed Detection & Response!
Please refer to the following overview of the SamurAI Endpoint Agent and also the FAQ for more information:
You can also review the following requirements, how to download and manage the agent within the SamurAI portal:
For our existing Beta clients the following updates are applicable:
Docs Assistant
We’ve launched the Docs Assistant, an AI-powered documentation tool embedded in the SamurAI Portal. Users can now ask natural language questions and instantly receive accurate answers sourced directly from our official documentation. This feature streamlines access to setup guides, feature explanations, and troubleshooting steps — no need to manually search or browse multiple pages.
Please refer to the following overview:
General Improvements / Bug Fixes
- All time filters are limited to 400 days to align with our data retention policy
- Fixed timestamp issue for collectors (last event seen) and integrations (created timestamp)
- The SamurAI Portal has been adapted for mobile devices, offering a smoother and more responsive experience on smartphones. Users can now access features with improved layout and usability across smaller screens
Samurai Documentation
The documentation site now supports light and dark mode, allowing users to choose their preferred viewing experience. This update improves readability and accessibility across devices and environments.
We have updated the SamurAI Cloud Collector guide to include required policy if using an existing AWS S3 bucket:
Supported Integrations
Find a link to the newly supported telemetry sources and integration guides:
We have made updates to the following integration guide:
- Trend Micro Vision One - updated broken links to vendor documentation
- FortiEDR On-Prem - removed the need for syslog configuration as we utilize the API
- Trellix Endpoint Security HX - removed broken links and updated steps
- Palo Alto Next Generation Firewall - inclusion of access to Wildfire when applicable
September 3 2025
SamurAI Portal
Security Incident Situation Room
- The Situation Room associated with a security incident has been updated to clearly articulate any Indicators of Compromise (IoCs) identified.
- A change history has now been added which displays any changes to a security incident as new revisions are created.
- MITRE ATT&CK tactic icons are now displayed for a security incident.
- Within the Details section of the Situation Room, Hosts has been renamed to Assets.
The following article has been updated:
User Management
- Additional fields are now displayed which include ‘account status’ and ’last login’ date/timestamps for all users.
User Profile
- Users can now set their preferred time zone. All timestamps will display according to the selected time zone.
The following article has been updated:
The SamurAI Endpoint Agent Beta
You may be aware that we have been running a BETA program for the SamurAI Endpoint Agent. We are excited to announce the launch in CYQ4 this year!
For our BETA clients and interested parties we have made some updates:
- Renamed the Spiral (a name used internally) menu item to SamurAI Agent and moved under the Telemetry menu.
- Selection on how to handle Agent Updates and Agents for Windows.
- Ability to delete offline agents.
We have also published preliminary articles which cover the SamurAI Endpoint Agent and these updates:
General Improvements / Bug Fixes
- Improved pagination - tables now display all rows in a continuous list instead of breaking them into separate pages.
Samurai Documentation
Supported Integrations
Find a link to the newly supported telemetry sources and integration guides:
We have made updates to the following integration guide:
- Palo Alto Next Next Generation Firewall - added support for vsys and optional threat severity ignore list.
Additional Subscriptions
Dynamic Block List (DBL) documentation has been updated to outline limitations, notably a maximum of 30 devices per client can access the DBL. Additionally each DBL configuration guide now clearly outlines the maximum list size.
June 11 2025
SamurAI Portal
The Samurai Network Traffic Analyzer (NTA)
We are excited to release the Samurai NTA, a virtual appliance designed to provide deep visibility into network activity and detect suspicious or malicious behaviour. We’ve had this capability for a long time, however it is now Samurai native with self service capabilities to configure, download and monitor NTA(s) via the Samurai portal!
Please refer to the following overview of the NTA to learn more:
You can also review the following requirements, how to deploy and NTA detail available in the Samurai portal:
General Improvements / Bug Fixes
- The Advanced Query result limit has been updated to additionally include 10000 possible results dependent on your requirement. The following article has been updated to reflect this change:
- We have updated the logic flow when creating an integration to clearly display and allow you to create the relevant collector type.
- You can now edit the description of a local collector after creation.
- Threat review column adjustments to ensure they are visible.
- A download indicator is now displayed when downloading an executive overview report.
- We now support both English and Swedish language for executive overview reports. The following article has been updated to reflect this change:
- Security Incident and General Tickets now have language and syntax support for code block to ensure readability.
Samurai Documentation
Supported Integrations
Find a link to the newly supported telemetry source and integration guide:
We have made updates to the following integration guides:
- Crowdstrike Falcon Insight - update of API scopes to include Threatgraph.
- Supported Integrations - fixed error in detection category for Squid Cache and general updates for supported integrations.
- Integration Fields - update to ‘Type Log’ - this is also displayed when we ingest logs through cloud storage.
- Cyber-Ark PAS - fixed errors in guide.
- Azure Virtual Networks - As Network Security Group (NSG) flow logs will be retired and you will no longer be able to create new NSG flows logs starting June 2025, we have updated our guide to leverage virtual network (VNet) flow logs which will overcome the limitations of NSG Flow Logs. You can read more at the Azure Updates.
- Palo Alto Networks Cortex XDR Pro - fixed broken links.
Other new or updated documentation
Samurai MDR Service Description
We have made some changes to the Samurai MDR Service Description for clarity, updates are outlined below:
Added Section 5. Supplements & Add-ons:
- Moved Dynamic Blocklist to Section 5.1
- Addition of the Samurai NTA to Section 5.2
- Moved Incident Response to 5.3
Added Section 6 Data Retention
- For clarity we have included our data retention period of 12 months.
Client Responsibilities
- We have added installation and deployment of the Samurai NTA.
February 24 2025
SamurAI Portal
Samurai MDR subscriptions include quarterly Threat Reviews with our SOC analysts. The Cybersecurity Advisor add-on subscription is also available for clients that require a dedicated resource with monthly Threat Reviews.
We now support Threat Review detail within the SamurAI Portal for you convenience and tracking. This release provides metrics and insights into the service Threat Review period and allows you to easily track and update all action points and recommendations in conjunction with the SOC to ensure continuous detection and response improvements.
Threat Review information will be published by the Samurai SOC in tandem with your scheduled Threat Review meetings.
The following articles have been created to provide a high level overview of the functionality:
General Improvements / Bug Fixes
- The search function within Security Incidents and General Tickets now searches within details of all Security Incidents or General Tickets.
- A numerical indicator displays the total number of evidence items for a Security Incident within the associated Situation Room.
- A numerical indicator displays the total number of attachments to a General Ticket.
Samurai Documentation
Supported Integrations
Find a link to the newly supported telemetry source and integration guide:
December 12 2024
SamurAI Portal
We now support Splunk HTTP Event Collection (HEC), a fast, efficient way to send telemetry data to the Samurai platform via HTTPS. We are currently working on new integrations which will leverage Splunk HEC.
The following articles have been updated:
General Improvements / Bug Fixes
- Ability to upload image files within the Security Incident Communication Channel and General Tickets.
Samurai Documentation
Supported Integrations
Find a link to the newly supported telemetry source and integration guide:
December 5 2024
SamurAI Portal
For simplicity and understanding how the Samurai platform collects and ingests data we have removed the collector type entitled ‘Cloud Native Collector’ and now refer to Cloud Collectors. We have updated the Collector articles to reflect this change. Please review:
With this change, we now support self service configuration for retrieval of telemetry data from Amazon Web Services (AWS) S3 storage. The Cloud Collector can monitor S3 bucket(s) for new or updated files and pull the data into the Samurai platform.
Samurai Documentation
- General look & feel updates
- Grammatical and spelling errors updates
- Broken links fixed
Supported Integrations
For the AWS S3 storage collector we have added the following integration configuration guides:
We have also updated the following guide:
October 2024
SamurAI Portal
Alert View
We are excited to announce the first iteration of our new Alert View feature. The Alert View gives you visibility to security detections made by the Samurai platform and also from your vendor integrations with wider visibility into the service for transparency and insight into potential threats. You do not need to review or act upon alerts as the Samurai platform and Security Operations Center (SOC) analysts triage and investigate alerts which may lead to a reported security incident.
For more information please refer to:
![]() We plan on expanding this feature so look out for updates!
We plan on expanding this feature so look out for updates!
Alerts Dashboard
In support of Alert View, a new Alerts dashboard is available that provides useful insights showcasing Samurai MDR’s scale and effectiveness at identifying threats to your organization.
For more information please refer to:
News Feed
We want to keep you updated on what the Samurai SOC analysts are working on, therefore will now provide a news feed within the SamurAI Portal. This feed will be used by the Samurai SOC to deliver real-time security updates and announcements that may include news such as how the SOC is dealing with the ongoing and emerging threats, issues we may be experiencing or notifying you of new releases.
We have updated the following article accordingly:
Telemetry Monitoring Improvements
We’ve made some improvements to Telemetry Monitoring to provide clarity on monitored integrations and notifications, this includes:
- the ability to disable email notifications by hiding an integration (also useful for unsupported integrations displayed as unknown).
- info on unsupported telemetry integrations where we do not notify you in the event of telemetry ingestion problems.
- info on telemetry integrations that do not generate enough events for us to monitor effectively.
- toggle on/off monitored integrations where the Samurai platform does not send notifications in the event of telemetry ingestion problems.
- Bar graph for log sources showing events over a specified time period allowing you to identify drops or spikes in events.
For more information please refer to:
Upload Evidence
You can now upload Evidence in relation to a Security Incident. We’ve made a minor update to the following article:
Language Support
We now support Swedish and Japanese language within the SamurAI Portal - you can toggle between the languages as required.
We have updated the following article:
Samurai Documentation
- We have updated nomenclature to avoid confusion, moving forward we refer to the ‘SamurAI Portal’ in all articles.
- To align with the updates withinin this release we have restructred the section SamurAI Portal User Guide within the main menu.
- Fixed formatting and errors found in articles.
Supported Integrations
Find links to the newly supported telemetry sources and integration guides:
We’ve made some updates to the following integration guides:
- Updated the log category as:
- NoninteractiveUserSignin Logs (with may cause high log volume - We have seen with some clients high log volume so be cautious when enabling!)
- Updated the log category as:
VMWare Carbon Black Cloud Enterprise EDR
- Updated permissions required in the API Access steps
- Added a Crowdstrike authorization form for access to Crowdstrike Falcon Host by the Samurai SOC.
- Renamed to Squid Cache from Squid Proxy and updated steps to configure log forwarding
Other new or updated documentation
- We have updated the Samurai Local Collector guide to reflect an update made to break out the cloud-init files from the ISO image. For AWS and Azure you no longer need to download the ISO image and extract the relevant cloud-init file as they can now be downloaded directly from the SamurAI Portal.
June 17 2024
SamurAI Portal
Advanced Query
There is now no need save your KQL queries offline!
- You can now save your KQL queries within a personal or shared library across SamurAI Portal users within your organization.
- We have created a standard library of useful queries which is populated by our SOC analysts that you can re-use. Expect to see this library updated regularly.
- You can now view the last 50 queries you have run and add them to a library as needed.
In support of this update we have updated the following article with addtional sections to reflect this update:
Security Incident Dashboard
Following the launch of the Situation Room in March, a new dashboard is available that provides useful security incident summary information over the past 12 months. Please review the following article:
To accomodate this update we renamed the existing dashboard to Telemetry Dashboard and updated the following article:
Save Views
You can now save filters you define for Collectors or Integrations using views, this is useful if, for example, you have a large number of integrations and wish to group them to view..
We have updated the following article to reflect this update:
General Improvements / Bug Fixes
- Mitigate excessive Security Incident Report PDF content.
- Align Security Incident Report PDF content - content was not always handled as expected in PDF version.
- Invite user bug fixed - if user was invited and did not complete registration and then invited again, the second registration would fail.
- UTC timezone clarity in all applicable areas.
Supported Integrations
Find links to newly supported telemetry sources and integration guides:
- Squid Proxy
- GestioIP IPAM (Note this integration only provides contextual data for use by the MDR SOC. No data from this integration will be visible in the SamurAI Portal)
April 2024
SamurAI Portal
Following our announcement on 29 April 2024 we shall launch in application ticketing on May 2nd 2024. This allows you to create tickets and view all historical tickets within the SamurAI Portal.
The update is intuitive however please review the following articles if needed:
To accomodate this update we have also amended our Dynamic Block List Configuration Guides outlining what information is required should you should raise a request for DBL onboarding
Samurai Documentation
We have launched our new Samurai Documentation Platform, hosted in GitHub Pages this allows us to manage our documentation just as we do with our code development! Expect to see alot more technical content in the coming months!
Supported Integrations
Find a link to the newly supported telemetry source and integration guide:
March 2024
SamurAI Portal
The Situation Room
Following our announcement on February 16 2024 we have now launched The Situation Room! Through this launch, all Security Incident and associated details are found within the SamurAI Portal. We no longer support Security Incident notifications with PDF reports attached, all notifications now provide a link to the Security Incident within the SamurAI Portal. Security Incidents in PDF format can be downloaded within the associated Situation Room.
Please review the following articles:
Reports
We have updated the Executive Overview Report to align with data shown within the Security Monitoring funnel in relation to Alerts.
You will now find two additional sections within the report:
- Alerts analyzed per vendor (graph)
- Alerts analyzed (table)
Depicted within the additional sections are vendor based alerts but also includes alerts generated by the Samurai platform based on ingested data.
Supported Integrations
We are constantly expanding our list of supported integrations, see links to the newly supported telemetry sources and Integration guides:
- Microsoft Entra ID
- Microsoft Azure Activity Logs
- Microsoft Azure Firewall
- ESET Protect
- Linux Apache HTTP Server Logs
Other new or updated documentation
Microsoft Azure Management Plane
We have deprecated the Microsoft Azure Management Plane configuration guide as we now leverage individual guides listed above and a Cloud Native Collector.
January 2024
SamurAI Portal
2FA Update
Following our announcement on January 11 2024 we have now deprecated support for SMS-based two factor authentication (2FA) and updated access to the SamurAI Portal through Time-based One-Time Passwords (TOTP) through authenticator apps. Please review the article if you require more information.
We have also updated Getting Started with Samurai Managed Detection & Response (MDR) to reflect this change.
Other new or updated documentation
Incident Response Retainer Service Description
We have made some updates to the Incident Response Retainer Service Description to include Emergency IR capabilities. Additional information can be found on our website Incident Response Services.
Supported Integration Categorization
We have updated Supported Integrations to include detection categories we define to provide clarity and set expectations on threat detection capabilities from each telemetry data source. You can read more on the categorization in Telemetry Data Source Categorization.
Microsoft Windows Defender
We have deprecated the dedicated Microsoft Windows Defender configuration guide as we now leverage the Microsoft Graph (Security).
Integration
We have updated the Integrations articles to include the Cloud Native Collector.
December 2023
Supported Integrations
See links to the newly supported telemetry sources and Integration guides:
Other new or updated documentation
We have updated the Local Collector Deployment guide to include deployment to an Azure Virtual Machine. View the updated article:
November 2023
Supported Integrations
We are constantly expanding our list of supported integrations, see links to the newly supported telemetry sources and Integration guides:
- Aruba Networks Clearpass
- Claroty xDome
- Trellix Endpoint Security (ENS)
- Microsoft Graph Security API
- Please review the guide for supported Microsoft products/services.
We have renamed FireEye HX to Trellix Endpoint Security (HX) to avoid any confusion.
October 2023
SamurAI Portal
Reports
Get valuable insights into your MDR service through the reporting feature!
You can now generate reports based on a time period you define which utilizes a standard template. This template has been designed to provide various metrics based on security incidents reported, requests you have submitted and also your data ingested into the Samurai platform. Refer to Samurai MDR Reporting for additional information.
Telemetry Monitoring Notifications
Receive notifications of telemetry data ingestion issues we encounter whilst providing you the MDR service!
Users of your SamurAI Portal can now receive email notifications of telemetry health issues. Refer to Telemetry Monitoring for additional information.
![]() We are improving our notifications functionality in coming releases - for example self service, user profile based selection of notifications…..watch this space!
We are improving our notifications functionality in coming releases - for example self service, user profile based selection of notifications…..watch this space!
Integration Descriptions
The integration description field has been extended to a larger multi-line text box of 256 characters and you can now edit the description field as required after an integration is complete.
Cloud Native Collector
We have released a new Collector type - we call it a Cloud Native Collector!
The Cloud Native Collector is effectively a new transport method to ingest telemetry from cloud based storage. It is built to monitor storage accounts and is completely agnostic to the data, it simply picks up any files for ingestion into the Samurai platform.
We currently support Azure Blob storage. Configuration is completed through an Azure Resource Manager (ARM) template in your subscription with a key to register with the Samurai platform.
The Cloud Native Collector will be used to support specific Azure products/services (for example Azure Firewall) and any supported third parties, therefore anticipate associated configuration guides that will utilize the new Collector type (we are currently in the process of writing the guides).
For more information on the Cloud Native Collector refer to Samurai Collectors and Samurai Cloud Native Collector.
![]() Support for Amazon Web Services (AWS) S3 is coming soon.
Support for Amazon Web Services (AWS) S3 is coming soon.
Release Notes
You’ve already found them if you are reading this article!
We want to ensure you are aware of any new features, bug fixes and enhancements therefore all will be documented here in future. You can easily find the release notes from a link that is now displayed within the SamurAI Portal Main Menu under Documentation.
What’s been fixed/enhanced?
- Case sensitivity when searching for products/vendors when completing an integration.
- Telemetry monitoring indicator in the main menu that displays the number of integrations with potential issues.
Supported Integrations
We are constantly expanding our list of supported integrations, see links to the newly supported telemetry sources and Integration guides:
Other new or updated documentation
We have updated some Microsoft integration guides in support of our preferred method of using Beat agents. See the updated integration guides for more information:
We have updated the Local Collector Deployment guide to include deployment to an Amazon EC2 instance. View the updated article:
Samurai MDR Add-on: Dynamic Block List Support
We have added support for Cisco FirePower.
Please review Dynamic Blocklist and the associated configuration guide.
If you want to onboard your devices then submit a DBL Onboarding request via the SamurAI Portal.
5.2 - Announcements
5.2.1 - SamurAI Portal Authentication Updates
| Announced on | Rollout on |
|---|---|
| August 21, 2025 | September 3, 2025 |
Following our initial email sent out on 1st August 2025 please find additional information of the change which will affect your access to the SamurAI portal.
What is changing?
We are migrating to a new identity and access management system.
Why does this change matter?
This change will allow us to create more flexibility and lay the foundation to introduce additional self-service capabilities and features.
When will this change occur?
We shall be rolling out the change on September 3rd 2025 unless any unforseen issues arise.
How am I affected?
You will need to reset your SamurAI portal user password and multifactor authentication (MFA) at first login following the deployment of the change.
What do I need to do?
After the updates have been made you will be unable to log in to the SamurAI portal unless you reset your password and multifactor (MFA) authentication.
Follow the steps below:
Navigate to the the SamurAI portal.
The following Sign in page will be displayed:

Click on Reset Password
Enter the email address associated with your account. You will receive a password reset email as below:

Within the email, click on Link to reset credentials
You will be redirected to the following page where you must setup a Mobile Authenticator as displayed below:

Follow the instructions to download your preferred application.
Open the authenticator application and scan the QR code on the screen to register your account.
Enter the One-time code from your authenticator application.
Enter a Device Name to help identify and manage your authenticator application accounts.
Click Submit.
You wil be redirected to Update your password.

Enter your New Password and confirm.
Click Submit.
You can now login to the SamurAI portal using your new password and OTP combination.
What if I encounter problems with the authenticator application?
Please refer to your authenticator application user guide however should you encounter any problems scanning the code select Unable to scan? which will allow you to manually your account.
Who do I contact if I am still having problems?
If you are still encountering problems contact your Cyber Security Advisor (CSA) or NTT representative who can assist.
5.2.2 - Samurai Ticketing and Documentation
| Announced on | Rollout on |
|---|---|
| April 29, 2024 | May 2, 2024 |
What is changing?
General tickets will now be available directly within the SamurAI Portal. As per an update in March where we made Security Incident handling and availability within the SamurAI Portal - we have done the same with General Tickets. We are also rolling out a new Samurai Documentation platform, however this will be relatively transparent to you!
Why are we making this change?
We want to continue providing you a world class Managed Detection & Response service and that includes improved customer service and enhanced documentation.
What are the benefits?
SamurAI Portal ticketing:
a single view to manage all tickets (e.g typically tickets you have submitted for the SOC to review)
search, sort and filter tickets you have submitted
communicate in real-time via a Communications Channel with our SOC analysts
The new Samurai Documentation platform will initially be a mirror of our current platform however we are busy working on an enhanced set of documentation
When will this change occur?
This rollout will occur on May 2, 2024 from 09:00 CET, we do not anticipate any service disruption.
How am I affected?
The updates are relatively transparent to you, however it is useful to bookmark our new Documentation Site and review updated documents relating to ticketing.
What do I need to do?
If you want to know how to raise a ticket in the SamurAI Portal please review ‘Getting Help’. You can also bookmark the new Samurai Documentation site.
Who do I contact if I need to ask questions?
Raise any questions you may have during a regular Threat Review or contact your Customer Success Manager who can assist.
5.2.3 - Samurai MDR Security Incidents and The Situation Room
| Announced on | Rollout on |
|---|---|
| February 16, 2024 | March 7, 2024 between 07.00 & 08:00 CET |
What is changing?
In short, your method of consuming Security Incidents. Through this change, all Security Incident details, evidence and communication will be available and handled directly within the SamurAI Portal within what we call - The Situation Room.
Why are we making this change?
We want to continue providing you a world class Managed Detection & Response service and ensure your data is handled securely. We believe in providing our customers as much visibility as possible of the service delivered and this change provides you many such benefits coupled with our ability to evolve and add more exciting features.
What are the benefits?
This change will provide you a multitude of benefits:
a single view to manage Security Incidents
far greater visibility into Security Incidents and associated details
search, sort and filter Security Incidents
allow you to pivot to Advanced Query and view corroborating evidence directly in the SamurAI Portal and continue any investigation/analysis if required
download and view evidence data
communicate in real-time via a Communications Channel with our SOC analysts
When will this change occur?
This rollout will occur on March 7, 2024 between 07.00 & 08:00 CET, we do not anticipate any service disruption.
How am I affected?
Today you receive Security Incidents via email in PDF format and communicate with our SOC analysts via a ticket in the Samurai Help Center. Through this change we will no longer send Security Incident reports in PDF format via email - instead all Security Incident information will be found within the SamurAI Portal. You will continue to receive email notifications of any Security Incidents, however notifications will include a link to the respective Security Incident within the SamurAI Portal.
What do I need to do?
We have published some articles in anticipation of this update so you can familiarize yourself ahead of time. We recommend you review the articles:
Who do I contact if I need to ask questions?
Raise any questions you may have during a regular Threat Review or contact your Customer Success Manager who can assist.
5.3 - Legal
5.3.1 - Beta Product Terms
Effective Date: 11 June 2025
We have updated our Beta Product Terms effective as of the date indicated in the above header. For the previous version of our Beta Product Terms, please click here
You are invited to participate in beta testing NTT’s Samurai Managed Detection and Response service (the “MDR Services”), subject to the Terms of Service and these Beta Program Terms (together, the “Applicable Terms”). The Applicable Terms are made by and between You and NTT and are effective as of the date You first accept them (whether via an online click-through or a signed agreement or by using the Beta Product) (the “Effective Date”).
- General Terms. From time to time, NTT may seek to test MDR Services and make them available to you under these Beta Program Terms (each, the “Beta Service”). You agree that these Applicable Terms are separate and independent agreements for each such Beta Service.
- Beta Test Participation. As the Beta Service is still in a testing phase, it is likely to contain errors. In addition to the disclaimers in the Terms of Service, you agree that the Beta Service is provided “AS IS” and “AS AVAILABLE.” You understand and agree that we may change, withdraw, terminate your access to, testing of and/or use of, or discontinue the Beta Service (or any portion thereof) at any time and in our sole discretion, with or without notice to you. During the term of these Beta Terms, you will use commercially reasonable efforts to provide suggestions, comments or ideas and report issues or problems related to your use of the Beta Service (collectively, “feedback”) to us in a timely basis or as otherwise agreed between the parties in writing (email will suffice). You agree not to disclose feedback to any third party and hereby assign to us all right, title and interest in and to any feedback, without any right to compensation or other obligation from us.
- Confidentiality. “Confidential Information” means any and all information disclosed by us to you, or accessed or provided by you, relating to the Service, including your use thereof, the relationship contemplated herein, feedback, and the Service Descriptions, except to the extent made public by us. You agree that you: (a) will not use any Confidential Information other than as necessary to use or test the Beta Service hereunder; (b) will maintain Confidential Information in strict confidence and will use the same degree of care to protect it as you use to protect your own confidential information, but in no circumstances less than reasonable care; and (c) will not disclose the Confidential Information to any person or entity other than those who need access to such Confidential Information to effect the intent of these Applicable Terms and who are bound by written confidentiality obligations at least as protective as those set forth in this section; provided, however, that you will remain responsible for each such person’s or entity’s compliance with and breach of the confidentiality terms herein. You will not make any public announcements related to the Beta Service without our prior written approval, which we may grant or withhold in our sole discretion. This confidentiality provision supersedes any prior agreements between the parties solely with respect to Confidential Information hereunder.
- Service Descriptions. Specific terms and policies may also apply to your use of the Beta Service (the “Service Descriptions”). In such case, Service Descriptions will be made available to you (online or, prior to being made available online, as separately provided to you) and will also apply to your use of the Beta Service. For clarity, once we post Service Descriptions online (in the Terms of Service, in other supplemental terms, or otherwise), the online version of such Service Descriptions will supersede any prior versions provided to you. By continuing to access, test, or use the Beta Service after any modification to the applicable Service Descriptions, you agree to be bound by them.
- Term. With respect to each Beta Service, the term of these Applicable Terms will begin on the Effective Date and, unless terminated earlier in accordance with the Applicable Terms, will expire on the earlier of (i) the date specified by us in our sole discretion (after which you will cease use of such Beta Service), (ii) the date we (in our sole discretion) make such Beta Service generally publicly available (after which any permitted use is subject to our Terms of Service alone, and not these Beta Terms, and payment of applicable fees and charges), or (iii) the date we discontinue such Beta Service (the “Term”). These Applicable Terms, as applied to each Beta Service, may be terminated by either party: (a) with cause immediately upon written notice to the other party; or (b) without cause upon thirty (30) days’ prior written notice to the other party. Sections 2, 3, 7, and 8 of these Beta Terms, and the provisions of the Terms of Service, will survive any termination or expiration of these Applicable Terms.
- Miscellaneous. You agree that your use of the Beta Service is subject to the Applicable Terms; the Service Descriptions; and Our Privacy Policy. To the extent these Beta Terms conflict with the Terms of Service, these Beta Terms will govern with respect to your use of the Beta Product to the extent of the conflict. As between the parties, we retain exclusive ownership of the Beta Product. Notwithstanding the foregoing, the Terms of Service (unmodified by these Beta Terms) continue to apply to your use of any NTT Services other than the Beta Product even if use thereof is in connection with the Beta Product. Terms used but not defined herein have the meaning given in the Terms of Service. The term “including” means including without limitation. Notwithstanding (and in further limitation of) the liability cap in the Terms of Service, OUR AGGREGATE LIABILITY ARISING OUT OF OR RELATING TO ANY ACCESS TO, TESTING OF OR USE OF THE BETA PRODUCT OR THESE BETA TERMS SHALL NOT EXCEED ONE HUNDRED DOLLARS ($100). We may modify Our Terms of Service or these Beta Terms at any time, and by continuing to access, test, or use the Beta Product after any modification to the Terms of Service or these Beta Terms, you agree to be bound.
5.3.2 - Cookie Statement
NTT Security Holdings Corporation Cookie Statement
Effective Date: April 1 2022
Cookies Statement
NTT Security Holdings Corporation (“NTT” “us” and “we”) and third parties we partner with use cookies and similar technologies on our websites (including mobile sites) and social media sites (“Sites”), mobile applications (Apps) (collectively “Online Services”) to give users (“you” or “your”) the best possible browsing experience.
This Cookies Statement explains:
- what cookies are,
- how we use cookies and similar technologies,
- how third parties we partner with may use cookies and similar technologies, and
- your choices regarding acceptance of cookies and similar technologies.
By creating or logging in to an online account with us or using our Online Services you agree to the use of cookies and similar technologies on our Online Services for the purposes we describe in this Cookies Statement.
1. What are cookies?
A cookie is a small text file, placed on your PC, tablet or mobile phone (collectively “Devices” and individually “a Device”) when you visit an online service. Cookies send information back to the originating online service or another online service that recognizes that cookie.
Cookies can be either permanent (persistent cookies) and remain on your device until you delete or clear them, or temporary (session cookies) where they stay until you close your browser.
Cookies can also be either first party cookies which are set by the online service you are visiting, or third party cookies which are set by an online service other than the online service you are visiting.
Cookies help us to do things such as:
- identify your Device when you use our Online Services;
- identify which browser you use;
- identify which specific pages you view and the time and date you visited our Online Services;
- remember you when you return;
- provide you with a faster, better, and safer browsing experience;
- keep track of your preferences;
- provide you with a more personalized experience; and
- measure and analyse traffic patterns and user behaviour on our Online Services.
2. How we use cookies
We use different types of cookies for different purposes including the following:
Sign-in and Authentication – to verify your account, remember you when you sign-in so that you don’t need to keep signing in, and keep you logged in so that you can navigate easily between pages on our Online Services.
Your Preferences and Settings – to help us remember your preferences including your preferred language, browser settings and communication and opt-out preferences, so that they do not have to be reset each time you return to our Online Services.
Performance – to assess the performance of our Online Services, and to improve the features, functions, content and design of our Online Services.
Analytics and Research – to collect usage and performance data in relation to our Online Services. For example, we may use cookies to count the number of unique visitors to pages on our Sites, what content was viewed and what links were clicked on, to log users’ IP addresses in order to analyse trends and to compile other statistics about use of our Online Services and user behaviour. These cookies include our cookies and third party cookies.
Security – to enable and support our security features, to keep your account safe and to help us combat fraud and any activity on our Online Services which violates our policies or applicable law.
3. Cookies and similar technologies used by us and third parties
NTT and the third parties that we partner with use the following cookies:
(a) Strictly necessary cookies
These cookies are essential for the technical operation of and proper functioning of our Online Services, and enable you to register and login, to easily move around our Online Services, and to access secure areas. Without these cookies our Online Services won’t function properly.
(b) Performance cookies
Performance cookies allow us to collect aggregated and anonymous data on how our Online Services are used, such as the number of visitors to our Online Services, how you navigate around and the time spent on our Online Services and also to identify any errors in functionality. These cookies also help us to improve the way our Online Services work by ensuring that you can find what you’re looking for easily, to better understand what you are interested in and to measure the effectiveness of the content of our Online Services. These cookies may be either permanent or temporary cookies, or first-party or third-party cookies.
(c) Functional cookies
These cookies help us to improve and personalize your browsing experience by storing your preferences and providing enhanced functionality.
(d) Third Party Cookies and Similar Technologies
Our Online Services display content and social media features from third parties including Facebook’s “Like” button, Twitter’s “Follow” button and LinkedIn’s “Share” button on our Online Services. When you visit web pages containing third party content, cookies used by those third parties may track your use of our Online Services and collect information such as your IP address and which pages you visit.
Third parties may also use similar technologies to cookies, such as web beacons (clear GIFs embedded on web pages), local shared objects (also known as flash cookies i.e. messages used in Adobe Flash) that are sent from a web server to a web browser and are then stored as a data file in a browser) to help us to deliver personalized content to you on our Online Services.
Third party cookies and similar technologies use browsing information collected to do things such as:
- count the number of visitors to our Online Services;
- identify the web pages you view and the links you click on and other actions you take on those web pages; and
- identify the online service from which you came before arriving at a particular web page.
We also use third party analytics tools such as Google Analytics which use cookies and similar technologies to collect data about your online activities, in order to analyze your behavior on our Online Services and activities and trends. This data helps us compile aggregated statistics about the effectiveness of our marketing campaigns or other operations. Please be aware that we do not control the use of third-party cookies and similar technologies.
4. Your Cookie Choices
If you don’t want to receive cookies, or want to adjust your cookies preferences, most browsers allow you to change your browser settings to block or delete cookies. Your browser’s “help” function will tell you how to do this.
You should be aware that if you block or delete cookies, our Online Services may not work properly and you may not be able to access certain areas.
5. Updates to this Cookies Statement
We may update this Cookies Statement at any time. If we do, we will update the “last modified” section at the bottom of this Cookies Statement.
We encourage you to regularly review this Cookies Statement to stay informed about our use of cookies.
6. How to contact us
If you have any queries regarding this Cookies Statement, please contact the Legal Department by using the following email address: privacy@security.ntt
5.3.3 - Data Processing Agreement
Effective Date: 11 June 2025
We have updated our Data Processing Agreement effective as of the date indicated in the above header. For the previous version of our Data Processing Agreement please click here
NTT SECURITY HOLDINGS CORPORATION
DATA PROCESSING AGREEMENT
By entering into the Client Agreement (as defined below), Client acknowledges it has accepted and agreed the Client Agreement, the Data Processing Agreement, and the additional documents which are incorporated therein by reference (collectively, the “Agreement”), and is legally bound thereby.
1. Introduction
1.1 Pursuant to Terms of Service and/or related order forms accepted and agreed by You with NTT Security Holdings Corporation or its subsidiaries (the “Client Agreement”), You have entered into an agreement for access, use or delivery and receipt of certain services (the “Services”). In performing the Client Agreement NTT or it’s sub-processors may have access to personal data relating to You, Your employees, or end-users. In certain jurisdictions, it is a requirement under applicable data protection laws to have a data processing agreement in place to provide certain services to you which may involve the access, processing and storage of personal data. The data protection related obligations between parties are set out in this ‘Data Processing Agreement’ or ‘DPA’ which is a standalone agreement but is added as an addendum to the Client Agreement. In this DPA and its attachments NTT Security Holdings Corporation and its subsidiary are referred to as “NTT” and You are referred to as “Client”.
1.2 To the extent NTT may be required to process personal data on behalf of Client under the Client Agreement, NTT will do so in accordance with the terms set out in this Data Processing Agreement (‘DPA’).
2. Defined terms
2.1 ‘Contact’ means, in the case of Client, the contact information entered at the time it subscribed for the NTT Services and, in the case of NTT the contact information provided in the commercial agreement.
2.2 ‘GDPR’ means the General Data Protection Regulation ((EU) 2016/679).
2.3 ‘Personal Data’ means all personal data provided to NTT by, or on behalf of, Client through use of the Services.
2.4 ‘Restricted Transfer’ means a transfer of Personal Data from a member state of the European Economic Area (‘EEA’), the UK or Switzerland (a country not in the EEA or the EU) to a country outside the European Union, EEA, the UK or Switzerland.
2.5 ‘Standard Contractual Clauses’ or ‘SCCs’ means the EU SCCs and UK SCCs as may be updated, supplemented or replaced from time to time under applicable Data Protection Laws, as a recognized transfer or processing mechanism (as applicable).
2.6 ‘UK GDPR’ means the GDPR as implemented in the UK.
2.7 ‘UK GDPR Terms’ means those terms otherwise required pursuant to UK GDPR which are not comprised in the SCCs, as set out in Attachment C
2.8 Lower case terms. The following lower case terms used but not defined in this DPA, such as ‘controller’, ‘data subject’, ‘personal data’, ‘processor’ and ‘processing’ will have the same meaning as set forth in Article 4 of the GDPR, irrespective of whether the GDPR applies.
3. Applicable law
3.1 NTT may be required to process personal data on behalf of Client under (a) any applicable law including (b) subordinate legislation and regulations implementing the GDPR and (c) UK GDPR, (collectively referred to ‘applicable Data Protection Laws’).
3.2 Unless expressly stated otherwise, in the event of any conflict between (a) the main body of this DPA; and (b) UK GDPR (to the extent the applicable UK GDPR applies), the applicable local law will prevail.
3.3 To the extent NTT is a processor of personal data subject to the GDPR and/or UK GDPR, the mandatory sections required by Article 28(3) of the GDPR (or UK GDPR, as applicable) for contracts between controllers and processors that govern the processing of personal data are set out in clauses 5.1, 6.1, 6.3, 6.4, 7, 8.1, 8.2, 9.1, 9.2, 10 to 14 (inclusive). The UK GDPR Terms will govern any processing in relation to any terms required by the UK GDPR which are not covered elsewhere in this DPA.
4. Duration and termination
4.1 This DPA will commence on the date it is signed by the party who signs it last and will remain in force so long as the Client Agreement remains in effect or NTT retains any Personal Data related to the Client Agreement in its possession or control.
4.2 NTT will process Personal Data until the date of expiration or termination of the Client Agreement, unless instructed otherwise by Client in writing, or until such Personal Data is returned or destroyed on the written instructions of Client or to the extent that NTT is required to retain such Personal Data to comply with applicable laws.
5. Personal data types and processing purposes
5.1 Where the applicable Data Protection Law is the GDPR or UK GDPR:
(a) Client and NTT acknowledge that Client is the controller and NTT is the processor or sub-processor.
(b) The details of the processing operations, in particular the categories of personal data and the purposes of processing for which the personal data is processed on behalf of the controller, are specified in Attachment A.
5.2 The Client retains control of the Personal Data and remains responsible for its compliance obligations under applicable Data Protection Laws, including providing any required notices, obtaining any required consents, and for the processing instructions it gives to NTT.
**5.3 [Attachment A](#attachment-a-particulars-of-processing] further describes the purpose of processing and the categories of data subjects and Personal Data that NTT may process in relation to the Services described in the Client Agreement (‘Business Purposes’).
6. NTT obligations
6.1 Client instructions. When NTT acts as the processor of Personal Data, it will only process the Personal Data on Client’s documented instructions and to the extent that this is required to fulfil the Business Purposes. NTT will not process the Personal Data for any other purpose or in a way that does not comply with this DPA or applicable Data Protection Laws. Should NTT reasonably believe that a specific processing activity beyond the scope of Client’s instructions is required to comply with a legal obligation to which NTT is subject, NTT must inform Client of that legal obligation and seek explicit authorization from Client before undertaking such processing. NTT will not process the Personal Data in a manner inconsistent with Client’s documented instructions.
6.2 Independent controller. To the extent NTT uses or otherwise processes Personal Data in connection with NTT’s legitimate business operations, NTT will be an independent controller for such use and will be responsible for complying with all applicable laws and controller obligations.
6.3 Compliance. NTT will reasonably assist Client in complying with Client’s obligations under applicable Data Protection Laws, taking into account the nature of NTT’s processing and the information made available to NTT, including in relation to data subject rights, data protection impact assessments and reporting to and consulting with data protection authorities under applicable Data Protection Laws. NTT will promptly notify Client if, in its opinion, any instruction infringes applicable Data Protection Laws. This notification will not constitute a general obligation on the part of NTT to monitor or interpret the laws applicable to Client, and this notification will not constitute legal advice to Client.
6.4 Disclosure. NTT will not disclose personal data except: (a) as Client directs in writing, (b) as described in this DPA or (c) as required by law. Where NTT is permitted by law to do so, upon receiving a request from a public authority, NTT will use reasonable endeavors to notify the Client and attempt to redirect the public authority to request the personal data directly from Client.
7. Contracting with sub-processors
7.1 List of sub-processors. A list of NTT’s sub-processors that NTT directly engages for the specific Services as a processor is available HERE or on request to the NTT Contact or as otherwise made available on an NTT website.
7.2 General authorization. Client provides its general authorization to NTT’s engagement with sub-processors, including current and future subsidiaries of NTT, to provide some or all Services and process Personal Data on its behalf. To the fullest extent permissible under applicable Data Protection Laws this DPA will constitute Client’s general written authorization to the subcontracting by NTT of the processing of Personal Data to this agreed list of sub-processors.
7.3 Changes. NTT will notify the Client in writing of any intended changes to the agreed list of sub-processors at least 30 days in advance, thereby giving the Client the opportunity to object to such changes. Such objection must be made in writing to the NTT Contact within 30 days of notification. Client’s failure to submit a written objection to the agreed list of sub-processors within 30 days of notification, will be deemed acceptance of the changes to the agreed list of sub-processors.
7.4 Performance. Where a sub-processor fails to fulfil its data protection obligations, NTT shall remain liable to the Client for the performance of that sub-processor’s obligations.
8. Client obligations
8.1 Data subject requests. If NTT receives a request from Client’s data subject to exercise one or more of its rights under applicable Data Protection Laws, in connection with a Service for which NTT is a processor or sub-processor, NTT will redirect the data subject to make its request directly to Client. Client will be responsible for responding to any such request. NTT will comply with reasonable requests by Client to assist with Client’s response to such a data subject request.
8.2 Client requests. NTT must promptly comply with any Client request or instruction from persons authorized by Client requiring (a) NTT to amend, transfer, delete or otherwise process the Personal Data, or to stop, mitigate or remedy any unauthorized processing, (b) Client’s obligations regarding security of processing and (c) Client’s prior consultation obligations in terms of applicable Data Protection Laws, considering the nature of the processing and the information available to NTT.
8.3 Warranty. Client warrants that: (a) it has all necessary rights to provide the Personal Data to NTT for the processing to be performed in relation to the Services; and (b) NTT’s expected use of the Personal Data for the Business Purposes and as specifically instructed by the Client will comply with all applicable Data Protection Laws.
8.4 Privacy notices. To the extent required by applicable Data Protection Laws, Client is responsible for ensuring that all necessary privacy notices are provided to data subjects, and unless another legal basis set forth in applicable Data Protection Laws supports the lawfulness of the processing, that any necessary data subject consents to the processing are obtained and a record of such consents is maintained. Should such a consent be revoked by a data subject, Client is responsible for communicating the fact of such revocation to NTT, and NTT remains responsible for implementing Client’s instruction with respect to the processing of that Personal Data.
9. Security
9.1 TOMs. NTT will implement appropriate Technical and Organizational Measures (‘TOMs’) to ensure the security of the Personal Data in terms of applicable Data Protection Laws, including the security measures set out in Attachment B. This includes protecting the Personal Data against a breach of security leading to accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access to the Personal Data.
9.2 Access to Personal Data. NTT will grant access to the Personal Data undergoing processing to members of its personnel only to the extent strictly necessary for implementing, managing and monitoring of the Client Agreement. NTT will ensure that persons authorized to process the Personal Data received have committed themselves to confidentiality or are under an appropriate statutory obligation of confidentiality.
9.3 Cost negotiations. The parties will negotiate in good faith the cost, if any, to implement material changes other than to the extent required by specific updated security requirements set forth in applicable Data Protection Laws or by data protection authorities of competent jurisdiction (in which case NTT would bear the responsibilities of such cost to the extent required by applicable Data Protection Laws or by the data protection authority).
10. Audits
10.1 Certifications. NTT will maintain any certifications that it is contractually obligated to maintain and comply with as expressly stated in the Client Agreement. NTT will re-certify against those certifications as reasonably required.
10.2 Provision of evidence. At Client’s written request, NTT will provide Client with evidence of those certifications relating to the processing of Personal Data, including applicable certifications or audit reports of its computing environment and physical data centers that it uses in processing Personal Data to provide the Services, so that Client can reasonably verify NTT’s compliance with its obligations under this DPA.
10.3 Compliance with TOMS. NTT may also rely on those certifications to demonstrate compliance with the requirements set out in clause 9.1.
10.4 Confidential information. Any evidence provided by NTT is confidential information and is subject to non-disclosure and distribution limitations of NTT and/or any NTT sub-processor.
10.5 Client Audits. Client may carry out audits of NTT´s premises and operations as these relate to the Personal Data of Client if:
(a) NTT has not provided sufficient evidence of the measures taken under clause 9; or
(b) an audit is formally required by a data protection authority of competent jurisdiction; or
(c) applicable Data Protection Laws provide Client with a direct audit right (and as long as Client only conducts an audit once in any twelve-month period, unless mandatory applicable Data Protection Laws requires more frequent audits).
NTT subsidiaries are intended third-party beneficiaries of this section.
10.6 Client audit process. The Client audit may be carried out by a third party (but must not be a competitor of NTT or not suitably qualified or independent) who must first enter into a confidentiality agreement with NTT. Client must provide at least 60 days advance notice of any audit unless mandatory applicable Data Protection Laws or a data protection authority of competent jurisdiction requires shorter notice. NTT will cooperate with such audits carried out and will grant Client´s auditors reasonable access to any premises and devices involved with the processing of the Client’s Personal Data. The Client audits will be limited in time to a maximum of three business days. Beyond such restrictions, the parties will use current certifications or other audit reports to avoid or minimize repetitive audits. The Client must bear the costs of any Client audit unless the audit reveals a material breach by NTT of this DPA in which case NTT will bear the costs of the audit. If the audit determines that NTT has breached its obligations under the DPA, NTT will promptly remedy the breach at its own cost.
11. Incident management
11.1 Security incidents. If NTT becomes aware of a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to Personal Data while processed by NTT (each a ‘Security Incident’), NTT will promptly and without undue delay:
(a) notify Client of the Security Incident;
(b) investigate the Security Incident and provide Client with sufficient information about the Security Incident, including whether the Security Incident involves Personal Data of the Client;
(c) take reasonable steps to mitigate the effects and to minimize any damage resulting from the Security Incident.
11.2 Security incident notification. Notification(s) of Security Incidents will take place in accordance with clause 11.4. Where the Security Incident involves Personal Data of the Client, NTT will make reasonable efforts to enable Client to perform a thorough investigation into the Security Incident, to formulate a correct response, and to take suitable further steps in respect of the Security Incident. NTT will make reasonable efforts to assist Client in fulfilling Client’s obligation under applicable Data Protection Laws to notify the relevant data protection authority and data subjects about such Security Incident. NTT’s notification of or response to a Security Incident under this clause is not an acknowledgement by NTT of any fault or liability with respect to the Security Incident.
11.3 Other incidents. NTT will notify Client promptly if NTT becomes aware of:
(a) a complaint or a request with respect to the exercise of a data subject’s rights under any applicable Data Protection Laws in relation to Personal Data NTT processes on behalf of Client and its data subjects; or
(b) an investigation into or seizure of the Personal Data of Client by government officials, or a specific indication that such an investigation or seizure is imminent; or
(c) where, in the opinion of NTT, implementing an instruction received from Client in relation to the processing of Personal Data would violate applicable laws to which Client or NTT are subject.
11.4 Client notifications. Any notifications made to Client pursuant to this clause 11 will be addressed to the Client Contact.
12. General cross border transfers of Personal Data
12.1 Except as described elsewhere in the DPA, Personal Data that NTT processes on Client’s behalf may be transferred to and stored and processed in any country in which NTT or its sub-processors may operate.
12.2 Transfer restrictions. If an applicable Data Protection Law restricts cross-border transfers of Personal Data, the Client will only transfer that Personal Data to NTT if NTT, either through its location or participation in a valid cross-border transfer mechanism under the applicable Data Protection Laws, may legally receive that Personal Data.
12.3 Transfer mechanism. Where the parties determine that cross-border transfers of Personal data are necessary, the parties shall agree and implement the appropriate SCCs or other specific statutory mechanism prior to commencing such cross-border transfer. To the extent that NTT is relying on the SCCs or another specific statutory mechanisms to normalize international data transfers and those mechanisms are subsequently modified, revoked, or held in a court of competent jurisdiction to be invalid, Client and NTT agree to cooperate in good faith to promptly suspend the transfer or to pursue a suitable alternate mechanism that can lawfully support the transfer.
13. GDPR and UK GDPR cross border transfers of Personal Data
13.1 Where the GDPR or UK GDPR is the applicable Data Protection Law NTT may only process, or permit the processing, of Personal Data by the Services in respect of a Restricted Transfer under the following conditions:
(a) Adequacy decision. Where the European Commission or the UK (as applicable) has found that that the relevant countries provides adequate protection for the privacy rights of data subjects;
(b) Adequate safeguards. In the absence of an adequacy decision, where appropriate safeguards have been provided by the controller or processor established in third countries which do not ensure an adequate level of data protection, and who receive the Personal Data by way of a valid transfer mechanism under Article 46(2) of the GDPR, UK GDPR or other applicable Data Protection Law.
(c) Standard Contractual Clauses. SCCs may be used as follows:
(i) the UK SCCs’ for Personal Data subject to UK GDPR;
(ii) the applicable Module(s) of the EU SCCs for Personal Data subject to GDPR and/or Swiss Federal Act of 19 June 1992 on Data Protection (FADP).
13.2 Execution of SCCs. If any cross-border transfer of Personal Data between NTT and the Client requires execution of SCCs to comply with the applicable Data Protection Law, the parties will complete all relevant details in, and execute, the applicable SCCs, and take all other actions required to legitimize the transfer.
13.3 Sub-processors. Where Client provides it general written authorization to NTT (located in the EEA or UK, as applicable) appointing a sub-processor located outside the EEA or UK (as applicable), Client authorizes NTT to enter into the applicable form of the applicable SCCs with the sub-processor in Client’s name and on its behalf (in which case Client will no longer require to enter into direct agreements itself with such sub-processors). NTT will make the executed applicable SCC available to Client on request.
14. Return or destruction of Personal Data
14.1 Client deletion. For certain Services the Client is responsible for installing, hosting, processing and using Personal Data. Here only Client has the ability to access, extract and delete Personal Data stored in that Service. Where the particular Service does not support access, retention or extraction of software provided by Client, NTT has no liability for the deletion of Personal Data as described in this clause 14.1.
14.2 Delete or return. Where the Client Agreement requires NTT to retain Personal Data, NTT will delete that Personal Data within the time period agreed to in the Client Agreement, unless NTT is permitted or required by applicable law to retain such Personal Data. Where the retention of Personal Data has not been addressed in the Client Agreement, NTT will either delete, destroy or return all Personal Data to Client and destroy or return any existing copies when NTT has finished providing Services:
(a) related to the processing;
(b) this DPA terminates;
(c) Client requests NTT to do so in writing; or
(d) NTT has otherwise fulfilled all purposes agreed in the context of the Services related to the processing activities where Client does not require NTT to do any further processing.
14.3 Certificate of destruction. NTT will provide Client with a destruction certificate at Client’s request. Where the deletion or return of the Personal Data is impossible for any reason, or where backups and/or archived copies have been made of the Personal Data, NTT will retain such Personal Data in compliance with applicable Data Protection Laws.
14.4 Third parties. On termination of this DPA, NTT will notify all sub-processors supporting its own processing and make sure that they either destroy the Personal Data or return the Personal Data to Client, at the discretion of Client.
15. Liability and warranty
15.1 Any limitation of liability or monetary cap in the Client Agreement (including Terms of Service) will apply to this DPA, other than to the extent such limitation (a) limits the liability of the parties to data subjects rights or claims or (b) is not permitted by applicable law.
16. Notice
16.1 Any notice or other communication given to a party under or in connection with this DPA must be in writing and delivered to the other party by email.
16.2 Clause 16.1 does not apply to the service of any proceedings or other documents in any legal action or, where applicable, any arbitration or other method of dispute resolution.
16.3 Any notice or other communication will be deemed given when:
(a) delivered in person;
(b) received by mail (postage prepaid, registered or certified mail, return receipt requested); or
(c) received by an internationally recognized courier service (proof of delivery received by the noticing party) at the physical notice address (as identified above), with an electronic copy sent to the electronic notice address (as identified in the table above).
17. Miscellaneous
17.1 Conflict of terms. The Client Agreement terms remain in full force and effect except as modified in this DPA. Insofar as NTT will be processing Personal Data subject to applicable Data Protection Laws on behalf of the Client in the course of the performance of the Client Agreement, the terms of this DPA will apply. If the terms of this DPA conflict with the terms of the Client Agreement, the terms of this DPA will take precedence over the terms of the Client Agreement.
17.2 Governing law. This DPA is governed by the laws of the jurisdiction specified in the relevant provisions of the Client Agreement.
17.3 Dispute resolution. Any disputes arising from or in connection with this DPA will be brought exclusively before the tribunal specified in the relevant provisions of the Client Agreement.
17.4 Execution: This DPA may be executed in any number of counterparts, each of which will constitute an original, but which will together constitute one agreement. The parties will execute this DPA by electronic signature, and intend and agree that the electronic signature will have the same validity and legal effect as the use of a signature affixed by hand and is made with the intention of authenticating this DPA and evidencing the intention of that party to be bound by this DPA.
Attachment A: Particulars of Processing
Categories of data subjects whose personal data is transferred
Data subjects include the Client’s users including employees, contractors, and Clients. NTT acknowledges that, depending on Client’s use of the Services, NTT may process the personal data of any of the following types of data subjects:
- Employees, contractors, temporary workers, agents and representatives of Client;
- Users (e.g., clients end users) and other data subjects that are users of Client’s Services;
- Juristic persons (where applicable).
Categories of personal data transferred
NTT acknowledges that, depending on Client’s use of the Services, NTT may process the following types of Personal Data:
- Basic personal data (for example first name, last name, email address);
- Authentication data (for example username and password);
- Contact information (for example work email and phone number);
- Unique identification numbers and signatures (for example IP addresses);
- Biometric Information (for example fingerprints at NTT data centers);
- Location data (for example, geo-location network data);
- Device identification (for example IMEI-number and MAC address);
- Special category personal data as identified in Article 9 of the GDPR;
- Any other personal data identified in Article 4 of the GDPR.
The frequency of the transfer (e.g. whether the data is transferred on a one-off or continuous basis).
Personal data may be transferred on a continuous basis in order to provide the Services under the existing Client Agreement
Nature of the processing
The nature of processing personal data is for NTT to provide the Services under the existing Client Agreement.
Purpose(s) of the data transfer and further processing
NTT will Process Personal Data, as necessary to perform the Services pursuant to the Client Agreement to the extent determined and controlled by Client. Further, NTT will also Process and enrich the Personal Data in NTT’s systems to (i) improve, enhance, support and operate the Services and its availability; (ii) develop new products and services; (iii) compile statistical reports and insights into usage patterns.
NTT may further transfer Personal Data to third-party service providers that host and maintain NTT’s applications, backup, storage, payment processing, analytics and other services as specified in the section on sub-processors below. These third-party service providers may have access to or Process Personal Data for the purpose of providing these services to NTT.
The period for which the personal data will be retained, or, if that is not possible, the criteria used to determine that period
See clause 14 of the DPA
For transfers to (sub-) processors, also specify subject matter, nature and duration of the processing
In accordance with the DPA, NTT may engage sub-processors to provide some or all of the Services on NTT’s behalf or use any of current or future subsidiaries of NTT for the duration of the Client Agreement. Any such sub-processors will be permitted to obtain personal data only to provide some or all of the Services NTT has engaged them to provide, and they are prohibited from using personal data for any other purpose.
A list of sub-processors engaged by NTT is available.
Attachment B: Technical and Organizational Measures
NTT maintains Technical and Organizational Measures (‘TOMs’) to ensure it processes and protects Personal Data in a responsible way, considering the types of Personal Data that NTT processes, industry standards, the interests and rights of NTT’s employees, clients and communities, and the reasonable cost of implementation in accordance with clause 9 of the DPA and/or, as applicable, incorporated in the applicable SCCs and/or applicable Data Protection Laws. The TOMs maintained by NTT as referenced in this B are described at [ link – security (TOMs) ].
Attachment C: UK GDPR Terms
To the extent that the DPA does not address all of the issues in this Attachment C or provides lesser data protection commitments to Client in the DPA where NTT processes Personal Data within the scope of the UK GDPR on behalf of Client, NTT makes the commitments in this Attachment to the Client (‘UK GDPR Terms’, for short). These UK GDPR Terms do not limit or reduce any data protection commitments NTT makes to Client in the Client Agreement.
For purposes of these UK GDPR Terms, Client and NTT agree that Client is the controller and NTT is the processor of Personal Data, except when Client acts as a processor, in which case NTT is a sub-processor. These UK GDPR Terms do not apply where NTT is a controller of Personal Data.
18. Supplementary contractual measures
18.1 To the extent that the processing of Personal Data carried out by NTT is subject to the UK GDPR and NTT makes a transfer to its sub-processors the obligations set out in 1 to 1.11. inclusive will apply.
18.2 Each party warrants that it has no reason to believe that applicable laws to which it is subject, including any requirements to disclose Personal Data or measures authorising access by public authorities, prevent it from fulfilling its obligations under this DPA and the UK SCCs. Each party declares that in providing this warranty, it has taken due account in particular of the following elements:
(a) the specific circumstances of the processing, including the scale and regularity of processing subject to such applicable laws; the transmission channels used; the nature of the relevant Personal Data; any relevant practical experience with prior instances, or the absence of requests for disclosure from public authorities received by it for the type of Personal Data processed by it;
(b) the applicable laws to which it is/are subject, including those requiring to disclose data to public authorities or authorising access by such authorities, as well as the applicable limitations and safeguards; and
(c) safeguards in addition to those under this DPA, including the technical and organisational measures applied to the processing of the Personal Data by NTT and the relevant sub-processor.
18.3 Each party warrants that, in carrying out the assessment under clause 1.2, it has made best efforts to provide Client with relevant information and agrees that it will continue to cooperate with Client in ensuring compliance with this DPA. NTT agrees to document this assessment and make it available to Client on request and it agrees that such assessment may also be made available to a data protection authority.
18.4 NTT agrees to promptly notify Client if, after having agreed to this DPA and for the duration of the term of this DPA, it has reason to believe that it (or a relevant sub-processor to whom a transfer is made) is or has become subject to applicable laws not in line with the requirements under 1.2, including following a change of applicable laws to which is it (or the relevant sub-processor) is subject or a measure (such as a disclosure request) indicating an application of such applicable laws in practice that is not in line with the requirements under clause 1.2. Following such notification, or if Client otherwise has reason to believe that NTT can no longer fulfil its obligations under this DPA (including in relation to the relevant sub-processor), Client (and the relevant subsidiaries who are controllers) will promptly identify appropriate measures (such as, for instance, technical or organisational measures to ensure security and confidentiality) to be adopted by itself or NTT (and/or the relevant sub-processor), at Client’s cost, to address the situation, if appropriate in consultation with the competent data protection authority.
18.5 NTT agrees to promptly notify Client if it (or the relevant sub-processor to whom a transfer is made):
(a) receives a legally binding request by a public authority under applicable laws to which it (or the relevant sub-processor) is subject for disclosure of Personal Data; such notification will include information about the Personal Data requested, the requesting authority, the legal basis for the request and the response provided;
(b) becomes aware of any direct access by public authorities to Personal Data in accordance with applicable laws to which it (or the relevant sub-processor) is subject; such notification will include all information available to NTT (and the relevant sub-processor).
18.6 If NTT (or the relevant sub-processor to whom the transfer is made) is prohibited from notifying Client as set out in clause 1.4 it agrees to use its best efforts to obtain (and to procure that the relevant sub-processor obtains) a waiver of the prohibition, with a view to communicate as much information and as soon as possible. NTT agrees to document its (and the relevant sub-processor’s) best efforts in order to be able to demonstrate them upon request of Client.
18.7 To the extent permissible under the applicable laws to which NTT (and the relevant sub-processor) is subject, NTT agrees to provide to Client, for the duration of the processing, the relevant information on the requests received by it and the relevant sub-processor (in particular, number of requests, type of data requested, requesting authority or authorities, whether requests have been challenged and the outcome of such challenges, etc.).
18.8 NTT agrees to preserve the information pursuant to clauses 1.1 to 1.7 for the duration of the processing and make it available to the competent data protection authority upon request.
18.9 NTT agrees to review (and to procure that the relevant sub-processor to whom the transfer is made will review), having regard to applicable laws to which it (and the relevant sub-processor) is subject, the legality of the request for disclosure, notably whether it remains within the powers granted to the requesting public authority, and to exhaust all available remedies to challenge the request if, after a careful assessment, it (or the relevant sub-processor) concludes that there are grounds under applicable laws to which it (or the relevant sub-processor) is subject to do so. When challenging a request, NTT will (and will procure that the relevant sub-processor will) seek interim measures with a view to suspend the effects of the request until the court has decided on the merits. NTT will not (and will procure that the relevant sub-processor will not) disclose the Personal Data requested until required to do so under the applicable procedural rules. These requirements are notwithstanding the obligations on NTT pursuant to clause 1.4. NTT agrees to document its (and the relevant sub-processor’s) legal assessment as well as any challenge to the request for disclosure and, to the extent permissible under applicable laws to which it (or the relevant sub-processor) is subject, make it available to Client. It will also make it available to the competent data protection authority upon request.
18.10 NTT will use reasonable endeavours to provide (and to procure that the relevant sub-processor to whom the transfer is made will provide) the minimum amount of information permissible when responding to a request for disclosure, based on a reasonable interpretation of the request.
18.11 NTT will inform (and will procure that the relevant sub-processor to whom the transfer is made will inform) data subjects in a transparent and easily accessible format, on its website, of a contact point authorised to handle complaints or requests and NTT will (and will procure that the sub-processors will) promptly deal with any complaints.
5.3.4 - List of Sub-processors
Effective Date: 11 June 2025
We have updated our List of Sub processors effective as of the date indicated in the above header. For the previous version of our List of Sub processors please click here
In order to provide Samurai services, we make use of third party sub-processors to assist with components of our delivery. By using Samurai Managed Detection and Response powered by Samurai you authorize us to use these sub-processors. Third party sub-processors include:
| Name of sub-processor | Purpose | Location |
|---|---|---|
| Microsoft Azure | Cloud Hosting | EEA |
| Amazon Web Services | Cloud Hosting | EEA |
| Salesforce.com | CRM | EEA |
| Visma | ERP System | EEA |
| Sendgrid | Sending of email notifications | USA |
EEA - European Economic Area
Group Sub-processors
The following entities are group members of NTT Security Holdings and function as sub-processors in providing support, maintenance and research and development:
| Group Company | Location |
|---|---|
| NTT Security (Sweden) AB | Sweden |
| NTT Security (Japan) KK | Japan |
| NTT Security Holdings Corporation | Japan |
NTT Security Holdings reserves the right to add or replace sub-processors named in this document as required for delivery of services. We will notify you by email or by means of a notice on this page prior to any addition or replacement becoming effective. By continuing to use Samurai you consent to the additional or replacement sub-processors and reaffirm your authorization to us to use the sub-processors.
5.3.5 - Master Partner Agreement
Effective Date: 11 June 2025
We have updated our Master Partner Agreement effective as of the date indicated in the above header. For the previous version of our Master Partner Agreement, please click here.
MASTER PARTNER TERMS AND CONDITIONS
1.Definitions.
1.1 “Affiliate” means any majority-owned subsidiary or other entity which a party controls or is controlled by, or with which it is under common control with a party.
1.2 “Consulting” means the consulting services provided by NTT as provided for under the terms of the applicable Service Descriptions. By way of example, Consulting may include, incident response and investigation, compromise assessments, forensic services related to cyber security adversaries, tabletop exercises and penetration tests related to cyber security and typically provided on a time and material basis and sometimes sold as a retainer.
1.3 “Customer(s)” means the current or potential customers of Partner for the applicable NTT Samurai Services or Consulting excluding any entity or person deemed in NTT reasonable discretion as a competitor of NTT; provided, when “Customer” is used in the Terms of Service as referenced in Sections 1.10, 2.1, 2.4 and 2.6 of this Agreement, it shall mean Partner.
1.4 “Evidence Data" means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
1.5 “Intellectual Property Rights” means copyrights (including, without limitation, the exclusive right to use, reproduce, modify, distribute, publicly display, and publicly perform the copyrighted work), trademark rights (including rights in, without limitation, trade names, trademarks, service marks, and trade dress), patent rights (including, without limitation, (i) all rights worldwide in patent applications, any patents issuing therefrom, and all provisional rights with respect to patent applications, (ii) all rights worldwide in any improvements, substitutions, divisionals, patents of addition, continuations, continuations-in-part, reissues, renewals, registrations, confirmations, re-examinations, extensions, supplementary protection certificates, term extensions (under applicable patent law or regulation or other law or regulation), and certificates of invention of any patents or patent applications, and (iii) all rights worldwide to exploit any of the foregoing), know-how, trade secrets, moral rights, right of publicity, authors’ rights, contract and licensing rights, all other intellectual property rights as may exist now and/or hereafter come into existence, and all renewals and extensions thereof, regardless of whether such rights arise under the law of the Territory or any other state, country, region, or jurisdiction.
1.6 “NTT Content” means NTTs proprietary data that is contained in or made available as part of Services and Consulting.
1.7 “Samurai Services” consists of NTT MDR offerings for security operations management which are listed and further described in the relevant Service Descriptions.
1.8 “Services” means Samurai Services and Consulting. The Service Descriptions for the Services can be found here https://docs.mdr.security.ntt/docs/reference/legal/service_descriptions/
1.9 “Trademarks” means the words, names, symbols, designs, or any combination thereof, used in commerce to identify and distinguish the products, services, and company, of a party from those of others and to indicate the source of such consulting and services.
1.10 “Terms of Service” or “ToS” means the current standard terms, conditions, and legal notices, applicable to the Samurai Services found here https://docs.mdr.security.ntt/docs/reference/legal/, including any product specific terms that are included in valid quotes issued by NTT and related to the Samurai Services.
1.11 “Territory” means the jurisdiction(s) listed in the Cover sheet.
1.12 “Partner Tier” means the type of obligations to, and benefits and support the Partner will receive from, NTT as defined in the Partner Program Guide
1.13 “End User Agreement” means the same as “Terms of Service” as defined in clause 1.10 above.
2. Appointment and Restrictions.
2.1 Nonexclusive Appointment. Provided that Partner complies at all times with the terms and conditions of this Agreement, NTT appoints Partner and Partner accepts appointment as a nonexclusive Partner with non-transferable, limited right to market and promote the Services to Customers within the Territory provided, Partner shall expressly accept and agree to the Terms of Service with NTT prior to accessing the Services. The applicable Samurai Services and Consulting to which this appointment applies will be specified in the applicable Service Description(s). Partner agrees that nothing in this Agreement shall be construed to preclude NTT from directly or indirectly marketing, distributing, selling, or servicing any Services or Consulting to or for any third party in any location, including without limitation, other partners, resellers, distributors, managed service providers, and end-users. The rights and licenses granted to Partner under this Agreement are personal to Partner and Partner may not transfer or sublicense the appointment set forth in this Agreement.
2.2 Ownership. Except for the limited license(s) expressly granted to Partner in this Agreement, all right, title and interest in and to the Services, Consulting, NTT Content, including the concepts and technology inherent in the Services, NTT Content and deliverables, all Intellectual Property Rights related thereto, shall at all times be and remain, relative to Partner, the sole and exclusive property of NTT. No other licenses, immunity or rights, express or implied are granted by NTT, by implication, estoppel, or otherwise.
2.3. Restrictions. Partner shall, by all appropriate means, prevent unauthorized disclosure, publication, display or use of the Services, Consulting and NTT Content. Partner shall not, and shall not encourage or authorize any third party to, modify or reverse engineer any Services or the technology related thereto, or attempt to gain unauthorized access to the Services or the NTT Content. Partner shall not remove, alter, cover or obfuscate any end-user agreement, privacy notice, copyright notices or other proprietary legends placed or embedded by NTT on or in the Services documentation, NTT Content, deliverables or literature related to any of the foregoing. Partner shall not affix or place any labels or markings on the Services, Consulting output, Service deliverables, or literature related to the foregoing, that might be interpreted as a claim of ownership by Partner or any third party in the foregoing.** Without NTT’s prior written consent (an email from the Chief Operating Officer shall suffice), Partner shall not, nor have a third party, (i) perform a competitive analysis on the Services or Consulting, or (ii) publish a review or the results of any internal evaluation of the Services or Consulting.
2.4 Terms of Service. With respect to each accepted quote for Services, Partner shall expressly accept and agree to be bound by the Terms of Service with NTT. Partner shall not be granted, and shall not grant to Customers, any access, use or other rights to the Services, unless Partner has accepted and agreed to the Terms of Service. Partner will promptly report to NTT any breach, or suspected breach, of the Terms of Service of which it becomes aware. NTT reserves the right to refuse to issue a quote, accept an order, or make the Services available to any Customer; provided that NTT provides to Partner a written notice of its objection to such Customer.
2.5 Changes to ToS. Partner acknowledges that NTT may update the Terms of Services from time to time as set forth in the Terms of Service.
2.6 Governing Terms and Conditions. Partner acknowledges and agree that, A) as to Partner, NTT’s obligations to Partner shall be as stated in this Agreement and the Terms of Service, and B) as to Customers, i) Partner shall be solely liable to Customers.
2.7 Partner Tier. Partner agrees to abide by the obligations of the Tier they hold. Partner further agrees that should they cease to meet such obligations NTT may, at it’s sole discretion, reduce Partner’s tier or remove Partner’s status as a Partner.
2.8 Partner Conduct. Partner shall: (i) conduct business in a manner that reflects favorably at all times on the Services, Consulting, goodwill and reputation of NTT; (ii) avoid deceptive, misleading or unethical practices that are or might be detrimental to NTT; (iii) refrain from making any false or misleading representations or warranties with regard to NTT, the Services or Consulting; and (iv) comply with all applicable laws, rules, ordinances, decrees and regulations applicable to Partner’s activities under this Agreement, including without limitation, any applicable privacy laws and the Foreign Corrupt Practices Act, export laws and sanctions regulations or any similar legislation. Partner has reviewed and understands NTT’s Privacy Notice located at https://docs.mdr.security.ntt/docs/reference/legal/privacy_policy/. Partner shall not, directly or indirectly, through action or inaction, cause NTT to be in violation of its Privacy Notice or applicable laws.
2.9 Affiliate Appointment. An Affiliate of Partner may be authorized by NTTSH to resell Services pursuant to and in accordance with the terms and conditions of this Agreement, provided such Affiliate is approved by NTTSH and executes and delivers an agreement in form and substance required by NTTSH whereby Affiliate adopts and agrees to be bound by this Agreement (an “Adoption Agreement”). Any such Adoption Agreement shall constitute an individual contractual relationship between the respective Affiliate and NTTSH and will govern any purchase order executed or issued by such Affiliate. Each Affiliate shall only be liable under the Adoption Agreement it has executed, and NTTSH shall be liable only to the Affiliate executing such Adoption Agreement. In no event shall either NTTSH or Partner have recourse or be liable to the other or another Affiliate with regard to any acts or omissions, obligations, duties, or claims under an Adoption Agreement or any local purchase order entered into by the Affiliates and NTTSH.
3. Services. During the term of the MPA and subject to the terms and conditions therein and herein, NTT agrees to provide certain: (i) Samurai Services, and/or (ii) Consulting services purchased by Partner in accordance with the terms of this MPA. The Services purchased are specified in a quote delivered by NTT and accepted by Partner without alteration (“Order”) or statement of work (“SOW”) executed (or, if online, accepted pursuant to an online order process) by the parties which references this MPA. A detailed description of the Services being purchased is provided in the service description and for such Services attached to the Order (or linked to if the Partner is purchasing online) and incorporated therein by reference. All Orders (whether signed or accepted pursuant to an online order process) and all SOWs are subject to the terms and conditions of this MPA and will include the following: (i) the particular Services to be performed, including, if applicable, the applicable Specification Document; (i) the subscription term of the Services; (iii) the compensation and billing method for the Services; and (iv) any other applicable information agreed to by the parties.
4. Go To Market and Use of Trademarks.
4.1 Go To Market. Subject to the terms of this Section 4, each party will have the right to refer to the fact that Partner is in a collaborative relationship with NTT on its website and in marketing collateral. Otherwise, neither party will make any public statement or issue any press release with respect to this relationship without the prior written consent of the other party.
4.2 Trademark Use. Each party (the “Trademark Party”) grants the other party a worldwide, non-exclusive, non-transferable royalty free limited license (with no right of sublicense) during the term of this Agreement to use the Trademark Party’s Trademarks solely for the purpose of carrying out the terms of the Go To Market Plan and as otherwise contemplated by this Agreement, including but not limited to, the promotion of the Services and Consulting, the parties’ joint efforts and channel programs; provided, that, such Trademarks are used solely in accordance with the Trademark Party’s specifications as to style, color, and typeface, as such specifications may be modified by such party from time to time and communicated to the other party. Partner agrees not to attach any other trademarks, logos or trade designations to the Services, nor to remove or modify any of NTT’s Trademarks or proprietary notices affixed to the Services, Service deliverables or documentation. Partner shall not affix any NTT Trademarks to services other than the genuine Services. Upon notice from the Trademark Party of its objection to any improper or incorrect use of the Trademark Party’s Trademarks, the other party shall correct or stop such usage as soon as reasonably practicable.
4.3 Ownership of Trademarks. Each Trademark Party claims ownership of all right, title, and interest in and to its Trademarks, together with any new or revised trademarks, trade names, and logos that such Trademark Party may adopt to identify it or any of its products or services. Neither party shall claim any rights in the other party’s Trademarks or take any action that threatens or challenges the Trademark Party’s proprietary rights therein. All use by a party of the Trademark Party’s Trademarks and all goodwill associated therewith shall inure exclusively to the benefit of the Trademark Party and its Affiliates. Partner is prohibited from using or registering any of NTT’s Trademarks or domain names, including without limitation any terms containing the terms “Samurai” as part of Partner’s company name, service name, trade names or domain names. NTT does not authorize Partner’s use of any of the NTT Trademarks to promote or use for search engine ranking or ad word purchase or as part of a trade name, business name or Internet domain name in any manner that could be detrimental to the interests of NTT. If Partner registers or otherwise obtains rights to marks (as trademarks, service marks, URLs, company names or otherwise) in violation of this Agreement, Partner will, at its own expense, transfer and assign such rights to NTT, and execute all documents reasonably requested by NTT to facilitate such assignment or transfer.
5. Samurai Service Fees. NTT’s’ fees for the Samurai Services are set forth on the Order. The Samurai Services ordered will commence on the date set forth in the Order (the “Commencement Date”), and NTT shall invoice Partner for Samurai Services on the Commencement Date and thereafter in advance on the renewal date. If there is no date in the Order, the date on which the Quote was accepted shall be the Commencement Date.
6. Consulting Service Fees. NTT’s fees and billing milestones for the Consulting Services are set forth on the applicable Order or Statement of Work (“SOW”) (as applicable).
7. Invoice and Payment. NTT will invoice Partner in accordance with the billing terms set forth and detailed on the applicable Order or SOW. All charges, fees, payments and amounts hereunder will be in currency designated in the applicable Order or SOW, and (ii) all undisputed amounts due hereunder are payable within thirty (30) days from the date of the invoice, which shall be submitted to Partner electronically (the “Invoice Due Date”).
8. Disputes and Nonpayment. Partner shall have the right to reasonably, and in good faith, dispute any invoice or any portion of any invoice claimed by NTT as due and payable provided that, prior to the Invoice Due Date, Partner (i) timely pays any undisputed portion of the amount due and payable, and (ii) provides NTT with written notice specifying the disputed amount and the basis for the dispute in reasonable detail. Except for amounts that are disputed in good faith by Partner in accordance with this Section 8, NTT reserves the right to charge Partner a late fee of one and a half percent (1.5%) per month or the maximum rate permitted by law, whichever is less, for invoices not paid on or before the Invoice Due Date. In addition, NTT, without waiving any other rights or remedies to which it may be entitled, shall have the right, upon prior written notice to Partner, to suspend the Services until such payment is received.
9. Taxes. Partner shall be responsible for the payment of all taxes and fees assessed or imposed on the Services provided or the amounts charged under the Order/SOW in any country or territory in which the Partner receives the benefit of the Services, including any sales, use, excise, value-added, or comparable taxes, but excluding taxes: (i) for which the Partner has provided a valid resale or exemption certificate, or (ii) imposed on NTT’ income or arising from the employment relationship between NTT and its employees. Should any payments become subject to withholding tax, the Partner will deduct these taxes from the amount owed and pay the taxes to the appropriate tax authority in accordance with applicable tax laws. Partner will promptly provide NTT with receipts or documents evidencing these tax payments. NTT shall not be liable for any withholding tax, penalty or interest due as a result of Partner’s failure to withhold any applicable tax.
10. Change Control. “Change” means any change to the scope of engagement that (i) would modify NTT’s obligations in relation to delivery of the Services, or (ii) would alter the cost to Partner for the Services, or (iii) is agreed by Partner and NTT in writing to be a Change. From time to time during the term of the Services, Partner or NTT may propose Changes to the scope of the engagement. Any Change to the applicable Order/SOW shall be implemented by request for, issuance of, and acceptance of a quote. For the avoidance of doubt, change described in this Section 10 does not apply to the composition of the Samurai Service as defined in the Service Description.
11.Confidentiality.
11.1 Definitions. In connection with this Agreement, each party (“Recipient”) may be exposed to or acquire Confidential Information of the other party (“Discloser”) or third parties to whom Discloser has a duty of confidentiality. “Confidential Information” means non-public information in any form and regardless of the method of acquisition that the Discloser designates as confidential to Recipient or which, due to the nature of such information and/or under the circumstances surrounding disclosure ought to be treated as confidential by the Recipient. Confidential Information shall not include information that is: (i) in or becomes part of the public domain (other than by disclosure by Recipient in violation of this Agreement); (ii) previously known to Recipient (which must be demonstrable) without an obligation of confidentiality; (iii) independently developed by Recipient without use of Discloser’s Confidential Information; (iv) rightfully obtained by Recipient from third parties without an obligation of confidentiality, or (v) Evidence Data.
11.2 Restrictions on Use. Recipient shall hold Discloser’s Confidential Information in strict confidence and shall not disclose any such Confidential Information to any third party, other than to its employees, agents and consultants, including without limitation, counsel, accountants and advisors (collectively, “Representatives”) and its Affiliates and their Representatives who need to know such information and who are bound by restrictions regarding disclosure and use of such information comparable to and no less restrictive than those set forth herein. Recipient shall not use Discloser’s Confidential Information for any purpose other than to carry out the terms of this Agreement and further the parties’ business relationship. Recipient shall take the same degree of care that it uses to protect its own confidential information of similar nature and importance (but in no event less than reasonable care) to protect the confidentiality and avoid the unauthorized use, disclosure, publication or dissemination of the Discloser’s Confidential Information. Recipient shall promptly notify Discloser of any breach of this Agreement that it becomes aware, and in any event, shall be responsible for any breach of this Agreement by any of its Affiliates, Representatives or Affiliates’ Representatives.
11.3 Exceptions. Recipient may disclose Discloser’s Confidential Information: (i) to the extent required by applicable law or regulation, or (ii) pursuant to a subpoena or order of a court or regulatory, self-regulatory or legislative body of competent jurisdiction, or (iii) in connection with any regulatory report, audit or inquiry, or (iv) where requested by a regulator with jurisdiction over Recipient. In the event of such a requirement or request, Recipient shall to the extent permissible by law give the Discloser prompt written notice of such requirement or request prior to such disclosure and reasonable assistance (at Discloser’s expense) in obtaining an order protecting the information from public disclosure. NTT and Partner agree that the terms and conditions of this Agreement as it relates to the other party shall be treated as Confidential Information and shall not be disclosed to any third party except as otherwise provided in this Section 11 (Confidentiality) and (i) in connection with the enforcement of this Agreement or rights under this Agreement; or (ii) in confidence, in connection with an actual or proposed merger, acquisition or similar transaction.
11.4 Return or Destruction. Upon Discloser’s written request, Recipient shall use commercially reasonable efforts to either return or destroy the Confidential Information and any copies or extracts thereof. However, Recipient, its Affiliates and their Representatives may retain any Confidential Information that: (i) they are required to keep for compliance purposes under a document retention policy or as required by applicable law, professional standards, a court or regulatory agency; or (ii) have been created electronically pursuant to automatic or ordinary course archiving, back-up, security or disaster recovery systems or procedures; provided, however, that any such retained information shall remain subject to this Agreement. If Recipient elects to destroy Discloser’s Confidential Information (subject to any retention rights provided in this Agreement), Discloser may request that Recipient provide it with written confirmation of destruction in compliance with this provision.
11.6 Equitable Relief. Each party acknowledges that a breach of this Section 11 (Confidentiality) shall cause the other party irreparable injury and damage. Therefore, each party agrees that those breaches may be stopped through injunctive proceedings in addition to any other rights and remedies which may be available to the injured party at law or in equity without the posting of a bond.
11.6 NTT Development; Communications. It is expressly understood, acknowledged and agreed that Partner may, regardless of whether or not formally requested, provide to NTT suggestions, comments and feedback regarding the Services or Consulting, including but not limited to usability, bug reports and test results, with respect to the foregoing (collectively, “Feedback”). Partner grants NTT, under all of its intellectual property and proprietary rights, the following worldwide, non-exclusive, perpetual, irrevocable, royalty free, fully paid up rights without any attribution of any kind: (i) to make, use, copy, modify, sell, distribute, sub-license, and create derivative works of, the Feedback as part of any NTT Service or Consulting or related technology, specification or other documentation; (ii) to publicly perform or display, import, broadcast, transmit, distribute, license, offer to sell, and sell, rent, lease or lend copies of the Feedback (and derivative works thereof) as part of any NTT’s Service or Consulting or related technology, specification or other documentation; (iii) solely with respect to your copyright and trade secret rights, to sublicense to third parties the foregoing rights, including the right to sublicense to further third parties; and (iv) to sublicense to third parties any claims of any patents owned or licensable by Partner that are necessarily infringed by a third party product, technology or service that uses, interfaces, interoperates or communicates with the Feedback or portion thereof incorporated into an NTT Service or Consulting or related technology, specification or other documentation. Further, Partner warrants that its Feedback is not subject to any license terms that would purport to require NTT to comply with any additional obligations with respect to any NTT Service or Consulting or related technology, specification or other documentation that incorporate any Feedback.
12.Representations and Warranties.
12.1 Each party represents and warrants that it has full power and authority to execute this Agreement and to take all actions required by, and to perform the agreements contained in, this Agreement, and that each party’s obligations under this Agreement do not conflict with its obligations under any other agreement to which it is a party.
12.2 WARRANTY DISCLAIMER. EXCEPT FOR ANY LIMITED EXPRESS WARRANTIES MADE BY NTT FOR THE SERVICES AND/OR CONSULTING IN ITS END USER AGREEMENT(S) (WHICH SHALL BE APPLICABLE ONLY IF PARTNER OR CUSTOMER IS AN END USER OF THE APPLICABLE SERVICE OR CONSULTING UNDER SUCH AN AGREEMENT), NTT MAKES NO OTHER WARRANTIES RELATING TO THE SERVICES OR CONSULTING, EXPRESS, IMPLIED OR STATUTORY (EXCEPT FOR THOSE PRESCRIBED BY LAW WHICH CANNOT BE EXCLUDED), INCLUDING WITHOUT LIMITATION ANY WARRANTIES OF NON-INFRINGEMENT OF THIRD PARTY RIGHTS, FITNESS FOR A PARTICULAR PURPOSE, OR MERCHANTABILITY. PARTNER ACKNOWLEDGES, UNDERSTANDS AND AGREES THAT NTT DOES NOT GUARANTEE OR WARRANT THAT USE OF THE SERVICES OR CONSULTING WILL FIND, LOCATE OR DISCOVER ALL SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND WILL NOT HOLD NTT RESPONSIBLE THEREFOR. PARTNER AGREES NOT TO REPRESENT TO CUSTOMER OR ANY THIRD PARTY THAT NTT HAS PROVIDED SUCH GUARANTEE OR WARRANTY. NTT SERVICES ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENTS REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NTT SERVICES ARE NOT FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY OR PROPERTY DAMAGE.
12.3 No individual is authorized by NTT to make any warranty or representation concerning the performance of the Services or Consulting. Partner shall make no warranty, express or implied, on behalf of NTT.
13. Indemnification.
13.1 Infringement Indemnity. NTT will defend, at its own expense, a third-party claim, suit or proceeding brought against Partner insofar as it is based on a claim that a Service or a Consulting deliverable when used by Partner in accordance with the terms of this Agreement, constitutes an infringement of a patent or copyright valid within the Territory. NTT shall pay all damages, costs and expenses finally awarded to third parties as a result of a final judgment against Partner or settlement of such claim negotiated by NTT, but shall not be responsible for any compromise made without its consent. To qualify for such defense and payment, the Partner must: (i) give NTT prompt written notice of any such claim, and (ii) allow NTT to control, and fully cooperate with NTT in, the defense and all related settlement negotiations. Upon notice of an alleged infringement, or if, in NTT’s opinion, such a claim is likely, NTT shall have the right, at its option, to obtain the right to continue the distribution of Services, substitute other products or services with similar operating capabilities and/or performance, or modify the Service or Consulting deliverable so that it is no longer infringing or subject to a third party claim. In the event that none of the above options are reasonably available in NTT’s sole discretion, NTT may terminate this Agreement’ and all accompanying subscription licenses. In the event of such termination, NTT shall, without limiting its obligation to defend and indemnify Partner, refund to Partner: (i) the fees paid for Services subscriptions prorated for the remainder of any pre-paid subscription term unused by the Customer, or (ii) the portion of the fees attributable to the Service deliverable, as applicable. This Section 13 (Infringement Indemnity) states NTT’s entire liability under this Agreement for all claims of intellectual property infringement. NTT shall not be responsible for any claim of infringement that arises from (i) modifications to a Service or Consulting deliverable not made by NTT, (ii) use of a Service or Consulting deliverable in a manner or in combination with products or services not provided by NTT to the extent such claim would not have occurred except for such modifications, use or combination; (iii) use of other than the latest available version of the Services or Consulting deliverable made available to Partner or the Customer; or (iv) any use of the Services or Consulting deliverable not in accordance with this Agreement or the applicable end user terms, documentation or specifications.
13.2 Indemnity. NTT and Partner (each an “Indemnitor”) shall defend and indemnify the other party and its Affiliates, and their officers, directors, employees, and agents (collectively, “Indemnitees,” respectively, for each of NTT and Partner), from any third party claims and the associated costs, damages or settlement (inclusive of attorney’s fees and court costs) that an Indemnitee may incur as a result of: (i) an Indemnitor’s breach of this Agreement or any agreement with the Customer; (ii) an Indemnitor making a representation, warranty, or other statement to a Customer on behalf of the other party that is not specifically authorized in writing; or (iii) an Indemnitor’s or its representative’s gross negligence, fraud or willful misconduct. To qualify for such defense and payment, the Indemnitee must: (i) give the Indemnitor prompt written notice of any such claim, and (ii) allow Indemnitor to control, and fully cooperate with Indemnitor in, the defense and all related settlement negotiations.
14.Limitation of Liability. Each party’s sole remedy and the other party’s sole obligation shall be governed by this Agreement.
14.1.Maximum Liability.
EXCEPT IN THE CASE OF NTT’s DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.1, AND EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.2, IN NO EVENT SHALL EITHER PARTY’S LIABILITY TO THE OTHER EXCEED THE GREATER OF: (A) THE AGGREGATE AMOUNTS PAID OR OWED BY PARTNER TO NTT UNDER THIS AGREEMENT WITH RESPECT TO THE SERVICE OR CONSULTING DELIVERABLE THAT IS SUBJECT OF THE CLAIM IN THE 12 MONTHS PRECEDING THE FIRST OCCURRENCE OF THE EVENTS GIVING RISE TO ANY CLAIM, OR (B) $250,000.
14.2 EXCEPT IN THE CASE OF EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13 IN NO EVENT SHALL A PARTY BE LIABLE TO THE OTHER PARTY FOR ANY SPECIAL, INDIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING FROM BREACH OF WARRANTY, BREACH OF CONTRACT, NEGLIGENCE, OR ANY OTHER LEGAL THEORY, WHETHER IN TORT OR CONTRACT, EVEN IF SUCH PARTY IS AWARE OF THE LIKELIHOOD OF SUCH DAMAGES OCCURRING. NTT SHALL NOT BE RESPONSIBLE FOR ANY DAMAGES OR EXPENSES RESULTING FROM ALTERATION OR UNAUTHORIZED USE OF THE SERVICE, OR FROM THE UNINTENDED AND UNFORESEEN RESULTS OBTAINED BY PARTNER OR ANY CUSTOMERS RESULTING FROM SUCH USE.
15.Legal Compliance.
15.1 Export. The parties shall comply with all applicable United States and foreign laws and regulations, including without limitation: (i) all applicable laws and regulations relating to the advertising, packaging, sale, and distribution of the Service and Consulting deliverables, (ii) all United States export laws and regulations governing the export or re-export of all Services/Consulting and any products or services provided in connection with the Services/Consulting, including without limitation the U.S. Export Administration Regulations, the International Traffic in Arms Regulations, and any regulations administered by the Department of the Treasury’s Office of Foreign Assets Control, and (iii) all applicable laws and regulations of countries other than the United States that govern the importation, use, or re-export of the Services/Consulting. Partner further agrees to comply with any reasonable conditions that NTT notifies Partner are contained in any applicable export licenses pertaining to the Services/Consulting. Partner shall comply with any reporting requirements that may apply to the export or re-export of the Services/Consulting deliverables and shall provide to NTT and the appropriate governmental authority any periodic reports containing such information as may be required under applicable law. Partner further agrees to pay any taxes or tariffs that may apply to the export, or re-export of the Services/Consulting.
15.2 Sanctions. Partner warrants that (i) neither it or its Affiliates are subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”), and (ii) if at any time it or an Affiliate become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under this Agreement, or the continuing performance of this Agreement exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate this Agreement.
15.3 Applicable Laws. The parties shall at all times conduct their efforts hereunder with the highest commercial standards and in strict accordance with all applicable laws, rules, directives and regulations (“Laws”). Each party shall be responsible for current and ongoing familiarity and compliance with all Laws applicable to the importation, distribution, marketing, sale, operation, use or support of the Services and Consulting, and the privacy and protection of personal data.
15.4 Anti-bribery. Each party will maintain adequate policies and procedures designed to ensure that its officers, directors, employees and contractors comply, at all times, with all relevant and applicable laws concerning anti-bribery and corruption.
15.5 Foreign Corrupt Practices Act. In conformity with the United States Foreign Corrupt Practices Act and with NTTs policies regarding foreign business practices, Partner and its employees and agents shall not directly or indirectly make and offer, payment, promise to pay, or authorize payment, or offer a gift, promise to give, or authorize the giving of anything of value for the purpose of influencing an act or decision of an official of any government (including a decision not to act) or inducing such a person to use his or her influence to affect any such governmental act or decision in order to assist Partner and/or NTT in obtaining, retaining or directing any such business.
16.Personal Information. Subject to compliance with applicable laws, including data protection laws, each party reserves the rights to transfer (both domestically and cross-border) and disclose information, including relevant confidential information and, as applicable, personal data of the other party’s personnel to the receiving party’s (and its affiliates’) directors, officers, employees, contractors, professional advisors, and third-party service providers, solely as needed to support or facilitate the performance and administration of the Agreement by the receiving party, provided that such information will be disclosed a) on a need-to-know basis only (based on the receiving party’s business operations); and b) subject to appropriate obligations of confidentiality and/or personal data transfer arrangements with such parties, as applicable.
17.Termination.
17.1 Term. The term of this Agreement shall commence as of the Effective Date of this Agreement and continue until terminated by either party as provided herein.
17.2 Termination Without Cause. Upon ninety (90) days prior written notice and payment of any unpaid amounts owed by the terminating party, either party may terminate this Agreement at any time without cause to the other party.
17.3 Termination With Cause. Either party may terminate this Agreement upon 30 days written notice for a material breach of this Agreement if such breach is not cured within such 30-day period.
17.4 Rights Upon Termination. Upon any termination of this Agreement: (i) Partner shall remit all a) accrued but unpaid amounts due NTT and b) the unamortized portion of any fees prepaid by clients for Services or Consulting less the agreed Partner discounts (Samurai MDR subscription discounts (RRP), Services discounts, Additional subscription discounts and possible other agreed discounts),, (ii) Partner is no longer authorized to conduct any activities under this Agreement; (iv) Partner shall immediately cease using the Trademarks of NTT and discontinue all representations that it has a relationship with NTT; and (iv) Partner shall promptly return to NTT any tangible sales literature, brochures, technical information, price lists, samples, evaluation units, and other materials received from NTT or if intangible, destroy such items in a secure manner, except to the extent such materials are reasonably required for delivery of Services or provisions of Consulting ordered prior to termination as directed by NTT.
17.5 Survival. The Sections entitled Ownership, Restrictions, Ownership of Trademarks, Confidentiality, Warranty Disclaimer, Indemnification, Limitation of Liability, Rights Upon Termination, Survival and Miscellaneous shall survive expiration or termination of this Agreement for any reason.
18.Order of Precedence. In the event of a conflict between the terms of the MPA, and an Order/SOW (including any exhibits or attachments thereto), the terms of the Order/SOW shall govern but only as regards such Order/SOW.
19. Miscellaneous.
19.1 Assignment. Partner may not assign this Agreement without the prior written approval of NTT. For the purposes of this section, a change in the persons or entities that control 50% or more of the equity securities or voting interest of Partner shall be considered an assignment of Partner’s rights. NTT may assign this Agreement at any time and may delegate aspects of its performance under this Agreement to any of its Affiliates.
19.2 Audit Rights. Once per calendar year, upon reasonable notice and during Partner’s normal business hours, NTT shall have the right to audit, through an independent third party auditor selected by NTT and approved by Partner (which approval will not be unreasonably withheld or delayed) Partner’s books of account and business records as necessary to verify Partner’s compliance with this Agreement, including but not limited to, compliance with the requirements of Sections 2.1, 2.4 and 2.5 and the accuracy of the amounts paid pursuant to this Agreement. The auditor may disclose to NTT Security Holdings, with a written copy to Partner, only whether the amounts paid are correct or incorrect and the amount of any discrepancy. No other information may be provided to NTT Security Holdings. If the auditor identifies a discrepancy, the appropriate party shall pay to the other party the amount of the discrepancy (plus interest) within thirty (30) days of the date Partner receives the auditor’s written report.
19.3 Notices. All notices given pursuant to this Agreement shall be in writing and effective: (i) upon receipt if hand delivered; (ii) on the next day after being sent by email if followed by the methods in subsections (iii) or (iv); (iii) on the third business day after being sent prepaid by certified or registered mail; or (iv) on the second business day after being sent prepaid by commercial express courier. Notices to NTT shall be sent to Råsundavägen 12, 169 67 Solna, Sweden, Attention: COO, with a copy to legal@security.ntt. Notices to Partner will be sent to the address first set forth above, attention Chief Executive Officer for Partner, with a “copy to:” _______________.
19.4 Waiver. The waiver by either party of a breach of any provision contained herein shall be in writing and shall in no way be construed as a waiver of any succeeding breach of such provision or the waiver of the provision itself.
19.5 Severability. In the event that any provision of this Agreement shall be unenforceable or invalid under any applicable law or be so held by applicable court decision, such unenforceability or invalidity shall not render this Agreement unenforceable or invalid as a whole. In such event, such provision shall be changed and interpreted so as to best accomplish the objectives of such provision within the limits of applicable law or applicable court decisions, or if necessary to maintain the validity of the remaining terms, removed from the Agreement.
19.6 Controlling Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules.. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
19.7 Dispute Resolution and Attorneys’ Fees. Except for claims for breach of confidentiality obligations, the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
19.8 No Agency. The use of the term “Partner” is for convenience and does not reflect an intention of the parties to form a legal partnership. The parties are independent contractors under this Agreement, and nothing contained herein shall be construed as creating any agency, partnership, employment, or other form of joint enterprise between the parties and nothing contained in this Agreement (including use of the term “Partner”) will be construed to (i) give either Party the power to direct and control the day-to-day activities of the other, (ii) create a principal-agent or employer-employee relationship, or (iii) give either Party the authority to bind the other Party to any contract with a third party.
19.9 Force Majeure. NTT, NTT agents and Affiliates, Partner and Partner’s agents shall not be liable for any delay or failure to perform for any cause beyond their reasonable control, except for the payment of money, to the extent that performance is rendered impossible by strike, fire, flood, wars, sabotage, civil unrest, governmental acts, or any other reason where failure to perform is beyond the reasonable control of and is not caused by the negligence of the nonperforming party.
19.10 Counterparts and Electronic Copies. This Agreement may be e-signed. Further, if this Agreement is signed in two counterparts, the two counterparts together shall form a single agreement as if both parties had executed the same document. Electronic copies (e.g., .pdf, .tif) and facsimile signature pages shall be binding as if original.
19.11 Entire Agreement; Order of Precedence. This Agreement completely and exclusively states the agreement of the parties regarding its subject matter. This Agreement supersedes all prior proposals, agreements or other communications between the parties, oral or written, regarding such subject matter. This Agreement shall not be modified except by a subsequently dated written amendment or appendix signed on behalf of NTT and Partner by their duly authorized representatives. Any provision of Partner’s purchase order or other document purporting to vary or add to the provisions hereof shall be void.
5.3.6 - NTT Software Terms of Use
Effective Date: 11 June 2025
We have updated the NTT Software Terms of Use effective as of the date indicated in the above header. For the previous version of the NTT Software Terms of Use click here.
PLEASE READ CAREFULLY: YOU AND ANY COMPANY OR ENTITY THAT YOU ARE ACTING FOR (“YOU” OR “YOUR”) ACCEPTS THESE SOFTWARE TERMS OF USE (THE “SOFTWARE TERMS”) BY INSTALLING AND/OR USING THE SOFTWARE. YOU REPRESENT THAT YOU: 1. ARE LAWFULLY ABLE TO ENTER INTO THESE SOFTWARE TERMS, AND 2. HAVE FULL AUTHORITY TO BIND THE SOFTWARE USER TO THESE SOFTWARE TERMS. THESE SOFTWARE TERMS ARE A BINDING CONTRACT BETWEEN YOU AND NTT SECURITY HOLDINGS CORPORATION, A CORPORATION ORGANIZED AND EXISTING UNDER THE LAWS OF JAPAN (“NTT”), ON BEHALF OF ITSELF AND ANY OF ITS AFFILIATES PERFORMING HEREUNDER (COLLECTIVELY, “NTT”). IF YOU DO NOT HAVE THIS AUTHORITY, OR YOU DO NOT AGREE TO, OR CANNOT COMPLY WITH, ALL THE SOFTWARE TERMS, THEN YOU MAY NOT USE THE SOFTWARE. THESE SOFTWARE TERMS GOVERN YOUR USE OF THE SOFTWARE UNLESS YOU HAVE ANOTHER VALID AGREEMENT WITH NTT FOR THE USE OF THIS SOFTWARE.
Updating the Software Terms. NTT may revise and update these Software Terms from time to time in our sole discretion. Your continued use of the Software following the update of revised Software Terms means that you accept and agree to the changes. When accepted by you, the revised Software Terms automatically supersede the prior version. New Terms apply prospectively only.
Definitions.
“NTT Competitor” means a person or entity in the business of developing, distributing, or commercializing Internet security products or services substantially similar to or competitive with NTT’s products or services.
“Generated Data” shall mean the data generated by the Software, including but not limited to, correlative and/or contextual data, and/or detections. For the avoidance of doubt, Generated Data does not include Your Data. Any access to or use of Generated Data through the Software is expressly limited to your Internal Use.
“Documentation” means the Software end-user technical documentation.
“Endpoint” means any physical or virtual device, such as, a computer, server, laptop, desktop computer, mobile, cellular, container or virtual machine image.
“Evidence Data” means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by a Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither the Partner nor any Customer(s) are identified in such information.
“Internal Use” means access or use solely for Your own internal information security purposes. By way of example and not limitation, Internal Use does not include access or use: (i) for the benefit of any person or entity other than You, or (ii) in any event, for the development of any product or service. Internal Use is limited to access and use by your employees or your Third Party Providers for your benefit.
“Personal Data” means any information relating to an identified or identifiable person or other similar definition under the applicable data privacy laws; an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.
“Software” means the software accompanying these Software Terms, or NTT software that you or a Third Party Provider have installed or used on your Endpoints, including any updates thereto and/or related Documentation that may be made available from time to time by NTT. NTT software may commonly be referred to as “MDR” or “Samurai”.
“Third Party Provider” means any individual or entity (other than an NTT Competitor) that: (i) has access or use of the Software: (a) under these Software Terms solely on behalf of and for your Internal Use, or (b) under a separate valid agreement with NTT, (ii) has an agreement to provide you (or your Affiliates) services, and (iii) is subject to confidentiality obligations covering NTT’s Confidential Information.
“Your Data” means the data generated by your Endpoints or otherwise from Your network and collected by the Software, but excluding Evidence Data. For the avoidance of doubt, Your Data does not include Generated Data.Your Account. You (and each user seeking access, use or receipt of the Software) will be asked to create a customer account. As part of the account creation process, you and each user be asked to provide a valid email address, create a password, and otherwise authenticate yourself through an NTT designated multi-factor authentication protocol. When registering for an account, you and each user must provide true, accurate, current and complete information about as requested during the account creation process. You and each user must keep that information true, accurate, current and complete after you create each account.
License and Restrictions.
- License. Subject to these Software Terms, if you have obtained a valid evaluation license or subscription to the Software through NTT or a designated NTT partner or reseller, You may, solely for your own Internal Use and during the period of time such evaluation or subscription remains valid, install and run this Software up to the validly licensed quantity.
- Restrictions. In addition to any restrictions stated in the Software Terms, you agree that the rights set forth in 4.1 above do not include any rights to, and you shall not: (i) employ or authorize a NTT Competitor to use the Software or the Documentation, or to provide management, hosting, or support for Software; (ii) alter, publicly display, translate, create derivative works of or otherwise modify the Software; (iii) sublicense, distribute or otherwise transfer the Software to any third party; (iv) allow third parties to access or use the Software; (v) reverse engineer, decompile, disassemble or otherwise attempt to derive the source code for the Software (except to the extent that such prohibition is expressly precluded by applicable law), circumvent its functions, or attempt to gain unauthorized access to NTT’s hosted software or its related systems or networks; (vi) use the Software to circumvent the security of another party’s network/information, develop malware, unauthorized surreptitious surveillance, data modification, data exfiltration, data ransom or data destruction; (vii) remove or alter any notice of proprietary right appearing on the Software; (viii) conduct any stress tests, competitive benchmarking or analysis on, or publish any performance data of, the Software (provided, that this does not prevent you from comparing Software to other products for legitimate purchase evaluation decisions and your Internal Use); or (x) cause, encourage or assist any third party to do any of the foregoing. You agree to use the Software in accordance with laws, rules and regulations directly applicable to you and acknowledges that you are solely responsible for determining whether a particular use of the Software is compliant with such laws. NTT Competitors or any other party with interests or intentions adverse to NTT may not access, install or use the Software or Generated Data.
- Third Party Software. NTT uses certain third party software in its Software, including what is commonly referred to as open source software. Under some of these third party licenses, NTT is required to provide you with notice of the license terms and attribution to the third party. See the licensing terms and attributions for such third party software that NTT uses in NTT’s list of Third Party Licensing Software Terms.
- Ownership & Feedback. Software is made available for use and licensed, not sold. NTT owns and retains all right, title and interest (including all intellectual property rights) in and to the Software. Any feedback or suggestions that you provide to NTT regarding any NTT products or services is non-confidential and may be used by NTT for any purpose without acknowledgement or compensation; provided, You will not be identified publicly as the source of the feedback or suggestion.
Your Obligations and Third Party Providers.
- Your Obligations. You represent and warrant that: (i) it owns or has a right of use from a third party, and controls, directly or indirectly, all of the software, hardware and computer systems (collectively, “Systems”) where the Software will be installed, (ii) to the extent required under any federal, state, or local U.S. or non-US laws it has authorized NTT to access the Systems and process and transmit data through the Software and any other NTT offerings in accordance with these Software Terms and as necessary to provide the Software and other services, (iii) it has a lawful basis in having the Software operate on the Systems, and collect and process the Your Data and the Personal Data; (iv) that it is and will at all relevant times remain duly and effectively authorized to instruct NTT to carry out the services related to the Software, (v) it has made all necessary disclosures, obtained all necessary consents and government authorizations required under applicable law to permit the processing and international transfer of Your Data and Personal Data from you and your Affiliate, to NTT; and (vi) you authorize NTT to provide access to and use of the Software and Your Data to Third Party Providers.
- Third Party Providers. You are solely responsible for: (i) independently testing and validating any Third Party Provider products and services and the Software before deploying it or them in a test or production environment, (ii) evaluating whether using any Third Party Provider products or services are lawful under the laws that apply to you or are permitted in your jurisdiction, and (iii) paying for the Third Party Provider products and services and any claims that arise out of your use of their products and services. Any breach by a Third Party Provider of these Software Terms is a breach by you. NTT is not responsible or liable for any loss, costs or damages arising out of Third Party Provider’s actions or inactions in any manner, including but not limited to, for any disclosure, transfer, modification or deletion of Your Data. NTT does not control, monitor, maintain or provide support for, Third Party Providers or their services or products. NTT disclaims all warranties of any kind, and all indemnities, obligations, and other liabilities in connection with the Third Party Provider’s services and products, and any Third Party Provider interface or integration with NTT’s products or services (including the Software).
NTT Use of Data.
- Data Collection. The Software uses Your Data, Generated Data, Evidence Data and Execution Profile/Metric Data, for the benefit of all users, to help users protect themselves against suspicious and potentially destructive activities. NTT uses such data to: (i) analyze, characterize, attribute, warn of, and/or respond to threats against you and other users, (ii) analyze trends and performance, (iii) improve the functionality of, and develop, NTT’s products and services, and enhance cybersecurity; provided, however, that in all of the foregoing use cases, in a way that does not identify you or your Personal Data to other NTT users (other than your Third Party Providers). NTT may also enable you and/or your Third Party Providers to use Your Data, Generated Data, Evidence Data or Execution Profile Metric Data in other applications or services. Neither Execution Profile/Metric Data nor Evidence Data are your confidential information or Your Data.
- File Collection. You and your Third Party Providers may have the option to upload (by submission, configuration, and/or, retrieval) files and other information related to the files for security analysis and response or, when submitting crash reports, to make the product more reliable and/or improve NTT’s products and services or enhance cyber-security. These potentially suspicious or unknown files may be transmitted and analyzed to determine functionality and their potential to cause instability or damage to your endpoints and systems. In some instances, these files could contain Personal Data.
- Processing Personal Data. Personal Data may be collected and used during the provisioning and use of the Software, to deliver, support and improve NTT’s products and services, further our business relationship, comply with law, act in accordance with your written instructions, or otherwise in accordance with these Software Terms and the Documentation. You authorize NTT to collect, use, store, and transfer the Personal Data that you provide to NTT as contemplated in these Software Terms, NTT’s documentation and NTT’s Privacy Policy and Cookie Statement.
No Warranty.
- Disclaimer. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE PROVIDED “AS-IS” AND WITHOUT WARRANTY OF ANY KIND. NTT AND ITS AFFILIATES DISCLAIM ALL OTHER WARRANTIES, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE. TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, NTT AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE SOFTWARE AND ALL OTHER NTT OFFERINGS. THERE IS NO WARRANTY THAT THE SOFTWARE OR ANY OTHER NTT OFFERINGS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF YOUR PARTICULAR PURPOSES OR NEEDS. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE NOT FAULT FREE OR FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE SOFTWARE OR ANY OTHER NTT OFFERINGS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE. YOU AGREE THAT IT IS YOUR RESPONSIBILITY TO ENSURE SAFE USE OF SOFTWARE AND ANY OTHER NTT OFFERING IN SUCH APPLICATIONS AND INSTALLATIONS. NTT DOES NOT WARRANT ANY THIRD PARTY PRODUCTS OR SERVICES.
- No Guarantee. YOU ACKNOWLEDGE, UNDERSTAND, AND AGREE THAT NTT DOES NOT GUARANTEE OR WARRANT THAT IT WILL FIND, LOCATE, DISCOVER, PREVENT OR WARN OF, ALL OF YOUR OR YOUR AFFILIATES’ SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND YOU AND YOUR AFFILIATES WILL NOT HOLD NTT RESPONSIBLE THEREFOR.
Limitation of Liability. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW NTT SHALL NOT BE LIABLE TO YOU (UNDER ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STATUTE, TORT OR OTHERWISE) FOR: (A) ANY LOST PROFITS, REVENUE, OR SAVINGS, LOST BUSINESS OPPORTUNITIES, LOST DATA, OR SPECIAL, INCIDENTAL, CONSEQUENTIAL, OR PUNITIVE DAMAGES, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES OR LOSSES OR SUCH DAMAGES OR LOSSES WERE REASONABLY FORESEEABLE; OR (B) AN AMOUNT THAT EXCEEDS IN THE AGGREGATE $100. THESE LIMITATIONS WILL APPLY NOTWITHSTANDING ANY FAILURE OF ESSENTIAL PURPOSE OF ANY REMEDY SPECIFIED IN THESE SOFTWARE TERMS. MULTIPLE CLAIMS SHALL NOT EXPAND THE LIMITATIONS SPECIFIED IN THIS SECTION 7.
Compliance with Laws. You agree to comply with all laws directly applicable to it in the performance of these Software Terms and use of the Software, including but not limited to, applicable export and import, anti-corruption and employment laws. You acknowledge and agree the Software shall not be used, transferred, or otherwise exported or re-exported to regions that the United Nations, the United States of America, the European Union and/or the United Kingdom maintains an embargo or comprehensive sanctions (collectively, “Embargoed Countries”), or to or by a national or resident thereof, or any person or entity subject to individual prohibitions (e.g., the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state), without first obtaining all required authorizations from the applicable government(s). You represent and warrant that you are not located in, or is under the control of, or a national or resident of, an Embargoed Country or Designated National
Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy
Beta Test. NTT may, directly or through a reseller, invite you to participate in a beta test program. If you are invited by NTT to participate in a beta test of certain Software (“Beta Program”), your usage of the subject Software will be subject to these Software Terms and the additional beta program terms (the “Beta Terms”). With respect to the Beta Program, in the event of a conflict between these Software Terms and the Beta Program Terms, the Beta Program Terms will take precedence. IN A BETA, THE SOFTWARE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT
General.
Incorporation by Reference; Priority. These Software Terms are subject to and incorporate by reference the Terms of Service. As it relates to access to and use of the Software, in the event of a conflict between the terms of these Software Terms and the Terms of Service, the terms of these Software Terms shall control.
Entire Agreement. Unless you have another valid agreement with NTT for the use of this Software, these Software Terms constitute the entire agreement between you and NTT concerning the Software. It is expressly agreed that as between you and NTT and regarding the Software, these Software Terms supersede any other terms you have on your procurement Internet portal, purchase order or any other agreement with any reseller, prime contractor or service provider. NTT is not obligated under Third Party Provider’s, or any reseller’s, prime contractor’s or other service provider’s agreement with you unless an officer of NTT executes the agreement. These Software Terms shall not be construed for or against any party to these Software Terms because that party or that party’s legal representative drafted any of its provisions.
Governing Law; Venue. These Software Terms, and the rights and duties of the parties arising hereunder, shall be governed by, construed, and enforced in accordance with the laws of Sweden, excluding its conflicts-of-law principles. The sole and exclusive jurisdiction and venue for actions arising under these Software Terms shall be the courts in Sweden, and the parties agree to service of process in accordance with the rules of such courts. The Uniform Computer Information Transactions Act and the United Nations Convention on the International Sale of Goods shall not apply. Notwithstanding the foregoing, each party reserves the right to file a suit or action in any court of competent jurisdiction as such party deems necessary to protect its intellectual property rights and, in NTT’s case, to recoup any payments due.
Waiver, Severability & Amendments. The failure of either party to enforce any provision of these Software Terms shall not constitute a waiver of any other provision or any subsequent breach. If any provision of these Software Terms is held to be illegal, invalid, or unenforceable, the provision will be enforced to the maximum extent permissible so as to affect the intent of the parties, and the remaining provisions of these Software Terms will remain in full force and effect.
Force Majeure. Neither party shall be liable for, nor shall either party be considered in breach of these Software Terms due to, any failure to perform its obligations under these Software Terms (other than its payment obligations) as a result of a cause beyond its control, including but not limited to, act of God or a public enemy, act of any military, civil or regulatory authority, change in any law or regulation, fire, flood, earthquake, storm or other like event, disruption or outage of communications (including an upstream server block and Internet or other networked environment disruption or outage), power or other utility, labor problem, or any other cause, whether similar or dissimilar to any of the foregoing, which could not have been prevented with reasonable care. The party experiencing a force majeure event, shall use commercially reasonable efforts to provide notice of such to the other party.
5.3.7 - Privacy Policy
NTT Security Holdings Corporation Privacy Policy
Effective Date: April 1, 2022
1. INTRODUCTION
1.1 Purpose
NTT Security Holdings Corporation (“NTT,” “we,” or “us”) recognizes that your privacy is very important and takes it seriously. This Privacy Policy (“Policy”) describes NTT’s policies and procedures on the collection, use, and disclosure of personal information collected through any of our websites and or our various web security solutions (“Services”). We will not use or share your personal information with anyone except as described in this Policy.
1.2 Scope
This Policy is intended to meet requirements globally, including those in North America, Europe, APAC, and other jurisdictions. This Policy does not apply to information we collect by other means (including offline) or from other sources.
This Policy applies to all of NTT’s operating divisions, branches, and subsidiaries, and any additional entities directly controlled by NTT that we may subsequently form.
2. INFORMATION WE MAY GATHER FROM YOU
The types of personal information we may collect (directly from you or from Third-Party sources) and our privacy practices depend on the nature of the relationship you have with NTT and the requirements of applicable law. Some of the ways that NTT may collect personal information include:
2.1 Information You Provide Directly to Us
- Inquiries and Requests – We may provide you with the opportunity to contact us via e-mail or chat to ask questions, request information and materials, register or sign up for guides, seminars, or training classes, or provide comments and suggestions. You may also be offered the opportunity to have one of our representatives contact you personally to provide additional information about our Services. To facilitate this request, we may request additional personal information from you, such as your name, telephone number, and other contact information, to help us satisfy your request.
- Service Enrollment –If you choose to enroll for one of our Services, we may require, without limitation, your name, address (including country, city and state), telephone number, e-mail address, credit card number, bank account information, IP address, IP range, domain name(s), or Web Application URL(s). The types of information required to fulfill a service request depend on the types of Services being requested.
- Statistical Information about Your Visit – We may collect certain information automatically through our Services or other methods of web analysis, such as your Internet protocol (IP) address, cookie identifiers, mobile advertising identifiers, and other device identifiers that are automatically assigned to your computer or device when you access the Internet, browser type, operating system, Internet service provider, pages that you visit before and after using the Services, the date and time of your visit, the amount of time you spend on each page, information about the links you click and pages you view within the Services, and other actions taken through use of the Services.
- Surveys – From time to time we may request information from customers via surveys. Participation in these surveys is completely voluntary and the user therefore has a choice whether or not to disclose this information. Survey information will be used for improving our customer service and service offerings.
- Human Resources Data – NTT collects personal information from current, prospective, and former Employees, their contact points in case of a medical emergency, and beneficiaries under any insurance policy (“Human Resources Data”). The Human Resources Data we collect may include title, name, address, phone number, email address, date of birth, passport number, driver’s license number, Social Security number or other government-issued identification number, financial information related to credit checks, bank details for payroll, information that may be recorded on a resumé or application form, language abilities, contact information of Third Parties in case of an emergency, and beneficiaries under any insurance policy.
We may also collect Sensitive Human Resources Data such as the need for a leave of absence due to a disability, including mental health, medical leave, and maternity leave; information about national origin or immigration status; and optional demographic information such as race, which helps us achieve our diversity goals. We acquire, hold, use, and process Human Resources-related personal information for a variety of business purposes that may include, but are not limited to the following: - Workflow management, including assigning, managing and administering projects;
- Human Resources administration and communication;
- Payroll and the provision of benefits;
- Compensation, including bonuses and long-term incentive administration, stock plan administration, compensation analysis, including monitoring overtime and compliance with labor laws, and company recognition programs;
- Job grading activities;
- Performance and employee development management;
- Organizational development and succession planning;
- Benefits and personnel administration;
- Absence management;
- Helpdesk and IT support services;
- Regulatory compliance;
- Internal and/or external or governmental compliance investigations;
- Internal or external audits;
- Litigation evaluation, prosecution, and defense;
- Diversity and inclusion initiatives;
- Restructuring and relocation;
- Emergency contacts and services;
- Employee safety;
- Compliance with statutory requirements;
- Processing of Employee expenses and travel charges; and
- Acquisitions, divestitures, and integrations.
2.2 Information from Other Sources.
We may receive information about you from other sources, including through Third-Party services and organizations to supplement information provided by you. This supplemental information allows us to verify information that you have provided to NTT and to enhance our ability to provide you with information about our business, products, and Services.
2.3 Cookies, Pixel Tags/Web Beacons, Analytics Information, and Interest-Based Advertising
We, as well as Third Parties that provide content, advertising, or other functionality on our Services, may use cookies, pixel tags, local storage, and other technologies (“Technologies”) to automatically collect information through the Services. For additional information regarding such Technologies, please review our Cookie Policy.
3. HOW WE USE YOUR INFORMATION
3.1 Business Information
Generally, we use the personal information we receive to:
- Provide the Services, respond to inquiries or send you administrative messages regarding the operation and use of the Services;
- Personalize and improve the Services;
- Monitor and analyze usage and trends of the Services;
- Send communications related to the Services;
- Process any transactions initiated by you;
- For any other purpose for which the information was collected;
- To meet our legal obligations;
- For audit and reporting purposes;
- To perform accounting and administrative tasks;
- To respond to requests for information by competent public bodies and judicial authorities;
- To respond to inquiries we receive from you or your company or organization;
- To enforce or manage legal claims;
- To deliver promotional and other communications, including periodically contacting you with offers and information about our products, services, features, and events and sending you newsletters or other information about topics that we believe may be of interest; conducting online surveys; and otherwise promoting our products, services, features, and events; and
3.2 Human resources information
With regard to personal information we receive in connection with the employment relationship:
- we will use such personal information only for employment-related purposes as more fully described in this Policy; and
- if we intend to use this personal information for any other purpose, we will provide the individual with an opportunity to opt out of such uses.
3.3 Additional Uses Aligned with Our Legitimate Interests
In addition, we may use your personal information for the following purposes for which we have a legitimate interest:
- Processing for research purposes (including marketing research);
- Disclosure to affiliated organizations;
- Network and information security (e.g., server logs may be reviewed for security purposes – e.g., to detect unauthorized activity on the Services. In such cases, server log data containing IP addresses may be shared with law enforcement bodies in order that they may identify users in connection with their investigation of the unauthorized activities.);
- Physical security;
- Enforcement of legal claims including debt collection via out-of-court procedures;
- Prevention of fraud, misuse of services or money laundering;
- Employee monitoring for safety or management purposes;
- Whistle-blowing schemes;
- Processing for historical, scientific or statistical purposes.
3.4 Instances Where We May Share Personal Information
- General: We will share your personal information with Third Parties only as described in this Policy. We do not sell your personal information to Third Parties.
- Vendors and Service Providers: In some cases NTT may share personal information with our vendors and service providers who assist us to collect, use, analyze, and otherwise process information on our behalf. It is our practice to require such entities to handle information in a manner consistent with NTT’s policies and to use your personal information only as necessary to provide these services to us.
- Business Partners: NTT may share personal information with our business partners and affiliates for their internal business purposes or to provide you with a product or service that you have requested. NTT may also provide personal information to business partners with whom we may jointly offer products or services, or whose products or services we believe may be of interest to you. In such cases, our business partner’s name will appear, along with NTT’s. We require our affiliates and business partners to agree in writing to maintain the confidentiality and security of personal information they maintain on our behalf and not to use it for any purpose other than the purpose for which NTT provided it to them.
- To Protect Ourselves or Others: We may access, preserve, and disclose your personal information, other account information, and content if we believe doing so is required or appropriate to: (i) comply with law enforcement or national security requests and legal process, such as a court order or subpoena; (ii) respond to your requests; (iii) protect yours’, ours’ or others’ rights, property, or safety; (iv) to enforce NTT policies or contracts; (v) to collect amounts owed to NTT; (vi) when we believe disclosure is necessary or appropriate to prevent physical harm or financial loss or in connection with an investigation or prosecution of suspected or actual illegal activity; or (vii) if we, in good faith, believe that disclosure is otherwise necessary or advisable.
- Merger, Sale, or Other Asset Transfers: If we are involved in a merger, acquisition, financing due diligence, reorganization, bankruptcy, receivership, sale of company assets, or transition of service to another provider, then your information may be sold or transferred as part of such a transaction as permitted by law and/or contract. Should such an event occur, NTT will endeavor to direct the transferee to use personal information in a manner that is consistent with the Policy in effect at the time such personal information was collected.
- NTT Supported Blogs and Forums: If you use a blog or forum, or other chat tool on this website, you should be aware that any personal information you submit there can be read, collected, or used by other users of those forums, and could be used to send you unsolicited messages. NTT is not responsible for the personal information you choose to submit in these forums. You are also responsible for using these forums in a manner consistent with the applicable Terms of Use or other terms and conditions set forth on the relevant forum site. To request removal of your personal information from our blog or community forum, by contacting us as described in the “How to Contact Us” section below. In some cases, we may not be able to remove your personal information, in which case we will let you know that we are unable to do so and why.
- Testimonials: We may display personal testimonials of satisfied customers on our site in addition to other endorsements. With your consent we may post your testimonial along with your name. If you wish to update or delete your testimonial, you can contact the NTT Privacy Contact as described in the “How to Contact Us” section below.
- Social Media Widgets: Our website may include social media features, such as the Facebook “Like” button and widgets, and the “Share This” button or interactive mini-programs that may run on our site. These features may collect your IP address, which page you are visiting on our site, and may set a cookie to enable the feature to function properly. Social media features and widgets are either hosted by a Third Party or hosted directly on our website. Your interactions with these features are governed by the privacy policy of the company providing the feature.
- Data Transfers: All personal information collected via or by NTT may be stored anywhere in the world, in the cloud, on our servers, on the servers of our affiliates or the servers of our service providers. Your personal information may be accessible to law enforcement or other authorities pursuant to a lawful request. By providing information to NTT, you consent to the storage of your personal information in these locations.
- Cross border transfers: As a global company, NTT may transfer your personal data to countries where we do business or to international organizations in connection with the purposes identified above and in accordance with this Privacy Policy. For individuals in the EEA or Switzerland: Your personal information will be stored within the European Economic Area (the “EEA”) or Switzerland. Where we transfer your personal data from a location within the EEA or Switzerland to a country or international organization outside the EEA or Switzerland and that country or international organization does not provide a level of protection for personal data which the European Commission (“Commission”) deems adequate, we use and adhere to the standard contractual clauses (“SCCs”) approved by the Commission to legitimately transfer personal data. You may obtain a copy of these measures by contacting us as described in the “How to Contact Us” section below.
4. YOUR CHOICES
Where you have consented to NTT’s processing of your personal information, you may withdraw that consent at any time and opt out of further processing by following the instructions in this section. Even if you opt out, we may still collect and use non-personal information regarding your activities on our websites and/or information from the advertisements on Third-Party websites for non-interest based advertising purposes, such as to determine the effectiveness of the advertisements.
4.1 Email and Telephone Communications
If you would like to discontinue receiving promotional communications from us, you may update your email preferences by using the “Unsubscribe” link found in emails we send to you.
Note that even if you opt out, you will continue to receive transaction-related emails regarding products or services you have requested. We may also send you certain communications regarding NTT and our Services and you will not be able to opt out of those communications (e.g., communications regarding updates to our Terms of Service or this Policy, information regarding the security, initial use, expiration, product enhancement or migration of our products or services from this site).
We maintain telephone “do-not-call” and “do-not-mail” lists as mandated by law. We process requests to be placed on do-not-mail, do-not-phone and do-not-contact lists within 60 days after receipt, or such shorter time as may be required by law.
4.2 “Do Not Track”
Do Not Track (“DNT”) is a privacy preference that users can set in certain web browsers. DNT is a way for users to inform websites and services that they do not want certain information about their webpage visits collected over time and across websites or online services. NTT does not recognize or respond to browser-initiated DNT signals. For information about “do-not-track”, please visit http://www.allaboutdnt.org/.
4.3 Cookies and Interest-Based Advertising
You may stop or restrict the placement of cookies on your computer or remove them from your browser by adjusting your web browser preferences. Please note that cookie-based opt-outs are not effective on mobile applications. However, on many mobile devices, application users may opt out of certain mobile ads via their device settings.
The online advertising industry also provides websites from which you may opt-out of receiving targeted ads from our data partners and our other advertising partners that participate in self-regulatory programs. You can access these, and also learn more about targeted advertising and consumer choice and privacy, at www.networkadvertising.org/managing/opt_out.asp, or http://www.youronlinechoices.eu/ and www.aboutads.info/choices/. You can also choose not to be included in Google Analytics here.
To be clear, whether you are using our opt-out or an online industry opt-out, these cookie-based opt-outs must be performed on each device and browser that you wish to have opted out. For example, if you have opted out on your computer browser, that opt-out will not be effective on your mobile device. You must separately opt out on each device. Advertisements on Third Party websites that contain the AdChoices link may have been directed to you based on information collected by advertising partners over time and across websites. These advertisements provide a mechanism to opt out of the advertising partners’ use of this information for interest-based advertising purposes.
5. THIRD-PARTY LINKS
Our website may contain links to other websites for news and other information. Our Policy only applies to the NTT website and we are not responsible for the privacy practices or the content of other websites. You should check the privacy policies of those sites before providing your personal information to them.
6. YOUR PRIVACY RIGHTS
In accordance with applicable law, you may have the following rights:
- the right to rectify inaccurate personal data we hold about you without undue delay, and taking into account the purposes of the processing, to have incomplete personal data about you completed;
- the right to ask us to erase your personal data (the right to be forgotten) without undue delay in certain circumstances;
- the right to restrict the processing of your personal data in certain circumstances;
- the right to receive your personal data from us in a structured, commonly used and machine-readable format and to transmit your personal data to a third party without obstruction (right to data portability) in certain circumstances;
- where we process personal data based on your consent, you have the right to withdraw your consent at any time for future processing;
- where we process your personal data based upon our legitimate interests or those of a third party, you have the right to object to the processing of your personal data at any time (including to any profiling);
- where we process your personal data for direct marketing purposes, you have the right to object to processing of your personal data at any time, including profiling to the extent that it is related to such direct marketing;
- the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning you or similarly significantly affects you;
- the right to opt in or opt out of the sale of your personal information to Third Parties, if applicable, where such requests are permitted by law;
- if you are a California resident, you also have the right not to receive discriminatory treatment by us for the exercise of your rights conferred by the California Consumer Privacy Act.
6.1 Exercising these Rights
If you would like to exercise any of these rights, please contact us as described in the “How to Contact Us” section below.
Although NTT makes good faith efforts to provide individuals with access to their personal information, there may be circumstances in which NTT is unable to provide access, including but not limited to: where the information contains legal privilege, would compromise others’ privacy or other legitimate rights, where the burden or expense of providing access would be disproportionate to the risks to the individual’s privacy in the case in question or where it is commercially proprietary. If NTT determines that access should be restricted in any particular instance, we will provide you with an explanation of why that determination has been made and a contact point for any further inquiries. To protect your privacy, NTT will take commercially reasonable steps to verify your identity before granting access to or making any changes to your personal information.
7. DATA RETENTION
NTT will retain personal information for as long as needed to provide Services or as otherwise permitted by law. NTT will retain and use this personal information as necessary to comply with our legal obligations, resolve disputes, and enforce our agreements.
8. SECURITY
We consider the protection of all personal information we receive as critical. Please be assured that we have security measures in place to protect against the loss, misuse, and alteration of any personal information we receive from you. As with any transmission over the Internet, however, there is always some element of risk involved in sending personal information. In order to try to minimize this risk, we encrypt all information that you submit in ordering the Services using the Transport Layer Security (TLS) protocol.
9. CHILDREN’S PRIVACY
Because of the nature of our business, this website is not designed to appeal to children under the age of 13 (or 16 in certain jurisdictions) and we do not knowingly request or receive any information from children under the age of 13 (or 16 in certain jurisdictions). If you learn that your child has provided us with personal information without your consent, you may alert us at privacy@security.ntt. If we learn that we have collected any personal information from children under 13 (or 16 in certain jurisdictions), we will promptly take steps to delete such information and terminate the child’s account.
10. LAW and VENUE
By choosing to visit the website, utilize the Services or otherwise provide information to us, you agree that the governing law applicable to this Policy and any dispute over privacy or the terms contained in this Policy, and the venue for adjudication of any disputes arising hereunder, will be in accordance with the Terms of Service.
11. CALIFORNIA PRIVACY RIGHTS
California law permits users who are California residents to request and obtain from us once a year, free of charge, a list of the third parties to whom we have disclosed their personal information (if any) for their direct marketing purposes in the prior calendar year, as well as the type of personal information disclosed to those parties. NTT does not share personal information with third parties for their own marketing purposes.
12. CHANGES TO THIS POLICY
We may update this Policy to reflect changes to our information practices. If we make any material changes we may notify you by email or by means of a notice on this site prior to the change becoming effective. We encourage you to periodically review this page for the latest information on our privacy practices.
13. REDRESS/COMPLIANCE
13.1 Redress
If you are an EU citizen and feel that NTT is not abiding by the terms of this Policy or is not in compliance with the Standard Contractual Clauses, if applicable, please contact us as described in the “How to Contact Us” section below.
In addition, you may lodge a complaint with a data protection supervisory authority if you believe that your data protection rights relating to your personal data have been breached by NTT or that your personal data has been compromised in some way. A list of data protection authorities is available at https://ec.europa.eu/newsroom/article29/items/612080
13.2 Compliance
This Policy shall be implemented by NTT and all its operating divisions, branches and subsidiaries, and any additional entities directly controlled by NTT that we may subsequently form. NTT has put in place mechanisms to verify ongoing compliance with Standard Contractual Clauses and this Policy. Any Employee who violates these privacy principles will be subject to disciplinary procedures.
14. HOW TO CONTACT US
If you have questions about this Policy or would like to exercise any of your rights described in this Policy, please contact us at:
email: privacy@security.ntt.
15. DEFINITIONS
The following capitalized terms shall have the meanings herein as set forth below.
“Agent” means any Third Party that Processes personal information pursuant to the instructions of, and solely for, NTT or to which NTT discloses personal information for use on its behalf.
“Employee” refers to any current, temporary, permanent, prospective or former employee, director, contractor, worker, or retiree of NTT or its subsidiaries worldwide.
“Process” or “Processing” means any operation which is performed upon personal information, whether or not by automatic means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, restriction, erasure, or destruction.
“Sensitive Data” or “Sensitive Personal Information” is a subset of personal information which, due to its nature, has been classified by law or by policy as deserving additional privacy and security protections. Sensitive Personal Information includes personal information regarding EU residents that is classified as a “Special Category of Personal Data” under EU law, which consists of the following data elements: (1) race or ethnic origin; (2) political opinions; (3) religious or philosophical beliefs; (4) trade union membership; (5) genetic data; (6) biometric data where Processed to uniquely identify a person; (6) health information; (7) sexual orientation or information about the Individual’s sex life; or (8) information relating to the commission of a criminal offense.
“Standard Contractual Clauses” is a data transfer mechanism described in Article 46(2)(c) of the General Data Protection Regulation (GDPR) and approved by the EU Commission Decision 2010/87/EU on February 5, 2010 and includes any successor standard contractual clauses that may be adopted pursuant to an EU Commission decision.
“Third Party” is any company, natural or legal person, public authority, agency, or body other than the Individual, NTT or NTT’s Agents.
5.3.8 - Service Descriptions
This document provides links to the service descriptions of Managed and Consulting services provided by NTT Security Holdings. All of these services are subject to the Terms of Service and Privacy Policy which are also published on this site.
Any orders for a service provided by NTT Security Holdings will be subject to the applicable service description(s) as listed below, and the acceptance of an order will be subject to acceptance of the applicable service description(s).
Managed Services
- Samurai Managed Detection and Response
- Dynamic Blocklist (add-on to Managed Detection and Response)
Consulting Services
5.3.9 - Support Policy
Application Support
Support of the SamurAI Portal is included as part of all subscriptions. Included in support:
- Technical issues regarding the SamurAI Portal, which includes features, options and configurations
- Providing suggestions for features or solution configurations of the application
- SamurAI Portal and Samurai Documentation (Knowledge Base).
Support will be provided on a best effort basis inline with hours of service.
Managed Detection and Response
In addition to Application Support for the SamurAI Portal, clients of the Managed Detection and Response service receive the services provided by the NTT SOC in respect of Investigations, Threat Hunting and Incident Response as outlined in the Managed Detection and Response Service Description.
Hours of Service
- Application support is provided during business hours from 9am to 5pm Central European Time.
- Managed Detection and Response services is delivered by the NTT SOC 24 hours 7 days a week.
Authorised Client Representatives
Registered users of the SamurAI Portal can open support tickets via the web application.
Procedures for interaction by authorized client representatives with the NTT SOC for clients of the Managed Detection and Response service will be covered during the introductory teleconference.
How to open a ticket
Registered users of Samurai MDR can open a ticket via the web interface of the application.
Self-Service Capabilities
The SamurAI Portal provides a link to a wide range of self-help documentation in the Samurai Documentation site. This documentation can be accessed by all users at any time.
Language
All support services for the Managed Detection and Response are provided in English.
5.3.10 - Terms of Service
Effective Date: 11 June 2025
We have updated our Terms of Service effective as of the date indicated in the above header. For the previous version of our Terms of Service, please click here.
These NTT Security Holdings Corporation (“NTT”) Terms of Service (these “Terms”) apply to your purchase of NTT’s Samurai Managed Detection and Response service, related managed services and applicable documentation and applicable Service Descriptions (“Samurai Services”), and consulting services and applicable Service Descriptions (“Consulting Services”, and together with Samurai Services, the “NTT Services”) directly from NTT or through any of NTT’s authorized resellers as identified in the quote, order form or online ordering document applicable to the NTT Services (the “Order”). The Service Descriptions for the Samurai Services and Consulting Service are found here. The purpose of these Terms is to establish the terms and conditions under which you will access, use and receive NTT Services as described in the “Order”. These Terms shall take precedence over any other agreements, contracts or general terms that Customer may have entered into with a reseller as it relates to the NTT Services only. An Order is an integral part of these Terms and is fully incorporated herein; provided, only those transaction-specific terms stating the NTT Services ordered, quantity, price, payment terms, Subscription/Order Term, and billing/provisioning contact information (and for the avoidance of doubt, specifically excluding any pre-printed terms on a customer or reseller purchase order) will have any force or effect unless a particular Order is executed by an authorized signer of NTT and returned to customer (or the applicable reseller). If any such Order is so executed and delivered, then only those specific terms on the face of such Order that expressly identify those portions of these Terms that are to be superseded will prevail over any conflicting terms herein but only with respect to those NTT Services ordered on such Order.
These Terms are solely between NTT and you; any third party to whose services the NTT Services may allow connection is not a party to these Terms. Separate license terms apply to your use of such third-party services.
To be eligible to register for a customer account in order to use or receive the NTT Services, you must review and accept these Terms by clicking on the “I Accept” or “Get Started” button or other mechanism provided. If you are accepting these Terms on behalf of a company or other legal entity, you represent and warrant that you have the authority to bind that company or other legal entity to these Terms, and, in such event, “you” and “your”, whether or not capitalised, will refer to that company or other legal entity. You and NTT may be referred to as a “Party” or, together, as the “Parties”.
The NTT Services are subject to these Terms, the related documentation and Service Descriptions, and any applicable Order submitted by you and expressly accepted by NTT. All documentation related to these Terms can be found here.
You acknowledge and agree that you have read, understood and agreed to these terms. If you do not agree with all the terms, conditions and limitations of these terms, you should not click the “I Accept” or “Get Started” button and you are not authorized to receive the NTT services. Written approval by NTT is not a prerequisite to the validity or enforceability of these terms and no solicitation of any such written approval by or on behalf of NTT shall be construed as an inference to the contrary. Acceptance by NTT is expressly conditional on your assent to these terms to the exclusion of all other terms; if these terms are considered an offer by NTT, acceptance is expressly limited to these terms.
Important note: these terms limit our liability to you. For more details, go to Section 18.
In addition, disputes related to terms or related to your use of the services generally must be resolved by a dispute resolution process which may lead to binding arbitration. For more details, go to Sections 25 and 27.
Changes to These Terms. NTT may update these Terms from time to time by providing you with prior written notice of material updates at least thirty (30) days in advance of the effective date. Notice will be given in your account portal or via an email to the email address of the owner of your account. This notice will highlight the intended updates. Except as otherwise specified by NTT, updates will be effective upon the effective date indicated at the top of these Terms of Service. The updated version of these Terms will supersede all prior versions. Following such notice, your continued access or use of the NTT Services on or after the effective date of the changes to the Terms constitutes your acceptance of any updates. If you do not agree to any updates, you should stop using the NTT Services. If you cease using the NTT Services for this reason you will receive a refund of the unused portion of subscription fees paid in advance. Every user will be required to accept the Software Terms of Use upon first login. You are required to accept these Terms before using the Service and upon changes to these Terms.
Your Account: Login. To access, use, or receive, the NTT Services or related software, you will be asked to create a customer account. As part of the account creation process, you’ll be asked to provide your email address, create a password, and verify that you’re a human being by providing a telephone number to which we’ll send you a verification code to enter into a form. When registering for an account, you must provide true, accurate, current, and complete information, about yourself as requested during the account creation process. You must keep that information true, accurate, current, and complete, after you create each account.
Your Responsibility. You are solely responsible for all access, use, and receipt, (whether or not authorized) of the NTT Services under your customer account(s) and for all acts and omissions of you or anyone to whom you provide access to or otherwise permit to use or receive the NTT Service (“Users”). You agree to take all reasonable precautions to prevent unauthorized access to or use of the NTT Service and will notify us promptly of any unauthorized access or use. We will not be liable for any loss or damage arising from unauthorized use of your customer account(s). You will be solely responsible, at your own expense, for acquiring, installing and maintaining all hardware, software and other equipment as may be necessary for you to connect to, access, use or receive the NTT Services.
Access to Services. During the term and subject to and conditioned on your payment of applicable fees and compliance with all the terms and conditions of these Terms, NTT will make the NTT Service available to you in accordance with these Terms, the applicable documentation and Service Descriptions, and any applicable Order, on a limited, non-exclusive and non-transferable basis, for use, access and receipt by you, limited to, in the case of Samurai Services, the number of Users for whom access to the NTT Services has been purchased.
Restrictions and Unauthorized Use. You shall not (and shall not authorize any third party to): (i) decompile, disassemble, or otherwise reverse-engineer the NTT Services or attempt to reconstruct or discover any source code, underlying ideas, algorithms, file formats or programming interfaces of the NTT Services by any means whatsoever; (ii) sell, sublicense, rent, loan, lease, distribute, market, or commercialize the NTT Services for any purpose, including timesharing or service bureau purposes; (iii) remove any product identification, proprietary, copyright or other notices contained in the NTT Services; (iv) modify or create a derivative work of any part of the NTT Services, or incorporate the NTT Services into or with other products or software not contemplated by these Terms or the documentation (v) use the NTT Services for any competitive purpose or publicly disseminate performance information or analysis (including, without limitation, benchmarks) from any source relating to the NTT Services, or (vi) except for back-up purposes, copy or otherwise reproduce the NTT Services. Further, you will not use the NTT Services in any manner that violates any applicable law. NTT reserves the right to refuse any User access to the NTT Services without notice for any reason, including but not limited to a violation of these Terms. If you violate these Terms NTT reserves the right to issue you a warning regarding the violation or immediately suspend or terminate any or all accounts you have created using the NTT Services.
Applications and APIs. In some cases, it may be necessary for you to grant NTT access to an API or an Application which NTT is required to access in order to provide the NTT Services. You hereby grant NTT the right to access, use, assess and test the application(s) and/or application programming interface(s) (“API(s)”) in connection with providing NTT Services. You acknowledge and agree that NTT’s access and use of the application(s) and/or API(s) to provide NTT Services, is not subject to any “Terms of Use” or other terms or conditions that may be posted on, linked or otherwise provided with, the application(s) and/or API(s). You represent that you are either the owner of the application(s) and/or API(s) or have the authority to permit NTT to provide NTT Services in connection with such applications and/or API(s). You shall provide NTT adequate written evidence thereof upon NTT’s In the event any of the applications and/or API(s) are subject to third-party rights, you shall defend, indemnify and hold harmless NTT for any claims against NTT that arise from NTT accessing or using such applications and/or APIs to provide NTT Services.
Reservation of Rights. Each party reserves all rights not expressly granted in these Terms and no licenses are granted by either party to the other party under these Terms except as expressly stated in an Order, whether by implication, estoppel or otherwise. NTT or its licensors own and retain all right, title and interest (including all intellectual property rights) in and to the NTT Services, documentation and associated software, as applicable, including any modifications or improvements thereof, and applicable Service Descriptions.
Third-Party Services. We may use third-party services to help us provide the NTT Services, but such use does not indicate that we endorse the third-party or the third-party services, or applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services. Privacy Policy applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services.
Modification by NTT. Without materially degrading the Service, NTT reserves the right to modify, enhance, or otherwise change, the NTT Services (or any part thereof), including the Service Description, with or without notice.
Taxes. Unless otherwise stated, the fees do not include taxes, levies, or similar governmental assessments, including value-added, sales, use or withholding taxes assessable by any local, state, provincial or foreign jurisdiction (“Taxes”). You are responsible for paying Taxes assessed in connection with your subscription to the NTT Services except those assessable against NTT or the reseller measured by its net income. You will be invoiced for such Taxes if NTT or the reseller believes it has a legal obligation to do so. You agree to pay such Taxes if so invoiced.
Term, Termination. The term for the NTT Services is as specified in the applicable Order for the NTT Service. Unless otherwise specified at the time of purchase, Samurai Services will automatically renew for like term unless a Party provides thirty (30) days prior notice of nonrenewal. Either Party may terminate these Terms or an Order subject hereto upon thirty (30) days written notice to the other Party (the “Notice Period”) in the event of a material breach that the other Party fails to cure within the Notice Period. Further, except in any case where the Order specifies the Samurai Services are subject to a minimum term, you may i) terminate your account or cancel the Samurai Services without cause at any time and for any reason, or for no reason, and ii) receive a refund of the unamortized portion of the prepaid fee for the terminated Samurai Services. Where the Order specifies the Samurai Services are subject to a minimum term, you will have no right to terminate the Samurai Services without cause during the minimum term or any renewal term, or receive a refund of prepaid fees. You acknowledge that you may, as the result of a termination, lose your account and all information and data associated and you shall not be entitled to compensation for any such loss.
Updates, Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy.
Confidential Information. Both Parties acknowledge that they may obtain information relating to the each other’s services or businesses that has not been released to the public, including, but not limited to, code, technology, know-how, ideas, algorithms, testing procedures, structure, interfaces, specifications, documentation, bugs, problem reports, analysis and performance information, and other technical, business, product, and data (“Confidential Information”). A Party shall not disclose Confidential Information to any third party or use Confidential Information for any purpose other than the use of the NTT Services as licensed under these Terms or other purposes for which the Information has been provided. Each Party agrees to use the same degree of care that it uses to protect the confidentiality of its own confidential information of like kind and, in any case, at least a reasonable degree of care. Each Party acknowledges and agrees that no adequate remedy may exist at law for an actual or threatened breach of this Section 14 and that, in the event of an actual or threatened breach of the provisions of this Section 14, the non-breaching party will be entitled to seek immediate injunctive and other equitable relief, without waiving any other rights or remedies available to it.
Warranty Disclaimer. THE NTT SERVICES, THE DOCUMENTATION AND SERVICE DESCRIPTIONS ARE PROVIDED “AS IS” AND “AS AVAILABLE” WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT. YOUR USE OF THE NTT SERVICES IS AT YOUR SOLE RISK. IN ADDITION, WHILE NTT ATTEMPTS TO PROVIDE A GOOD USER EXPERIENCE, WE CANNOT AND DO NOT REPRESENT OR WARRANT THAT THE NTT SERVICES WILL ALWAYS BE SECURE OR ERROR-FREE OR THAT THE NTT SERVICES WILL ALWAYS FUNCTION WITHOUT DELAYS, DISRUPTIONS, OR IMPERFECTIONS. THE FOREGOING DISCLAIMERS SHALL APPLY TO THE EXTENT PERMITTED BY APPLICABLE LAW.
Indemnification by NTT. NTT will indemnify and defend you from and against any claim brought by a third party against you by reason of your use of a Samurai Service, as permitted hereunder, alleging that such Samurai Service infringes or misappropriates a third party’s valid patent, copyright, or trade secret (a “Claim”). NTT shall, at its expense, defend such IP Claim and pay damages finally awarded against you in connection therewith, including the reasonable fees and expenses of the attorneys engaged by NTT for such defense, provided that (a) you promptly notify NTT of the threat or notice of such IP Claim; (b) NTT will have the sole and exclusive control and authority to select defense attorneys, and defend and/or settle any such IP Claim (however, NTT shall not settle or compromise any claim that results in liability or admission of any liability by you without your prior written consent); and (c) you fully cooperate with NTT in connection therewith. If use of a Service by you, your agents or users has become, or, in NTT’s opinion, is likely to become, the subject of any such Claim, NTT may, at NTT’s option and expense, (i) procure for you the right to continue using the Samurai Service(s) as set forth hereunder; (ii) replace or modify a Service to make it non-infringing; or (iii) if options (i) or (ii) are not commercially reasonable or practicable as determined by NTT, terminate your subscription to the Samurai Service(s) and repay you, on a pro-rata basis, any subscription fees previously paid to NTT for the corresponding unused portion of the term of your subscription for such Samurai Service(s). NTT will have no liability or obligation to indemnify you with respect to any Claim if such claim is caused in whole or in part by (x) compliance with designs, data, instructions or specifications provided by you; (y) modification of the Samurai Service(s) by anyone other than NTT; or (z) the combination, operation or use of the Samurai Service(s) with other hardware or software where a Service would not by itself be infringing. The provisions of this Section 15 state the sole, exclusive and entire liability of NTT to you and constitute your sole remedy with respect to a Claim brought by reason of access to or use of a Service by you, your agents or users.
Indemnification by You. You agree to defend, indemnify and hold NTT, harmless from and against any loss, liability, claim, demand, damages, costs and expenses, including reasonable attorney’s fees, arising out of or in connection with: (i) your use of and access to the NTT Service; (ii) your violation of any term of these Terms; (iii) your violation of any third party right, including without limitation any copyright, property, or privacy right or any third party agreement; (iv) any information you provide on or through the Service, or NTT’s access or use of applications or APIs (each, a “Claim”). As used in this Section 16, “you” shall include anyone accessing the Service using your password.
Conditions of Indemnification. As a condition of the foregoing indemnification obligations set forth in Sections 15 and 16: (a) the indemnified party (“Indemnified Party”) will promptly notify the indemnifying party (“Indemnifying Party”) of any Infringement Claim or Customer Indemnifiable Claim, as applicable (collectively referred to as a “Claim”), provided, however, that the failure to give such prompt notice shall not relieve the Indemnifying Party of its obligations hereunder except to the extent that the Indemnifying Party was actually and materially prejudiced by such failure; (b) the Indemnifying Party will have the sole and exclusive authority to defend or settle any such Claim (provided that, the Indemnifying Party will obtain the Indemnified Party’s consent in connection with any act or forbearance required by the Indemnified Party, which consent will not be unreasonably withheld); and (c) the Indemnified Party will reasonably cooperate with the Indemnifying Party in connection with the Indemnifying Party’s activities hereunder, at the Indemnifying Party’s expense. The Indemnified Party reserves the right, at its own expense, to participate in the defense of a Claim. Notwithstanding anything herein to the contrary, the Indemnifying Party will not settle any Claims for which it has an obligation to indemnify pursuant to this Section 17 admitting liability or fault on behalf of the Indemnified Party, nor create any obligation on behalf of the Indemnified Party without the Indemnified Party’s prior written consent.
Limitation of Damages and Remedies. IN NO EVENT SHALL NTT OR ITS LICENSORS BE LIABLE UNDER CONTRACT, TORT, STRICT LIABILITY OR OTHER LEGAL OR EQUITABLE THEORY FOR ANY INDIRECT, INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH YOUR USE OF THE NTT SERVICES, THIRD-PARTY USE OF THE NTT SERVICES ENABLED BY YOU, OR YOUR OR THIRD-PARTY USE OF ANY DATA OR SOFTWARE ENABLED BY YOU VIA THE NTT SERVICES. NTT SHALL NOT BE LIABLE FOR LOSS, INACCURACY, INCOMPLETENESS, OR RELEASE OF DATA, COST OF PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, SYSTEM DOWNTIME, GOODWILL, PROFITS OR OTHER BUSINESS LOSS, REGARDLESS OF LEGAL THEORY, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. NOTWITHSTANDING ANYTHING HEREIN TO THE CONTRARY, THE TOTAL LIABILITY OF NTT ARISING OUT OF THESE TERMS, INCLUDING BUT NOT LIMITED TO DAMAGES OR LIABILITY OF NTT ARISING OUT OF CONTRACT, TORT, BREACH OF WARRANTY, INFRINGEMENT OR OTHERWISE, SHALL NOT IN ANY EVENT EXCEED THE FEES PAID BY YOU WITH RESPECT TO THE SPECIFIC NTT SERVICE WHICH CAUSED THE CLAIM DURING THE TWELVE (12) MONTHS PRIOR TO THE FIRST EVENT OR OCCURRENCE GIVING RISE TO SUCH LIABILITY. THE PARTIES AGREE THAT THE LIMITATIONS OF THIS SECTION 18 ARE ESSENTIAL AND THAT NTT WOULD NOT PERMIT YOU TO USE THE NTT SERVICES ABSENT THE TERMS OF THIS SECTION 18. THIS SECTION 19 SHALL SURVIVE AND APPLY EVEN IF ANY REMEDY SPECIFIED IN THESE TERMS SHALL BE FOUND TO HAVE FAILED OF ITS ESSENTIAL PURPOSE. THE PROVISIONS OF THIS SECTION 18 ALLOCATE THE RISKS PURSUANT TO THESE TERMS BETWEEN THE PARTIES, AND THE PARTIES HAVE RELIED ON THE LIMITATIONS SET FORTH HEREIN IN DETERMINING WHETHER TO ENTER INTO THESE TERMS.
Export Compliance, Sanctions. You acknowledge that the NTT Services may be subject to export restrictions by the United States government and import restrictions by certain foreign governments. You shall not and shall not authorize any third-party to remove or export from the United States or allow the export or re-export of any part of the NTT Services or any direct product thereof: (i) into (or to a national or resident of) any embargoed or terrorist-supporting country; (ii) to anyone on the U.S. Commerce Department’s Table of Denial Orders or U.S. Treasury Department’s list of Specially Designated Nationals; (iii) to any country to which such export or re-export is restricted or prohibited, or as to which the United States government or any agency thereof requires an export license or other governmental approval at the time of export or re-export without first obtaining such license or approval; or (iv) otherwise in violation of any export or import restrictions, laws or regulations of any United States or foreign agency or authority. You agree to the foregoing and warrant that you are not located in, under the control of, or a national or resident of any such prohibited country or on any such prohibited party list. The NTT Services are further restricted from being used for the design or development of nuclear, chemical, or biological weapons or missile technology, or for terrorist activity, without the prior permission of the United States government. You warrant that neither you or any entity or person that has direct or indirect control of fifty percent or more of your shares are not subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”). You agree that if at any time you become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under the Terms, or the performance of the Terms exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate the NTT Services upon such Sanctions becoming effective. A breach of this Section 19 shall be a material default for the purpose of Section 11.
Ownership. NTT exclusively owns and reserves all right, title and interest in and to the NTT Services, documentation, Service Descriptions, our Confidential Information, and all anonymized or aggregated data resulting from use and operation of the NTT Services and that do not identify a natural person as the source of the information, and NTT trademarks, ideas and any and all other works and materials developed by NTT in connection with performing the NTT Services (including without limitation all intellectual property rights therein and thereto) (collectively, the “NTT Materials”) and that title to NTT Materials shall remain with NTT. For the avoidance of doubt, NTT Materials do not include any customer confidential information or other customer provided material. You agree that Consulting Services or other professional services provided by NTT do not constitute “works for hire,” “works made in the course of duty,” or similar terms under laws where the transfer of intellectual property occurs on the performance of services to a payor.
Suggestions, Feedback and Contributions. If you submit suggestions, feedback or contributions (“Contributions”) you agree that: (a) NTT is not under any obligation of confidentiality with respect to the Contributions; (b) NTT may use or disclose (or choose not to use or disclose) the Contributions for any purpose and in any way; (c) NTT will own the Contributions; and (d) you are not entitled to any compensation or reimbursement of any kind from NTT under any circumstances with respect to the Contributions.
Additional Terms. Your use of the NTT Services, and associated software are subject to the NTT Privacy Policy,Cookie Statement and Data Processing Agreement. To the extent your use of the NTT Service allows you to use the associated software, or you otherwise access and use the NTT software, such access and use shall be subject to the Software Terms of Use.
Data Protection. The terms of the Data Processing Agreement shall apply when personal data is being processed pursuant to these Terms. Additionally, personal data may be disclosed in accordance with the Privacy Policy. You acknowledge that you have read the Privacy Policy and understand that it sets forth how NTT will collect, store, use and disclose your data including personal data. If you do not agree with our Privacy Policy, then you must stop using the NTT Service immediately.
Survival. Upon termination of these Terms, your payment obligations, the terms of this Section 24, and the terms of the following Sections will survive (i.e. still apply): Section 13 (Confidentiality), Section 14 Warranty Disclaimer, Section 15 (Indemnification by NTT), Section 16 (Indemnification by You), Section 17 (Conditions of Indemnification), Section 18 (Limitation of Damages and Remedies), Section 20 (Ownership), Section 24 (Survival), Section 25 (Governing Law), and Section 27 (Agreement to Arbitration).
Governing Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
Venue. Except as provided in Section 27 (Agreement to Arbitration), any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in the applicable courts of Stockholm, Sweden, and we each consent to the personal jurisdiction of these courts.
Agreement to Arbitration. Except for a disputes relating to you, your affiliates’, NTT or NTT’s affiliates’ intellectual property (e.g., trademarks, trade dress, domain names, trade secrets, copyrights or patents) (the “Excepted Disputes”) the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute resolution. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty-day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
Beta Test. NTT may, directly or through a reseller, invite you to participate in a beta test program. If you are invited by NTT to participate in a beta test of certain Samurai Services features (“Beta Program”), your usage of the subject Samurai Services features will be subject to these Terms of Service and NTT’s additional beta program terms. In the event of a conflict between these Terms of Service and the Beta Program Terms, the Beta Program Terms will take precedence. IN A BETA, THE SERVICE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT.
Service True-Up. NTT reserves the right to review the number of endpoints you have onboarded to the Samurai Service and, should that number exceed the number your subscription includes, to adjust (“True-Up”) your service charges to reflect the number onboarded as of the date of the review revealing the excess endpoints (“True-Up Date”). The revised service charge will be applied from the True-Up Date and reflected in your next billing point and for the remainder of your service term or until a further change to the number of endpoints onboarded is made. The service is designed with a log volume allowance of 5GB per endpoint per month. If your log volumes exceed this allowance NTT reserves the right to True-Up your service charge by the number of endpoints needed to cover the excess log volume.
Proof of Value. NTT may, but is not obligated to, offer you a Samurai MDR Proof of Value (POV) subscription as described in the Samurai MDR Service Description. The offer will be made by delivery of a quote. Commencing on acceptance of the quote, you will be entitled to use the Samurai MDR Service for a maximum of 90 days at the reduced price stated in the quote. There is no option to extend or renew the POV subscription. The fee paid for the POV subscription is non-refundable. At any time during the term of the POV subscription and upon notice to NTT you may elect to terminate the POV subscription without further obligation or convert it to a full commercial Samurai MDR subscription. If you choose to convert to a full commercial Samurai MDR subscription you will receive a quote from NTT. Upon acceptance of the quote the POV subscription will end, the full Samurai MDR subscription will commence, and you will a receive a credit for value equal to the POV subscription fee which you may redeem solely for the purchase of NTT Services. The credit has no cash value. If you elect to terminate your POV subscription, or upon its expiration, the Samurai tenant and all data, logs, and configurations associated with your account and the Samurai tenant itself will be irrevocably deleted.
Payment for Services. NTT will bill and you agree to pay, (i) for Samurai Services a subscription fee for the term in advance commencing on the subscription date, order date, or renewal date, and (ii) for Consulting Services in accordance with the order. If you choose to upgrade your subscriptions for Samurai Services during your subscription term, any incremental subscription fees associated with such upgrade will be charged in accordance with the remaining subscription term and any renewal and you will be invoiced by NTT or the reseller promptly following the date of upgrade of renewal. Payment will be due 30 days after invoice unless stated otherwise on your quotation.
Marketing. Each Party agrees that the use of the other Party’s trademarks, service marks, and/or logos shall be subject to the other Party’s prior consent.
Miscellaneous. Neither these Terms nor the licenses granted hereunder are assignable or transferable by you (and any attempt to do so shall be void). NTT may freely assign, delegate, license and/or transfer these Terms , in whole or in part, to an affiliate upon written notice to you.. For purposes of this provision regarding assignment by NTT, “affiliate” shall mean any entity controlling, controlled by or under common control with NTT. You and NTT are independent contractors in the performance of each and every part of these Terms. Nothing in these Terms is intended to create or shall be construed as creating an employer-employee relationship or a partnership, agency, joint venture, or franchise. Subject to the foregoing, the provisions hereof are for the benefit of the parties only and not for any other person or entity. Any notice, report, approval, authorization, agreement or consent required or permitted hereunder shall be in writing; notices shall be sent to the address the applicable party has or may provide by written notice or, if there is no such address, the most recent address the party giving notice can locate using reasonable efforts. No failure or delay in exercising any right hereunder will operate as a waiver thereof, nor will any partial exercise of any right or power hereunder preclude further exercise. If any provision shall be adjudged by any court of competent jurisdiction to be unenforceable or invalid, that provision shall be limited or eliminated to the minimum extent necessary so that these Terms shall otherwise remain in full force and effect and enforceable. This is the complete and exclusive statement of the mutual understanding of the parties with respect to the license granted herein and supersedes and cancels all previous written and oral agreements and communications relating to such license and any waivers or amendments shall be effective only if executed in writing by NTT; however, any pre-printed or standard terms of any purchase order, confirmation, or similar form, unless signed by NTT after the effectiveness hereof, shall have no force or effect. You are responsible for the information you provide or make available to the NTT Services and you must ensure it is accurate, not misleading and does not contain material that is obscene, defamatory, or infringing on any rights of any third party; does not contain malicious code and is not otherwise legally actionable. The substantially prevailing party in any action to enforce these Terms will be entitled to recover its attorney’s fees and costs in connection with such action. Except as described in Section 27 (Agreement to Arbitrate), if any provision of these Terms is held by a court or other tribunal of competent jurisdiction to be unenforceable, that provision will be limited or eliminated to the minimum extent necessary to make it enforceable and, in any event, the rest of these Terms will continue in full force and effect. NTT’s failure to enforce at any time any provision of these Terms, or any other of your obligations does not waive our right to do so later. And, if we do expressly waive any provision of these Terms, or any of your other obligations, that does not mean it is waived for all time in the future. Any waiver must be in writing and signed by NTT and you to be legally binding. No failure, delay or default in performance of any obligation of a party shall constitute an event of default or breach of these Terms to the extent that such failure to perform, delay or default arises out of a cause, existing or future, that is beyond the control and without negligence of such party, including action or inaction of governmental, civil or military authority; fire; strike, lockout or other labor dispute; flood, terrorist act; war; riot; theft; earthquake and other natural disaster. The party affected by such cause shall take all reasonable actions to minimize the consequences of any such cause. In the event of a conflict between a provision of these Terms and the provisions of an Order subject to these Terms, the provision of the Order will control.
5.3.11 - Third Party Software Terms
Effective Date: 11 June 2025
We have updated our Third Party Software Terms effective as of the date indicated in the above header. For the previous version of our Third Party Software Terms, please click here.
All rights to NTT’s software products (“NTT Software”) not expressly granted by NTT are reserved. No part of the NTT Software may be used, reproduced, modified, distributed, displayed, performed, reverse engineered or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without prior written permission of NTT, except as otherwise expressly permitted by the license terms below with respect to the applicable third party software or files.
The logos and all other trademarks, logos and service marks displayed on NTT software, products or website (“Marks”) are the property of NTT or third parties. You are not permitted to use these Marks without the prior written consent of the respective Mark owner.
Notwithstanding the foregoing, certain components of the NTT Software may be governed by additional terms or by a separate license as described below.
Third-party software or files may be included in or distributed with the NTT Software. Some software or files require NTT to license it to you with additional terms or under separate license terms below, and in such case, those software and files are licensed to you as described below and either, as applicable, (1) with the terms below in addition to the terms of your license, subscription or other similar agreement with NTT for the applicable NTT Software, or (2) separately under the terms below and not under the terms of such agreement with NTT.
See the licencing terms and attributions for third party software that NTT uses here.
To the extent the license for any open source software requires NTT to make available to you the corresponding source code and/or modifications (the “Source Files”), you may obtain a copy of the applicable Source Files by sending a written request, with your name, address, and applicable NTT Software, including, where applicable, the version to: NTT Security Holdings Corporation c/o legal@security.ntt. All requests should clearly specify: Open Source Files Request, Attention: OSS. This offer to obtain a copy of the Source Files is valid for three years from the date you acquired the NTT Software.
5.3.12 - Website Terms and Conditions
Effective Date: February 9, 2023
Terms and Conditions of Use of the NTT Security Holdings Website
For purposes of these terms and conditions of use of the website, “NTT” shall mean NTT Security Holdings Corporation, and all of its direct and indirect subsidiaries.
1. Acceptance of Terms and Conditions of Use
NTT provides the information contained on this website (“Website”) and any pages comprising the Website to you subject to the terms and conditions of use of the NTT website set out herein (“Terms and Conditions”). By accessing, using, uploading any information to the Website and/or downloading any information from the Website, you are deemed to have accepted and agreed to the Terms and Conditions. If you do not accept and agree to the Terms and Conditions, do not access, use, upload and/or download any information from the Website.
2. Modification of Terms and Conditions of Use
NTT may at any time in its sole and absolute discretion modify these Terms and Conditions without notice to you and your continued access or use of the Website will be subject to the Terms and Conditions in force at the time of such access or use. Accordingly, you should review the Terms and Conditions periodically as your continued access or use of the Website shall be deemed to be your acceptance of the amended Terms and Conditions.
3. Content of the Website
Whilst every effort is made to update the information contained on this Website on a regular basis, NTT makes no representations or warranties, whether express, implied in law or residual, as to the accuracy, completeness or reliability of information, opinions, data and/or content contained on the Website and shall not be bound in any manner by any information contained on the Website. NTT reserves the right at any time to change the content or discontinue without notice, any aspect or feature of the Website. No opinions, research information, data or content contained on the Website (and whether posted by NTT; its direct and/or indirect subsidiaries or affiliate companies or a third party) should be construed as advice and same are offered for information purposes only.
4. Links to other websites
Links to the websites of other companies, including direct and indirect subsidiary companies of NTT, may be provided on the Website for your convenience, however NTT will not have any control over the content that is loaded, amended or deleted from such websites and assumes no liability is this regard. The use of or reliance on the content linked to the Website does not imply endorsement by NTT of such site or the contents thereof. Use of or reliance on any such links is at your own risk. External links, including links to other websites that are not associated with NTT or the direct and indirect subsidiary companies of NTT, may be provided for your convenience, but they are beyond the control of NTT and no representation is made as to their content. The inclusion of any link does not imply endorsement by NTT of such site or the contents thereof. Use of or reliance on any external links is at your own risk. No hypertext links may be created from any website controlled by you (whether directly or indirectly) to the Website without the express prior written permission of NTT
5. Copyright and intellectual property rights
Copyright and all intellectual property rights in and to all materials, texts, drawings and data made available on the Website (collectively “Materials”) are owned by NTT or, alternatively, NTT is the lawful user thereof and same are protected by international intellectual property laws. Accordingly, any unauthorized copying, reproduction, retransmission, distribution, dissemination, sale, publication, broadcast or other circulation or exploitation of the Materials or any component thereof will constitute an infringement of such copyright and other intellectual property rights. The trademarks, names, logos and service marks (collectively “Trademarks”) displayed on the Website are the registered and unregistered Trademarks of NTT. Nothing contained on the Website should be construed as granting any licence or right to use any Trademark without the prior written permission of NTT. Without detracting from this, NTT hereby authorizes you to view and use the content of this Website, or any part thereof, provided that such content is used for information purposes only.
6. Public forums and user submissions
NTT is not responsible for any Material submitted to the public area, including bulletin boards, chat rooms, or any other public area found on the Website (whether submitted by you or any other user). Any Material (whether submitted by you or any other user) is not endorsed, reviewed or approved by NTT. NTT reserves the right to remove any Material submitted or posted by you in the public areas, without notice to you, if it becomes aware and determines, in its sole and absolute discretion, that there is a possibility that you or the Material may -
- defame, abuse, harass, stalk, threaten or otherwise violate the rights of other users or any third parties;
- publish, post, distribute or disseminate any defamatory, obscene, indecent or unlawful material or information;
- upload files that contain viruses, corrupted files or any other similar software or (computer) programs that may damage the operation of NTT’s and/or a third party’s computer system and/or network;
- violate any copyright, trademark, other applicable laws or intellectual property rights of NTT or any other third party;
- submit contents containing marketing or promotional material which is intended to solicit business.
7. Transmission of information
Your attention is drawn to the fact that information transmitted via the internet to NTT is susceptible to monitoring and interception. NTT reserves the right to request independent verification in compliance with all applicable laws of any information transmitted and your consent to such verification should NTT deem it necessary. You further agree not to use the Website to send or post any message or Material that is unlawful, harassing, defamatory, abusive, indecent, threatening, harmful, vulgar, obscene, sexually orientated, racially offensive, profane, pornographic or which violates any applicable laws and you hereby indemnify NTT against any loss, liability, damage or expense of whatever nature which NTT or any third party may suffer which is caused by or attributable to, whether directly or indirectly, your use of the Website.
8. Warranties and disclaimers
NTT makes no warranties, representations, statements or guarantees (whether express, implied in law or residual) regarding the Website or your access and use of the Website. To the extent permitted by applicable laws, NTT shall not be responsible for and disclaims all liability for any loss, liability, damage (whether direct, indirect or consequential), personal injury or expense of any nature whatsoever which may be suffered by you or any third party, as a result of or which may be attributable, directly or indirectly, to your access and/or use of the Website and any information contained on the Website and you waive any and all claims which you may have against NTT in respect of any loss, liability, damage (whether direct, indirect or consequential) or expense of any nature whatsoever, which may be suffered by you as a result of or which may be attributable directly or indirectly to the aforesaid. These limitations of liability shall apply regardless of the form of action, whether in contract, tort, delict, strict liability or otherwise, and regardless of whether either party has been advised of the possibility of such damages. Notwithstanding anything to the contrary contained herein, NTT shall not be liable for any indirect, contingent or consequential loss (including but not limited to loss of business or loss of profits) incurred or sustained by you or any third party howsoever arising in respect of your access, use of or reliance on the Website or any information offered on or via the Website.
9. Privacy and data protection
NTT understands the importance of protecting your personal data. The NTT Privacy Policy applies to the use of the Website and it also sets out how NTT manages your personal data. Any personal data collected from you during your access or use of the Website will be collected and managed in terms of the NTT Policy, as amended from time to time, and all applicable privacy and data protection laws.
10. General
- These Terms and Conditions constitute the sole record of the agreement between you and NTT in relation to the subject matter hereof. Neither you nor NTT shall be bound by any express, tacit or implied representation, warranty, promise or the like not recorded herein.
- These Terms and Conditions supersede and replace all prior commitments, undertakings or representations, whether written or oral, between you and NTT in respect of the subject matter hereof. No addition to, variation or agreed cancellation of any provision of these Terms and Conditions shall be binding upon NTT unless agreed to by NTT in writing. No indulgence or extension of time which NTT may grant to you will constitute a waiver of or, whether by estoppel or otherwise, limit any of the existing or future rights of NTT in terms hereof, save in the event or to the extent that NTT has signed a written document expressly waiving or limiting such rights.
- NTT shall be entitled to cede, assign and delegate all or any of its rights and obligations in terms of these Terms and Conditions to any third party without notice to you.
- All provisions of these Terms and Conditions are, notwithstanding the manner in which they have been linked grammatically, severable from each other. Any provision of these Terms and Conditions which is or becomes unenforceable in any jurisdiction, whether due to voidness, invalidity, illegality, unlawfulness or for any reason whatever shall, in such jurisdiction only and only to the extent that it is so unenforceable, be disregarded and the remaining provisions of these Terms and Conditions shall remain of full force and effect.
- These Terms and Conditions will be governed by and interpreted according to the substantive laws of Japan without regard to conflicts of laws and principles that would cause laws of another jurisdiction to apply; provided, if your principal place of business is in the European Union, Iceland, Liechtenstein, Norway, Switzerland or the United Kingdom, these Terms will be governed by the substantive laws of Sweden without regard to conflicts of laws and principles that would cause laws of another jurisdiction to apply. When the laws of Japan govern, any legal suit, action or proceeding arising out of or related to these Terms and Conditions shall be instituted in the Tokyo District Court, Tokyo, Japan, and we each consent to the personal jurisdiction of the court; provided, when the laws of Sweden govern these Terms and Conditions, any legal suit, action or proceeding arising out of or related to these Terms and Conditions shall be instituted in the applicable courts of Stockholm, Sweden, and we each consent to the personal jurisdiction of these courts.
5.4 - Superseded Documents
5.4.1 - Beta Product Terms
5.4.1.1 - Product Beta Terms (v1.0 2023-05-25)
This document has been superseded. For the latest version please click HERE.
You are invited to participate in beta testing NTT’s Samurai XDR subject to the Terms of Service and these beta terms (“Beta Terms,” together with the Terms of Service, the “Applicable Terms”). The Applicable Terms are made by and between You and NTT and are effective as of the date You first accept them (whether via an online click-through or a signed agreement or by using the Beta Product) (the “Effective Date”).
- General Terms. From time to time, NTT may seek to test XDR Services and make them available to you under these Beta Terms (each, the “Beta Product”). You agree that these Beta Terms are separate and independent agreements for each such Beta Product.
- Beta Test Participation. As the Beta Product is still in a testing phase, it is likely to contain errors. In addition to the disclaimers in the Terms of Service, you agree that the Beta Product is provided “AS IS” and “AS AVAILABLE.” You understand and agree that we may change, withdraw, terminate your access to, testing of and/or use of, or discontinue the Beta Product (or any portion thereof) at any time and in our sole discretion, with or without notice to you. During the term of these Beta Terms, you will use commercially reasonable efforts to provide suggestions, comments or ideas and report issues or problems related to your use of the Beta Product (collectively, “feedback”) to us in a timely basis or as otherwise agreed between the parties in writing (email will suffice). You agree not to disclose feedback to any third party and hereby assign to us all right, title and interest in and to any feedback, without any right to compensation or other obligation from us.
- Fee. Your use of the Beta Product pursuant to these Applicable Terms is free of charge during the Term (as define at Section 6 below). Upon the expiration or termination of the Beta Term in accordance with Section 6, You agree to immediately discontinue any use of the Beta Product; provided, in the event of an expiration occurring pursuant to Section 6(ii) You may elect to continue using the applicable Samurai XDR product subject to the Terms of Use and payment of applicable fees and charges.
- Confidentiality. “Confidential Information” means any and all information disclosed by us to you, or accessed or provided by you, relating to the Beta Product, including your use thereof, the relationship contemplated herein, feedback, and the Service Descriptions, except to the extent made public by us. You agree that you: (a) will not use any Confidential Information other than as necessary to use or test the Beta Product hereunder; (b) will maintain Confidential Information in strict confidence and will use the same degree of care to protect it as you use to protect your own confidential information, but in no circumstances less than reasonable care; and (c) will not disclose the Confidential Information to any person or entity other than those who need access to such Confidential Information to effect the intent of these Beta Terms and who are bound by written confidentiality obligations at least as protective as those set forth in this section; provided, however, that you will remain responsible for each such person’s or entity’s compliance with and breach of the confidentiality terms herein. You will not make any public announcements related to the Beta Product without our prior written approval, which we may grant or withhold in our sole discretion. This confidentiality provision supersedes any prior agreements between the parties solely with respect to Confidential Information hereunder.
- Service Descriptions. Product-specific terms and policies may also apply to your use of the Beta Product (the “Service Descriptions”). In such case, Service Descriptions will be made available to you (online or, prior to being made available online, as separately provided to you) and will also apply to your use of the Beta Product. For clarity, once we post Service Descriptions online (in the Terms of Service, in other supplemental terms, or otherwise), the online version of such Service Descriptions will supersede any prior versions provided to you. By continuing to access, test, or use the Beta Product after any modification to the applicable Service Descriptions, you agree to be bound by them.
- Term. With respect to each Beta Product, the term of these Beta Terms will begin on the Effective Date and, unless terminated earlier in accordance with the Applicable Terms, will expire on the earlier of (i) the date specified by us in our sole discretion (after which you will cease use of such Beta Product), (ii) the date we (in our sole discretion) make such Beta Product generally publicly available (after which any permitted use is subject to our Terms of Service alone, and not these Beta Terms, and payment of applicable fees and charges), or (iii) the date we discontinue such Beta Product (the “Term”). These Beta Terms, as applied to each Beta Product, may be terminated by either party: (a) with cause immediately upon written notice to the other party; or (b) without cause upon thirty (30) days’ prior written notice to the other party. Sections 2, 3, 7, and 8 of these Beta Terms, and the provisions of the Terms of Service, will survive any termination or expiration of these Beta Terms.
- Miscellaneous. You agree that your use of the Beta Product is subject to the Applicable Terms; the Service Descriptions; and Our Privacy Policy. To the extent these Beta Terms conflict with the Terms of Service, these Beta Terms will govern with respect to your use of the Beta Product to the extent of the conflict. As between the parties, we retain exclusive ownership of the Beta Product. Notwithstanding the foregoing, the Terms of Service (unmodified by these Beta Terms) continue to apply to your use of any NTT Services other than the Beta Product even if use thereof is in connection with the Beta Product. Terms used but not defined herein have the meaning given in the Terms of Service. The term “including” means including without limitation. Notwithstanding (and in further limitation of) the liability cap in the Terms of Service, OUR AGGREGATE LIABILITY ARISING OUT OF OR RELATING TO ANY ACCESS TO, TESTING OF OR USE OF THE BETA PRODUCT OR THESE BETA TERMS SHALL NOT EXCEED ONE HUNDRED DOLLARS ($100). We may modify Our Terms of Service or these Beta Terms at any time, and by continuing to access, test, or use the Beta Product after any modification to the Terms of Service or these Beta Terms, you agree to be bound by them.
5.4.1.2 - Product Beta Terms (v2.0 2025-06-11)
This document has been superseded. For the latest version please click HERE.
You are invited to participate in beta testing NTT’s Samurai Managed Detection and Response service (the “MDR Services”), subject to the Terms of Service and these Beta Program Terms (together, the “Applicable Terms”). The Applicable Terms are made by and between You and NTT and are effective as of the date You first accept them (whether via an online click-through or a signed agreement or by using the Beta Product) (the “Effective Date”).
- General Terms. From time to time, NTT may seek to test MDR Services and make them available to you under these Beta Program Terms (each, the “Beta Service”). You agree that these Applicable Terms are separate and independent agreements for each such Beta Service.
- Beta Test Participation. As the Beta Service is still in a testing phase, it is likely to contain errors. In addition to the disclaimers in the Terms of Service, you agree that the Beta Service is provided “AS IS” and “AS AVAILABLE.” You understand and agree that we may change, withdraw, terminate your access to, testing of and/or use of, or discontinue the Beta Service (or any portion thereof) at any time and in our sole discretion, with or without notice to you. During the term of these Beta Terms, you will use commercially reasonable efforts to provide suggestions, comments or ideas and report issues or problems related to your use of the Beta Service (collectively, “feedback”) to us in a timely basis or as otherwise agreed between the parties in writing (email will suffice). You agree not to disclose feedback to any third party and hereby assign to us all right, title and interest in and to any feedback, without any right to compensation or other obligation from us.
- Confidentiality. “Confidential Information” means any and all information disclosed by us to you, or accessed or provided by you, relating to the Service, including your use thereof, the relationship contemplated herein, feedback, and the Service Descriptions, except to the extent made public by us. You agree that you: (a) will not use any Confidential Information other than as necessary to use or test the Beta Service hereunder; (b) will maintain Confidential Information in strict confidence and will use the same degree of care to protect it as you use to protect your own confidential information, but in no circumstances less than reasonable care; and (c) will not disclose the Confidential Information to any person or entity other than those who need access to such Confidential Information to effect the intent of these Applicable Terms and who are bound by written confidentiality obligations at least as protective as those set forth in this section; provided, however, that you will remain responsible for each such person’s or entity’s compliance with and breach of the confidentiality terms herein. You will not make any public announcements related to the Beta Service without our prior written approval, which we may grant or withhold in our sole discretion. This confidentiality provision supersedes any prior agreements between the parties solely with respect to Confidential Information hereunder.
- Service Descriptions. Specific terms and policies may also apply to your use of the Beta Service (the “Service Descriptions”). In such case, Service Descriptions will be made available to you (online or, prior to being made available online, as separately provided to you) and will also apply to your use of the Beta Service. For clarity, once we post Service Descriptions online (in the Terms of Service, in other supplemental terms, or otherwise), the online version of such Service Descriptions will supersede any prior versions provided to you. By continuing to access, test, or use the Beta Service after any modification to the applicable Service Descriptions, you agree to be bound by them.
- Term. With respect to each Beta Service, the term of these Applicable Terms will begin on the Effective Date and, unless terminated earlier in accordance with the Applicable Terms, will expire on the earlier of (i) the date specified by us in our sole discretion (after which you will cease use of such Beta Service), (ii) the date we (in our sole discretion) make such Beta Service generally publicly available (after which any permitted use is subject to our Terms of Service alone, and not these Beta Terms, and payment of applicable fees and charges), or (iii) the date we discontinue such Beta Service (the “Term”). These Applicable Terms, as applied to each Beta Service, may be terminated by either party: (a) with cause immediately upon written notice to the other party; or (b) without cause upon thirty (30) days’ prior written notice to the other party. Sections 2, 3, 7, and 8 of these Beta Terms, and the provisions of the Terms of Service, will survive any termination or expiration of these Applicable Terms.
- Miscellaneous. You agree that your use of the Beta Service is subject to the Applicable Terms; the Service Descriptions; and Our Privacy Policy. To the extent these Beta Terms conflict with the Terms of Service, these Beta Terms will govern with respect to your use of the Beta Product to the extent of the conflict. As between the parties, we retain exclusive ownership of the Beta Product. Notwithstanding the foregoing, the Terms of Service (unmodified by these Beta Terms) continue to apply to your use of any NTT Services other than the Beta Product even if use thereof is in connection with the Beta Product. Terms used but not defined herein have the meaning given in the Terms of Service. The term “including” means including without limitation. Notwithstanding (and in further limitation of) the liability cap in the Terms of Service, OUR AGGREGATE LIABILITY ARISING OUT OF OR RELATING TO ANY ACCESS TO, TESTING OF OR USE OF THE BETA PRODUCT OR THESE BETA TERMS SHALL NOT EXCEED ONE HUNDRED DOLLARS ($100). We may modify Our Terms of Service or these Beta Terms at any time, and by continuing to access, test, or use the Beta Product after any modification to the Terms of Service or these Beta Terms, you agree to be bound.
5.4.2 - Data Processing Agreement
5.4.2.1 - Data Processing Agreement (v1.0 2023-05-25)
This document has been superseded. For the latest version please click HERE.
NTT SECURITY HOLDINGS CORPORATION
DATA PROCESSING AGREEMENT
By entering into the Client Agreement (as defined below), Client acknowledges it has accepted and signed the Client Agreement, the Data Processing Agreement, and the additional documents which are incorporated therein by reference (collectively, the “Agreement”), and is legally bound thereby.
1. Introduction
1.1 Pursuant to Terms of Service and/or related order forms accepted and agreed by You with NTT Security Holdings Corporation or its subsidiaries (the “Client Agreement”), You have entered into an agreement for access, use or delivery and receipt of certain services (the “Services”). In performing the Client Agreement NTT or it’s sub-processors may have access to personal data relating to You, Your employees, or end-users. In certain jurisdictions, it is a requirement under applicable data protection laws to have a data processing agreement in place to provide certain services to you which may involve the access, processing and storage of personal data. The data protection related obligations between parties are set out in this ‘Data Processing Agreement’ or ‘DPA’ which is a standalone agreement but is added as an addendum to the Client Agreement. In this DPA and its attachments NTT Security Holdings Corporation and its subsidiary are referred to as “NTT” and You are referred to as “Client”.
1.2 To the extent NTT may be required to process personal data on behalf of Client under the Client Agreement, NTT will do so in accordance with the terms set out in this Data Processing Agreement (‘DPA’).
2. Defined terms
2.1 ‘Contact’ means, in the case of Client, the contact information entered at the time it subscribed for the NTT Services and, in the case of NTT the contact information provided [here]contact points for Client and NTT as set forth pursuant to Attachment A
2.2 ‘GDPR’ means the General Data Protection Regulation ((EU) 2016/679).
2.3 ‘Personal Data’ means all personal data provided to NTT by, or on behalf of, Client through use of the Services.
2.4 ‘Restricted Transfer’ means a transfer of Personal Data from a member state of the European Economic Area (‘EEA’), the UK or Switzerland (a country not in the EEA or the EU) to a country outside the European Union, EEA, the UK or Switzerland.
2.5 ‘Standard Contractual Clauses’ or ‘SCCs’ means the EU SCCs and UK SCCs as may be updated, supplemented or replaced from time to time under applicable Data Protection Laws, as a recognized transfer or processing mechanism (as applicable).
2.6 ‘UK GDPR’ means the GDPR as implemented in the UK.
2.7 ‘UK GDPR Terms’ means those terms otherwise required pursuant to UK GDPR which are not comprised in the SCCs, as set out in Attachment C.
2.8 Lower case terms. The following lower case terms used but not defined in this DPA, such as ‘controller’, ‘data subject’, ‘personal data’, ‘processor’ and ‘processing’ will have the same meaning as set forth in Article 4 of the GDPR, irrespective of whether the GDPR applies.
3. Applicable law
3.1 NTT may be required to process personal data on behalf of Client under (a) any applicable law including (b) subordinate legislation and regulations implementing the GDPR and (c) UK GDPR, (collectively referred to ‘applicable Data Protection Laws’).
3.2 Unless expressly stated otherwise, in the event of any conflict between (a) the main body of this DPA; and (b) UK GDPR (to the extent the applicable UK GDPR applies), the applicable local law will prevail.
3.3 To the extent NTT is a processor of personal data subject to the GDPR and/or UK GDPR, the mandatory sections required by Article 28(3) of the GDPR (or UK GDPR, as applicable) for contracts between controllers and processors that govern the processing of personal data are set out in clauses 5.1, 6.1, 6.3, 6.4, 7, 8.1, 8.2, 9.1, 9.2, 10 to 14 (inclusive). The UK GDPR Terms will govern any processing in relation to any terms required by the UK GDPR which are not covered elsewhere in this DPA.
4. Duration and termination
4.1 This DPA will commence on the date it is signed by the party who signs it last and will remain in force so long as the Client Agreement remains in effect or NTT retains any Personal Data related to the Client Agreement in its possession or control.
4.2 NTT will process Personal Data until the date of expiration or termination of the Client Agreement, unless instructed otherwise by Client in writing, or until such Personal Data is returned or destroyed on the written instructions of Client or to the extent that NTT is required to retain such Personal Data to comply with applicable laws.
5. Personal data types and processing purposes
5.1 Where the applicable Data Protection Law is the GDPR or UK GDPR:
(a) Client and NTT acknowledge that Client is the controller and NTT is the processor or sub-processor.
(b) The details of the processing operations, in particular the categories of personal data and the purposes of processing for which the personal data is processed on behalf of the controller, are specified in Attachment B.
5.2 The Client retains control of the Personal Data and remains responsible for its compliance obligations under applicable Data Protection Laws, including providing any required notices, obtaining any required consents, and for the processing instructions it gives to NTT.
5.3 Attachment B describes the purpose of processing and the categories of data subjects and Personal Data that NTT may process in relation to the Services described in the Client Agreement (‘Business Purposes’).
6. NTT obligations
6.1 Client instructions. When NTT acts as the processor of Personal Data, it will only process the Personal Data on Client’s documented instructions and to the extent that this is required to fulfil the Business Purposes. NTT will not process the Personal Data for any other purpose or in a way that does not comply with this DPA or applicable Data Protection Laws. Should NTT reasonably believe that a specific processing activity beyond the scope of Client’s instructions is required to comply with a legal obligation to which NTT is subject, NTT must inform Client of that legal obligation and seek explicit authorization from Client before undertaking such processing. NTT will not process the Personal Data in a manner inconsistent with Client’s documented instructions.
6.2 Independent controller. To the extent NTT uses or otherwise processes Personal Data in connection with NTT’s legitimate business operations, NTT will be an independent controller for such use and will be responsible for complying with all applicable laws and controller obligations.
6.3 Compliance. NTT will reasonably assist Client in complying with Client’s obligations under applicable Data Protection Laws, taking into account the nature of NTT’s processing and the information made available to NTT, including in relation to data subject rights, data protection impact assessments and reporting to and consulting with data protection authorities under applicable Data Protection Laws. NTT will promptly notify Client if, in its opinion, any instruction infringes applicable Data Protection Laws. This notification will not constitute a general obligation on the part of NTT to monitor or interpret the laws applicable to Client, and this notification will not constitute legal advice to Client.
6.4 Disclosure. NTT will not disclose personal data except: (a) as Client directs in writing, (b) as described in this DPA or (c) as required by law. Where NTT is permitted by law to do so, upon receiving a request from a public authority, NTT will use reasonable endeavors to notify the Client and attempt to redirect the public authority to request the personal data directly from Client.
7. Contracting with sub-processors
7.1 List of sub-processors. A list of NTT’s sub-processors that NTT directly engages for the specific Services as a processor is available HERE or on request to the NTT Contact or as otherwise made available on an NTT website.
7.2 General authorization. Client provides its general authorization to NTT’s engagement with sub-processors, including current and future subsidiaries of NTT, to provide some or all Services and process Personal Data on its behalf. To the fullest extent permissible under applicable Data Protection Laws this DPA will constitute Client’s general written authorization to the subcontracting by NTT of the processing of Personal Data to this agreed list of sub-processors.
7.3 Changes. NTT will notify the Client in writing of any intended changes to the agreed list of sub-processors at least 14 days in advance, thereby giving the Client the opportunity to object to such changes. Such objection must be made in writing to the NTT Contact within 10 days of notification. Client’s failure to submit a written objection to the agreed list of sub-processors within 10 days of notification, will be deemed acceptance of the changes to the agreed list of sub-processors.
7.4 Performance. NTT is responsible for its sub-processors compliance with NTT’s obligations in this DPA.
8. Client obligations
8.1 Data subject requests. If NTT receives a request from Client’s data subject to exercise one or more of its rights under applicable Data Protection Laws, in connection with a Service for which NTT is a processor or sub-processor, NTT will redirect the data subject to make its request directly to Client. Client will be responsible for responding to any such request. NTT will comply with reasonable requests by Client to assist with Client’s response to such a data subject request. Client will be responsible for reasonable costs NTT incurs in providing this assistance.
8.2 Client requests. NTT must promptly comply with any Client request or instruction from persons authorized by Client requiring (a) NTT to amend, transfer, delete or otherwise process the Personal Data, or to stop, mitigate or remedy any unauthorized processing, (b) Client’s obligations regarding security of processing and (c) Client’s prior consultation obligations in terms of applicable Data Protection Laws, considering the nature of the processing and the information available to NTT.
8.3 Warranty. Client warrants that: (a) it has all necessary rights to provide the Personal Data to NTT for the processing to be performed in relation to the Services; and (b) NTT’s expected use of the Personal Data for the Business Purposes and as specifically instructed by the Client will comply with all applicable Data Protection Laws.
8.4 Privacy notices. To the extent required by applicable Data Protection Laws, Client is responsible for ensuring that all necessary privacy notices are provided to data subjects, and unless another legal basis set forth in applicable Data Protection Laws supports the lawfulness of the processing, that any necessary data subject consents to the processing are obtained and a record of such consents is maintained. Should such a consent be revoked by a data subject, Client is responsible for communicating the fact of such revocation to NTT, and NTT remains responsible for implementing Client’s instruction with respect to the processing of that Personal Data.
9. Security
9.1 TOMs. NTT will implement appropriate Technical and Organizational Measures (‘TOMs’) to ensure the security of the Personal Data in terms of applicable Data Protection Laws, including the security measures set out in B. This includes protecting the Personal Data against a breach of security leading to accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access to the Personal Data.
9.2 Access to Personal Data. NTT will grant access to the Personal Data undergoing processing to members of its personnel only to the extent strictly necessary for implementing, managing and monitoring of the Client Agreement. NTT will ensure that persons authorized to process the Personal Data received have committed themselves to confidentiality or are under an appropriate statutory obligation of confidentiality.
9.3 Cost negotiations. The parties will negotiate in good faith the cost, if any, to implement material changes other than to the extent required by specific updated security requirements set forth in applicable Data Protection Laws or by data protection authorities of competent jurisdiction (in which case NTT would bear the responsibilities of such cost to the extent required by applicable Data Protection Laws or by the data protection authority).
10. Audits
10.1 Certifications. NTT will maintain any certifications that it is contractually obligated to maintain and comply with as expressly stated in the Client Agreement. NTT will re-certify against those certifications as reasonably required.
10.2 Provision of evidence. At Client’s written request, NTT will provide Client with evidence of those certifications relating to the processing of Personal Data, including applicable certifications or audit reports of its computing environment and physical data centers that it uses in processing Personal Data to provide the Services, so that Client can reasonably verify NTT’s compliance with its obligations under this DPA.
10.3 Compliance with TOMS. NTT may also rely on those certifications to demonstrate compliance with the requirements set out in clause 9.1.
10.4 Confidential information. Any evidence provided by NTT is confidential information and is subject to non-disclosure and distribution limitations of NTT and/or any NTT sub-processor.
10.5 Client Audits. Client may carry out audits of NTT´s premises and operations as these relate to the Personal Data of Client if:
(a) NTT has not provided sufficient evidence of the measures taken under clause 9; or
(b) an audit is formally required by a data protection authority of competent jurisdiction; or
(c) applicable Data Protection Laws provide Client with a direct audit right (and as long as Client only conducts an audit once in any twelve-month period, unless mandatory applicable Data Protection Laws requires more frequent audits).
NTT subsidiaries are intended third-party beneficiaries of this section.
10.6 Client audit process. The Client audit may be carried out by a third party (but must not be a competitor of NTT or not suitably qualified or independent) who must first enter into a confidentiality agreement with NTT. Client must provide at least 60 days advance notice of any audit unless mandatory applicable Data Protection Laws or a data protection authority of competent jurisdiction requires shorter notice. NTT will cooperate with such audits carried out and will grant Client´s auditors reasonable access to any premises and devices involved with the processing of the Client’s Personal Data. The Client audits will be limited in time to a maximum of three business days. Beyond such restrictions, the parties will use current certifications or other audit reports to avoid or minimize repetitive audits. The Client must bear the costs of any Client audit unless the audit reveals a material breach by NTT of this DPA in which case NTT will bear the costs of the audit. If the audit determines that NTT has breached its obligations under the DPA, NTT will promptly remedy the breach at its own cost.
11. Incident management
11.1 Security incidents. If NTT becomes aware of a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to Personal Data while processed by NTT (each a ‘Security Incident’), NTT will promptly and without undue delay:
(a) notify Client of the Security Incident;
(b) investigate the Security Incident and provide Client with sufficient information about the Security Incident, including whether the Security Incident involves Personal Data of the Client;
(c) take reasonable steps to mitigate the effects and to minimize any damage resulting from the Security Incident.
11.2 Security incident notification. Notification(s) of Security Incidents will take place in accordance with clause 11.4. Where the Security Incident involves Personal Data of the Client, NTT will make reasonable efforts to enable Client to perform a thorough investigation into the Security Incident, to formulate a correct response, and to take suitable further steps in respect of the Security Incident. NTT will make reasonable efforts to assist Client in fulfilling Client’s obligation under applicable Data Protection Laws to notify the relevant data protection authority and data subjects about such Security Incident. NTT’s notification of or response to a Security Incident under this clause is not an acknowledgement by NTT of any fault or liability with respect to the Security Incident.
11.3 Other incidents. NTT will notify Client promptly if NTT becomes aware of:
(a) a complaint or a request with respect to the exercise of a data subject’s rights under any applicable Data Protection Laws in relation to Personal Data NTT processes on behalf of Client and its data subjects; or
(b) an investigation into or seizure of the Personal Data of Client by government officials, or a specific indication that such an investigation or seizure is imminent; or
(c) where, in the opinion of NTT, implementing an instruction received from Client in relation to the processing of Personal Data would violate applicable laws to which Client or NTT are subject.
11.4 Client notifications. Any notifications made to Client pursuant to this clause 11 will be addressed to the Client Contact mentioned in Attachment A.
12. General cross border transfers of Personal Data
12.1 Except as described elsewhere in the DPA, Personal Data that NTT processes on Client’s behalf may be transferred to and stored and processed in any country in which NTT or its sub-processors may operate.
12.2 Transfer restrictions. If an applicable Data Protection Law restricts cross-border transfers of Personal Data, the Client will only transfer that Personal Data to NTT if NTT, either through its location or participation in a valid cross-border transfer mechanism under the applicable Data Protection Laws, may legally receive that Personal Data.
12.3 Transfer mechanism. Where the parties determine that cross-border transfers of Personal data are necessary, the parties shall agree and implement the appropriate SCCs or other specific statutory mechanism prior to commencing such cross-border transfer. To the extent that NTT is relying on the SCCs or another specific statutory mechanisms to normalize international data transfers and those mechanisms are subsequently modified, revoked, or held in a court of competent jurisdiction to be invalid, Client and NTT agree to cooperate in good faith to promptly suspend the transfer or to pursue a suitable alternate mechanism that can lawfully support the transfer.
13. GDPR and UK GDPR cross border transfers of Personal Data
13.1 Where the GDPR or UK GDPR is the applicable Data Protection Law NTT may only process, or permit the processing, of Personal Data by the Services in respect of a Restricted Transfer under the following conditions:
(a) Adequacy decision. Where the European Commission or the UK (as applicable) has found that that the relevant countries provides adequate protection for the privacy rights of data subjects;
(b) Adequate safeguards. In the absence of an adequacy decision, where appropriate safeguards have been provided by the controller or processor established in third countries which do not ensure an adequate level of data protection, and who receive the Personal Data by way of a valid transfer mechanism under Article 46(2) of the GDPR, UK GDPR or other applicable Data Protection Law.
(c) Standard Contractual Clauses. SCCs may be used as follows:
(i) the UK SCCs’ for Personal Data subject to UK GDPR;
(ii) the applicable Module(s) of the EU SCCs for Personal Data subject to GDPR and/or Swiss Federal Act of 19 June 1992 on Data Protection (FADP).
13.2 Execution of SCCs. If any cross-border transfer of Personal Data between NTT and the Client requires execution of SCCs to comply with the applicable Data Protection Law, the parties will complete all relevant details in, and execute, the applicable SCCs, and take all other actions required to legitimize the transfer.
13.3 Sub-processors. Where Client provides it general written authorization to NTT (located in the EEA or UK, as applicable) appointing a sub-processor located outside the EEA or UK (as applicable), Client authorizes NTT to enter into the applicable form of the applicable SCCs with the sub-processor in Client’s name and on its behalf (in which case Client will no longer require to enter into direct agreements itself with such sub-processors). NTT will make the executed applicable SCC available to Client on request.
14. Return or destruction of Personal Data
14.1 Client deletion. For certain Services the Client is responsible for installing, hosting, processing and using Personal Data. Here only Client has the ability to access, extract and delete Personal Data stored in that Service. Where the particular Service does not support access, retention or extraction of software provided by Client, NTT has no liability for the deletion of Personal Data as described in this clause 14.1.
14.2 Delete or return. Where the Client Agreement requires NTT to retain Personal Data, NTT will delete that Personal Data within the time period agreed to in the Client Agreement, unless NTT is permitted or required by applicable law to retain such Personal Data. Where the retention of Personal Data has not been addressed in the Client Agreement, NTT will either delete, destroy or return all Personal Data to Client and destroy or return any existing copies when NTT has finished providing Services:
(a) related to the processing;
(b) this DPA terminates;
(c) Client requests NTT to do so in writing; or
(d) NTT has otherwise fulfilled all purposes agreed in the context of the Services related to the processing activities where Client does not require NTT to do any further processing.
14.3 Certificate of destruction. NTT will provide Client with a destruction certificate at Client’s request. Where the deletion or return of the Personal Data is impossible for any reason, or where backups and/or archived copies have been made of the Personal Data, NTT will retain such Personal Data in compliance with applicable Data Protection Laws.
14.4 Third parties. On termination of this DPA, NTT will notify all sub-processors supporting its own processing and make sure that they either destroy the Personal Data or return the Personal Data to Client, at the discretion of Client.
15. Liability and warranty
15.1 Any limitation of liability in the Client Agreement will apply to this DPA, other than to the extent such limitation (a) limits the liability of the parties to data subjects or (b) is not permitted by applicable law.
16. Notice
16.1 Any notice or other communication given to a party under or in connection with this DPA must be in writing and delivered to the other party by email.
16.2 Clause 16.1 does not apply to the service of any proceedings or other documents in any legal action or, where applicable, any arbitration or other method of dispute resolution.
16.3 Any notice or other communication will be deemed given when:
(a) delivered in person;
(b) received by mail (postage prepaid, registered or certified mail, return receipt requested); or
(c) received by an internationally recognized courier service (proof of delivery received by the noticing party) at the physical notice address (as identified above), with an electronic copy sent to the electronic notice address (as identified in the table above).
17. Miscellaneous
17.1 Conflict of terms. The Client Agreement terms remain in full force and effect except as modified in this DPA. Insofar as NTT will be processing Personal Data subject to applicable Data Protection Laws on behalf of the Client in the course of the performance of the Client Agreement, the terms of this DPA will apply. If the terms of this DPA conflict with the terms of the Client Agreement, the terms of this DPA will take precedence over the terms of the Client Agreement.
17.2 Governing law. This DPA is governed by the laws of the jurisdiction specified in the relevant provisions of the Client Agreement.
17.3 Dispute resolution. Any disputes arising from or in connection with this DPA will be brought exclusively before the tribunal specified in the relevant provisions of the Client Agreement.
17.4 Execution: This DPA may be executed in any number of counterparts, each of which will constitute an original, but which will together constitute one agreement. The parties will execute this DPA by electronic signature, and intend and agree that the electronic signature will have the same validity and legal effect as the use of a signature affixed by hand and is made with the intention of authenticating this DPA and evidencing the intention of that party to be bound by this DPA.
Attachment A: Particulars of Processing
Categories of data subjects whose personal data is transferred
Data subjects include the Client’s
-users including employees, contractors, and Clients. NTT acknowledges that, depending on Client’s use of the Services, NTT may process the personal data of any of the following types of data subjects:
- Employees, contractors, temporary workers, agents and representatives of Client;
- Users (e.g., clients end users) and other data subjects that are users of Client’s Services;
- Juristic persons (where applicable).
Categories of personal data transferred
NTT acknowledges that, depending on Client’s use of the Services, NTT may process the following types of Personal Data:
- Basic personal data (for example first name, last name, email address);
- Authentication data (for example username and password);
- Contact information (for example work email and phone number);
- Unique identification numbers and signatures (for example IP addresses);
- Biometric Information (for example fingerprints at NTT data centers);
- Location data (for example, geo-location network data);
- Device identification (for example IMEI-number and MAC address);
- Special category personal data as identified in Article 9 of the GDPR;
- Any other personal data identified in Article 4 of the GDPR.
The frequency of the transfer (e.g. whether the data is transferred on a one-off or continuous basis).
Personal data may be transferred on a continuous basis in order to provide the Services under the existing Client Agreement
Nature of the processing
The nature of processing personal data is for NTT to provide the Services under the existing Client Agreement.
Purpose(s) of the data transfer and further processing
NTT will Process Personal Data, as necessary to perform the Services pursuant to the Client Agreement to the extent determined and controlled by Client. Further, NTT will also Process and enrich the Personal Data in NTT’s systems to (i) improve, enhance, support and operate the Services and its availability; (ii) develop new products and services; (iii) compile statistical reports and insights into usage patterns.
NTT may further transfer Personal Data to third-party service providers that host and maintain NTT’s applications, backup, storage, payment processing, analytics and other services as specified in the section on sub-processors below. These third-party service providers may have access to or Process Personal Data for the purpose of providing these services to NTT.
The period for which the personal data will be retained, or, if that is not possible, the criteria used to determine that period
See clause 14 of the DPA
For transfers to (sub-) processors, also specify subject matter, nature and duration of the processing
In accordance with the DPA, NTT may engage sub-processors to provide some or all of the Services on NTT’s behalf or use any of current or future subsidiaries of NTT for the duration of the Client Agreement. Any such sub-processors will be permitted to obtain personal data only to provide some or all of the Services NTT has engaged them to provide, and they are prohibited from using personal data for any other purpose.
A list of sub-processors engaged by NTT is available.
Attachment B: Technical and Organizational Measures
NTT maintains Technical and Organizational Measures (‘TOMs’) to ensure it processes and protects Personal Data in a responsible way, considering the types of Personal Data that NTT processes, industry standards, the interests and rights of NTT’s employees, clients and communities, and the reasonable cost of implementation in accordance with clause 9 of the DPA and/or, as applicable, incorporated in the applicable SCCs and/or applicable Data Protection Laws. The TOMs maintained by NTT as referenced in this B are described at [ link – security (TOMs) ].
Attachment C: UK GDPR Terms
To the extent that the DPA does not address all of the issues in this Attachment C or provides lesser data protection commitments to Client in the DPA where NTT processes Personal Data within the scope of the UK GDPR on behalf of Client, NTT makes the commitments in this Attachment to the Client (‘UK GDPR Terms’, for short). These UK GDPR Terms do not limit or reduce any data protection commitments NTT makes to Client in the Client Agreement.
For purposes of these UK GDPR Terms, Client and NTT agree that Client is the controller and NTT is the processor of Personal Data, except when Client acts as a processor, in which case NTT is a sub-processor. These UK GDPR Terms do not apply where NTT is a controller of Personal Data.
18. Supplementary contractual measures
18.1 To the extent that the processing of Personal Data carried out by NTT is subject to the UK GDPR and NTT makes a transfer to its sub-processors the obligations set out in 1 to 1.11. inclusive will apply.
18.2 Each party warrants that it has no reason to believe that applicable laws to which it is subject, including any requirements to disclose Personal Data or measures authorising access by public authorities, prevent it from fulfilling its obligations under this DPA and the UK SCCs. Each party declares that in providing this warranty, it has taken due account in particular of the following elements:
(a) the specific circumstances of the processing, including the scale and regularity of processing subject to such applicable laws; the transmission channels used; the nature of the relevant Personal Data; any relevant practical experience with prior instances, or the absence of requests for disclosure from public authorities received by it for the type of Personal Data processed by it;
(b) the applicable laws to which it is/are subject, including those requiring to disclose data to public authorities or authorising access by such authorities, as well as the applicable limitations and safeguards; and
(c) safeguards in addition to those under this DPA, including the technical and organisational measures applied to the processing of the Personal Data by NTT and the relevant sub-processor.
18.3 Each party warrants that, in carrying out the assessment under clause 1.2, it has made best efforts to provide Client with relevant information and agrees that it will continue to cooperate with Client in ensuring compliance with this DPA. NTT agrees to document this assessment and make it available to Client on request and it agrees that such assessment may also be made available to a data protection authority.
18.4 NTT agrees to promptly notify Client if, after having agreed to this DPA and for the duration of the term of this DPA, it has reason to believe that it (or a relevant sub-processor to whom a transfer is made) is or has become subject to applicable laws not in line with the requirements under 1.2, including following a change of applicable laws to which is it (or the relevant sub-processor) is subject or a measure (such as a disclosure request) indicating an application of such applicable laws in practice that is not in line with the requirements under clause 1.2. Following such notification, or if Client otherwise has reason to believe that NTT can no longer fulfil its obligations under this DPA (including in relation to the relevant sub-processor), Client (and the relevant subsidiaries who are controllers) will promptly identify appropriate measures (such as, for instance, technical or organisational measures to ensure security and confidentiality) to be adopted by itself or NTT (and/or the relevant sub-processor), at Client’s cost, to address the situation, if appropriate in consultation with the competent data protection authority.
18.5 NTT agrees to promptly notify Client if it (or the relevant sub-processor to whom a transfer is made):
(a) receives a legally binding request by a public authority under applicable laws to which it (or the relevant sub-processor) is subject for disclosure of Personal Data; such notification will include information about the Personal Data requested, the requesting authority, the legal basis for the request and the response provided;
(b) becomes aware of any direct access by public authorities to Personal Data in accordance with applicable laws to which it (or the relevant sub-processor) is subject; such notification will include all information available to NTT (and the relevant sub-processor).
18.6 If NTT (or the relevant sub-processor to whom the transfer is made) is prohibited from notifying Client as set out in clause 1.4 it agrees to use its best efforts to obtain (and to procure that the relevant sub-processor obtains) a waiver of the prohibition, with a view to communicate as much information and as soon as possible. NTT agrees to document its (and the relevant sub-processor’s) best efforts in order to be able to demonstrate them upon request of Client.
18.7 To the extent permissible under the applicable laws to which NTT (and the relevant sub-processor) is subject, NTT agrees to provide to Client, for the duration of the processing, the relevant information on the requests received by it and the relevant sub-processor (in particular, number of requests, type of data requested, requesting authority or authorities, whether requests have been challenged and the outcome of such challenges, etc.).
18.8 NTT agrees to preserve the information pursuant to clauses 1.1 to 1.7 for the duration of the processing and make it available to the competent data protection authority upon request.
18.9 NTT agrees to review (and to procure that the relevant sub-processor to whom the transfer is made will review), having regard to applicable laws to which it (and the relevant sub-processor) is subject, the legality of the request for disclosure, notably whether it remains within the powers granted to the requesting public authority, and to exhaust all available remedies to challenge the request if, after a careful assessment, it (or the relevant sub-processor) concludes that there are grounds under applicable laws to which it (or the relevant sub-processor) is subject to do so. When challenging a request, NTT will (and will procure that the relevant sub-processor will) seek interim measures with a view to suspend the effects of the request until the court has decided on the merits. NTT will not (and will procure that the relevant sub-processor will not) disclose the Personal Data requested until required to do so under the applicable procedural rules. These requirements are notwithstanding the obligations on NTT pursuant to clause 1.4. NTT agrees to document its (and the relevant sub-processor’s) legal assessment as well as any challenge to the request for disclosure and, to the extent permissible under applicable laws to which it (or the relevant sub-processor) is subject, make it available to Client. It will also make it available to the competent data protection authority upon request.
18.10 NTT will use reasonable endeavours to provide (and to procure that the relevant sub-processor to whom the transfer is made will provide) the minimum amount of information permissible when responding to a request for disclosure, based on a reasonable interpretation of the request.
18.11 NTT will inform (and will procure that the relevant sub-processor to whom the transfer is made will inform) data subjects in a transparent and easily accessible format, on its website, of a contact point authorised to handle complaints or requests and NTT will (and will procure that the sub-processors will) promptly deal with any complaints.
5.4.2.2 - Data Processing Agreement (v2 2025-06-11)
This document has been superseded. For the latest version please click HERE.
NTT SECURITY HOLDINGS CORPORATION
DATA PROCESSING AGREEMENT
By entering into the Client Agreement (as defined below), Client acknowledges it has accepted and signed the Client Agreement, the Data Processing Agreement, and the additional documents which are incorporated therein by reference (collectively, the “Agreement”), and is legally bound thereby.
1. Introduction
1.1 Pursuant to Terms of Service and/or related order forms accepted and agreed by You with NTT Security Holdings Corporation or its subsidiaries (the “Client Agreement”), You have entered into an agreement for access, use or delivery and receipt of certain services (the “Services”). In performing the Client Agreement NTT or it’s sub-processors may have access to personal data relating to You, Your employees, or end-users. In certain jurisdictions, it is a requirement under applicable data protection laws to have a data processing agreement in place to provide certain services to you which may involve the access, processing and storage of personal data. The data protection related obligations between parties are set out in this ‘Data Processing Agreement’ or ‘DPA’ which is a standalone agreement but is added as an addendum to the Client Agreement. In this DPA and its attachments NTT Security Holdings Corporation and its subsidiary are referred to as “NTT” and You are referred to as “Client”.
1.2 To the extent NTT may be required to process personal data on behalf of Client under the Client Agreement, NTT will do so in accordance with the terms set out in this Data Processing Agreement (‘DPA’).
2. Defined terms
2.1 ‘Contact’ means, in the case of Client, the contact information entered at the time it subscribed for the NTT Services and, in the case of NTT the contact information provided [here]contact points for Client and NTT as set forth pursuant to Attachment A
2.2 ‘GDPR’ means the General Data Protection Regulation ((EU) 2016/679).
2.3 ‘Personal Data’ means all personal data provided to NTT by, or on behalf of, Client through use of the Services.
2.4 ‘Restricted Transfer’ means a transfer of Personal Data from a member state of the European Economic Area (‘EEA’), the UK or Switzerland (a country not in the EEA or the EU) to a country outside the European Union, EEA, the UK or Switzerland.
2.5 ‘Standard Contractual Clauses’ or ‘SCCs’ means the EU SCCs and UK SCCs as may be updated, supplemented or replaced from time to time under applicable Data Protection Laws, as a recognized transfer or processing mechanism (as applicable).
2.6 ‘UK GDPR’ means the GDPR as implemented in the UK.
2.7 ‘UK GDPR Terms’ means those terms otherwise required pursuant to UK GDPR which are not comprised in the SCCs, as set out in Attachment C
2.8 Lower case terms. The following lower case terms used but not defined in this DPA, such as ‘controller’, ‘data subject’, ‘personal data’, ‘processor’ and ‘processing’ will have the same meaning as set forth in Article 4 of the GDPR, irrespective of whether the GDPR applies.
3. Applicable law
3.1 NTT may be required to process personal data on behalf of Client under (a) any applicable law including (b) subordinate legislation and regulations implementing the GDPR and (c) UK GDPR, (collectively referred to ‘applicable Data Protection Laws’).
3.2 Unless expressly stated otherwise, in the event of any conflict between (a) the main body of this DPA; and (b) UK GDPR (to the extent the applicable UK GDPR applies), the applicable local law will prevail.
3.3 To the extent NTT is a processor of personal data subject to the GDPR and/or UK GDPR, the mandatory sections required by Article 28(3) of the GDPR (or UK GDPR, as applicable) for contracts between controllers and processors that govern the processing of personal data are set out in clauses 5.1, 6.1, 6.3, 6.4, 7, 8.1, 8.2, 9.1, 9.2, 10 to 14 (inclusive). The UK GDPR Terms will govern any processing in relation to any terms required by the UK GDPR which are not covered elsewhere in this DPA.
4. Duration and termination
4.1 This DPA will commence on the date it is signed by the party who signs it last and will remain in force so long as the Client Agreement remains in effect or NTT retains any Personal Data related to the Client Agreement in its possession or control.
4.2 NTT will process Personal Data until the date of expiration or termination of the Client Agreement, unless instructed otherwise by Client in writing, or until such Personal Data is returned or destroyed on the written instructions of Client or to the extent that NTT is required to retain such Personal Data to comply with applicable laws.
5. Personal data types and processing purposes
5.1 Where the applicable Data Protection Law is the GDPR or UK GDPR:
(a) Client and NTT acknowledge that Client is the controller and NTT is the processor or sub-processor.
(b) The details of the processing operations, in particular the categories of personal data and the purposes of processing for which the personal data is processed on behalf of the controller, are specified in Attachment B.
5.2 The Client retains control of the Personal Data and remains responsible for its compliance obligations under applicable Data Protection Laws, including providing any required notices, obtaining any required consents, and for the processing instructions it gives to NTT.
5.3 Attachment B describes the purpose of processing and the categories of data subjects and Personal Data that NTT may process in relation to the Services described in the Client Agreement (‘Business Purposes’).
6. NTT obligations
6.1 Client instructions. When NTT acts as the processor of Personal Data, it will only process the Personal Data on Client’s documented instructions and to the extent that this is required to fulfil the Business Purposes. NTT will not process the Personal Data for any other purpose or in a way that does not comply with this DPA or applicable Data Protection Laws. Should NTT reasonably believe that a specific processing activity beyond the scope of Client’s instructions is required to comply with a legal obligation to which NTT is subject, NTT must inform Client of that legal obligation and seek explicit authorization from Client before undertaking such processing. NTT will not process the Personal Data in a manner inconsistent with Client’s documented instructions.
6.2 Independent controller. To the extent NTT uses or otherwise processes Personal Data in connection with NTT’s legitimate business operations, NTT will be an independent controller for such use and will be responsible for complying with all applicable laws and controller obligations.
6.3 Compliance. NTT will reasonably assist Client in complying with Client’s obligations under applicable Data Protection Laws, taking into account the nature of NTT’s processing and the information made available to NTT, including in relation to data subject rights, data protection impact assessments and reporting to and consulting with data protection authorities under applicable Data Protection Laws. NTT will promptly notify Client if, in its opinion, any instruction infringes applicable Data Protection Laws. This notification will not constitute a general obligation on the part of NTT to monitor or interpret the laws applicable to Client, and this notification will not constitute legal advice to Client.
6.4 Disclosure. NTT will not disclose personal data except: (a) as Client directs in writing, (b) as described in this DPA or (c) as required by law. Where NTT is permitted by law to do so, upon receiving a request from a public authority, NTT will use reasonable endeavors to notify the Client and attempt to redirect the public authority to request the personal data directly from Client.
7. Contracting with sub-processors
7.1 List of sub-processors. A list of NTT’s sub-processors that NTT directly engages for the specific Services as a processor is available HERE or on request to the NTT Contact or as otherwise made available on an NTT website.
7.2 General authorization. Client provides its general authorization to NTT’s engagement with sub-processors, including current and future subsidiaries of NTT, to provide some or all Services and process Personal Data on its behalf. To the fullest extent permissible under applicable Data Protection Laws this DPA will constitute Client’s general written authorization to the subcontracting by NTT of the processing of Personal Data to this agreed list of sub-processors.
7.3 Changes. NTT will notify the Client in writing of any intended changes to the agreed list of sub-processors at least 30 days in advance, thereby giving the Client the opportunity to object to such changes. Such objection must be made in writing to the NTT Contact within 30 days of notification. Client’s failure to submit a written objection to the agreed list of sub-processors within 30 days of notification, will be deemed acceptance of the changes to the agreed list of sub-processors.
7.4 Performance. Where a sub-processor fails to fulfil its data protection obligations, NTT shall remain liable to the Client for the performance of that sub-processor’s obligations.
8. Client obligations
8.1 Data subject requests. If NTT receives a request from Client’s data subject to exercise one or more of its rights under applicable Data Protection Laws, in connection with a Service for which NTT is a processor or sub-processor, NTT will redirect the data subject to make its request directly to Client. Client will be responsible for responding to any such request. NTT will comply with reasonable requests by Client to assist with Client’s response to such a data subject request.
8.2 Client requests. NTT must promptly comply with any Client request or instruction from persons authorized by Client requiring (a) NTT to amend, transfer, delete or otherwise process the Personal Data, or to stop, mitigate or remedy any unauthorized processing, (b) Client’s obligations regarding security of processing and (c) Client’s prior consultation obligations in terms of applicable Data Protection Laws, considering the nature of the processing and the information available to NTT.
8.3 Warranty. Client warrants that: (a) it has all necessary rights to provide the Personal Data to NTT for the processing to be performed in relation to the Services; and (b) NTT’s expected use of the Personal Data for the Business Purposes and as specifically instructed by the Client will comply with all applicable Data Protection Laws.
8.4 Privacy notices. To the extent required by applicable Data Protection Laws, Client is responsible for ensuring that all necessary privacy notices are provided to data subjects, and unless another legal basis set forth in applicable Data Protection Laws supports the lawfulness of the processing, that any necessary data subject consents to the processing are obtained and a record of such consents is maintained. Should such a consent be revoked by a data subject, Client is responsible for communicating the fact of such revocation to NTT, and NTT remains responsible for implementing Client’s instruction with respect to the processing of that Personal Data.
9. Security
9.1 TOMs. NTT will implement appropriate Technical and Organizational Measures (‘TOMs’) to ensure the security of the Personal Data in terms of applicable Data Protection Laws, including the security measures set out in B. This includes protecting the Personal Data against a breach of security leading to accidental or unlawful destruction, loss, alteration, unauthorized disclosure or access to the Personal Data.
9.2 Access to Personal Data. NTT will grant access to the Personal Data undergoing processing to members of its personnel only to the extent strictly necessary for implementing, managing and monitoring of the Client Agreement. NTT will ensure that persons authorized to process the Personal Data received have committed themselves to confidentiality or are under an appropriate statutory obligation of confidentiality.
9.3 Cost negotiations. The parties will negotiate in good faith the cost, if any, to implement material changes other than to the extent required by specific updated security requirements set forth in applicable Data Protection Laws or by data protection authorities of competent jurisdiction (in which case NTT would bear the responsibilities of such cost to the extent required by applicable Data Protection Laws or by the data protection authority).
10. Audits
10.1 Certifications. NTT will maintain any certifications that it is contractually obligated to maintain and comply with as expressly stated in the Client Agreement. NTT will re-certify against those certifications as reasonably required.
10.2 Provision of evidence. At Client’s written request, NTT will provide Client with evidence of those certifications relating to the processing of Personal Data, including applicable certifications or audit reports of its computing environment and physical data centers that it uses in processing Personal Data to provide the Services, so that Client can reasonably verify NTT’s compliance with its obligations under this DPA.
10.3 Compliance with TOMS. NTT may also rely on those certifications to demonstrate compliance with the requirements set out in clause 9.1.
10.4 Confidential information. Any evidence provided by NTT is confidential information and is subject to non-disclosure and distribution limitations of NTT and/or any NTT sub-processor.
10.5 Client Audits. Client may carry out audits of NTT´s premises and operations as these relate to the Personal Data of Client if:
(a) NTT has not provided sufficient evidence of the measures taken under clause 9; or
(b) an audit is formally required by a data protection authority of competent jurisdiction; or
(c) applicable Data Protection Laws provide Client with a direct audit right (and as long as Client only conducts an audit once in any twelve-month period, unless mandatory applicable Data Protection Laws requires more frequent audits).
NTT subsidiaries are intended third-party beneficiaries of this section.
10.6 Client audit process. The Client audit may be carried out by a third party (but must not be a competitor of NTT or not suitably qualified or independent) who must first enter into a confidentiality agreement with NTT. Client must provide at least 60 days advance notice of any audit unless mandatory applicable Data Protection Laws or a data protection authority of competent jurisdiction requires shorter notice. NTT will cooperate with such audits carried out and will grant Client´s auditors reasonable access to any premises and devices involved with the processing of the Client’s Personal Data. The Client audits will be limited in time to a maximum of three business days. Beyond such restrictions, the parties will use current certifications or other audit reports to avoid or minimize repetitive audits. The Client must bear the costs of any Client audit unless the audit reveals a material breach by NTT of this DPA in which case NTT will bear the costs of the audit. If the audit determines that NTT has breached its obligations under the DPA, NTT will promptly remedy the breach at its own cost.
11. Incident management
11.1 Security incidents. If NTT becomes aware of a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to Personal Data while processed by NTT (each a ‘Security Incident’), NTT will promptly and without undue delay:
(a) notify Client of the Security Incident;
(b) investigate the Security Incident and provide Client with sufficient information about the Security Incident, including whether the Security Incident involves Personal Data of the Client;
(c) take reasonable steps to mitigate the effects and to minimize any damage resulting from the Security Incident.
11.2 Security incident notification. Notification(s) of Security Incidents will take place in accordance with clause 11.4. Where the Security Incident involves Personal Data of the Client, NTT will make reasonable efforts to enable Client to perform a thorough investigation into the Security Incident, to formulate a correct response, and to take suitable further steps in respect of the Security Incident. NTT will make reasonable efforts to assist Client in fulfilling Client’s obligation under applicable Data Protection Laws to notify the relevant data protection authority and data subjects about such Security Incident. NTT’s notification of or response to a Security Incident under this clause is not an acknowledgement by NTT of any fault or liability with respect to the Security Incident.
11.3 Other incidents. NTT will notify Client promptly if NTT becomes aware of:
(a) a complaint or a request with respect to the exercise of a data subject’s rights under any applicable Data Protection Laws in relation to Personal Data NTT processes on behalf of Client and its data subjects; or
(b) an investigation into or seizure of the Personal Data of Client by government officials, or a specific indication that such an investigation or seizure is imminent; or
(c) where, in the opinion of NTT, implementing an instruction received from Client in relation to the processing of Personal Data would violate applicable laws to which Client or NTT are subject.
11.4 Client notifications. Any notifications made to Client pursuant to this clause 11 will be addressed to the Client Contact mentioned in Attachment A.
12. General cross border transfers of Personal Data
12.1 Except as described elsewhere in the DPA, Personal Data that NTT processes on Client’s behalf may be transferred to and stored and processed in any country in which NTT or its sub-processors may operate.
12.2 Transfer restrictions. If an applicable Data Protection Law restricts cross-border transfers of Personal Data, the Client will only transfer that Personal Data to NTT if NTT, either through its location or participation in a valid cross-border transfer mechanism under the applicable Data Protection Laws, may legally receive that Personal Data.
12.3 Transfer mechanism. Where the parties determine that cross-border transfers of Personal data are necessary, the parties shall agree and implement the appropriate SCCs or other specific statutory mechanism prior to commencing such cross-border transfer. To the extent that NTT is relying on the SCCs or another specific statutory mechanisms to normalize international data transfers and those mechanisms are subsequently modified, revoked, or held in a court of competent jurisdiction to be invalid, Client and NTT agree to cooperate in good faith to promptly suspend the transfer or to pursue a suitable alternate mechanism that can lawfully support the transfer.
13. GDPR and UK GDPR cross border transfers of Personal Data
13.1 Where the GDPR or UK GDPR is the applicable Data Protection Law NTT may only process, or permit the processing, of Personal Data by the Services in respect of a Restricted Transfer under the following conditions:
(a) Adequacy decision. Where the European Commission or the UK (as applicable) has found that that the relevant countries provides adequate protection for the privacy rights of data subjects;
(b) Adequate safeguards. In the absence of an adequacy decision, where appropriate safeguards have been provided by the controller or processor established in third countries which do not ensure an adequate level of data protection, and who receive the Personal Data by way of a valid transfer mechanism under Article 46(2) of the GDPR, UK GDPR or other applicable Data Protection Law.
(c) Standard Contractual Clauses. SCCs may be used as follows:
(i) the UK SCCs’ for Personal Data subject to UK GDPR;
(ii) the applicable Module(s) of the EU SCCs for Personal Data subject to GDPR and/or Swiss Federal Act of 19 June 1992 on Data Protection (FADP).
13.2 Execution of SCCs. If any cross-border transfer of Personal Data between NTT and the Client requires execution of SCCs to comply with the applicable Data Protection Law, the parties will complete all relevant details in, and execute, the applicable SCCs, and take all other actions required to legitimize the transfer.
13.3 Sub-processors. Where Client provides it general written authorization to NTT (located in the EEA or UK, as applicable) appointing a sub-processor located outside the EEA or UK (as applicable), Client authorizes NTT to enter into the applicable form of the applicable SCCs with the sub-processor in Client’s name and on its behalf (in which case Client will no longer require to enter into direct agreements itself with such sub-processors). NTT will make the executed applicable SCC available to Client on request.
14. Return or destruction of Personal Data
14.1 Client deletion. For certain Services the Client is responsible for installing, hosting, processing and using Personal Data. Here only Client has the ability to access, extract and delete Personal Data stored in that Service. Where the particular Service does not support access, retention or extraction of software provided by Client, NTT has no liability for the deletion of Personal Data as described in this clause 14.1.
14.2 Delete or return. Where the Client Agreement requires NTT to retain Personal Data, NTT will delete that Personal Data within the time period agreed to in the Client Agreement, unless NTT is permitted or required by applicable law to retain such Personal Data. Where the retention of Personal Data has not been addressed in the Client Agreement, NTT will either delete, destroy or return all Personal Data to Client and destroy or return any existing copies when NTT has finished providing Services:
(a) related to the processing;
(b) this DPA terminates;
(c) Client requests NTT to do so in writing; or
(d) NTT has otherwise fulfilled all purposes agreed in the context of the Services related to the processing activities where Client does not require NTT to do any further processing.
14.3 Certificate of destruction. NTT will provide Client with a destruction certificate at Client’s request. Where the deletion or return of the Personal Data is impossible for any reason, or where backups and/or archived copies have been made of the Personal Data, NTT will retain such Personal Data in compliance with applicable Data Protection Laws.
14.4 Third parties. On termination of this DPA, NTT will notify all sub-processors supporting its own processing and make sure that they either destroy the Personal Data or return the Personal Data to Client, at the discretion of Client.
15. Liability and warranty
15.1 Any limitation of liability or monetary cap in the Client Agreement (including Terms of Service) will apply to this DPA, other than to the extent such limitation (a) limits the liability of the parties to data subjects rights or claims or (b) is not permitted by applicable law.
16. Notice
16.1 Any notice or other communication given to a party under or in connection with this DPA must be in writing and delivered to the other party by email.
16.2 Clause 16.1 does not apply to the service of any proceedings or other documents in any legal action or, where applicable, any arbitration or other method of dispute resolution.
16.3 Any notice or other communication will be deemed given when:
(a) delivered in person;
(b) received by mail (postage prepaid, registered or certified mail, return receipt requested); or
(c) received by an internationally recognized courier service (proof of delivery received by the noticing party) at the physical notice address (as identified above), with an electronic copy sent to the electronic notice address (as identified in the table above).
17. Miscellaneous
17.1 Conflict of terms. The Client Agreement terms remain in full force and effect except as modified in this DPA. Insofar as NTT will be processing Personal Data subject to applicable Data Protection Laws on behalf of the Client in the course of the performance of the Client Agreement, the terms of this DPA will apply. If the terms of this DPA conflict with the terms of the Client Agreement, the terms of this DPA will take precedence over the terms of the Client Agreement.
17.2 Governing law. This DPA is governed by the laws of the jurisdiction specified in the relevant provisions of the Client Agreement.
17.3 Dispute resolution. Any disputes arising from or in connection with this DPA will be brought exclusively before the tribunal specified in the relevant provisions of the Client Agreement.
17.4 Execution: This DPA may be executed in any number of counterparts, each of which will constitute an original, but which will together constitute one agreement. The parties will execute this DPA by electronic signature, and intend and agree that the electronic signature will have the same validity and legal effect as the use of a signature affixed by hand and is made with the intention of authenticating this DPA and evidencing the intention of that party to be bound by this DPA.
Attachment A: Particulars of Processing
Categories of data subjects whose personal data is transferred
Data subjects include the Client’s users including employees, contractors, and Clients. NTT acknowledges that, depending on Client’s use of the Services, NTT may process the personal data of any of the following types of data subjects:
- Employees, contractors, temporary workers, agents and representatives of Client;
- Users (e.g., clients end users) and other data subjects that are users of Client’s Services;
- Juristic persons (where applicable).
Categories of personal data transferred
NTT acknowledges that, depending on Client’s use of the Services, NTT may process the following types of Personal Data:
- Basic personal data (for example first name, last name, email address);
- Authentication data (for example username and password);
- Contact information (for example work email and phone number);
- Unique identification numbers and signatures (for example IP addresses);
- Biometric Information (for example fingerprints at NTT data centers);
- Location data (for example, geo-location network data);
- Device identification (for example IMEI-number and MAC address);
- Special category personal data as identified in Article 9 of the GDPR;
- Any other personal data identified in Article 4 of the GDPR.
The frequency of the transfer (e.g. whether the data is transferred on a one-off or continuous basis).
Personal data may be transferred on a continuous basis in order to provide the Services under the existing Client Agreement
Nature of the processing
The nature of processing personal data is for NTT to provide the Services under the existing Client Agreement.
Purpose(s) of the data transfer and further processing
NTT will Process Personal Data, as necessary to perform the Services pursuant to the Client Agreement to the extent determined and controlled by Client. Further, NTT will also Process and enrich the Personal Data in NTT’s systems to (i) improve, enhance, support and operate the Services and its availability; (ii) develop new products and services; (iii) compile statistical reports and insights into usage patterns.
NTT may further transfer Personal Data to third-party service providers that host and maintain NTT’s applications, backup, storage, payment processing, analytics and other services as specified in the section on sub-processors below. These third-party service providers may have access to or Process Personal Data for the purpose of providing these services to NTT.
The period for which the personal data will be retained, or, if that is not possible, the criteria used to determine that period
See clause 14 of the DPA
For transfers to (sub-) processors, also specify subject matter, nature and duration of the processing
In accordance with the DPA, NTT may engage sub-processors to provide some or all of the Services on NTT’s behalf or use any of current or future subsidiaries of NTT for the duration of the Client Agreement. Any such sub-processors will be permitted to obtain personal data only to provide some or all of the Services NTT has engaged them to provide, and they are prohibited from using personal data for any other purpose.
A list of sub-processors engaged by NTT is available.
Attachment B: Technical and Organizational Measures
NTT maintains Technical and Organizational Measures (‘TOMs’) to ensure it processes and protects Personal Data in a responsible way, considering the types of Personal Data that NTT processes, industry standards, the interests and rights of NTT’s employees, clients and communities, and the reasonable cost of implementation in accordance with clause 9 of the DPA and/or, as applicable, incorporated in the applicable SCCs and/or applicable Data Protection Laws. The TOMs maintained by NTT as referenced in this B are described at [ link – security (TOMs) ].
Attachment C: UK GDPR Terms
To the extent that the DPA does not address all of the issues in this Attachment C or provides lesser data protection commitments to Client in the DPA where NTT processes Personal Data within the scope of the UK GDPR on behalf of Client, NTT makes the commitments in this Attachment to the Client (‘UK GDPR Terms’, for short). These UK GDPR Terms do not limit or reduce any data protection commitments NTT makes to Client in the Client Agreement.
For purposes of these UK GDPR Terms, Client and NTT agree that Client is the controller and NTT is the processor of Personal Data, except when Client acts as a processor, in which case NTT is a sub-processor. These UK GDPR Terms do not apply where NTT is a controller of Personal Data.
18. Supplementary contractual measures
18.1 To the extent that the processing of Personal Data carried out by NTT is subject to the UK GDPR and NTT makes a transfer to its sub-processors the obligations set out in 1 to 1.11. inclusive will apply.
18.2 Each party warrants that it has no reason to believe that applicable laws to which it is subject, including any requirements to disclose Personal Data or measures authorising access by public authorities, prevent it from fulfilling its obligations under this DPA and the UK SCCs. Each party declares that in providing this warranty, it has taken due account in particular of the following elements:
(a) the specific circumstances of the processing, including the scale and regularity of processing subject to such applicable laws; the transmission channels used; the nature of the relevant Personal Data; any relevant practical experience with prior instances, or the absence of requests for disclosure from public authorities received by it for the type of Personal Data processed by it;
(b) the applicable laws to which it is/are subject, including those requiring to disclose data to public authorities or authorising access by such authorities, as well as the applicable limitations and safeguards; and
(c) safeguards in addition to those under this DPA, including the technical and organisational measures applied to the processing of the Personal Data by NTT and the relevant sub-processor.
18.3 Each party warrants that, in carrying out the assessment under clause 1.2, it has made best efforts to provide Client with relevant information and agrees that it will continue to cooperate with Client in ensuring compliance with this DPA. NTT agrees to document this assessment and make it available to Client on request and it agrees that such assessment may also be made available to a data protection authority.
18.4 NTT agrees to promptly notify Client if, after having agreed to this DPA and for the duration of the term of this DPA, it has reason to believe that it (or a relevant sub-processor to whom a transfer is made) is or has become subject to applicable laws not in line with the requirements under 1.2, including following a change of applicable laws to which is it (or the relevant sub-processor) is subject or a measure (such as a disclosure request) indicating an application of such applicable laws in practice that is not in line with the requirements under clause 1.2. Following such notification, or if Client otherwise has reason to believe that NTT can no longer fulfil its obligations under this DPA (including in relation to the relevant sub-processor), Client (and the relevant subsidiaries who are controllers) will promptly identify appropriate measures (such as, for instance, technical or organisational measures to ensure security and confidentiality) to be adopted by itself or NTT (and/or the relevant sub-processor), at Client’s cost, to address the situation, if appropriate in consultation with the competent data protection authority.
18.5 NTT agrees to promptly notify Client if it (or the relevant sub-processor to whom a transfer is made):
(a) receives a legally binding request by a public authority under applicable laws to which it (or the relevant sub-processor) is subject for disclosure of Personal Data; such notification will include information about the Personal Data requested, the requesting authority, the legal basis for the request and the response provided;
(b) becomes aware of any direct access by public authorities to Personal Data in accordance with applicable laws to which it (or the relevant sub-processor) is subject; such notification will include all information available to NTT (and the relevant sub-processor).
18.6 If NTT (or the relevant sub-processor to whom the transfer is made) is prohibited from notifying Client as set out in clause 1.4 it agrees to use its best efforts to obtain (and to procure that the relevant sub-processor obtains) a waiver of the prohibition, with a view to communicate as much information and as soon as possible. NTT agrees to document its (and the relevant sub-processor’s) best efforts in order to be able to demonstrate them upon request of Client.
18.7 To the extent permissible under the applicable laws to which NTT (and the relevant sub-processor) is subject, NTT agrees to provide to Client, for the duration of the processing, the relevant information on the requests received by it and the relevant sub-processor (in particular, number of requests, type of data requested, requesting authority or authorities, whether requests have been challenged and the outcome of such challenges, etc.).
18.8 NTT agrees to preserve the information pursuant to clauses 1.1 to 1.7 for the duration of the processing and make it available to the competent data protection authority upon request.
18.9 NTT agrees to review (and to procure that the relevant sub-processor to whom the transfer is made will review), having regard to applicable laws to which it (and the relevant sub-processor) is subject, the legality of the request for disclosure, notably whether it remains within the powers granted to the requesting public authority, and to exhaust all available remedies to challenge the request if, after a careful assessment, it (or the relevant sub-processor) concludes that there are grounds under applicable laws to which it (or the relevant sub-processor) is subject to do so. When challenging a request, NTT will (and will procure that the relevant sub-processor will) seek interim measures with a view to suspend the effects of the request until the court has decided on the merits. NTT will not (and will procure that the relevant sub-processor will not) disclose the Personal Data requested until required to do so under the applicable procedural rules. These requirements are notwithstanding the obligations on NTT pursuant to clause 1.4. NTT agrees to document its (and the relevant sub-processor’s) legal assessment as well as any challenge to the request for disclosure and, to the extent permissible under applicable laws to which it (or the relevant sub-processor) is subject, make it available to Client. It will also make it available to the competent data protection authority upon request.
18.10 NTT will use reasonable endeavours to provide (and to procure that the relevant sub-processor to whom the transfer is made will provide) the minimum amount of information permissible when responding to a request for disclosure, based on a reasonable interpretation of the request.
18.11 NTT will inform (and will procure that the relevant sub-processor to whom the transfer is made will inform) data subjects in a transparent and easily accessible format, on its website, of a contact point authorised to handle complaints or requests and NTT will (and will procure that the sub-processors will) promptly deal with any complaints.
5.4.3 - List of sub processors
5.4.3.1 - List of Sub-processors (v1.0 2025-06-11)
This document has been superseded. For the latest version please click HERE.
In order to provide Samurai services, we make use of third party sub-processors to assist with components of our delivery. By using Samurai Managed Detection and Response powered by Samurai you authorize us to use these sub-processors. Third party sub-processors include:
| Name of sub-processor | Purpose | Location |
|---|---|---|
| Microsoft Azure | Cloud Hosting | EEA |
| Amazon Web Services | Cloud Hosting | EEA |
| Chargebee | Subscription Management | EEA |
| Stripe | Payment Gateway | EEA |
| Zendesk | Support Centre | EEA |
| Salesforce.com | CRM | EEA |
| Avalara | Tax liability calculation | EEA |
| Visma | ERP System | EEA |
| Sendgrid | Sending of email notifications | USA |
EEA - European Economic Area
Group Sub-processors
The following entities are group members of NTT Security Holdings and function as sub-processors in providing support, maintenance and research and development:
| Group Company | Location |
|---|---|
| NTT Security (Sweden) AB | Sweden |
| NTT Security (Japan) KK | Japan |
| NTT Security Holdings Corporation | Japan |
NTT Security Holdings reserves the right to add or replace sub-processors named in this document as required for delivery of services. We will notify you by email or by means of a notice on this page prior to any addition or replacement becoming effective. By continuing to use Samurai you consent to the additional or replacement sub-processors and reaffirm your authorization to us to use the sub-processors.
5.4.4 - Master Partner Agreement
5.4.4.1 - Master Partner Agreement (v1.0 2023-05-25)
This document has been superseded. For the latest version please click HERE.
1. Definitions.
1.1. “Affiliate” means any majority-owned subsidiary or other entity which a party controls or is controlled by, or with which it is under common control with a party.
1.2. “Consulting” means the consulting services provided by NTT as provided for under the terms of the applicable Addendum. By way of example, Consulting may include, incident response and investigation, compromise assessments, forensic services related to cyber security adversaries, tabletop exercises and penetration tests related to cyber security and typically provided on a time and material basis and sometimes sold as a retainer.
1.3. “Customer(s)” means the current or potential customers of Partner for the applicable NTT Samurai Services or Consulting, as specified in the applicable Addendum, excluding any entity or person deemed in NTT reasonable discretion as a competitor of NTT.
1.4. “Evidence Data” means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
1.5. “Intellectual Property Rights” means copyrights (including, without limitation, the exclusive right to use, reproduce, modify, distribute, publicly display, and publicly perform the copyrighted work), trademark rights (including rights in, without limitation, trade names, trademarks, service marks, and trade dress), patent rights (including, without limitation, (i) all rights worldwide in patent applications, any patents issuing therefrom, and all provisional rights with respect to patent applications, (ii) all rights worldwide in any improvements, substitutions, divisionals, patents of addition, continuations, continuations-in-part, reissues, renewals, registrations, confirmations, re-examinations, extensions, supplementary protection certificates, term extensions (under applicable patent law or regulation or other law or regulation), and certificates of invention of any patents or patent applications, and (iii) all rights worldwide to exploit any of the foregoing), know-how, trade secrets, moral rights, right of publicity, authors’ rights, contract and licensing rights, all other intellectual property rights as may exist now and/or hereafter come into existence, and all renewals and extensions thereof, regardless of whether such rights arise under the law of the Territory or any other state, country, region, or jurisdiction.
1.6. “NTT Content” means NTTs proprietary data that is contained in or made available as part of Services and Consulting.
1.7. “Samurai Services” consists of NTT offers under the applicable Addendum as: proprietary, cloud-based software platform (“Samurai”), which can be accessed and used on a hosted basis, and related services, for security operations management, which are specified in the applicable Addendum and are described on the relevant Sales Order.
1.8. “Services” means Samurai Services and Consulting.
1.9. “Trademarks” means the words, names, symbols, designs, or any combination thereof, used in commerce to identify and distinguish the products, services, and company, of a party from those of others and to indicate the source of such consulting and services.
1.10 “Terms of Service” or “ToS” means the current standard terms , conditions, and legal notices, applicable to the Samurai Services found here https://support.samurai.security.ntt/hc/en-001/sections/5261260577681-Legal,, including any product specific terms that are included in valid quotes issued by NTT and related to the Samurai Services.
1.11 “Territory" means the jurisdiction(s) listed in the Addendum.
2. Appointment and Restrictions.
2.1. Nonexclusive Appointment. Provided that Partner complies at all times with the terms and conditions of this Agreement, NTT appoints Partner and Partner accepts appointment as a nonexclusive Partner as set forth in the executed Addendum(s) hereto, with non-transferable, limited right to market and promote the Services to Customers within the Territory; provided, Partner shall require and ensure that each such Customer shall accept and agree to the Terms of Service with NTT prior to accessing the Services.
a)
The applicable Samurai Services and Consulting to which this appointment applies will be specified in the applicable Addendum(s). Samurai Services and Consulting that are not specified in the applicable Addendum are not eligible for use under this Agreement. Partner agrees that nothing in this Agreement shall be construed to preclude NTT from directly or indirectly marketing, distributing, selling, or servicing any Services or Consulting to or for any third party in any location, including without limitation, other partners, resellers, distributors, managed service providers, and end-users. The rights and licenses granted to Partner under this Agreement are personal to Partner and Partner may not transfer or sublicense the appointment set forth in this Agreement.
2.2. Ownership. Except for the limited license(s) expressly granted to Partner in this Agreement, all right, title and interest in and to the Services, Consulting, NTT Content, including the concepts and technology inherent in the Services, NTT Content and deliverables, all Intellectual Property Rights related thereto, shall at all times remain relative to Partner, the sole and exclusive property of NTT. No other licenses, immunity or rights, express or implied are granted by NTT, by implication, estoppel, or otherwise.
2.3. Restrictions. Partner shall, by all appropriate means, prevent unauthorized disclosure, publication, display or use of the Services, Consulting and NTT Content. Partner shall not, and shall not encourage or authorize any third party to, modify or reverse engineer any Services or the technology related thereto, or attempt to gain unauthorized access to the Services or the NTT Content. Partner shall not remove, alter, cover or obfuscate any end-user agreement, privacy notice, copyright notices or other proprietary legends placed or embedded by NTT on or in the Services documentation, NTT Content, deliverables or literature related to any of the foregoing. Partner shall not affix or place any labels or markings on the Services, Consulting output, Service deliverables, or literature related to the foregoing, that might be interpreted as a claim of ownership by Partner or any third party in the foregoing. Without NTT’s prior written consent (an email(s) from the Chief Operating Officer and Chief Technology Officer shall suffice), Partner shall not, nor have a third party, (i) perform a competitive analysis on the Services or Consulting, or (ii) publish a review or the results of any internal evaluation of the Services or Consulting.
2.4. Terms of Service. Partner shall ensure that each Customer shall accept and agree to be bound by the Terms of Service with NTT. Partner shall not a) grant to Customers any access, use or other rights to the Services or b) make to Customer any warranties with respect to NTT or the Services, other than pursuant to the Terms of Service. Partner will promptly report to NTT any breach, or suspected breach, of the Terms of Service of which it becomes aware. NTT reserves the right to refuse to make the Services available to any Customer; provided that NTT provides to Partner a written notice of its objection to such Customer
2.5. Changes to ToS. Partner acknowledges that NTT may update the Terms of Services from time to time by providing notice to Customers as set forth in the Terms of Service, and shall ensure that Customers shall accept and agree to be bound by the modified Terms of Service with NTT. Partner shall not delete or modify, or make additions to any of the representations, warranties, covenants or other terms and conditions set forth in the Terms of Service when entering into agreements with Customers.
2.6. Experienced Staff. Partner shall maintain a staff of employees with a good working knowledge of the Services and Consulting, including their use, applications, limitations, installation, maintenance and related subjects. Partner’s employees shall also be knowledgeable in the use of complementary consulting and services. Partner shall appoint employees of appropriate experience and skill to participate in training programs required by NTT from time to time as mutually agreed by the parties. Partner shall appoint one primary point of contact to coordinate the collaborative relationship with NTT’s designated point of contact.
2.7. Partner Conduct. Partner shall: (i) conduct business in a manner that reflects favorably at all times on the Services, Consulting, goodwill and reputation of NTT; (ii) avoid deceptive, misleading or unethical practices that are or might be detrimental to NTT; (iii) refrain from making any false or misleading representations or warranties with regard to NTT, the Services or Consulting; and (iv) comply with all applicable laws, rules, ordinances, decrees and regulations applicable to Partner’s activities under this Agreement, including without limitation, any applicable privacy laws and the Foreign Corrupt Practices Act, export laws and sanctions regulations or any similar legislation. Partner has reviewed and understands NTT’s Privacy Notice located at https://support.samurai.security.ntt/hc/en-001/articles/5295566187281-Privacy-Policy. Partner shall not, directly or indirectly, through action or inaction, cause NTT to be in violation of its Privacy Notice or applicable laws.
2.8. Partner will not be liable to NTT for Customer breach except as and to the extent such breach is due to or occurs as a result of breach of this Agreement by Partner, including, without limitation, the requirements of Sections 2.1, 2.4 and 2.5.
3. Go To Market and Use of Trademarks.
3.1. Go To Market. Subject to the terms of this Section 3, each party will have the right to refer to the fact that Partner is in a collaborative relationship with NTT on its website and in marketing collateral with respect to the subject matter of the applicable Addendum(s) in effect between the parties. Otherwise, neither party will make any public statement or issue any press release with respect to this relationship without the prior written consent of the other party.
3.2. Trademark Use. Each party (the “Trademark Party”) grants the other party a worldwide, non-exclusive, non-transferable royalty free limited license (with no right of sublicense) during the term of this Agreement to use the Trademark Party’s Trademarks solely for the purpose of carrying out the terms of the Go To Market Plan and as otherwise contemplated by this Agreement, including but not limited to, the promotion of the Services and Consulting, the parties’ joint efforts and channel programs; provided, that, such Trademarks are used solely in accordance with the Trademark Party’s specifications as to style, color, and typeface, as such specifications may be modified by such party from time to time and communicated to the other party. Partner agrees not to attach any other trademarks, logos or trade designations to the Services, nor to remove or modify any of NTT’s Trademarks or proprietary notices affixed to the Services, Service deliverables or documentation. Partner shall not affix any NTT Trademarks to services other than the genuine Services. Upon notice from the Trademark Party of its objection to any improper or incorrect use of the Trademark Party’s Trademarks, the other party shall correct or stop such usage as soon as reasonably practicable.
3.3. Ownership of Trademarks. Each Trademark Party claims ownership of all right, title, and interest in and to its Trademarks, together with any new or revised trademarks, trade names, and logos that such Trademark Party may adopt to identify it or any of its products or services. Neither party shall claim any rights in the other party’s Trademarks or take any action that threatens or challenges the Trademark Party’s proprietary rights therein. All use by a party of the Trademark Party’s Trademarks and all goodwill associated therewith shall inure exclusively to the benefit of the Trademark Party and its Affiliates. Partner is prohibited from using or registering any of NTT’s Trademarks or domain names, including without limitation any terms containing the terms “Samurai” as part of Partner’s company name, service name, trade names or domain names. NTT does not authorize Partner’s use of any of the NTT Trademarks to promote or use for search engine ranking or ad word purchase or as part of a trade name, business name or Internet domain name in any manner that could be detrimental to the interests of NTT. If Partner registers or otherwise obtains rights to marks (as trademarks, service marks, URLs, company names or otherwise) in violation of this Agreement, Partner will, at its own expense, transfer and assign such rights to NTT, and execute all documents reasonably requested by NTT to facilitate such assignment or transfer.
4. Confidentiality.
4.1. Definitions. In connection with this Agreement, each party (“Recipient”) may be exposed to or acquire Confidential Information of the other party (“Discloser”) or third parties to whom Discloser has a duty of confidentiality. “Confidential Information” means non-public information in any form and regardless of the method of acquisition that the Discloser designates as confidential to Recipient or which, due to the nature of such information and/or under the circumstances surrounding disclosure ought to be treated as confidential by the Recipient. Confidential Information shall not include information that is: (i) in or becomes part of the public domain (other than by disclosure by Recipient in violation of this Agreement); (ii) previously known to Recipient (which must be demonstrable) without an obligation of confidentiality; (iii) independently developed by Recipient without use of Discloser’s Confidential Information; (iv) rightfully obtained by Recipient from third parties without an obligation of confidentiality, or (v) Evidence Data.
4.2. Restrictions on Use. Recipient shall hold Discloser’s Confidential Information in strict confidence and shall not disclose any such Confidential Information to any third party, other than to its employees, agents and consultants, including without limitation, counsel, accountants and advisors (collectively, “Representatives”) and its Affiliates and their Representatives who need to know such information and who are bound by restrictions regarding disclosure and use of such information comparable to and no less restrictive than those set forth herein. Recipient shall not use Discloser’s Confidential Information for any purpose other than to carry out the terms of this Agreement and further the parties’ business relationship. Recipient shall take the same degree of care that it uses to protect its own confidential information of similar nature and importance (but in no event less than reasonable care) to protect the confidentiality and avoid the unauthorized use, disclosure, publication or dissemination of the Discloser’s Confidential Information. Recipient shall promptly notify Discloser of any breach of this Agreement that it becomes aware, and in any event, shall be responsible for any breach of this Agreement by any of its Affiliates, Representatives or Affiliates’ Representatives.
4.3. Exceptions. Recipient may disclose Discloser’s Confidential Information: (i) to the extent required by applicable law or regulation, or (ii) pursuant to a subpoena or order of a court or regulatory, self-regulatory or legislative body of competent jurisdiction, or (iii) in connection with any regulatory report, audit or inquiry, or (iv) where requested by a regulator with jurisdiction over Recipient. In the event of such a requirement or request, Recipient shall to the extent permissible by law give the Discloser prompt written notice of such requirement or request prior to such disclosure and reasonable assistance (at Discloser’s expense) in obtaining an order protecting the information from public disclosure. NTT and Partner agree that the terms and conditions of this Agreement as it relates to the other party shall be treated as Confidential Information and shall not be disclosed to any third party except as otherwise provided in this Section (Confidentiality) and (i) in connection with the enforcement of this Agreement or rights under this Agreement; or (ii) in confidence, in connection with an actual or proposed merger, acquisition or similar transaction.
4.4. Return or Destruction. Upon Discloser’s written request, Recipient shall use commercially reasonable efforts to either return or destroy the Confidential Information and any copies or extracts thereof. However, Recipient, its Affiliates and their Representatives may retain any Confidential Information that: (i) they are required to keep for compliance purposes under a document retention policy or as required by applicable law, professional standards, a court or regulatory agency; or (ii) have been created electronically pursuant to automatic or ordinary course archiving, back-up, security or disaster recovery systems or procedures; provided, however, that any such retained information shall remain subject to this Agreement. If Recipient elects to destroy Discloser’s Confidential Information (subject to any retention rights provided in this Agreement), Discloser may request that Recipient provide it with written confirmation of destruction in compliance with this provision.
4.5. Equitable Relief. Each party acknowledges that a breach of this Section (Confidentiality) shall cause the other party irreparable injury and damage. Therefore, each party agrees that those breaches may be stopped through injunctive proceedings in addition to any other rights and remedies which may be available to the injured party at law or in equity without the posting of a bond.
4.6. NTT Development; Communications. It is expressly understood, acknowledged and agreed that Partner may, regardless of whether or not formally requested, provide to NTT suggestions, comments and feedback regarding the Services or Consulting, including but not limited to usability, bug reports and test results, with respect to the foregoing (collectively, “Feedback”). Partner grants NTT, under all of its intellectual property and proprietary rights, the following worldwide, non-exclusive, perpetual, irrevocable, royalty free, fully paid up rights without any attribution of any kind: (i) to make, use, copy, modify, sell, distribute, sub-license, and create derivative works of, the Feedback as part of any NTT Service or Consulting or related technology, specification or other documentation; (ii) to publicly perform or display, import, broadcast, transmit, distribute, license, offer to sell, and sell, rent, lease or lend copies of the Feedback (and derivative works thereof) as part of any NTT’s Service or Consulting or related technology, specification or other documentation; (iii) solely with respect to your copyright and trade secret rights, to sublicense to third parties the foregoing rights, including the right to sublicense to further third parties; and (iv) to sublicense to third parties any claims of any patents owned or licensable by Partner that are necessarily infringed by a third party product, technology or service that uses, interfaces, interoperates or communicates with the Feedback or portion thereof incorporated into an NTT Service or Consulting or related technology, specification or other documentation. Further, Partner warrants that its Feedback is not subject to any license terms that would purport to require NTT to comply with any additional obligations with respect to any NTT Service or Consulting or related technology, specification or other documentation that incorporate any Feedback.
5. Representations and Warranties.
Each party represents and warrants that it has full power and authority to execute this Agreement and to take all actions required by, and to perform the agreements contained in, this Agreement, and that each party’s obligations under this Agreement do not conflict with its obligations under any other agreement to which it is a party.
6. WARRANTY DISCLAIMER. EXCEPT FOR ANY LIMITED EXPRESS WARRANTIES MADE BY NTT FOR THE SERVICES AND/OR CONSULTING IN ITS END USER AGREEMENT(S) (WHICH SHALL BE APPLICABLE ONLY IF PARTNER OR CUSTOMER IS AN END USER OF THE APPLICABLE SERVICE OR CONSULTING UNDER SUCH AN AGREEMENT), NTT MAKES NO OTHER WARRANTIES RELATING TO THE SERVICES OR CONSULTING, EXPRESS, IMPLIED OR STATUTORY (EXCEPT FOR THOSE PRESCRIBED BY LAW WHICH CANNOT BE EXCLUDED), INCLUDING WITHOUT LIMITATION ANY WARRANTIES OF NON-INFRINGEMENT OF THIRD PARTY RIGHTS, FITNESS FOR A PARTICULAR PURPOSE, OR MERCHANTABILITY. PARTNER ACKNOWLEDGES, UNDERSTANDS AND AGREES THAT NTT DOES NOT GUARANTEE OR WARRANT THAT USE OF THE SERVICES OR CONSULTING WILL FIND, LOCATE OR DISCOVER ALL SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND WILL NOT HOLD NTT RESPONSIBLE THEREFOR. PARTNER AGREES NOT TO REPRESENT TO CUSTOMER OR ANY THIRD PARTY THAT NTT HAS PROVIDED SUCH GUARANTEE OR WARRANTY. NTT SERVICES ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENTS REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NTT SERVICES ARE NOT FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY OR PROPERTY DAMAGE.
7. No individual is authorized by NTT to make any warranty or representation concerning the performance of the Services or Consulting. Partner shall make no warranty, express or implied, on behalf of NTT.
8. Indemnification.
8.1. Infringement Indemnity. NTT will defend, at its own expense, a third-party claim, suit or proceeding brought against Partner insofar as it is based on a claim that a Service or a Consulting deliverable when used by Partner in accordance with the terms of this Agreement, constitutes an infringement of a patent or copyright valid within the Territory. NTT shall pay all damages, costs and expenses finally awarded to third parties as a result of a final judgment against Partner or settlement of such claim negotiated by NTT, but shall not be responsible for any compromise made without its consent. To qualify for such defense and payment, the Partner must: (i) give NTT prompt written notice of any such claim, and (ii) allow NTT to control, and fully cooperate with NTT in, the defense and all related settlement negotiations. Upon notice of an alleged infringement, or if, in NTT’s opinion, such a claim is likely, NTT shall have the right, at its option, to obtain the right to continue the distribution of Services, substitute other products or services with similar operating capabilities and/or performance, or modify the Service or Consulting deliverable so that it is no longer infringing or subject to a third party claim. In the event that none of the above options are reasonably available in NTT’s sole discretion, NTT may terminate this Agreement’ and all accompanying subscription licenses. In the event of such termination, NTT shall, without limiting its obligation to defend and indemnify Partner, refund to Partner: (i) the fees paid for Services subscriptions prorated for the remainder of any pre-paid subscription term unused by the Customer, or (ii) the portion of the fees attributable to the Service deliverable, as applicable. This Section (Infringement Indemnity) states NTT’s entire liability under this Agreement for all claims of intellectual property infringement. NTT shall not be responsible for any claim of infringement that arises from (i) modifications to a Service or Consulting deliverable not made by NTT, (ii) use of a Service or Consulting deliverable in a manner or in combination with products or services not provided by NTT to the extent such claim would not have occurred except for such modifications, use or combination; (iii) use of other than the latest available version of the Services or Consulting deliverable made available to Partner or the Customer; or (iv) any use of the Services or Consulting deliverable not in accordance with this Agreement or the applicable end user terms, documentation or specifications.
8.2. Indemnity. NTT and Partner (each an “Indemnitor”) shall defend and indemnify the other party and its Affiliates, and their officers, directors, employees, and agents (collectively, “Indemnitees,” respectively, for each of NTT and Partner), from any third party claims and the associated costs, damages or settlement (inclusive of attorney’s fees and court costs) that an Indemnitee may incur as a result of: (i) an Indemnitor’s breach of this Agreement or any agreement with the Customer; (ii) an Indemnitor making a representation, warranty, or other statement on behalf of the other party that is not specifically authorized in writing; or (iii) an Indemnitor’s or its representative’s negligent act or negligent omission, fraud or willful misconduct. To qualify for such defense and payment, the Indemnitee must: (i) give the Indemnitor prompt written notice of any such claim, and (ii) allow Indemnitor to control, and fully cooperate with Indemnitor in, the defense and all related settlement negotiations.
9. Limitation of Liability. Each party’s sole remedy and the other party’s sole obligation shall be governed by this Agreement.
9.1. Maximum Liability.
9.1.1 EXCEPT IN THE CASE OF NTT’s DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 8.1, EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 8.2, FRAUD, GROSS NEGLIGENCE OR WILLFUL MISCONDUCT, BREACHES OF SECTION 4 (CONFIDENTIALITY) AND PARTNER’S BREACH OF SECTION 2.3 (RESTRICTIONS) OF THIS AGREEMENT, IN NO EVENT SHALL EITHER PARTY’S LIABILITY TO THE OTHER EXCEED THE GREATER OF: (A) THE AGGREGATE AMOUNTS PAID OR OWED BY PARTNER TO NTT UNDER THIS AGREEMENT WITH RESPECT TO THE SERVICE OR CONSULTING DELIVERABLE THAT IS THE SUBJECT OF THE CLAIM IN THE 12 MONTHS PRECEDING THE FIRST OCCURRENCE OF THE EVENTS GIVING RISE TO ANY CLAIM, OR (B) $250,000.
9.1.2 IN THE CASE OF EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 8.2, FRAUD, GROSS NEGLIGENCE OR WILLFUL MISCONDUCT, BREACHES OF SECTION 4 (CONFIDENTIALITY), IN NO EVENT SHALL EITHER PARTY’S LIABILITY TO THE OTHER EXCEED THE GREATER OF: (A) FOUR (4) TIMES THE AGGREGATE AMOUNTS PAID OR OWED BY PARTNER TO NTT UNDER THIS AGREEMENT OR (B) $1,000,000.
9.2. EXCEPT IN THE CASE OF EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 6, FRAUD, GROSS NEGLIGENCE OR WILLFUL MISCONDUCT, BREACHES OF SECTION 4 (CONFIDENTIALITY) AND PARTNER’S BREACH OF SECTION 2.3 (RESTRICTIONS) OF THIS AGREEMENT IN NO EVENT SHALL A PARTY BE LIABLE TO THE OTHER PARTY FOR ANY SPECIAL, INDIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING FROM BREACH OF WARRANTY, BREACH OF CONTRACT, NEGLIGENCE, OR ANY OTHER LEGAL THEORY, WHETHER IN TORT OR CONTRACT, EVEN IF SUCH PARTY IS AWARE OF THE LIKELIHOOD OF SUCH DAMAGES OCCURRING. NTT SHALL NOT BE RESPONSIBLE FOR ANY DAMAGES OR EXPENSES RESULTING FROM ALTERATION OR UNAUTHORIZED USE OF THE SERVICE, OR FROM THE UNINTENDED AND UNFORESEEN RESULTS OBTAINED BY PARTNER OR ANY CUSTOMERS RESULTING FROM SUCH USE.
10. Legal Compliance.
10.1. Export. The parties shall comply with all applicable United States and foreign laws and regulations, including without limitation: (i) all applicable laws and regulations relating to the advertising, packaging, sale, and distribution of the Service and Consulting deliverables, (ii) all United States export laws and regulations governing the export or re-export of all Services/Consulting and any products or services provided in connection with the Services/Consulting, including without limitation the U.S. Export Administration Regulations, the International Traffic in Arms Regulations, and any regulations administered by the Department of the Treasury’s Office of Foreign Assets Control, and (iii) all applicable laws and regulations of countries other than the United States that govern the importation, use, or re-export of the Services/Consulting. Partner further agrees to comply with any reasonable conditions that NTT notifies Partner are contained in any applicable export licenses pertaining to the Services/Consulting. Partner shall comply with any reporting requirements that may apply to the export or re-export of the Services/Consulting deliverables and shall provide to NTT and the appropriate governmental authority any periodic reports containing such information as may be required under applicable law. Partner further agrees to pay any taxes or tariffs that may apply to the export, or re-export of the Services/Consulting.
10.2. Sanctions. Partner warrants that (i) neither it or its Affiliates are subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”), and (ii) if at any time it or an Affiliate become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under this Agreement, or the continuing performance of this Agreement exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate this Agreement.
10.3. Applicable Laws. The parties shall at all times conduct their efforts hereunder with the highest commercial standards and in strict accordance with all applicable laws, rules, directives and regulations (“Laws”). Each party shall be responsible for current and ongoing familiarity and compliance with all Laws applicable to the importation, distribution, marketing, sale, operation, use or support of the Services and Consulting, and the privacy and protection of personal data.
10.4. Anti-bribery. Each party will maintain adequate policies and procedures designed to ensure that its officers, directors, employees and contractors comply, at all times, with all relevant and applicable laws concerning anti-bribery and corruption
10.5. Foreign Corrupt Practices Act. In conformity with the United States Foreign Corrupt Practices Act and with NTTs policies regarding foreign business practices, Partner and its employees and agents shall not directly or indirectly make and offer, payment, promise to pay, or authorize payment, or offer a gift, promise to give, or authorize the giving of anything of value for the purpose of influencing an act or decision of an official of any government (including a decision not to act) or inducing such a person to use his or her influence to affect any such governmental act or decision in order to assist Partner and/or NTT in obtaining, retaining or directing any such business.
11. Personal Information. Subject to compliance with applicable laws, including data protection laws, each party reserves the rights to transfer (both domestically and cross-border) and disclose information, including relevant confidential information and, as applicable, personal data of the other party’s personnel to the receiving party’s (and its affiliates’) directors, officers, employees, contractors, professional advisors, and third-party service providers, solely as needed to support or facilitate the performance and administration of the Agreement by the receiving party, provided that such information will be disclosed a) on a need-to-know basis only (based on the receiving party’s business operations); and b) subject to appropriate obligations of confidentiality and/or personal data transfer arrangements with such parties, as applicable.
12. Termination.
12.1. Term. The term of this Agreement shall commence as of the Effective Date of this Agreement and continue until terminated by either party as provided herein.
12.2. Termination Without Cause. Upon ninety (90) days prior written notice and payment of any unpaid amounts owed by the terminating party, either party may terminate this Agreement or any Addendum at any time without cause to the other party.
12.3. Termination With Cause. Either party may terminate this Agreement or any Addendum upon 30 days written notice for a material breach of this Agreement if such breach is not cured within such 30-day period.
12.4. Rights Upon Termination. Upon any termination of this Agreement: (i) all Addendum(s) executed under this Agreement shall automatically terminate, (ii) Partner shall remit all a) accrued but unpaid amounts due NTT and b) the unamortized portion of any fees prepaid by clients for Services or Consulting, (iii) Partner is no longer authorized to conduct any activities under this Agreement, including without limitation under any executed Addendum(s); (iv) Partner shall immediately cease using the Trademarks of NTT and discontinue all representations that it has a relationship with NTT; and (iv) Partner shall promptly return to NTT any tangible sales literature, brochures, technical information, price lists, samples, evaluation units, and other materials received from NTT Security Holdings or if intangible, destroy such items in a secure manner, except to the extent such materials are reasonably required for delivery of Services or provisions of Consulting ordered prior to termination as directed by NTT.
12.5. Survival. The Sections entitled Ownership, Restrictions, Ownership of Trademarks, Confidentiality, Warranty Disclaimer, Indemnification, Limitation of Liability, Rights Upon Termination, Survival and Miscellaneous shall survive expiration or termination of this Agreement for any reason.
13. Miscellaneous.
13.1. Assignment. Partner may not assign this Agreement without the prior written approval of NTT. For the purposes of this section, a change in the persons or entities that control 50% or more of the equity securities or voting interest of Partner shall be considered an assignment of Partner’s rights. NTT may assign this Agreement at any time and may delegate aspects of its performance under this Agreement to any of its Affiliates.
13.2. Audit Rights. Once per calendar year, upon reasonable notice and during Partner’s normal business hours, NTT shall have the right to audit, through an independent third party auditor selected by NTT and approved by Partner (which approval will not be unreasonably withheld or delayed) Partner’s books of account and business records as necessary to verify Partner’s compliance with this Agreement, including but not limited to, compliance with the requirements of Sections 2.1, 2.4 and 2.5 and the accuracy of the amounts paid pursuant to this Agreement. The auditor may disclose to NTT Security Holdings, with a written copy to Partner, only whether the amounts paid are correct or incorrect and the amount of any discrepancy. No other information may be provided to NTT Security Holdings. If the auditor identifies a discrepancy, the appropriate party shall pay to the other party the amount of the discrepancy (plus interest) within thirty (30) days of the date Partner receives the auditor’s written report. If such audit reveals an underpayment of more than 5%, Partner shall also reimburse NTT Security Holdings for the reasonable costs and expenses of such audit.
13.3. Notices. All notices given pursuant to this Agreement shall be in writing and effective: (i) upon receipt if hand delivered; (ii) on the next day after being sent by email if followed by the methods in subsections (iii) or (iv); (iii) on the third business day after being sent prepaid by certified or registered mail; or (iv) on the second business day after being sent prepaid by commercial express courier. Notices to NTT shall be sent to Råsundavägen 12, 169 67 Solna, Sweden, Attention: COO, with a copy to legal@security.ntt. Notices to Partner will be sent to the address first set forth above, attention Chief Executive Officer for Partner, with a “copy to:”.
13.4. Waiver. The waiver by either party of a breach of any provision contained herein shall be in writing and shall in no way be construed as a waiver of any succeeding breach of such provision or the waiver of the provision itself.
13.5. Severability. In the event that any provision of this Agreement shall be unenforceable or invalid under any applicable law or be so held by applicable court decision, such unenforceability or invalidity shall not render this Agreement unenforceable or invalid as a whole. In such event, such provision shall be changed and interpreted so as to best accomplish the objectives of such provision within the limits of applicable law or applicable court decisions, or if necessary to maintain the validity of the remaining terms, removed from the Agreement.
13.6. Controlling Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
13.7. Dispute Resolution and Attorneys’ Fees. Except for claims for breach of confidentiality obligations, the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
13.8. No Agency. The use of the term “Partner” is for convenience and does not reflect an intention of the parties to form a legal partnership. The parties are independent contractors under this Agreement, and nothing contained herein shall be construed as creating any agency, partnership, employment, or other form of joint enterprise between the parties and nothing contained in this Agreement (including use of the term “Partner”) will be construed to (i) give either Party the power to direct and control the day-to-day activities of the other, (ii) create a principal-agent or employer-employee relationship, or (iii) give either Party the authority to bind the other Party to any contract with a third party.
13.9. Force Majeure. NTT, NTT agents and Affiliates, Partner and Partner’s agents shall not be liable for any delay or failure to perform for any cause beyond their reasonable control, except for the payment of money, to the extent that performance is rendered impossible by strike, fire, flood, wars, sabotage, civil unrest, governmental acts, or any other reason where failure to perform is beyond the reasonable control of and is not caused by the negligence of the nonperforming party.
13.10. Counterparts and Electronic Copies. This Agreement may be e-signed. Further, if this Agreement is signed in two counterparts, the two counterparts together shall form a single agreement as if both parties had executed the same document. Electronic copies (e.g., .pdf, .tif) and facsimile signature pages shall be binding as if original.
13.11. Entire Agreement; Order of Precedence. This Agreement completely and exclusively states the agreement of the parties regarding its subject matter. This Agreement supersedes all prior proposals, agreements or other communications between the parties, oral or written, regarding such subject matter. This Agreement shall not be modified except by a subsequently dated written amendment or appendix signed on behalf of NTT and Partner by their duly authorized representatives. Any provision of Partner’s purchase order or other document purporting to vary or add to the provisions hereof shall be void. In the event of any conflict between the Terms and those of any Addendum, the Terms will govern, except when the Addendum states that the conflicting provision is intended to apply with respect to the subject matter of the Addendum and then such provision will apply with respect to the subject matter of that Addendum only.
5.4.4.2 - Master Partner Agreement (v2.0 2024-04-25)
This document has been superseded. For the latest version please click HERE.
We have updated our Master Partner Agreement. If you are a new Partner, then the Master Partner Agreement will be effective as of 26 May 2023. If you are an existing Partner, we are providing you with prior notice of these changes which will be effective as of 26 June 2023. For the previous version of our Master Partner Agreement, please click here.
1. Definitions.
1.1 “Affiliate” means any majority-owned subsidiary or other entity which a party controls or is controlled by, or with which it is under common control with a party.
1.2 “Consulting” means the consulting services provided by NTT as provided for under the terms of the applicable Service Descriptions. By way of example, Consulting may include, incident response and investigation, compromise assessments, forensic services related to cyber security adversaries, tabletop exercises and penetration tests related to cyber security and typically provided on a time and material basis and sometimes sold as a retainer.
1.3 “Customer(s)” means the current or potential customers of Partner for the applicable NTT Samurai Services or Consulting excluding any entity or person deemed in NTT reasonable discretion as a competitor of NTT; provided, when used in the Terms of Service as referenced in Sections 1.10, 2.1, 2.4 and 2.6 of this Agreement, “Customer” shall mean Partner.
1.4 “Evidence Data” means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
1.5 “Intellectual Property Rights” means copyrights (including, without limitation, the exclusive right to use, reproduce, modify, distribute, publicly display, and publicly perform the copyrighted work), trademark rights (including rights in, without limitation, trade names, trademarks, service marks, and trade dress), patent rights (including, without limitation, (i) all rights worldwide in patent applications, any patents issuing therefrom, and all provisional rights with respect to patent applications, (ii) all rights worldwide in any improvements, substitutions, divisionals, patents of addition, continuations, continuations-in-part, reissues, renewals, registrations, confirmations, re-examinations, extensions, supplementary protection certificates, term extensions (under applicable patent law or regulation or other law or regulation), and certificates of invention of any patents or patent applications, and (iii) all rights worldwide to exploit any of the foregoing), know-how, trade secrets, moral rights, right of publicity, authors’ rights, contract and licensing rights, all other intellectual property rights as may exist now and/or hereafter come into existence, and all renewals and extensions thereof, regardless of whether such rights arise under the law of the Territory or any other state, country, region, or jurisdiction.
1.6 “NTT Content” means NTTs proprietary data that is contained in or made available as part of Services and Consulting.
1.7 “Samurai Services” consists of NTT MDR offerings for security operations management which are listed and further described in the relevant Service Descriptions.
1.8 “Services” means Samurai Services and Consulting. The Service Descriptions for the Services can be found here
1.9 “Trademarks” means the words, names, symbols, designs, or any combination thereof, used in commerce to identify and distinguish the products, services, and company, of a party from those of others and to indicate the source of such consulting and services.
1.10 “Terms of Service” or “ToS” means the current standard terms, conditions, and legal notices, applicable to the Samurai Services found here including any product specific terms that are included in valid quotes issued by NTT and related to the Samurai Services.
1.11 “Territory" means the jurisdiction(s) listed in the Cover sheet.
1.12 “Partner Tier” means the type of obligations to, and benefits and support the Partner will receive from, NTT as defined in the Partner Program Guide
2. Appointment and Restrictions.
2.1. Nonexclusive Appointment.Provided that Partner complies at all times with the terms and conditions of this Agreement, NTT appoints Partner and Partner accepts appointment as a nonexclusive Partner with non-transferable, limited right to market and promote the Services to Customers within the Territory provided, Partner shall expressly accept and agree to the Terms of Service with NTT prior to accessing the Services. The applicable Samurai Services and Consulting to which this appointment applies will be specified in the applicable Service Description(s). Partner agrees that nothing in this Agreement shall be construed to preclude NTT from directly or indirectly marketing, distributing, selling, or servicing any Services or Consulting to or for any third party in any location, including without limitation, other partners, resellers, distributors, managed service providers, and end-users. The rights and licenses granted to Partner under this Agreement are personal to Partner and Partner may not transfer or sublicense the appointment set forth in this Agreement.
2.2. Ownership. Except for the limited license(s) expressly granted to Partner in this Agreement, all right, title and interest in and to the Services, Consulting, NTT Content, including the concepts and technology inherent in the Services, NTT Content and deliverables, all Intellectual Property Rights related thereto, shall at all times be and remain, relative to Partner, the sole and exclusive property of NTT. No other licenses, immunity or rights, express or implied are granted by NTT, by implication, estoppel, or otherwise.
2.3 Restrictions. Partner shall, by all appropriate means, prevent unauthorized disclosure, publication, display or use of the Services, Consulting and NTT Content. Partner shall not, and shall not encourage or authorize any third party to, modify or reverse engineer any Services or the technology related thereto, or attempt to gain unauthorized access to the Services or the NTT Content. Partner shall not remove, alter, cover or obfuscate any end-user agreement, privacy notice, copyright notices or other proprietary legends placed or embedded by NTT on or in the Services documentation, NTT Content, deliverables or literature related to any of the foregoing. Partner shall not affix or place any labels or markings on the Services, Consulting output, Service deliverables, or literature related to the foregoing, that might be interpreted as a claim of ownership by Partner or any third party in the foregoing. Without NTT’s prior written consent (an email from the Chief Operating Officer shall suffice), Partner shall not, nor have a third party, (i) perform a competitive analysis on the Services or Consulting, or (ii) publish a review or the results of any internal evaluation of the Services or Consulting.
2.4 Terms of Service. With respect to each accepted quote for Services, Partner shall expressly accept and agree to be bound by the Terms of Service with NTT. Partner shall not be granted, and shall not grant to Customers, any access, use or other rights to the Services, unless Partner has accepted and agreed to the Terms of Service. Partner will promptly report to NTT any breach, or suspected breach, of the Terms of Service of which it becomes aware. NTT reserves the right to refuse to issue a quote, accept an order, or make the Services available to any Customer; provided that NTT provides to Partner a written notice of its objection to such Customer.
2.5 Changes to ToS. Partner acknowledges that NTT may update the Terms of Services from time to time as set forth in the Terms of Service.
2.6 Governing Terms and Conditions. Partner acknowledges and agree that, A) as to Partner, NTT’s obligations to Partner shall be as stated in this Agreement and the Terms of Service, and B) as to Customers, i) Partner shall be solely liable to Customers.
2.7 Partner Tier. Partner agrees to abide by the obligations of the Tier they hold. Partner further agrees that should they cease to meet such obligations NTT may, at it’s sole discretion, reduce Partner’s tier or remove Partner’s status as a Partner.
2.8 Partner Conduct. Partner shall: (i) conduct business in a manner that reflects favorably at all times on the Services, Consulting, goodwill and reputation of NTT; (ii) avoid deceptive, misleading or unethical practices that are or might be detrimental to NTT; (iii) refrain from making any false or misleading representations or warranties with regard to NTT, the Services or Consulting; and (iv) comply with all applicable laws, rules, ordinances, decrees and regulations applicable to Partner’s activities under this Agreement, including without limitation, any applicable privacy laws and the Foreign Corrupt Practices Act, export laws and sanctions regulations or any similar legislation. Partner has reviewed and understands NTT’s Privacy Notice located here Partner shall not, directly or indirectly, through action or inaction, cause NTT to be in violation of its Privacy Notice or applicable laws.
3. Services.
During the term of the MPA and subject to the terms and conditions therein and herein, NTT agrees to provide certain: (i) Samurai Services, and/or (ii) Consulting services purchased by Partner in accordance with the terms of this MPA. The Services purchased are specified in a quote delivered by NTT and accepted by Partner without alteration (“Order”) or statement of work (“SOW”) executed (or, if online, accepted pursuant to an online order process) by the parties which references this MPA. A detailed description of the Services being purchased is provided in the service description and for such Services attached to the Order (or linked to if the Partner is purchasing online) and incorporated therein by reference. All Orders (whether signed or accepted pursuant to an online order process) and all SOWs are subject to the terms and conditions of this MPA and will include the following: (i) the particular Services to be performed, including, if applicable, the applicable Specification Document; (i) the subscription term of the Services; (iii) the compensation and billing method for the Services; and (iv) any other applicable information agreed to by the parties.
4. Go To Market and Use of Trademarks.
4.1 Go To Market. Subject to the terms of this Section 4, each party will have the right to refer to the fact that Partner is in a collaborative relationship with NTT on its website and in marketing collateral. Otherwise, neither party will make any public statement or issue any press release with respect to this relationship without the prior written consent of the other party.
4.2 Trademark Use. Each party (the “Trademark Party”) grants the other party a worldwide, non-exclusive, non-transferable royalty free limited license (with no right of sublicense) during the term of this Agreement to use the Trademark Party’s Trademarks solely for the purpose of carrying out the terms of the Go To Market Plan and as otherwise contemplated by this Agreement, including but not limited to, the promotion of the Services and Consulting, the parties’ joint efforts and channel programs; provided, that, such Trademarks are used solely in accordance with the Trademark Party’s specifications as to style, color, and typeface, as such specifications may be modified by such party from time to time and communicated to the other party. Partner agrees not to attach any other trademarks, logos or trade designations to the Services, nor to remove or modify any of NTT’s Trademarks or proprietary notices affixed to the Services, Service deliverables or documentation. Partner shall not affix any NTT Trademarks to services other than the genuine Services. Upon notice from the Trademark Party of its objection to any improper or incorrect use of the Trademark Party’s Trademarks, the other party shall correct or stop such usage as soon as reasonably practicable.
4.3 Ownership of Trademarks. Each Trademark Party claims ownership of all right, title, and interest in and to its Trademarks, together with any new or revised trademarks, trade names, and logos that such Trademark Party may adopt to identify it or any of its products or services. Neither party shall claim any rights in the other party’s Trademarks or take any action that threatens or challenges the Trademark Party’s proprietary rights therein. All use by a party of the Trademark Party’s Trademarks and all goodwill associated therewith shall inure exclusively to the benefit of the Trademark Party and its Affiliates. Partner is prohibited from using or registering any of NTT’s Trademarks or domain names, including without limitation any terms containing the terms “Samurai” as part of Partner’s company name, service name, trade names or domain names. NTT does not authorize Partner’s use of any of the NTT Trademarks to promote or use for search engine ranking or ad word purchase or as part of a trade name, business name or Internet domain name in any manner that could be detrimental to the interests of NTT. If Partner registers or otherwise obtains rights to marks (as trademarks, service marks, URLs, company names or otherwise) in violation of this Agreement, Partner will, at its own expense, transfer and assign such rights to NTT, and execute all documents reasonably requested by NTT to facilitate such assignment or transfer.
5. Samurai Service Fees.
NTT’s’ fees for the Samurai Services are set forth on the Order. The Samurai Services ordered will commence on the date set forth in the Order (the “Commencement Date”), and NTT shall invoice Partner for Samurai Services on the Commencement Date and thereafter in advance on the renewal date. If there is no date in the Order, the date on which the Quote was accepted shall be the Commencement Date.
6. Consulting Service Fees.
NTT’s fees and billing milestones for the Consulting Services are set forth on the applicable Order or Statement of Work (“SOW”) (as applicable).
7. Invoice and Payment.
NTT will invoice Partner in accordance with the billing terms set forth and detailed on the applicable Order or SOW. All charges, fees, payments and amounts hereunder will be in currency designated in the applicable Order or SOW, and (ii) all undisputed amounts due hereunder are payable within thirty (30) days from the date of the invoice, which shall be submitted to Partner electronically (the “Invoice Due Date”).
8. Disputes and Nonpayment.
Partner shall have the right to reasonably, and in good faith, dispute any invoice or any portion of any invoice claimed by NTT as due and payable provided that, prior to the Invoice Due Date, Partner (i) timely pays any undisputed portion of the amount due and payable, and (ii) provides NTT with written notice specifying the disputed amount and the basis for the dispute in reasonable detail. Except for amounts that are disputed in good faith by Partner in accordance with this Section 8, NTT reserves the right to charge Partner a late fee of one and a half percent (1.5%) per month or the maximum rate permitted by law, whichever is less, for invoices not paid on or before the Invoice Due Date. In addition, NTT, without waiving any other rights or remedies to which it may be entitled, shall have the right, upon prior written notice to Partner, to suspend the Services until such payment is received.
9. Taxes.
Partner shall be responsible for the payment of all taxes and fees assessed or imposed on the Services provided or the amounts charged under the Order/SOW in any country or territory in which the Partner receives the benefit of the Services, including any sales, use, excise, value-added, or comparable taxes, but excluding taxes: (i) for which the Partner has provided a valid resale or exemption certificate, or (ii) imposed on NTT’ income or arising from the employment relationship between NTT and its employees. Should any payments become subject to withholding tax, the Partner will deduct these taxes from the amount owed and pay the taxes to the appropriate tax authority in accordance with applicable tax laws. Partner will promptly provide NTT with receipts or documents evidencing these tax payments. NTT shall not be liable for any withholding tax, penalty or interest due as a result of Partner’s failure to withhold any applicable tax.
10. Change Control.
“Change” means any change to the scope of engagement that (i) would modify NTT’s obligations in relation to delivery of the Services, or (ii) would alter the cost to Partner for the Services, or (iii) is agreed by Partner and NTT in writing to be a Change. From time to time during the term of the Services, Partner or NTT may propose Changes to the scope of the engagement. Any Change to the applicable Order/SOW shall be implemented by request for, issuance of, and acceptance of a quote. For the avoidance of doubt, change described in this Section 10 does not apply to the composition of the Samurai Service as defined in the Service Description.
11. Confidentiality.
11.1 Definitions. In connection with this Agreement, each party (“Recipient”) may be exposed to or acquire Confidential Information of the other party (“Discloser”) or third parties to whom Discloser has a duty of confidentiality. “Confidential Information” means non-public information in any form and regardless of the method of acquisition that the Discloser designates as confidential to Recipient or which, due to the nature of such information and/or under the circumstances surrounding disclosure ought to be treated as confidential by the Recipient. Confidential Information shall not include information that is: (i) in or becomes part of the public domain (other than by disclosure by Recipient in violation of this Agreement); (ii) previously known to Recipient (which must be demonstrable) without an obligation of confidentiality; (iii) independently developed by Recipient without use of Discloser’s Confidential Information; (iv) rightfully obtained by Recipient from third parties without an obligation of confidentiality, or (v) Evidence Data.
11.2 Restrictions on Use. Recipient shall hold Discloser’s Confidential Information in strict confidence and shall not disclose any such Confidential Information to any third party, other than to its employees, agents and consultants, including without limitation, counsel, accountants and advisors (collectively, “Representatives”) and its Affiliates and their Representatives who need to know such information and who are bound by restrictions regarding disclosure and use of such information comparable to and no less restrictive than those set forth herein. Recipient shall not use Discloser’s Confidential Information for any purpose other than to carry out the terms of this Agreement and further the parties’ business relationship. Recipient shall take the same degree of care that it uses to protect its own confidential information of similar nature and importance (but in no event less than reasonable care) to protect the confidentiality and avoid the unauthorized use, disclosure, publication or dissemination of the Discloser’s Confidential Information. Recipient shall promptly notify Discloser of any breach of this Agreement that it becomes aware, and in any event, shall be responsible for any breach of this Agreement by any of its Affiliates, Representatives or Affiliates’ Representatives.
11.3 Exceptions. Recipient may disclose Discloser’s Confidential Information: (i) to the extent required by applicable law or regulation, or (ii) pursuant to a subpoena or order of a court or regulatory, self-regulatory or legislative body of competent jurisdiction, or (iii) in connection with any regulatory report, audit or inquiry, or (iv) where requested by a regulator with jurisdiction over Recipient. In the event of such a requirement or request, Recipient shall to the extent permissible by law give the Discloser prompt written notice of such requirement or request prior to such disclosure and reasonable assistance (at Discloser’s expense) in obtaining an order protecting the information from public disclosure. NTT and Partner agree that the terms and conditions of this Agreement as it relates to the other party shall be treated as Confidential Information and shall not be disclosed to any third party except as otherwise provided in this Section 11 (Confidentiality) and (i) in connection with the enforcement of this Agreement or rights under this Agreement; or (ii) in confidence, in connection with an actual or proposed merger, acquisition or similar transaction.
11.4 Return or Destruction. Upon Discloser’s written request, Recipient shall use commercially reasonable efforts to either return or destroy the Confidential Information and any copies or extracts thereof. However, Recipient, its Affiliates and their Representatives may retain any Confidential Information that: (i) they are required to keep for compliance purposes under a document retention policy or as required by applicable law, professional standards, a court or regulatory agency; or (ii) have been created electronically pursuant to automatic or ordinary course archiving, back-up, security or disaster recovery systems or procedures; provided, however, that any such retained information shall remain subject to this Agreement. If Recipient elects to destroy Discloser’s Confidential Information (subject to any retention rights provided in this Agreement), Discloser may request that Recipient provide it with written confirmation of destruction in compliance with this provision.
11.5 Equitable Relief. Each party acknowledges that a breach of this Section 11 (Confidentiality) shall cause the other party irreparable injury and damage. Therefore, each party agrees that those breaches may be stopped through injunctive proceedings in addition to any other rights and remedies which may be available to the injured party at law or in equity without the posting of a bond.
11.6 NTT Development; Communications. It is expressly understood, acknowledged and agreed that Partner may, regardless of whether or not formally requested, provide to NTT suggestions, comments and feedback regarding the Services or Consulting, including but not limited to usability, bug reports and test results, with respect to the foregoing (collectively, “Feedback”). Partner grants NTT, under all of its intellectual property and proprietary rights, the following worldwide, non-exclusive, perpetual, irrevocable, royalty free, fully paid up rights without any attribution of any kind: (i) to make, use, copy, modify, sell, distribute, sub-license, and create derivative works of, the Feedback as part of any NTT Service or Consulting or related technology, specification or other documentation; (ii) to publicly perform or display, import, broadcast, transmit, distribute, license, offer to sell, and sell, rent, lease or lend copies of the Feedback (and derivative works thereof) as part of any NTT’s Service or Consulting or related technology, specification or other documentation; (iii) solely with respect to your copyright and trade secret rights, to sublicense to third parties the foregoing rights, including the right to sublicense to further third parties; and (iv) to sublicense to third parties any claims of any patents owned or licensable by Partner that are necessarily infringed by a third party product, technology or service that uses, interfaces, interoperates or communicates with the Feedback or portion thereof incorporated into an NTT Service or Consulting or related technology, specification or other documentation. Further, Partner warrants that its Feedback is not subject to any license terms that would purport to require NTT to comply with any additional obligations with respect to any NTT Service or Consulting or related technology, specification or other documentation that incorporate any Feedback.
12. Representations and Warranties.
12.1 Each party represents and warrants that it has full power and authority to execute this Agreement and to take all actions required by, and to perform the agreements contained in, this Agreement, and that each party’s obligations under this Agreement do not conflict with its obligations under any other agreement to which it is a party.
12.2 WARRANTY DISCLAIMER. EXCEPT FOR ANY LIMITED EXPRESS WARRANTIES MADE BY NTT FOR THE SERVICES AND/OR CONSULTING IN ITS END USER AGREEMENT(S) (WHICH SHALL BE APPLICABLE ONLY IF PARTNER OR CUSTOMER IS AN END USER OF THE APPLICABLE SERVICE OR CONSULTING UNDER SUCH AN AGREEMENT), NTT MAKES NO OTHER WARRANTIES RELATING TO THE SERVICES OR CONSULTING, EXPRESS, IMPLIED OR STATUTORY (EXCEPT FOR THOSE PRESCRIBED BY LAW WHICH CANNOT BE EXCLUDED), INCLUDING WITHOUT LIMITATION ANY WARRANTIES OF NON-INFRINGEMENT OF THIRD PARTY RIGHTS, FITNESS FOR A PARTICULAR PURPOSE, OR MERCHANTABILITY. PARTNER ACKNOWLEDGES, UNDERSTANDS AND AGREES THAT NTT DOES NOT GUARANTEE OR WARRANT THAT USE OF THE SERVICES OR CONSULTING WILL FIND, LOCATE OR DISCOVER ALL SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND WILL NOT HOLD NTT RESPONSIBLE THEREFOR. PARTNER AGREES NOT TO REPRESENT TO CUSTOMER OR ANY THIRD PARTY THAT NTT HAS PROVIDED SUCH GUARANTEE OR WARRANTY. NTT SERVICES ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENTS REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NTT SERVICES ARE NOT FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY OR PROPERTY DAMAGE.
12.3 No individual is authorized by NTT to make any warranty or representation concerning the performance of the Services or Consulting. Partner shall make no warranty, express or implied, on behalf of NTT.
13. Indemnification.
13.1 Infringement Indemnity. NTT will defend, at its own expense, a third-party claim, suit or proceeding brought against Partner insofar as it is based on a claim that a Service or a Consulting deliverable when used by Partner in accordance with the terms of this Agreement, constitutes an infringement of a patent or copyright valid within the Territory. NTT shall pay all damages, costs and expenses finally awarded to third parties as a result of a final judgment against Partner or settlement of such claim negotiated by NTT, but shall not be responsible for any compromise made without its consent. To qualify for such defense and payment, the Partner must: (i) give NTT prompt written notice of any such claim, and (ii) allow NTT to control, and fully cooperate with NTT in, the defense and all related settlement negotiations. Upon notice of an alleged infringement, or if, in NTT’s opinion, such a claim is likely, NTT shall have the right, at its option, to obtain the right to continue the distribution of Services, substitute other products or services with similar operating capabilities and/or performance, or modify the Service or Consulting deliverable so that it is no longer infringing or subject to a third party claim. In the event that none of the above options are reasonably available in NTT’s sole discretion, NTT may terminate this Agreement’ and all accompanying subscription licenses. In the event of such termination, NTT shall, without limiting its obligation to defend and indemnify Partner, refund to Partner: (i) the fees paid for Services subscriptions prorated for the remainder of any pre-paid subscription term unused by the Customer, or (ii) the portion of the fees attributable to the Service deliverable, as applicable. This Section 13 (Infringement Indemnity) states NTT’s entire liability under this Agreement for all claims of intellectual property infringement. NTT shall not be responsible for any claim of infringement that arises from (i) modifications to a Service or Consulting deliverable not made by NTT, (ii) use of a Service or Consulting deliverable in a manner or in combination with products or services not provided by NTT to the extent such claim would not have occurred except for such modifications, use or combination; (iii) use of other than the latest available version of the Services or Consulting deliverable made available to Partner or the Customer; or (iv) any use of the Services or Consulting deliverable not in accordance with this Agreement or the applicable end user terms, documentation or specifications.
13.2 Indemnity. NTT and Partner (each an “Indemnitor”) shall defend and indemnify the other party and its Affiliates, and their officers, directors, employees, and agents (collectively, “Indemnitees,” respectively, for each of NTT and Partner), from any third party claims and the associated costs, damages or settlement (inclusive of attorney’s fees and court costs) that an Indemnitee may incur as a result of: (i) an Indemnitor’s breach of this Agreement or any agreement with the Customer; (ii) an Indemnitor making a representation, warranty, or other statement to a Customer on behalf of the other party that is not specifically authorized in writing; or (iii) an Indemnitor’s or its representative’s gross negligence, fraud or willful misconduct. To qualify for such defense and payment, the Indemnitee must: (i) give the Indemnitor prompt written notice of any such claim, and (ii) allow Indemnitor to control, and fully cooperate with Indemnitor in, the defense and all related settlement negotiations.
14. Limitation of Liability.
Each party’s sole remedy and the other party’s sole obligation shall be governed by this Agreement.
14.1 Maximum Liability.
EXCEPT IN THE CASE OF NTT’s DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.1, AND EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.2, IN NO EVENT SHALL EITHER PARTY’S LIABILITY TO THE OTHER EXCEED THE GREATER OF: (A) THE AGGREGATE AMOUNTS PAID OR OWED BY PARTNER TO NTT UNDER THIS AGREEMENT WITH RESPECT TO THE SERVICE OR CONSULTING DELIVERABLE THAT IS SUBJECT OF THE CLAIM IN THE 12 MONTHS PRECEDING THE FIRST OCCURRENCE OF THE EVENTS GIVING RISE TO ANY CLAIM, OR (B) $250,000.
14.2 EXCEPT IN THE CASE OF EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13 IN NO EVENT SHALL A PARTY BE LIABLE TO THE OTHER PARTY FOR ANY SPECIAL, INDIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING FROM BREACH OF WARRANTY, BREACH OF CONTRACT, NEGLIGENCE, OR ANY OTHER LEGAL THEORY, WHETHER IN TORT OR CONTRACT, EVEN IF SUCH PARTY IS AWARE OF THE LIKELIHOOD OF SUCH DAMAGES OCCURRING. NTT SHALL NOT BE RESPONSIBLE FOR ANY DAMAGES OR EXPENSES RESULTING FROM ALTERATION OR UNAUTHORIZED USE OF THE SERVICE, OR FROM THE UNINTENDED AND UNFORESEEN RESULTS OBTAINED BY PARTNER OR ANY CUSTOMERS RESULTING FROM SUCH USE.
15. Legal Compliance.
15.1 Export. The parties shall comply with all applicable United States and foreign laws and regulations, including without limitation: (i) all applicable laws and regulations relating to the advertising, packaging, sale, and distribution of the Service and Consulting deliverables, (ii) all United States export laws and regulations governing the export or re-export of all Services/Consulting and any products or services provided in connection with the Services/Consulting, including without limitation the U.S. Export Administration Regulations, the International Traffic in Arms Regulations, and any regulations administered by the Department of the Treasury’s Office of Foreign Assets Control, and (iii) all applicable laws and regulations of countries other than the United States that govern the importation, use, or re-export of the Services/Consulting. Partner further agrees to comply with any reasonable conditions that NTT notifies Partner are contained in any applicable export licenses pertaining to the Services/Consulting. Partner shall comply with any reporting requirements that may apply to the export or re-export of the Services/Consulting deliverables and shall provide to NTT and the appropriate governmental authority any periodic reports containing such information as may be required under applicable law. Partner further agrees to pay any taxes or tariffs that may apply to the export, or re-export of the Services/Consulting.
15.2 Sanctions. Partner warrants that (i) neither it or its Affiliates are subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”), and (ii) if at any time it or an Affiliate become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under this Agreement, or the continuing performance of this Agreement exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate this Agreement.
15.3 Applicable Laws. The parties shall at all times conduct their efforts hereunder with the highest commercial standards and in strict accordance with all applicable laws, rules, directives and regulations (“Laws”). Each party shall be responsible for current and ongoing familiarity and compliance with all Laws applicable to the importation, distribution, marketing, sale, operation, use or support of the Services and Consulting, and the privacy and protection of personal data.
15.4 Anti-bribery. Each party will maintain adequate policies and procedures designed to ensure that its officers, directors, employees and contractors comply, at all times, with all relevant and applicable laws concerning anti-bribery and corruption.
15.5 Foreign Corrupt Practices Act. In conformity with the United States Foreign Corrupt Practices Act and with NTTs policies regarding foreign business practices, Partner and its employees and agents shall not directly or indirectly make and offer, payment, promise to pay, or authorize payment, or offer a gift, promise to give, or authorize the giving of anything of value for the purpose of influencing an act or decision of an official of any government (including a decision not to act) or inducing such a person to use his or her influence to affect any such governmental act or decision in order to assist Partner and/or NTT in obtaining, retaining or directing any such business.
16. Personal Information.
Subject to compliance with applicable laws, including data protection laws, each party reserves the rights to transfer (both domestically and cross-border) and disclose information, including relevant confidential information and, as applicable, personal data of the other party’s personnel to the receiving party’s (and its affiliates’) directors, officers, employees, contractors, professional advisors, and third-party service providers, solely as needed to support or facilitate the performance and administration of the Agreement by the receiving party, provided that such information will be disclosed a) on a need-to-know basis only (based on the receiving party’s business operations); and b) subject to appropriate obligations of confidentiality and/or personal data transfer arrangements with such parties, as applicable.
17. Termination.
17.1 Term. The term of this Agreement shall commence as of the Effective Date of this Agreement and continue until terminated by either party as provided herein.
17.2 Termination Without Cause. Upon ninety (90) days prior written notice and payment of any unpaid amounts owed by the terminating party, either party may terminate this Agreement at any time without cause to the other party.
17.3 Termination With Cause. Either party may terminate this Agreement upon 30 days written notice for a material breach of this Agreement if such breach is not cured within such 30-day period.
17.4 Rights Upon Termination. Upon any termination of this Agreement: (i) Partner shall remit all a) accrued but unpaid amounts due NTT and b) the unamortized portion of any fees prepaid by clients for Services or Consulting less the agreed Partner discounts (Samurai MDR subscription discounts (RRP), Services discounts, Additional subscription discounts and possible other agreed discounts),, (ii) Partner is no longer authorized to conduct any activities under this Agreement; (iv) Partner shall immediately cease using the Trademarks of NTT and discontinue all representations that it has a relationship with NTT; and (iv) Partner shall promptly return to NTT any tangible sales literature, brochures, technical information, price lists, samples, evaluation units, and other materials received from NTT or if intangible, destroy such items in a secure manner, except to the extent such materials are reasonably required for delivery of Services or provisions of Consulting ordered prior to termination as directed by NTT.
17.5 Survival. The Sections entitled Ownership, Restrictions, Ownership of Trademarks, Confidentiality, Warranty Disclaimer, Indemnification, Limitation of Liability, Rights Upon Termination, Survival and Miscellaneous shall survive expiration or termination of this Agreement for any reason.
18. Order of Precedence.
In the event of a conflict between the terms of the MPA, and an Order/SOW (including any exhibits or attachments thereto), the terms of the Order/SOW shall govern but only as regards such Order/SOW.
19. Miscellaneous.
19.1 Assignment. Partner may not assign this Agreement without the prior written approval of NTT. For the purposes of this section, a change in the persons or entities that control 50% or more of the equity securities or voting interest of Partner shall be considered an assignment of Partner’s rights. NTT may assign this Agreement at any time and may delegate aspects of its performance under this Agreement to any of its Affiliates.
19.2 Audit Rights. Once per calendar year, upon reasonable notice and during Partner’s normal business hours, NTT shall have the right to audit, through an independent third party auditor selected by NTT and approved by Partner (which approval will not be unreasonably withheld or delayed) Partner’s books of account and business records as necessary to verify Partner’s compliance with this Agreement, including but not limited to, compliance with the requirements of Sections 2.1, 2.4 and 2.5 and the accuracy of the amounts paid pursuant to this Agreement. The auditor may disclose to NTT Security Holdings, with a written copy to Partner, only whether the amounts paid are correct or incorrect and the amount of any discrepancy. No other information may be provided to NTT Security Holdings. If the auditor identifies a discrepancy, the appropriate party shall pay to the other party the amount of the discrepancy (plus interest) within thirty (30) days of the date Partner receives the auditor’s written report.
19.3 Notices. All notices given pursuant to this Agreement shall be in writing and effective: (i) upon receipt if hand delivered; (ii) on the next day after being sent by email if followed by the methods in subsections (iii) or (iv); (iii) on the third business day after being sent prepaid by certified or registered mail; or (iv) on the second business day after being sent prepaid by commercial express courier. Notices to NTT shall be sent to Råsundavägen 12, 169 67 Solna, Sweden, Attention: COO, with a copy to legal@security.ntt. Notices to Partner will be sent to the address first set forth above, attention Chief Executive Officer for Partner, with a “copy to:” _______________.
19.4 Waiver. The waiver by either party of a breach of any provision contained herein shall be in writing and shall in no way be construed as a waiver of any succeeding breach of such provision or the waiver of the provision itself.
19.5 Severability. In the event that any provision of this Agreement shall be unenforceable or invalid under any applicable law or be so held by applicable court decision, such unenforceability or invalidity shall not render this Agreement unenforceable or invalid as a whole. In such event, such provision shall be changed and interpreted so as to best accomplish the objectives of such provision within the limits of applicable law or applicable court decisions, or if necessary to maintain the validity of the remaining terms, removed from the Agreement.
19.6 Controlling Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules.. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
19.7 Dispute Resolution and Attorneys’ Fees. Except for claims for breach of confidentiality obligations, the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
19.8 No Agency. The use of the term “Partner” is for convenience and does not reflect an intention of the parties to form a legal partnership. The parties are independent contractors under this Agreement, and nothing contained herein shall be construed as creating any agency, partnership, employment, or other form of joint enterprise between the parties and nothing contained in this Agreement (including use of the term “Partner”) will be construed to (i) give either Party the power to direct and control the day-to-day activities of the other, (ii) create a principal-agent or employer-employee relationship, or (iii) give either Party the authority to bind the other Party to any contract with a third party.
19.9 Force Majeure. NTT, NTT agents and Affiliates, Partner and Partner’s agents shall not be liable for any delay or failure to perform for any cause beyond their reasonable control, except for the payment of money, to the extent that performance is rendered impossible by strike, fire, flood, wars, sabotage, civil unrest, governmental acts, or any other reason where failure to perform is beyond the reasonable control of and is not caused by the negligence of the nonperforming party.
19.10 Counterparts and Electronic Copies. This Agreement may be e-signed. Further, if this Agreement is signed in two counterparts, the two counterparts together shall form a single agreement as if both parties had executed the same document. Electronic copies (e.g., .pdf, .tif) and facsimile signature pages shall be binding as if original.
19.11 Entire Agreement; Order of Precedence. This Agreement completely and exclusively states the agreement of the parties regarding its subject matter. This Agreement supersedes all prior proposals, agreements or other communications between the parties, oral or written, regarding such subject matter. This Agreement shall not be modified except by a subsequently dated written amendment or appendix signed on behalf of NTT and Partner by their duly authorized representatives. Any provision of Partner’s purchase order or other document purporting to vary or add to the provisions hereof shall be void.
5.4.4.3 - Master Partner Agreement (v3.0 2025-06-11)
This document has been superseded. For the latest version please click HERE.
MASTER PARTNER TERMS AND CONDITIONS
1.Definitions.
1.1 “Affiliate” means any majority-owned subsidiary or other entity which a party controls or is controlled by, or with which it is under common control with a party.
1.2 “Consulting” means the consulting services provided by NTT as provided for under the terms of the applicable Service Descriptions. By way of example, Consulting may include, incident response and investigation, compromise assessments, forensic services related to cyber security adversaries, tabletop exercises and penetration tests related to cyber security and typically provided on a time and material basis and sometimes sold as a retainer.
1.3 “Customer(s)” means the current or potential customers of Partner for the applicable NTT Samurai Services or Consulting excluding any entity or person deemed in NTT reasonable discretion as a competitor of NTT; provided, when used in the Terms of Service as referenced in Sections 1.10, 2.1, 2.4 and 2.6 of this Agreement, “Customer” shall mean Partner.
1.4 “Evidence Data" means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
1.5 “Intellectual Property Rights” means copyrights (including, without limitation, the exclusive right to use, reproduce, modify, distribute, publicly display, and publicly perform the copyrighted work), trademark rights (including rights in, without limitation, trade names, trademarks, service marks, and trade dress), patent rights (including, without limitation, (i) all rights worldwide in patent applications, any patents issuing therefrom, and all provisional rights with respect to patent applications, (ii) all rights worldwide in any improvements, substitutions, divisionals, patents of addition, continuations, continuations-in-part, reissues, renewals, registrations, confirmations, re-examinations, extensions, supplementary protection certificates, term extensions (under applicable patent law or regulation or other law or regulation), and certificates of invention of any patents or patent applications, and (iii) all rights worldwide to exploit any of the foregoing), know-how, trade secrets, moral rights, right of publicity, authors’ rights, contract and licensing rights, all other intellectual property rights as may exist now and/or hereafter come into existence, and all renewals and extensions thereof, regardless of whether such rights arise under the law of the Territory or any other state, country, region, or jurisdiction.
1.6 “NTT Content” means NTTs proprietary data that is contained in or made available as part of Services and Consulting.
1.7 “Samurai Services” consists of NTT MDR offerings for security operations management which are listed and further described in the relevant Service Descriptions.
1.8 “Services” means Samurai Services and Consulting. The Service Descriptions for the Services can be found here https://docs.mdr.security.ntt/docs/reference/legal/service_descriptions/
1.9 “Trademarks” means the words, names, symbols, designs, or any combination thereof, used in commerce to identify and distinguish the products, services, and company, of a party from those of others and to indicate the source of such consulting and services.
1.10 “Terms of Service” or “ToS” means the current standard terms, conditions, and legal notices, applicable to the Samurai Services found here https://docs.mdr.security.ntt/docs/reference/legal/, including any product specific terms that are included in valid quotes issued by NTT and related to the Samurai Services.
1.11 “Territory” means the jurisdiction(s) listed in the Cover sheet.
1.12 “Partner Tier” means the type of obligations to, and benefits and support the Partner will receive from, NTT as defined in the Partner Program Guide
1.13 “End User Agreement” means the same as “Terms of Service” as defined in clause 1.10 above.
2. Appointment and Restrictions.
2.1 Nonexclusive Appointment. Provided that Partner complies at all times with the terms and conditions of this Agreement, NTT appoints Partner and Partner accepts appointment as a nonexclusive Partner with non-transferable, limited right to market and promote the Services to Customers within the Territory provided, Partner shall expressly accept and agree to the Terms of Service with NTT prior to accessing the Services. The applicable Samurai Services and Consulting to which this appointment applies will be specified in the applicable Service Description(s). Partner agrees that nothing in this Agreement shall be construed to preclude NTT from directly or indirectly marketing, distributing, selling, or servicing any Services or Consulting to or for any third party in any location, including without limitation, other partners, resellers, distributors, managed service providers, and end-users. The rights and licenses granted to Partner under this Agreement are personal to Partner and Partner may not transfer or sublicense the appointment set forth in this Agreement.
2.2 Ownership. Except for the limited license(s) expressly granted to Partner in this Agreement, all right, title and interest in and to the Services, Consulting, NTT Content, including the concepts and technology inherent in the Services, NTT Content and deliverables, all Intellectual Property Rights related thereto, shall at all times be and remain, relative to Partner, the sole and exclusive property of NTT. No other licenses, immunity or rights, express or implied are granted by NTT, by implication, estoppel, or otherwise.
2.3. Restrictions. Partner shall, by all appropriate means, prevent unauthorized disclosure, publication, display or use of the Services, Consulting and NTT Content. Partner shall not, and shall not encourage or authorize any third party to, modify or reverse engineer any Services or the technology related thereto, or attempt to gain unauthorized access to the Services or the NTT Content. Partner shall not remove, alter, cover or obfuscate any end-user agreement, privacy notice, copyright notices or other proprietary legends placed or embedded by NTT on or in the Services documentation, NTT Content, deliverables or literature related to any of the foregoing. Partner shall not affix or place any labels or markings on the Services, Consulting output, Service deliverables, or literature related to the foregoing, that might be interpreted as a claim of ownership by Partner or any third party in the foregoing.** Without NTT’s prior written consent (an email from the Chief Operating Officer shall suffice), Partner shall not, nor have a third party, (i) perform a competitive analysis on the Services or Consulting, or (ii) publish a review or the results of any internal evaluation of the Services or Consulting.
2.4 Terms of Service. With respect to each accepted quote for Services, Partner shall expressly accept and agree to be bound by the Terms of Service with NTT. Partner shall not be granted, and shall not grant to Customers, any access, use or other rights to the Services, unless Partner has accepted and agreed to the Terms of Service. Partner will promptly report to NTT any breach, or suspected breach, of the Terms of Service of which it becomes aware. NTT reserves the right to refuse to issue a quote, accept an order, or make the Services available to any Customer; provided that NTT provides to Partner a written notice of its objection to such Customer.
2.5 Changes to ToS. Partner acknowledges that NTT may update the Terms of Services from time to time as set forth in the Terms of Service.
2.6 Governing Terms and Conditions. Partner acknowledges and agree that, A) as to Partner, NTT’s obligations to Partner shall be as stated in this Agreement and the Terms of Service, and B) as to Customers, i) Partner shall be solely liable to Customers.
2.7 Partner Tier. Partner agrees to abide by the obligations of the Tier they hold. Partner further agrees that should they cease to meet such obligations NTT may, at it’s sole discretion, reduce Partner’s tier or remove Partner’s status as a Partner.
2.8 Partner Conduct. Partner shall: (i) conduct business in a manner that reflects favorably at all times on the Services, Consulting, goodwill and reputation of NTT; (ii) avoid deceptive, misleading or unethical practices that are or might be detrimental to NTT; (iii) refrain from making any false or misleading representations or warranties with regard to NTT, the Services or Consulting; and (iv) comply with all applicable laws, rules, ordinances, decrees and regulations applicable to Partner’s activities under this Agreement, including without limitation, any applicable privacy laws and the Foreign Corrupt Practices Act, export laws and sanctions regulations or any similar legislation. Partner has reviewed and understands NTT’s Privacy Notice located at https://docs.mdr.security.ntt/docs/reference/legal/privacy_policy/. Partner shall not, directly or indirectly, through action or inaction, cause NTT to be in violation of its Privacy Notice or applicable laws.
2.9 Affiliate Appointment. An Affiliate of Partner may be authorized by NTTSH to resell Services pursuant to and in accordance with the terms and conditions of this Agreement, provided such Affiliate is approved by NTTSH and executes and delivers an agreement in form and substance required by NTTSH whereby Affiliate adopts and agrees to be bound by this Agreement (an “Adoption Agreement”). Any such Adoption Agreement shall constitute an individual contractual relationship between the respective Affiliate and NTTSH and will govern any purchase order executed or issued by such Affiliate. Each Affiliate shall only be liable under the Adoption Agreement it has executed, and NTTSH shall be liable only to the Affiliate executing such Adoption Agreement. In no event shall either NTTSH or Partner have recourse or be liable to the other or another Affiliate with regard to any acts or omissions, obligations, duties, or claims under an Adoption Agreement or any local purchase order entered into by the Affiliates and NTTSH.
3. Services. During the term of the MPA and subject to the terms and conditions therein and herein, NTT agrees to provide certain: (i) Samurai Services, and/or (ii) Consulting services purchased by Partner in accordance with the terms of this MPA. The Services purchased are specified in a quote delivered by NTT and accepted by Partner without alteration (“Order”) or statement of work (“SOW”) executed (or, if online, accepted pursuant to an online order process) by the parties which references this MPA. A detailed description of the Services being purchased is provided in the service description and for such Services attached to the Order (or linked to if the Partner is purchasing online) and incorporated therein by reference. All Orders (whether signed or accepted pursuant to an online order process) and all SOWs are subject to the terms and conditions of this MPA and will include the following: (i) the particular Services to be performed, including, if applicable, the applicable Specification Document; (i) the subscription term of the Services; (iii) the compensation and billing method for the Services; and (iv) any other applicable information agreed to by the parties.
4. Go To Market and Use of Trademarks.
4.1 Go To Market. Subject to the terms of this Section 4, each party will have the right to refer to the fact that Partner is in a collaborative relationship with NTT on its website and in marketing collateral. Otherwise, neither party will make any public statement or issue any press release with respect to this relationship without the prior written consent of the other party.
4.2 Trademark Use. Each party (the “Trademark Party”) grants the other party a worldwide, non-exclusive, non-transferable royalty free limited license (with no right of sublicense) during the term of this Agreement to use the Trademark Party’s Trademarks solely for the purpose of carrying out the terms of the Go To Market Plan and as otherwise contemplated by this Agreement, including but not limited to, the promotion of the Services and Consulting, the parties’ joint efforts and channel programs; provided, that, such Trademarks are used solely in accordance with the Trademark Party’s specifications as to style, color, and typeface, as such specifications may be modified by such party from time to time and communicated to the other party. Partner agrees not to attach any other trademarks, logos or trade designations to the Services, nor to remove or modify any of NTT’s Trademarks or proprietary notices affixed to the Services, Service deliverables or documentation. Partner shall not affix any NTT Trademarks to services other than the genuine Services. Upon notice from the Trademark Party of its objection to any improper or incorrect use of the Trademark Party’s Trademarks, the other party shall correct or stop such usage as soon as reasonably practicable.
4.3 Ownership of Trademarks. Each Trademark Party claims ownership of all right, title, and interest in and to its Trademarks, together with any new or revised trademarks, trade names, and logos that such Trademark Party may adopt to identify it or any of its products or services. Neither party shall claim any rights in the other party’s Trademarks or take any action that threatens or challenges the Trademark Party’s proprietary rights therein. All use by a party of the Trademark Party’s Trademarks and all goodwill associated therewith shall inure exclusively to the benefit of the Trademark Party and its Affiliates. Partner is prohibited from using or registering any of NTT’s Trademarks or domain names, including without limitation any terms containing the terms “Samurai” as part of Partner’s company name, service name, trade names or domain names. NTT does not authorize Partner’s use of any of the NTT Trademarks to promote or use for search engine ranking or ad word purchase or as part of a trade name, business name or Internet domain name in any manner that could be detrimental to the interests of NTT. If Partner registers or otherwise obtains rights to marks (as trademarks, service marks, URLs, company names or otherwise) in violation of this Agreement, Partner will, at its own expense, transfer and assign such rights to NTT, and execute all documents reasonably requested by NTT to facilitate such assignment or transfer.
5. Samurai Service Fees. NTT’s’ fees for the Samurai Services are set forth on the Order. The Samurai Services ordered will commence on the date set forth in the Order (the “Commencement Date”), and NTT shall invoice Partner for Samurai Services on the Commencement Date and thereafter in advance on the renewal date. If there is no date in the Order, the date on which the Quote was accepted shall be the Commencement Date.
6. Consulting Service Fees. NTT’s fees and billing milestones for the Consulting Services are set forth on the applicable Order or Statement of Work (“SOW”) (as applicable).
7. Invoice and Payment. NTT will invoice Partner in accordance with the billing terms set forth and detailed on the applicable Order or SOW. All charges, fees, payments and amounts hereunder will be in currency designated in the applicable Order or SOW, and (ii) all undisputed amounts due hereunder are payable within thirty (30) days from the date of the invoice, which shall be submitted to Partner electronically (the “Invoice Due Date”).
8. Disputes and Nonpayment. Partner shall have the right to reasonably, and in good faith, dispute any invoice or any portion of any invoice claimed by NTT as due and payable provided that, prior to the Invoice Due Date, Partner (i) timely pays any undisputed portion of the amount due and payable, and (ii) provides NTT with written notice specifying the disputed amount and the basis for the dispute in reasonable detail. Except for amounts that are disputed in good faith by Partner in accordance with this Section 8, NTT reserves the right to charge Partner a late fee of one and a half percent (1.5%) per month or the maximum rate permitted by law, whichever is less, for invoices not paid on or before the Invoice Due Date. In addition, NTT, without waiving any other rights or remedies to which it may be entitled, shall have the right, upon prior written notice to Partner, to suspend the Services until such payment is received.
9. Taxes. Partner shall be responsible for the payment of all taxes and fees assessed or imposed on the Services provided or the amounts charged under the Order/SOW in any country or territory in which the Partner receives the benefit of the Services, including any sales, use, excise, value-added, or comparable taxes, but excluding taxes: (i) for which the Partner has provided a valid resale or exemption certificate, or (ii) imposed on NTT’ income or arising from the employment relationship between NTT and its employees. Should any payments become subject to withholding tax, the Partner will deduct these taxes from the amount owed and pay the taxes to the appropriate tax authority in accordance with applicable tax laws. Partner will promptly provide NTT with receipts or documents evidencing these tax payments. NTT shall not be liable for any withholding tax, penalty or interest due as a result of Partner’s failure to withhold any applicable tax.
10. Change Control. “Change” means any change to the scope of engagement that (i) would modify NTT’s obligations in relation to delivery of the Services, or (ii) would alter the cost to Partner for the Services, or (iii) is agreed by Partner and NTT in writing to be a Change. From time to time during the term of the Services, Partner or NTT may propose Changes to the scope of the engagement. Any Change to the applicable Order/SOW shall be implemented by request for, issuance of, and acceptance of a quote. For the avoidance of doubt, change described in this Section 10 does not apply to the composition of the Samurai Service as defined in the Service Description.
11.Confidentiality.
11.1 Definitions. In connection with this Agreement, each party (“Recipient”) may be exposed to or acquire Confidential Information of the other party (“Discloser”) or third parties to whom Discloser has a duty of confidentiality. “Confidential Information” means non-public information in any form and regardless of the method of acquisition that the Discloser designates as confidential to Recipient or which, due to the nature of such information and/or under the circumstances surrounding disclosure ought to be treated as confidential by the Recipient. Confidential Information shall not include information that is: (i) in or becomes part of the public domain (other than by disclosure by Recipient in violation of this Agreement); (ii) previously known to Recipient (which must be demonstrable) without an obligation of confidentiality; (iii) independently developed by Recipient without use of Discloser’s Confidential Information; (iv) rightfully obtained by Recipient from third parties without an obligation of confidentiality, or (v) Evidence Data.
11.2 Restrictions on Use. Recipient shall hold Discloser’s Confidential Information in strict confidence and shall not disclose any such Confidential Information to any third party, other than to its employees, agents and consultants, including without limitation, counsel, accountants and advisors (collectively, “Representatives”) and its Affiliates and their Representatives who need to know such information and who are bound by restrictions regarding disclosure and use of such information comparable to and no less restrictive than those set forth herein. Recipient shall not use Discloser’s Confidential Information for any purpose other than to carry out the terms of this Agreement and further the parties’ business relationship. Recipient shall take the same degree of care that it uses to protect its own confidential information of similar nature and importance (but in no event less than reasonable care) to protect the confidentiality and avoid the unauthorized use, disclosure, publication or dissemination of the Discloser’s Confidential Information. Recipient shall promptly notify Discloser of any breach of this Agreement that it becomes aware, and in any event, shall be responsible for any breach of this Agreement by any of its Affiliates, Representatives or Affiliates’ Representatives.
11.3 Exceptions. Recipient may disclose Discloser’s Confidential Information: (i) to the extent required by applicable law or regulation, or (ii) pursuant to a subpoena or order of a court or regulatory, self-regulatory or legislative body of competent jurisdiction, or (iii) in connection with any regulatory report, audit or inquiry, or (iv) where requested by a regulator with jurisdiction over Recipient. In the event of such a requirement or request, Recipient shall to the extent permissible by law give the Discloser prompt written notice of such requirement or request prior to such disclosure and reasonable assistance (at Discloser’s expense) in obtaining an order protecting the information from public disclosure. NTT and Partner agree that the terms and conditions of this Agreement as it relates to the other party shall be treated as Confidential Information and shall not be disclosed to any third party except as otherwise provided in this Section 11 (Confidentiality) and (i) in connection with the enforcement of this Agreement or rights under this Agreement; or (ii) in confidence, in connection with an actual or proposed merger, acquisition or similar transaction.
11.4 Return or Destruction. Upon Discloser’s written request, Recipient shall use commercially reasonable efforts to either return or destroy the Confidential Information and any copies or extracts thereof. However, Recipient, its Affiliates and their Representatives may retain any Confidential Information that: (i) they are required to keep for compliance purposes under a document retention policy or as required by applicable law, professional standards, a court or regulatory agency; or (ii) have been created electronically pursuant to automatic or ordinary course archiving, back-up, security or disaster recovery systems or procedures; provided, however, that any such retained information shall remain subject to this Agreement. If Recipient elects to destroy Discloser’s Confidential Information (subject to any retention rights provided in this Agreement), Discloser may request that Recipient provide it with written confirmation of destruction in compliance with this provision.
11.6 Equitable Relief. Each party acknowledges that a breach of this Section 11 (Confidentiality) shall cause the other party irreparable injury and damage. Therefore, each party agrees that those breaches may be stopped through injunctive proceedings in addition to any other rights and remedies which may be available to the injured party at law or in equity without the posting of a bond.
11.6 NTT Development; Communications. It is expressly understood, acknowledged and agreed that Partner may, regardless of whether or not formally requested, provide to NTT suggestions, comments and feedback regarding the Services or Consulting, including but not limited to usability, bug reports and test results, with respect to the foregoing (collectively, “Feedback”). Partner grants NTT, under all of its intellectual property and proprietary rights, the following worldwide, non-exclusive, perpetual, irrevocable, royalty free, fully paid up rights without any attribution of any kind: (i) to make, use, copy, modify, sell, distribute, sub-license, and create derivative works of, the Feedback as part of any NTT Service or Consulting or related technology, specification or other documentation; (ii) to publicly perform or display, import, broadcast, transmit, distribute, license, offer to sell, and sell, rent, lease or lend copies of the Feedback (and derivative works thereof) as part of any NTT’s Service or Consulting or related technology, specification or other documentation; (iii) solely with respect to your copyright and trade secret rights, to sublicense to third parties the foregoing rights, including the right to sublicense to further third parties; and (iv) to sublicense to third parties any claims of any patents owned or licensable by Partner that are necessarily infringed by a third party product, technology or service that uses, interfaces, interoperates or communicates with the Feedback or portion thereof incorporated into an NTT Service or Consulting or related technology, specification or other documentation. Further, Partner warrants that its Feedback is not subject to any license terms that would purport to require NTT to comply with any additional obligations with respect to any NTT Service or Consulting or related technology, specification or other documentation that incorporate any Feedback.
12.Representations and Warranties.
12.1 Each party represents and warrants that it has full power and authority to execute this Agreement and to take all actions required by, and to perform the agreements contained in, this Agreement, and that each party’s obligations under this Agreement do not conflict with its obligations under any other agreement to which it is a party.
12.2 WARRANTY DISCLAIMER. EXCEPT FOR ANY LIMITED EXPRESS WARRANTIES MADE BY NTT FOR THE SERVICES AND/OR CONSULTING IN ITS END USER AGREEMENT(S) (WHICH SHALL BE APPLICABLE ONLY IF PARTNER OR CUSTOMER IS AN END USER OF THE APPLICABLE SERVICE OR CONSULTING UNDER SUCH AN AGREEMENT), NTT MAKES NO OTHER WARRANTIES RELATING TO THE SERVICES OR CONSULTING, EXPRESS, IMPLIED OR STATUTORY (EXCEPT FOR THOSE PRESCRIBED BY LAW WHICH CANNOT BE EXCLUDED), INCLUDING WITHOUT LIMITATION ANY WARRANTIES OF NON-INFRINGEMENT OF THIRD PARTY RIGHTS, FITNESS FOR A PARTICULAR PURPOSE, OR MERCHANTABILITY. PARTNER ACKNOWLEDGES, UNDERSTANDS AND AGREES THAT NTT DOES NOT GUARANTEE OR WARRANT THAT USE OF THE SERVICES OR CONSULTING WILL FIND, LOCATE OR DISCOVER ALL SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND WILL NOT HOLD NTT RESPONSIBLE THEREFOR. PARTNER AGREES NOT TO REPRESENT TO CUSTOMER OR ANY THIRD PARTY THAT NTT HAS PROVIDED SUCH GUARANTEE OR WARRANTY. NTT SERVICES ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENTS REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NTT SERVICES ARE NOT FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY OR PROPERTY DAMAGE.
12.3 No individual is authorized by NTT to make any warranty or representation concerning the performance of the Services or Consulting. Partner shall make no warranty, express or implied, on behalf of NTT.
13. Indemnification.
13.1 Infringement Indemnity. NTT will defend, at its own expense, a third-party claim, suit or proceeding brought against Partner insofar as it is based on a claim that a Service or a Consulting deliverable when used by Partner in accordance with the terms of this Agreement, constitutes an infringement of a patent or copyright valid within the Territory. NTT shall pay all damages, costs and expenses finally awarded to third parties as a result of a final judgment against Partner or settlement of such claim negotiated by NTT, but shall not be responsible for any compromise made without its consent. To qualify for such defense and payment, the Partner must: (i) give NTT prompt written notice of any such claim, and (ii) allow NTT to control, and fully cooperate with NTT in, the defense and all related settlement negotiations. Upon notice of an alleged infringement, or if, in NTT’s opinion, such a claim is likely, NTT shall have the right, at its option, to obtain the right to continue the distribution of Services, substitute other products or services with similar operating capabilities and/or performance, or modify the Service or Consulting deliverable so that it is no longer infringing or subject to a third party claim. In the event that none of the above options are reasonably available in NTT’s sole discretion, NTT may terminate this Agreement’ and all accompanying subscription licenses. In the event of such termination, NTT shall, without limiting its obligation to defend and indemnify Partner, refund to Partner: (i) the fees paid for Services subscriptions prorated for the remainder of any pre-paid subscription term unused by the Customer, or (ii) the portion of the fees attributable to the Service deliverable, as applicable. This Section 13 (Infringement Indemnity) states NTT’s entire liability under this Agreement for all claims of intellectual property infringement. NTT shall not be responsible for any claim of infringement that arises from (i) modifications to a Service or Consulting deliverable not made by NTT, (ii) use of a Service or Consulting deliverable in a manner or in combination with products or services not provided by NTT to the extent such claim would not have occurred except for such modifications, use or combination; (iii) use of other than the latest available version of the Services or Consulting deliverable made available to Partner or the Customer; or (iv) any use of the Services or Consulting deliverable not in accordance with this Agreement or the applicable end user terms, documentation or specifications.
13.2 Indemnity. NTT and Partner (each an “Indemnitor”) shall defend and indemnify the other party and its Affiliates, and their officers, directors, employees, and agents (collectively, “Indemnitees,” respectively, for each of NTT and Partner), from any third party claims and the associated costs, damages or settlement (inclusive of attorney’s fees and court costs) that an Indemnitee may incur as a result of: (i) an Indemnitor’s breach of this Agreement or any agreement with the Customer; (ii) an Indemnitor making a representation, warranty, or other statement to a Customer on behalf of the other party that is not specifically authorized in writing; or (iii) an Indemnitor’s or its representative’s gross negligence, fraud or willful misconduct. To qualify for such defense and payment, the Indemnitee must: (i) give the Indemnitor prompt written notice of any such claim, and (ii) allow Indemnitor to control, and fully cooperate with Indemnitor in, the defense and all related settlement negotiations.
14.Limitation of Liability. Each party’s sole remedy and the other party’s sole obligation shall be governed by this Agreement.
14.1.Maximum Liability.
EXCEPT IN THE CASE OF NTT’s DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.1, AND EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13.2, IN NO EVENT SHALL EITHER PARTY’S LIABILITY TO THE OTHER EXCEED THE GREATER OF: (A) THE AGGREGATE AMOUNTS PAID OR OWED BY PARTNER TO NTT UNDER THIS AGREEMENT WITH RESPECT TO THE SERVICE OR CONSULTING DELIVERABLE THAT IS SUBJECT OF THE CLAIM IN THE 12 MONTHS PRECEDING THE FIRST OCCURRENCE OF THE EVENTS GIVING RISE TO ANY CLAIM, OR (B) $250,000.
14.2 EXCEPT IN THE CASE OF EACH PARTY’S DEFENSE AND INDEMNIFICATION OBLIGATIONS UNDER SECTION 13 IN NO EVENT SHALL A PARTY BE LIABLE TO THE OTHER PARTY FOR ANY SPECIAL, INDIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING FROM BREACH OF WARRANTY, BREACH OF CONTRACT, NEGLIGENCE, OR ANY OTHER LEGAL THEORY, WHETHER IN TORT OR CONTRACT, EVEN IF SUCH PARTY IS AWARE OF THE LIKELIHOOD OF SUCH DAMAGES OCCURRING. NTT SHALL NOT BE RESPONSIBLE FOR ANY DAMAGES OR EXPENSES RESULTING FROM ALTERATION OR UNAUTHORIZED USE OF THE SERVICE, OR FROM THE UNINTENDED AND UNFORESEEN RESULTS OBTAINED BY PARTNER OR ANY CUSTOMERS RESULTING FROM SUCH USE.
15.Legal Compliance.
15.1 Export. The parties shall comply with all applicable United States and foreign laws and regulations, including without limitation: (i) all applicable laws and regulations relating to the advertising, packaging, sale, and distribution of the Service and Consulting deliverables, (ii) all United States export laws and regulations governing the export or re-export of all Services/Consulting and any products or services provided in connection with the Services/Consulting, including without limitation the U.S. Export Administration Regulations, the International Traffic in Arms Regulations, and any regulations administered by the Department of the Treasury’s Office of Foreign Assets Control, and (iii) all applicable laws and regulations of countries other than the United States that govern the importation, use, or re-export of the Services/Consulting. Partner further agrees to comply with any reasonable conditions that NTT notifies Partner are contained in any applicable export licenses pertaining to the Services/Consulting. Partner shall comply with any reporting requirements that may apply to the export or re-export of the Services/Consulting deliverables and shall provide to NTT and the appropriate governmental authority any periodic reports containing such information as may be required under applicable law. Partner further agrees to pay any taxes or tariffs that may apply to the export, or re-export of the Services/Consulting.
15.2 Sanctions. Partner warrants that (i) neither it or its Affiliates are subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”), and (ii) if at any time it or an Affiliate become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under this Agreement, or the continuing performance of this Agreement exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate this Agreement.
15.3 Applicable Laws. The parties shall at all times conduct their efforts hereunder with the highest commercial standards and in strict accordance with all applicable laws, rules, directives and regulations (“Laws”). Each party shall be responsible for current and ongoing familiarity and compliance with all Laws applicable to the importation, distribution, marketing, sale, operation, use or support of the Services and Consulting, and the privacy and protection of personal data.
15.4 Anti-bribery. Each party will maintain adequate policies and procedures designed to ensure that its officers, directors, employees and contractors comply, at all times, with all relevant and applicable laws concerning anti-bribery and corruption.
15.5 Foreign Corrupt Practices Act. In conformity with the United States Foreign Corrupt Practices Act and with NTTs policies regarding foreign business practices, Partner and its employees and agents shall not directly or indirectly make and offer, payment, promise to pay, or authorize payment, or offer a gift, promise to give, or authorize the giving of anything of value for the purpose of influencing an act or decision of an official of any government (including a decision not to act) or inducing such a person to use his or her influence to affect any such governmental act or decision in order to assist Partner and/or NTT in obtaining, retaining or directing any such business.
16.Personal Information. Subject to compliance with applicable laws, including data protection laws, each party reserves the rights to transfer (both domestically and cross-border) and disclose information, including relevant confidential information and, as applicable, personal data of the other party’s personnel to the receiving party’s (and its affiliates’) directors, officers, employees, contractors, professional advisors, and third-party service providers, solely as needed to support or facilitate the performance and administration of the Agreement by the receiving party, provided that such information will be disclosed a) on a need-to-know basis only (based on the receiving party’s business operations); and b) subject to appropriate obligations of confidentiality and/or personal data transfer arrangements with such parties, as applicable.
17.Termination.
17.1 Term. The term of this Agreement shall commence as of the Effective Date of this Agreement and continue until terminated by either party as provided herein.
17.2 Termination Without Cause. Upon ninety (90) days prior written notice and payment of any unpaid amounts owed by the terminating party, either party may terminate this Agreement at any time without cause to the other party.
17.3 Termination With Cause. Either party may terminate this Agreement upon 30 days written notice for a material breach of this Agreement if such breach is not cured within such 30-day period.
17.4 Rights Upon Termination. Upon any termination of this Agreement: (i) Partner shall remit all a) accrued but unpaid amounts due NTT and b) the unamortized portion of any fees prepaid by clients for Services or Consulting less the agreed Partner discounts (Samurai MDR subscription discounts (RRP), Services discounts, Additional subscription discounts and possible other agreed discounts),, (ii) Partner is no longer authorized to conduct any activities under this Agreement; (iv) Partner shall immediately cease using the Trademarks of NTT and discontinue all representations that it has a relationship with NTT; and (iv) Partner shall promptly return to NTT any tangible sales literature, brochures, technical information, price lists, samples, evaluation units, and other materials received from NTT or if intangible, destroy such items in a secure manner, except to the extent such materials are reasonably required for delivery of Services or provisions of Consulting ordered prior to termination as directed by NTT.
17.5 Survival. The Sections entitled Ownership, Restrictions, Ownership of Trademarks, Confidentiality, Warranty Disclaimer, Indemnification, Limitation of Liability, Rights Upon Termination, Survival and Miscellaneous shall survive expiration or termination of this Agreement for any reason.
18.Order of Precedence. In the event of a conflict between the terms of the MPA, and an Order/SOW (including any exhibits or attachments thereto), the terms of the Order/SOW shall govern but only as regards such Order/SOW.
19. Miscellaneous.
19.1 Assignment. Partner may not assign this Agreement without the prior written approval of NTT. For the purposes of this section, a change in the persons or entities that control 50% or more of the equity securities or voting interest of Partner shall be considered an assignment of Partner’s rights. NTT may assign this Agreement at any time and may delegate aspects of its performance under this Agreement to any of its Affiliates.
19.2 Audit Rights. Once per calendar year, upon reasonable notice and during Partner’s normal business hours, NTT shall have the right to audit, through an independent third party auditor selected by NTT and approved by Partner (which approval will not be unreasonably withheld or delayed) Partner’s books of account and business records as necessary to verify Partner’s compliance with this Agreement, including but not limited to, compliance with the requirements of Sections 2.1, 2.4 and 2.5 and the accuracy of the amounts paid pursuant to this Agreement. The auditor may disclose to NTT Security Holdings, with a written copy to Partner, only whether the amounts paid are correct or incorrect and the amount of any discrepancy. No other information may be provided to NTT Security Holdings. If the auditor identifies a discrepancy, the appropriate party shall pay to the other party the amount of the discrepancy (plus interest) within thirty (30) days of the date Partner receives the auditor’s written report.
19.3 Notices. All notices given pursuant to this Agreement shall be in writing and effective: (i) upon receipt if hand delivered; (ii) on the next day after being sent by email if followed by the methods in subsections (iii) or (iv); (iii) on the third business day after being sent prepaid by certified or registered mail; or (iv) on the second business day after being sent prepaid by commercial express courier. Notices to NTT shall be sent to Råsundavägen 12, 169 67 Solna, Sweden, Attention: COO, with a copy to legal@security.ntt. Notices to Partner will be sent to the address first set forth above, attention Chief Executive Officer for Partner, with a “copy to:” _______________.
19.4 Waiver. The waiver by either party of a breach of any provision contained herein shall be in writing and shall in no way be construed as a waiver of any succeeding breach of such provision or the waiver of the provision itself.
19.5 Severability. In the event that any provision of this Agreement shall be unenforceable or invalid under any applicable law or be so held by applicable court decision, such unenforceability or invalidity shall not render this Agreement unenforceable or invalid as a whole. In such event, such provision shall be changed and interpreted so as to best accomplish the objectives of such provision within the limits of applicable law or applicable court decisions, or if necessary to maintain the validity of the remaining terms, removed from the Agreement.
19.6 Controlling Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules.. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
19.7 Dispute Resolution and Attorneys’ Fees. Except for claims for breach of confidentiality obligations, the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
19.8 No Agency. The use of the term “Partner” is for convenience and does not reflect an intention of the parties to form a legal partnership. The parties are independent contractors under this Agreement, and nothing contained herein shall be construed as creating any agency, partnership, employment, or other form of joint enterprise between the parties and nothing contained in this Agreement (including use of the term “Partner”) will be construed to (i) give either Party the power to direct and control the day-to-day activities of the other, (ii) create a principal-agent or employer-employee relationship, or (iii) give either Party the authority to bind the other Party to any contract with a third party.
19.9 Force Majeure. NTT, NTT agents and Affiliates, Partner and Partner’s agents shall not be liable for any delay or failure to perform for any cause beyond their reasonable control, except for the payment of money, to the extent that performance is rendered impossible by strike, fire, flood, wars, sabotage, civil unrest, governmental acts, or any other reason where failure to perform is beyond the reasonable control of and is not caused by the negligence of the nonperforming party.
19.10 Counterparts and Electronic Copies. This Agreement may be e-signed. Further, if this Agreement is signed in two counterparts, the two counterparts together shall form a single agreement as if both parties had executed the same document. Electronic copies (e.g., .pdf, .tif) and facsimile signature pages shall be binding as if original.
19.11 Entire Agreement; Order of Precedence. This Agreement completely and exclusively states the agreement of the parties regarding its subject matter. This Agreement supersedes all prior proposals, agreements or other communications between the parties, oral or written, regarding such subject matter. This Agreement shall not be modified except by a subsequently dated written amendment or appendix signed on behalf of NTT and Partner by their duly authorized representatives. Any provision of Partner’s purchase order or other document purporting to vary or add to the provisions hereof shall be void.
5.4.5 - NTT Software Terms of Use
5.4.5.1 - NTT Software Terms of Use (v1.0 2023-05-25)
This document has been superseded. For the latest version please click HERE.
Effective October 21, 2022
PLEASE READ CAREFULLY: YOU AND ANY COMPANY OR ENTITY THAT YOU ARE ACTING FOR (“YOU” OR “YOUR”) ACCEPTS THESE SOFTWARE TERMS OF USE (THE “SOFTWARE TERMS”) BY INSTALLING AND/OR USING THE SOFTWARE. YOU REPRESENT THAT YOU: 1. ARE LAWFULLY ABLE TO ENTER INTO THESE SOFTWARE TERMS, AND 2. HAVE FULL AUTHORITY TO BIND THE YOU TO THESE SOFTWARE TERMS. THESE SOFTWARE TERMS ARE A BINDING CONTRACT BETWEEN YOU AND NTT SECURITY HOLDINGS CORPORATION, A CORPORATION ORGANIZED AND EXISTING UNDER THE LAWS OF JAPAN (“NTT”), ON BEHALF OF ITSELF AND ANY OF ITS AFFILIATES PERFORMING HEREUNDER (COLLECTIVELY, “NTT”). IF YOU DO NOT HAVE THIS AUTHORITY, OR YOU DO NOT AGREE TO, OR CANNOT COMPLY WITH, ALL THE SOFTWARE TERMS, THEN YOU MAY NOT USE THE SOFTWARE. THESE SOFTWARE TERMS GOVERN YOUR USE OF THE SOFTWARE UNLESS YOU HAVE ANOTHER VALID AGREEMENT WITH NTT FOR THE USE OF THIS SOFTWARE.
Updating the Software Terms. NTT may revise and update these Software Terms from time to time in our sole discretion. Your continued use of the Software following the update of revised Software Terms means that you accept and agree to the changes. When accepted by you, the revised Software Terms automatically supersede the prior version. New Terms apply prospectively only.
Definitions.
“NTT Competitor” means a person or entity in the business of developing, distributing, or commercializing Internet security products or services substantially similar to or competitive with NTT’s products or services.
“Generated Data” shall mean the data generated by the Software, including but not limited to, correlative and/or contextual data, and/or detections. For the avoidance of doubt, Generated Data does not include Your Data. Any access to or use of Generated Data through the Software is expressly limited to your Internal Use.
“Documentation” means the Software end-user technical documentation.
“Endpoint” means any physical or virtual device, such as, a computer, server, laptop, desktop computer, mobile, cellular, container or virtual machine image.
“Evidence Data” means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
“Internal Use” means access or use solely for Software User’s own internal information security purposes. By way of example and not limitation, Internal Use does not include access or use: (i) for the benefit of any person or entity other than Software User, or (ii) in any event, for the development of any product or service. Internal Use is limited to access and use by Software User’s employees or your Third Party Providers for Software User’s benefit.
“Personal Data” means any information relating to an identified or identifiable person or other similar definition under the applicable data privacy laws; an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.
“Software” means the software accompanying these Software Terms, or NTT software that you or a Third Party Provider have installed or used on your Endpoints, including any updates thereto and/or related Documentation that may be made available from time to time by NTT. NTT software may commonly be referred to as “XDR” or “Samurai”.
“Third Party Provider” means any individual or entity (other than an NTT Competitor) that: (i) has access or use of the Software: (a) under these Software Terms solely on behalf of and for your Internal Use, or (b) under a separate valid agreement with NTT, (ii) has an agreement to provide you (or your Affiliates) services, and (iii) is subject to confidentiality obligations covering NTT’s Confidential Information.
“Your Data” means the data generated by your Endpoints and collected by the Software, but excluding Evidence Data. For the avoidance of doubt, Your Data does not include Generated Data.Your Account. You (and each user seeking access, use or receipt of the Software) will be asked to create a customer account. As part of the account creation process, you and each user be asked to provide a valid email address, create a password, and verify that they are a human being by providing a telephone number to which we’ll send a verification code to enter into a form. When registering for an account, you and each user must provide true, accurate, current and complete information about as requested during the account creation process. You and each user must keep that information true, accurate, current and complete after you create each account
License and Restrictions**.**
- License. Subject to these Software Terms, if you have obtained a valid evaluation license or subscription to the Software through NTT or a designated NTT partner or reseller, You may, solely for Software User’s own Internal Use and during the period of time such evaluation or subscription remains valid, install and run this Software up to the validly licensed quantity.
- Restrictions. In addition to any restrictions stated in the Software Terms, you agree that the rights set forth in 4.1 above do not include any rights to, and you shall not: (i) employ or authorize a NTT Competitor to use the Software or the Documentation, or to provide management, hosting, or support for Software; (ii) alter, publicly display, translate, create derivative works of or otherwise modify the Software; (iii) sublicense, distribute or otherwise transfer the Software to any third party; (iv) allow third parties to access or use the Software; (v) reverse engineer, decompile, disassemble or otherwise attempt to derive the source code for the Software (except to the extent that such prohibition is expressly precluded by applicable law), circumvent its functions, or attempt to gain unauthorized access to NTT’s hosted software or its related systems or networks; (vi) use the Software to circumvent the security of another party’s network/information, develop malware, unauthorized surreptitious surveillance, data modification, data exfiltration, data ransom or data destruction; (vii) remove or alter any notice of proprietary right appearing on the Software; (viii) conduct any stress tests, competitive benchmarking or analysis on, or publish any performance data of, the Software (provided, that this does not prevent you from comparing Software to other products for legitimate purchase evaluation decisions and Software User’s Internal Use); or (x) cause, encourage or assist any third party to do any of the foregoing. You agree to use the Software in accordance with laws, rules and regulations directly applicable to you and acknowledges that you are solely responsible for determining whether a particular use of the Software is compliant with such laws. NTT Competitors or any other party with interests or intentions adverse to NTT may not access, install or use the Software or Generated Data.
- Third Party Software. NTT uses certain third party software in its Software, including what is commonly referred to as open source software. Under some of these third party licenses, NTT is required to provide you with notice of the license terms and attribution to the third party. See the licensing terms and attributions for such third party software that NTT uses in NTT’s list of Third Party Software Licensing Terms.
- Ownership & Feedback. Software is made available for use and licensed, not sold. NTT owns and retains all right, title and interest (including all intellectual property rights) in and to the Software. Any feedback or suggestions that you provides to NTT regarding any NTT products or services is non-confidential and may be used by NTT for any purpose without acknowledgement or compensation; provided, You will not be identified publicly as the source of the feedback or suggestion.
Your Obligations and Third Party Providers.
- Your Obligations. You represents and warrants that: (i) it owns or has a right of use from a third party, and controls, directly or indirectly, all of the software, hardware and computer systems (collectively, “Systems”) where the Software will be installed, (ii) to the extent required under any federal, state, or local U.S. or non-US laws it has authorized NTT to access the Systems and process and transmit data through the Software and any other NTT offerings in accordance with these Software Terms and as necessary to provide the Software and other services, (iii) it has a lawful basis in having the Software operate on the Systems, and collect and process the Your Data and the Personal Data; (iv) that it is and will at all relevant times remain duly and effectively authorized to instruct NTT to carry out the services related to the Software, (v) it has made all necessary disclosures, obtained all necessary consents and government authorizations required under applicable law to permit the processing and international transfer of Your Data and Personal Data from you and your Affiliate, to NTT; and (vi) you authorize NTT to provide access to and use of the Software and Your Data to Third Party Providers.
- Third Party Providers. You are solely responsible for: (i) independently testing and validating any Third Party Provider products and services and the Software before deploying it or them in a test or production environment, (ii) evaluating whether using any Third Party Provider products or services are lawful under the laws that apply to you or are permitted in your jurisdiction, and (iii) paying for the Third Party Provider products and services and any claims that arise out of your use of their products and services. Any breach by a Third Party Provider of these Software Terms is a breach by you. NTT is not responsible or liable for any loss, costs or damages arising out of Third Party Provider’s actions or inactions in any manner, including but not limited to, for any disclosure, transfer, modification or deletion of Your Data. NTT does not control, monitor, maintain or provide support for, Third Party Providers or their services or products. NTT disclaims all warranties of any kind, and all indemnities, obligations, and other liabilities in connection with the Third Party Provider’s services and products, and any Third Party Provider interface or integration with NTT’s products or services (including the Software).
NTT Use of Data.
- Data Collection. The Software uses Your Data, Generated Data, Evidence Data and Execution Profile/Metric Data, for the benefit of all users, to help users protect themselves against suspicious and potentially destructive activities. NTT uses such data to: (i) analyze, characterize, attribute, warn of, and/or respond to threats against you and other users, (ii) analyze trends and performance, (iii) improve the functionality of, and develop, NTT’s products and services, and enhance cybersecurity; provided, however, that in all of the foregoing use cases, in a way that does not identify you or Software User’s Personal Data to other NTT users (other than your Third Party Providers). NTT may also enable Software Users and/or their Third Party Providers to use certain Your Data, Generated Data, Evidence Data or Execution Profile Metric Data in other applications or services. Neither Execution Profile/Metric Data nor Evidence Data are Software User’s confidential information or Your Data.
- File Collection. You and your Third Party Providers may have the option to upload (by submission, configuration, and/or, retrieval) files and other information related to the files for security analysis and response or, when submitting crash reports, to make the product more reliable and/or improve NTT’s products and services or enhance cyber-security. These potentially suspicious or unknown files may be transmitted and analyzed to determine functionality and their potential to cause instability or damage to Software User’s endpoints and systems. In some instances, these files could contain Personal Data.
- Processing Personal Data. Personal Data may be collected and used during the provisioning and use of the Software, to deliver, support and improve NTT’s products and services, further our business relationship, comply with law, act in accordance with Software User’s written instructions, or otherwise in accordance with these Software Terms and the Documentation. You authorizes NTT to collect, use, store, and transfer the Personal Data that you provide to NTT as contemplated in these Software Terms, NTT’s documentation and NTT’s Privacy Policy and Cookie Statement.
No Warranty.
- Disclaimer. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE PROVIDED “AS-IS” AND WITHOUT WARRANTY OF ANY KIND. NTT AND ITS AFFILIATES DISCLAIM ALL OTHER WARRANTIES, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE. TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, NTT AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE SOFTWARE AND ALL OTHER NTT OFFERINGS. THERE IS NO WARRANTY THAT THE SOFTWARE OR ANY OTHER NTT OFFERINGS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF SOFTWARE USER’S PARTICULAR PURPOSES OR NEEDS. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE SOFTWARE OR ANY OTHER NTT OFFERINGS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE. YOU AGREE THAT IT IS SOFTWARE USER’S RESPONSIBILITY TO ENSURE SAFE USE OF SOFTWARE AND ANY OTHER NTT OFFERING IN SUCH APPLICATIONS AND INSTALLATIONS. NTT DOES NOT WARRANT ANY THIRD PARTY PRODUCTS OR SERVICES.
- No Guarantee. YOU ACKNOWLEDGE, UNDERSTAND, AND AGREE THAT NTT DOES NOT GUARANTEE OR WARRANT THAT IT WILL FIND, LOCATE, DISCOVER, PREVENT OR WARN OF, ALL OF SOFTWARE USER’S OR ITS AFFILIATES’ SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND YOU AND YOUR AFFILIATES WILL NOT HOLD NTT RESPONSIBLE THEREFOR.
Limitation of Liability. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW NTT SHALL NOT BE LIABLE TO YOU (UNDER ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STATUTE, TORT OR OTHERWISE) FOR: (A) ANY LOST PROFITS, REVENUE, OR SAVINGS, LOST BUSINESS OPPORTUNITIES, LOST DATA, OR SPECIAL, INCIDENTAL, CONSEQUENTIAL, OR PUNITIVE DAMAGES, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES OR LOSSES OR SUCH DAMAGES OR LOSSES WERE REASONABLY FORESEEABLE; OR (B) AN AMOUNT THAT EXCEEDS IN THE AGGREGATE $100. THESE LIMITATIONS WILL APPLY NOTWITHSTANDING ANY FAILURE OF ESSENTIAL PURPOSE OF ANY REMEDY SPECIFIED IN THESE SOFTWARE TERMS. MULTIPLE CLAIMS SHALL NOT EXPAND THE LIMITATIONS SPECIFIED IN THIS SECTION 7.
Compliance with Laws. You agree to comply with all laws directly applicable to it in the performance of these Software Terms and use of the Software, including but not limited to, applicable export and import, anti-corruption and employment laws. You acknowledge and agree the Software shall not be used, transferred, or otherwise exported or re-exported to regions that the United Nations, the United States of America, the European Union and/or the United Kingdom maintains an embargo or comprehensive sanctions (collectively, “Embargoed Countries”), or to or by a national or resident thereof, or any person or entity subject to individual prohibitions (e.g., the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state), without first obtaining all required authorizations from the applicable government(s). You represent and warrant that you are not located in, or is under the control of, or a national or resident of, an Embargoed Country or Designated National.
Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy
Free Evaluation and Beta Test. NTT may, directly or through a reseller, offer you access to the Software for a free trial evaluation or invite you to participate in a beta test program. If you are permitted to access the Software on a free trial basis, you acknowledge and agree that the provisions of this Section 10 shall apply. In the event of a conflict between any other terms of these Software Terms of the Terms of Service and the provisions of this Section 11, the provisions of this Section 11shall control. A free trial evaluation may be requested by submitting a free trial evaluation request form and is subject to approval by NTT, in its sole discretion. The free trial access period is limited to thirty (30) days and will expire automatically without further action by you or NTT. During the free trial evaluation period NTT will monitor your use and communicate with you regarding the Software. The free trial does not include managed services. Other terms and conditions may apply. See the free trial evaluation request form. If you are invited by NTT to participate in a beta test of certain Software (“Beta Program”), your usage of the subject Software will be subject to these Software Terms and the additional beta program terms(the “Beta Terms”). With respect to the Beta Program, in the event of a conflict between these Software Terms and the Beta Program Terms, the Beta Program Terms will take precedence. IN AN EVALUATION OR BETA, THE SOFTWARE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT
General.
Incorporation by Reference; Priority. These Software Terms are subject to and incorporate by reference the Terms of Service. As it relates to access to and use of the Software, in the event of a conflict between the terms of these Software Terms and the Terms of Service, the terms of these Software Terms shall control.
Entire Agreement. Unless you have another valid agreement with NTT for the use of this Software, these Software Terms constitute the entire agreement between you and NTT concerning the Software. It is expressly agreed that as between you and NTT and regarding the Software, these Software Terms supersede any other terms you have on your procurement Internet portal, purchase order or any other agreement with any reseller, prime contractor or service provider. NTT is not obligated under Third Party Provider’s, or any reseller’s, prime contractor’s or other service provider’s agreement with you unless an officer of NTT executes the agreement. These Software Terms shall not be construed for or against any party to these Software Terms because that party or that party’s legal representative drafted any of its provisions.
Governing Law; Venue. These Software Terms, and the rights and duties of the parties arising hereunder, shall be governed by, construed, and enforced in accordance with the laws of Sweden, excluding its conflicts-of-law principles. The sole and exclusive jurisdiction and venue for actions arising under these Software Terms shall be the courts in Sweden, and the parties agree to service of process in accordance with the rules of such courts. The Uniform Computer Information Transactions Act and the United Nations Convention on the International Sale of Goods shall not apply. Notwithstanding the foregoing, each party reserves the right to file a suit or action in any court of competent jurisdiction as such party deems necessary to protect its intellectual property rights and, in NTT’s case, to recoup any payments due.
Waiver, Severability & Amendments. The failure of either party to enforce any provision of these Software Terms shall not constitute a waiver of any other provision or any subsequent breach. If any provision of these Software Terms is held to be illegal, invalid, or unenforceable, the provision will be enforced to the maximum extent permissible so as to affect the intent of the parties, and the remaining provisions of these Software Terms will remain in full force and effect.
Force Majeure. Neither party shall be liable for, nor shall either party be considered in breach of these Software Terms due to, any failure to perform its obligations under these Software Terms (other than its payment obligations) as a result of a cause beyond its control, including but not limited to, act of God or a public enemy, act of any military, civil or regulatory authority, change in any law or regulation, fire, flood, earthquake, storm or other like event, disruption or outage of communications (including an upstream server block and Internet or other networked environment disruption or outage), power or other utility, labor problem, or any other cause, whether similar or dissimilar to any of the foregoing, which could not have been prevented with reasonable care. The party experiencing a force majeure event, shall use commercially reasonable efforts to provide notice of such to the other party.
5.4.5.2 - NTT Software Terms of Use (v2.0 2025-06-11)
This document has been superseded. For the latest version please click HERE.
PLEASE READ CAREFULLY: YOU AND ANY COMPANY OR ENTITY THAT YOU ARE ACTING FOR (“YOU” OR “YOUR”) ACCEPTS THESE SOFTWARE TERMS OF USE (THE “SOFTWARE TERMS”) BY INSTALLING AND/OR USING THE SOFTWARE. YOU REPRESENT THAT YOU: 1. ARE LAWFULLY ABLE TO ENTER INTO THESE SOFTWARE TERMS, AND 2. HAVE FULL AUTHORITY TO BIND THE YOU TO THESE SOFTWARE TERMS. THESE SOFTWARE TERMS ARE A BINDING CONTRACT BETWEEN YOU AND NTT SECURITY HOLDINGS CORPORATION, A CORPORATION ORGANIZED AND EXISTING UNDER THE LAWS OF JAPAN (“NTT”), ON BEHALF OF ITSELF AND ANY OF ITS AFFILIATES PERFORMING HEREUNDER (COLLECTIVELY, “NTT”). IF YOU DO NOT HAVE THIS AUTHORITY, OR YOU DO NOT AGREE TO, OR CANNOT COMPLY WITH, ALL THE SOFTWARE TERMS, THEN YOU MAY NOT USE THE SOFTWARE. THESE SOFTWARE TERMS GOVERN YOUR USE OF THE SOFTWARE UNLESS YOU HAVE ANOTHER VALID AGREEMENT WITH NTT FOR THE USE OF THIS SOFTWARE.
Updating the Software Terms. NTT may revise and update these Software Terms from time to time in our sole discretion. Your continued use of the Software following the update of revised Software Terms means that you accept and agree to the changes. When accepted by you, the revised Software Terms automatically supersede the prior version. New Terms apply prospectively only.
Definitions.
“NTT Competitor” means a person or entity in the business of developing, distributing, or commercializing Internet security products or services substantially similar to or competitive with NTT’s products or services.
“Generated Data” shall mean the data generated by the Software, including but not limited to, correlative and/or contextual data, and/or detections. For the avoidance of doubt, Generated Data does not include Your Data. Any access to or use of Generated Data through the Software is expressly limited to your Internal Use.
“Documentation” means the Software end-user technical documentation.
“Endpoint” means any physical or virtual device, such as, a computer, server, laptop, desktop computer, mobile, cellular, container or virtual machine image.
“Evidence Data” means the malicious code, URL’s, malware, commands, techniques, objectives, or other information of unauthorized third parties either provided by Partner or Customer to NTT or collected or discovered during the course of providing the Products or Services; provided, neither Partner nor any Customer(s) are identified in such information.
“Internal Use” means access or use solely for Your own internal information security purposes. By way of example and not limitation, Internal Use does not include access or use: (i) for the benefit of any person or entity other than You, or (ii) in any event, for the development of any product or service. Internal Use is limited to access and use by your employees or your Third Party Providers for your benefit.
“Personal Data” means any information relating to an identified or identifiable person or other similar definition under the applicable data privacy laws; an identifiable natural person is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.
“Software” means the software accompanying these Software Terms, or NTT software that you or a Third Party Provider have installed or used on your Endpoints, including any updates thereto and/or related Documentation that may be made available from time to time by NTT. NTT software may commonly be referred to as “MDR” or “Samurai”.
“Third Party Provider” means any individual or entity (other than an NTT Competitor) that: (i) has access or use of the Software: (a) under these Software Terms solely on behalf of and for your Internal Use, or (b) under a separate valid agreement with NTT, (ii) has an agreement to provide you (or your Affiliates) services, and (iii) is subject to confidentiality obligations covering NTT’s Confidential Information.
“Your Data” means the data generated by your Endpoints and collected by the Software, but excluding Evidence Data. For the avoidance of doubt, Your Data does not include Generated Data.Your Account. You (and each user seeking access, use or receipt of the Software) will be asked to create a customer account. As part of the account creation process, you and each user be asked to provide a valid email address, create a password, and verify that they are a human being by providing a telephone number to which we’ll send a verification code to enter into a form. When registering for an account, you and each user must provide true, accurate, current and complete information about as requested during the account creation process. You and each user must keep that information true, accurate, current and complete after you create each account.
License and Restrictions.
- License. Subject to these Software Terms, if you have obtained a valid evaluation license or subscription to the Software through NTT or a designated NTT partner or reseller, You may, solely for your own Internal Use and during the period of time such evaluation or subscription remains valid, install and run this Software up to the validly licensed quantity.
- Restrictions. In addition to any restrictions stated in the Software Terms, you agree that the rights set forth in 4.1 above do not include any rights to, and you shall not: (i) employ or authorize a NTT Competitor to use the Software or the Documentation, or to provide management, hosting, or support for Software; (ii) alter, publicly display, translate, create derivative works of or otherwise modify the Software; (iii) sublicense, distribute or otherwise transfer the Software to any third party; (iv) allow third parties to access or use the Software; (v) reverse engineer, decompile, disassemble or otherwise attempt to derive the source code for the Software (except to the extent that such prohibition is expressly precluded by applicable law), circumvent its functions, or attempt to gain unauthorized access to NTT’s hosted software or its related systems or networks; (vi) use the Software to circumvent the security of another party’s network/information, develop malware, unauthorized surreptitious surveillance, data modification, data exfiltration, data ransom or data destruction; (vii) remove or alter any notice of proprietary right appearing on the Software; (viii) conduct any stress tests, competitive benchmarking or analysis on, or publish any performance data of, the Software (provided, that this does not prevent you from comparing Software to other products for legitimate purchase evaluation decisions and your Internal Use); or (x) cause, encourage or assist any third party to do any of the foregoing. You agree to use the Software in accordance with laws, rules and regulations directly applicable to you and acknowledges that you are solely responsible for determining whether a particular use of the Software is compliant with such laws. NTT Competitors or any other party with interests or intentions adverse to NTT may not access, install or use the Software or Generated Data.
- Third Party Software. NTT uses certain third party software in its Software, including what is commonly referred to as open source software. Under some of these third party licenses, NTT is required to provide you with notice of the license terms and attribution to the third party. See the licensing terms and attributions for such third party software that NTT uses in NTT’s list of Third Party Licensing Software Terms.
- Ownership & Feedback. Software is made available for use and licensed, not sold. NTT owns and retains all right, title and interest (including all intellectual property rights) in and to the Software. Any feedback or suggestions that you provides to NTT regarding any NTT products or services is non-confidential and may be used by NTT for any purpose without acknowledgement or compensation; provided, You will not be identified publicly as the source of the feedback or suggestion.
Your Obligations and Third Party Providers.
- Your Obligations. You represents and warrants that: (i) it owns or has a right of use from a third party, and controls, directly or indirectly, all of the software, hardware and computer systems (collectively, “Systems”) where the Software will be installed, (ii) to the extent required under any federal, state, or local U.S. or non-US laws it has authorized NTT to access the Systems and process and transmit data through the Software and any other NTT offerings in accordance with these Software Terms and as necessary to provide the Software and other services, (iii) it has a lawful basis in having the Software operate on the Systems, and collect and process the Your Data and the Personal Data; (iv) that it is and will at all relevant times remain duly and effectively authorized to instruct NTT to carry out the services related to the Software, (v) it has made all necessary disclosures, obtained all necessary consents and government authorizations required under applicable law to permit the processing and international transfer of Your Data and Personal Data from you and your Affiliate, to NTT; and (vi) you authorize NTT to provide access to and use of the Software and Your Data to Third Party Providers.
- Third Party Providers. You are solely responsible for: (i) independently testing and validating any Third Party Provider products and services and the Software before deploying it or them in a test or production environment, (ii) evaluating whether using any Third Party Provider products or services are lawful under the laws that apply to you or are permitted in your jurisdiction, and (iii) paying for the Third Party Provider products and services and any claims that arise out of your use of their products and services. Any breach by a Third Party Provider of these Software Terms is a breach by you. NTT is not responsible or liable for any loss, costs or damages arising out of Third Party Provider’s actions or inactions in any manner, including but not limited to, for any disclosure, transfer, modification or deletion of Your Data. NTT does not control, monitor, maintain or provide support for, Third Party Providers or their services or products. NTT disclaims all warranties of any kind, and all indemnities, obligations, and other liabilities in connection with the Third Party Provider’s services and products, and any Third Party Provider interface or integration with NTT’s products or services (including the Software).
NTT Use of Data.
- Data Collection. The Software uses Your Data, Generated Data, Evidence Data and Execution Profile/Metric Data, for the benefit of all users, to help users protect themselves against suspicious and potentially destructive activities. NTT uses such data to: (i) analyze, characterize, attribute, warn of, and/or respond to threats against you and other users, (ii) analyze trends and performance, (iii) improve the functionality of, and develop, NTT’s products and services, and enhance cybersecurity; provided, however, that in all of the foregoing use cases, in a way that does not identify you or your Personal Data to other NTT users (other than your Third Party Providers). NTT may also enable you and/or your Third Party Providers to use certain Your Data, Generated Data, Evidence Data or Execution Profile Metric Data in other applications or services. Neither Execution Profile/Metric Data nor Evidence Data are your confidential information or Your Data.
- File Collection. You and your Third Party Providers may have the option to upload (by submission, configuration, and/or, retrieval) files and other information related to the files for security analysis and response or, when submitting crash reports, to make the product more reliable and/or improve NTT’s products and services or enhance cyber-security. These potentially suspicious or unknown files may be transmitted and analyzed to determine functionality and their potential to cause instability or damage to your endpoints and systems. In some instances, these files could contain Personal Data.
- Processing Personal Data. Personal Data may be collected and used during the provisioning and use of the Software, to deliver, support and improve NTT’s products and services, further our business relationship, comply with law, act in accordance with your written instructions, or otherwise in accordance with these Software Terms and the Documentation. You authorizes NTT to collect, use, store, and transfer the Personal Data that you provide to NTT as contemplated in these Software Terms, NTT’s documentation and NTT’s Privacy Policy and Cookie Statement.
No Warranty.
- Disclaimer. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE PROVIDED “AS-IS” AND WITHOUT WARRANTY OF ANY KIND. NTT AND ITS AFFILIATES DISCLAIM ALL OTHER WARRANTIES, WHETHER EXPRESS, IMPLIED, STATUTORY OR OTHERWISE. TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, NTT AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE SOFTWARE AND ALL OTHER NTT OFFERINGS. THERE IS NO WARRANTY THAT THE SOFTWARE OR ANY OTHER NTT OFFERINGS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF YOUR PARTICULAR PURPOSES OR NEEDS. THE SOFTWARE AND ALL OTHER NTT OFFERINGS ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE SOFTWARE OR ANY OTHER NTT OFFERINGS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE. YOU AGREE THAT IT IS YOUR RESPONSIBILITY TO ENSURE SAFE USE OF SOFTWARE AND ANY OTHER NTT OFFERING IN SUCH APPLICATIONS AND INSTALLATIONS. NTT DOES NOT WARRANT ANY THIRD PARTY PRODUCTS OR SERVICES.
- No Guarantee. YOU ACKNOWLEDGE, UNDERSTAND, AND AGREE THAT NTT DOES NOT GUARANTEE OR WARRANT THAT IT WILL FIND, LOCATE, DISCOVER, PREVENT OR WARN OF, ALL OF YOUR OR YOUR AFFILIATES’ SYSTEM THREATS, VULNERABILITIES, MALWARE, AND MALICIOUS SOFTWARE, AND YOU AND YOUR AFFILIATES WILL NOT HOLD NTT RESPONSIBLE THEREFOR.
Limitation of Liability. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW NTT SHALL NOT BE LIABLE TO YOU (UNDER ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STATUTE, TORT OR OTHERWISE) FOR: (A) ANY LOST PROFITS, REVENUE, OR SAVINGS, LOST BUSINESS OPPORTUNITIES, LOST DATA, OR SPECIAL, INCIDENTAL, CONSEQUENTIAL, OR PUNITIVE DAMAGES, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES OR LOSSES OR SUCH DAMAGES OR LOSSES WERE REASONABLY FORESEEABLE; OR (B) AN AMOUNT THAT EXCEEDS IN THE AGGREGATE $100. THESE LIMITATIONS WILL APPLY NOTWITHSTANDING ANY FAILURE OF ESSENTIAL PURPOSE OF ANY REMEDY SPECIFIED IN THESE SOFTWARE TERMS. MULTIPLE CLAIMS SHALL NOT EXPAND THE LIMITATIONS SPECIFIED IN THIS SECTION 7.
Compliance with Laws. You agree to comply with all laws directly applicable to it in the performance of these Software Terms and use of the Software, including but not limited to, applicable export and import, anti-corruption and employment laws. You acknowledge and agree the Software shall not be used, transferred, or otherwise exported or re-exported to regions that the United Nations, the United States of America, the European Union and/or the United Kingdom maintains an embargo or comprehensive sanctions (collectively, “Embargoed Countries”), or to or by a national or resident thereof, or any person or entity subject to individual prohibitions (e.g., the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state), without first obtaining all required authorizations from the applicable government(s). You represent and warrant that you are not located in, or is under the control of, or a national or resident of, an Embargoed Country or Designated National
Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy
Beta Test. NTT may, directly or through a reseller, invite you to participate in a beta test program. If you are invited by NTT to participate in a beta test of certain Software (“Beta Program”), your usage of the subject Software will be subject to these Software Terms and the additional beta program terms (the “Beta Terms”). With respect to the Beta Program, in the event of a conflict between these Software Terms and the Beta Program Terms, the Beta Program Terms will take precedence. IN A BETA, THE SOFTWARE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT
General.
Incorporation by Reference; Priority. These Software Terms are subject to and incorporate by reference the Terms of Service. As it relates to access to and use of the Software, in the event of a conflict between the terms of these Software Terms and the Terms of Service, the terms of these Software Terms shall control.
Entire Agreement. Unless you have another valid agreement with NTT for the use of this Software, these Software Terms constitute the entire agreement between you and NTT concerning the Software. It is expressly agreed that as between you and NTT and regarding the Software, these Software Terms supersede any other terms you have on your procurement Internet portal, purchase order or any other agreement with any reseller, prime contractor or service provider. NTT is not obligated under Third Party Provider’s, or any reseller’s, prime contractor’s or other service provider’s agreement with you unless an officer of NTT executes the agreement. These Software Terms shall not be construed for or against any party to these Software Terms because that party or that party’s legal representative drafted any of its provisions.
Governing Law; Venue. These Software Terms, and the rights and duties of the parties arising hereunder, shall be governed by, construed, and enforced in accordance with the laws of Sweden, excluding its conflicts-of-law principles. The sole and exclusive jurisdiction and venue for actions arising under these Software Terms shall be the courts in Sweden, and the parties agree to service of process in accordance with the rules of such courts. The Uniform Computer Information Transactions Act and the United Nations Convention on the International Sale of Goods shall not apply. Notwithstanding the foregoing, each party reserves the right to file a suit or action in any court of competent jurisdiction as such party deems necessary to protect its intellectual property rights and, in NTT’s case, to recoup any payments due.
Waiver, Severability & Amendments. The failure of either party to enforce any provision of these Software Terms shall not constitute a waiver of any other provision or any subsequent breach. If any provision of these Software Terms is held to be illegal, invalid, or unenforceable, the provision will be enforced to the maximum extent permissible so as to affect the intent of the parties, and the remaining provisions of these Software Terms will remain in full force and effect.
Force Majeure. Neither party shall be liable for, nor shall either party be considered in breach of these Software Terms due to, any failure to perform its obligations under these Software Terms (other than its payment obligations) as a result of a cause beyond its control, including but not limited to, act of God or a public enemy, act of any military, civil or regulatory authority, change in any law or regulation, fire, flood, earthquake, storm or other like event, disruption or outage of communications (including an upstream server block and Internet or other networked environment disruption or outage), power or other utility, labor problem, or any other cause, whether similar or dissimilar to any of the foregoing, which could not have been prevented with reasonable care. The party experiencing a force majeure event, shall use commercially reasonable efforts to provide notice of such to the other party.
5.4.6 - Terms of Service
5.4.6.1 - Terms of Service (v1.0 2023-05-25)
This document has been superseded. For the latest version please click HERE.
Effective October 21, 2022
These NTT Security Holdings Corporation (“NTT”) Terms of Service (these “Terms”) apply to your purchase of NTT’s threat detection and response applications (including associated software and access to NTT’s hosted software applications) and related managed services and applicable documentation (“Samurai Services”), and consulting services and applicable service descriptions (“Consulting Services”, and together with Samurai Services, the “NTT Services”) directly from NTT or through any of NTT’s authorized resellers as identified in the quote, order form or online ordering document applicable to the NTT Services (the “Order”). The purpose of these Terms is to establish the terms and conditions under which you will access, use and receive NTT Services as described in the “Order”. These Terms shall take precedence over any other agreements, contracts or general terms that Customer may have entered into with a reseller as it relates to the NTT Services only. An Order is an integral part of these Terms and is fully incorporated herein.
These Terms are solely between NTT and you; any third party to whose services the NTT Services may allow connection is not a party to these Terms. Separate license terms apply to your use of such third-party services. To be eligible to register for a customer account in order to use or receive the NTT Services, you must review and accept these Terms by clicking on the “I Accept” or “Get Started” button or other mechanism provided. If you are accepting these Terms on behalf of a company or other legal entity, you represent and warrant that you have the authority to bind that company or other legal entity to these Terms, and, in such event, “you” and “your” will refer to that company or other legal entity. You and NTT may be referred to as a “Party” or, together, as the “Parties”.
The NTT Services are subject to these Terms, the related documentation and service descriptions, and any applicable Order submitted by you and expressly accepted by NTT.
YOU ACKNOWLEDGE AND AGREE THAT YOU HAVE READ, UNDERSTOOD AND AGREED TO THESE TERMS. IF YOU DO NOT AGREE WITH ALL THE TERMS, CONDITIONS AND LIMITATIONS OF THESE TERMS, YOU SHOULD NOT CLICK THE “I ACCEPT” OR “GET STARTED” BUTTON AND YOU ARE NOT AUTHORIZED TO RECEIVE THE NTT SERVICES. WRITTEN APPROVAL BY NTT IS NOT A PREREQUISITE TO THE VALIDITY OR ENFORCEABILITY OF THESE TERMS AND NO SOLICITATION OF ANY SUCH WRITTEN APPROVAL BY OR ON BEHALF OF NTT SHALL BE CONSTRUED AS AN INFERENCE TO THE CONTRARY. ACCEPTANCE BY NTT IS EXPRESSLY CONDITIONAL ON YOUR ASSENT TO THESE TERMS TO THE EXCLUSION OF ALL OTHER TERMS; IF THESE TERMS ARE CONSIDERED AN OFFER BY NTT, ACCEPTANCE IS EXPRESSLY LIMITED TO THESE TERMS.
IMPORTANT NOTE: THESE TERMS LIMIT OUR LIABILITY TO YOU. For more details, go to Section 19.
IN ADDITION, DISPUTES RELATED TO TERMS OR RELATED TO YOUR USE OF THE SERVICES GENERALLY MUST BE RESOLVED BY A DISPUTE RESOLUTION PROCESS WHICH MAY LEAD TO BINDING ARBITRATION. For more details, go to Sections 26 and 28.
Changes to These Terms. NTT may update these Terms from time to time by providing you with prior written notice of material updates at least thirty (30) days in advance of the effective date. Notice will be given in your account portal or via an email to the email address owner of your account. This notice will highlight the intended updates. Except as otherwise specified by NTT, updates will be effective upon the effective date indicated at the top of these Terms of Service. The updated version of these Terms will supersede all prior versions. Following such notice, your continued access or use of the NTT Services on or after the effective date of the changes to the Terms constitutes your acceptance of any updates. If you do not agree to any updates, you should stop using the NTT Services.You, and each user will be required to accept these Terms upon every log-in by a new user or upon changes to these Terms.
Your Account; Login. To access, use or receive the NTT Services or related software, you will be asked to create a customer account. As part of the account creation process, you’ll be asked to provide your email address, create a password, and verify that you’re a human being by providing a telephone number to which we’ll send you a verification code to enter into a form. When registering for an account, you must provide true, accurate, current and complete information about yourself as requested during the account creation process. You must keep that information true, accurate, current and complete after you create each account.
Your Responsibility. You are solely responsible for all access, use and receipt (whether or not authorized) of the NTT Services under your customer account(s) and for all acts and omissions of you or anyone to whom you provide access to or otherwise permit to use or receive the NTT Service (“Users”). You agree to take all reasonable precautions to prevent unauthorized access to or use of the NTT Service and will notify us promptly of any unauthorized access or use. We will not be liable for any loss or damage arising from unauthorized use of your customer account(s). You will be solely responsible, at your own expense, for acquiring, installing and maintaining all hardware, software and other equipment as may be necessary for you to connect to, access, use or receive the NTT Services.
Access to Services. During the term and subject to and conditioned on your payment of applicable fees and compliance with all the terms and conditions of these Terms, NTT will make the NTT Service available to you in accordance with these Terms, the applicable documentation and service descriptions, and any applicable Order, on a limited, non-exclusive and non-transferable basis, for use, access and receipt by you, limited to, in the case of Samurai Services, the number of Users for whom access to the NTT Services has been purchased. Such license grant for any software associated with the NTT Services that is to be downloaded by you shall include the right to make one copy for internal use in accordance with the documentation. You may upgrade the Samurai Services at any time through the Portal. Any such upgrade made through the Portal will constitute a valid and binding purchase order subject to these Terms, and the applicable subscription fee will be adjusted accordingly. Use of the Samurai Services is limited to your internal business purposes.
Restrictions and Unauthorized Use. You shall not (and shall not authorize any third party to): (i) decompile, disassemble, or otherwise reverse-engineer the NTT Services or attempt to reconstruct or discover any source code, underlying ideas, algorithms, file formats or programming interfaces of the NTT Services by any means whatsoever; (ii) sell, sublicense, rent, loan, lease, distribute, market, or commercialize the NTT Services for any purpose, including timesharing or service bureau purposes; (iii) remove any product identification, proprietary, copyright or other notices contained in the NTT Services; (iv) modify or create a derivative work of any part of the NTT Services, or incorporate the NTT Services into or with other products or software not contemplated by these Terms or the documentation (v) use the NTT Services for any competitive purpose or publicly disseminate performance information or analysis (including, without limitation, benchmarks) from any source relating to the NTT Services, or (vi) except for back-up purposes, copy or otherwise reproduce the NTT Services. Further, you will not use the NTT Services in any manner that violates any applicable law. In addition to complying with the other terms, conditions and restrictions set forth in these Terms, you agree to the Community Forum Guidelines which by this reference are hereby incorporated into this Agreement.
Applications and APIs. In some cases, it may be necessary for You to grant NTT access to an API or an Application which NTT is required to access in order to provide the NTT Services. You hereby grant NTT the right to access, use, assess and test the application(s) and/or application programming interface(s) (“API(s)”) in connection with providing NTT Services. You acknowledge and agree that NTT’s access and use of the application(s) and/or API(s) to provide NTT Services, is not subject to any “Terms of Use” or other terms or conditions that may be posted on, linked or otherwise provided with, the application(s) and/or API(s). You represent that you are either the owner of the application(s) and/or API(s) or have the authority to permit NTT to provide NTT Services in connection with such applications and/or API(s). You shall provide NTT adequate written evidence thereof upon NTT’s In the event any of the applications and/or API(s) are subject to third-party rights, you shall defend, indemnify and hold harmless NTT for any claims against NTT that arise from NTT accessing or using such applications and/or APIs to provide NTT Services.
Reservation of Rights. Each party reserves all rights not expressly granted in these Terms and no licenses are granted by either party to the other party under these Terms except as expressly stated in an Order, whether by implication, estoppel or otherwise. NTT or its licensors own and retain all right, title and interest (including all intellectual property rights) in and to the NTT Services, documentation and associated software, as applicable, including any modifications or improvements thereof, and applicable service descriptions.
Third-Party Services. We may use third-party services to help us provide the NTT Services, but such use does not indicate that we endorse the third-party or the third-party services, or are responsible or liable for the third-party services or the actions or omissions of the third-party. In addition, the NTT Services may link to third-party websites to facilitate its provision of services to you. If you use these links, you will leave the NTT Services. Please note that your use of such third-party services will be governed by the terms and Privacy Policy applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services.
Modification by NTT. NTT reserves the right to modify or discontinue, temporarily or permanently, the NTT Services (or any part thereof) with or without notice. NTT reserves the right to refuse any User access to the NTT Services without notice for any reason, including but not limited to a violation of these Terms. If you violate these Terms, including the Community Forum Guidelines, NTT reserves the right, in its discretion, to issue you a warning regarding the violation or immediately suspend or terminate any or all accounts you have created using the NTT Services.
Billing and Payment. NTT or the applicable reseller will bill, and you agree to pay, (i) for Samurai Services a subscription fee for the term in advance commencing on the subscription date, order date or renewal date, and (ii) for Consulting Services in accordance with the Order.
You are responsible for providing valid and current payment information and you agree to promptly update your account information, including payment information, with any changes that may occur (for example, a change in your billing address or credit card expiration date).
If you choose to upgrade your subscriptions for Samurai Services during your subscription term, any incremental subscription fees associated with such upgrade will be charged in accordance with the remaining subscription term and any renewal and you will be invoiced by NTT or the reseller promptly following the date of upgrade of renewal.
If you purchased the NTT Services from NTT and pay by credit card or certain other payment instruments, the portal provides an interface for you to change payment information (e.g. upon card renewal). Payments made by credit card, debit card or certain other payment instruments for NTT Services may be billed and processed by NTT using a third-party payment agent designated by NTT. You hereby authorize NTT or it’s payment agent to bill your credit card or other payment instrument in advance on a periodic basis in accordance with the terms of the applicable subscription or Order. You will receive a receipt upon each acceptance of payment by the payment agent, or you may obtain a receipt from within the portal to track subscription status. To the extent the payment agent is not NTT, the payment agent is acting solely as a billing and processing agent for and on behalf of NTT and shall not be construed to be providing the applicable NTT Service.
Taxes. Unless otherwise stated, the fees do not include taxes, levies, duties or similar governmental assessments, including value-added, sales, use or withholding taxes assessable by any local, state, provincial or foreign jurisdiction (“Taxes”). You are responsible for paying Taxes assessed in connection with your subscription to the NTT Services except those assessable against NTT or the reseller measured by its net income. You will be invoiced for such Taxes if NTT or the reseller believe it has a legal obligation to do so. You agree to pay such Taxes if so invoiced.
Term, Termination. The term for the NTT Services is as specified at the time you select the NTT Service through the cloud marketplace at the time of purchase (the “Portal”) or in the applicable Order. Unless otherwise specified at the time of purchase, Samurai Services will automatically renew for like term unless a Party provides thirty (30) days prior notice of nonrenewal. Either Party may terminate these Terms or an Order subject hereto upon thirty (30) days written notice to the other Party (the “Notice Period”) in the event of a material breach that the other Party fails to cure within the Notice Period. We may immediately terminate these Terms for cause and without advance notice if you violate the Community Forum Guidelines. Further, except in any case where the Order specifies the Samurai Services are subject to a minimum term, you may i) terminate your account or cancel the Samurai Services without cause at any time and for any reason, or for no reason, through the cloud marketplace where you purchased the Samurai Services, and ii) receive a refund of the unamortized portion of the prepaid fee for the terminated Samurai Services. Where the Order specifies the Samurai Services are subject to a minimum term, you will have no right to terminate the Samurai Services without cause during the minimum term or any renewal term, or receive a refund of prepaid fees. You acknowledge that you may, as the result of a termination, lose your account and all information and data associated therewith and you shall not be entitled to compensation for any such loss.
Updates, Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy.
Confidential Information. You acknowledge that you may obtain information relating to the NTT Services or NTT that has not been released to the public, including, but not limited to, code, technology, know-how, ideas, algorithms, testing procedures, structure, interfaces, specifications, documentation, bugs, problem reports, analysis and performance information, and other technical, business, product, and data (“Confidential Information”). You shall not disclose Confidential Information to any third party or use Confidential Information for any purpose other than the use of the NTT Services as licensed under these Terms. You will use the same degree of care that it uses to protect the confidentiality of its own confidential information of like kind and, in any case, at least a reasonable degree of care. You acknowledge and agree that no adequate remedy may exist at law for an actual or threatened breach of this Section 14 and that, in the event of an actual or threatened breach of the provisions of this Section 14, the non-breaching party will be entitled to seek immediate injunctive and other equitable relief, without waiving any other rights or remedies available to it.
Warranty Disclaimer. THE NTT SERVICES, THE DOCUMENTATION AND SERVICE DESCRIPTIONS ARE PROVIDED “AS IS” AND “AS AVAILABLE” WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT. YOUR USE OF THE NTT SERVICES IS AT YOUR SOLE RISK. IN ADDITION, WHILE NTT ATTEMPTS TO PROVIDE A GOOD USER EXPERIENCE, WE CANNOT AND DO NOT REPRESENT OR WARRANT THAT THE NTT SERVICES WILL ALWAYS BE SECURE OR ERROR-FREE OR THAT THE NTT SERVICES WILL ALWAYS FUNCTION WITHOUT DELAYS, DISRUPTIONS, OR IMPERFECTIONS. THE FOREGOING DISCLAIMERS SHALL APPLY TO THE EXTENT PERMITTED BY APPLICABLE LAW.
Indemnification by NTT. NTT will indemnify and defend you from and against any claim brought by a third party against you by reason of your use of a Samurai Service, as permitted hereunder, alleging that such Samurai Service infringes or misappropriates a third party’s valid patent, copyright, trademark or trade secret (a “Claim”). NTT shall, at its expense, defend such IP Claim and pay damages finally awarded against you in connection therewith, including the reasonable fees and expenses of the attorneys engaged by NTT for such defense, provided that (a) you promptly notify NTT of the threat or notice of such IP Claim; (b) NTT will have the sole and exclusive control and authority to select defense attorneys, and defend and/or settle any such IP Claim (however, NTT shall not settle or compromise any claim that results in liability or admission of any liability by you without your prior written consent); and (c) you fully cooperate with NTT in connection therewith. If use of a Service by you, your agents or users has become, or, in NTT’s opinion, is likely to become, the subject of any such Claim, NTT may, at NTT’s option and expense, (i) procure for you the right to continue using the Samurai Service(s) as set forth hereunder; (ii) replace or modify a Service to make it non-infringing; or (iii) if options (i) or (ii) are not commercially reasonable or practicable as determined by NTT, terminate your subscription to the Samurai Service(s) and repay you, on a pro-rata basis, any subscription fees previously paid to NTT for the corresponding unused portion of the term of your subscription for such Samurai Service(s). NTT will have no liability or obligation to indemnify you with respect to any Claim if such claim is caused in whole or in part by (x) compliance with designs, data, instructions or specifications provided by you; (y) modification of the Samurai Service(s) by anyone other than NTT; or (z) the combination, operation or use of the Samurai Service(s) with other hardware or software where a Service would not by itself be infringing. The provisions of this Section 16 state the sole, exclusive and entire liability of NTT to you and constitute your sole remedy with respect to an Claim brought by reason of access to or use of a Service by you, your agents or users.
Indemnification by You. You agree to defend, indemnify and hold NTT, harmless from and against any loss, liability, claim, demand, damages, costs and expenses, including reasonable attorney’s fees, arising out of or in connection with: (i) your use of and access to the NTT Service; (ii) your violation of any term of these Terms; (iii) your violation of any third party right, including without limitation any copyright, property, or privacy right or any third party agreement; (iv) any information you provide on or through the Service, or NTT’s access or use of applications or APIs (each, a “Claim”). As used in this Section 17, “you” shall include anyone accessing the Service using your password.
Conditions of Indemnification. As a condition of the foregoing indemnification obligations set forth in Sections 16 and 17: (a) the indemnified party (“Indemnified Party”) will promptly notify the indemnifying party (“Indemnifying Party”) of any Infringement Claim or Customer Indemnifiable Claim, as applicable (collectively referred to as a “Claim”), provided, however, that the failure to give such prompt notice shall not relieve the Indemnifying Party of its obligations hereunder except to the extent that the Indemnifying Party was actually and materially prejudiced by such failure; (b) the Indemnifying Party will have the sole and exclusive authority to defend or settle any such Claim (provided that, the Indemnifying Party will obtain the Indemnified Party’s consent in connection with any act or forbearance required by the Indemnified Party, which consent will not be unreasonably withheld); and (c) the Indemnified Party will reasonably cooperate with the Indemnifying Party in connection with the Indemnifying Party’s activities hereunder, at the Indemnifying Party’s expense. The Indemnified Party reserves the right, at its own expense, to participate in the defense of a Claim. Notwithstanding anything herein to the contrary, the Indemnifying Party will not settle any Claims for which it has an obligation to indemnify pursuant to this Section 18 admitting liability or fault on behalf of the Indemnified Party, nor create any obligation on behalf of the Indemnified Party without the Indemnified Party’s prior written consent.
Limitation of Damages and Remedies. IN NO EVENT SHALL NTT OR ITS LICENSORS BE LIABLE UNDER CONTRACT, TORT, STRICT LIABILITY OR OTHER LEGAL OR EQUITABLE THEORY FOR ANY INDIRECT, INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH YOUR USE OF THE NTT SERVICES, THIRD-PARTY USE OF THE NTT SERVICES ENABLED BY YOU, OR YOUR OR THIRD-PARTY USE OF ANY DATA OR SOFTWARE ENABLED BY YOU VIA THE NTT SERVICES. NTT SHALL NOT BE LIABLE FOR LOSS, INACCURACY, INCOMPLETENESS, OR RELEASE OF DATA, COST OF PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, SYSTEM DOWNTIME, GOODWILL, PROFITS OR OTHER BUSINESS LOSS, REGARDLESS OF LEGAL THEORY, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. NOTWITHSTANDING ANYTHING HEREIN TO THE CONTRARY, THE TOTAL LIABILITY OF NTT ARISING OUT OF THESE TERMS, INCLUDING BUT NOT LIMITED TO DAMAGES OR LIABILITY OF NTT ARISING OUT OF CONTRACT, TORT, BREACH OF WARRANTY, INFRINGEMENT OR OTHERWISE, SHALL NOT IN ANY EVENT EXCEED THE FEES PAID BY YOU WITH RESPECT TO THE SPECIFIC NTT SERVICE WHICH CAUSED THE CLAIM DURING THE TWELVE (12) MONTHS PRIOR TO THE FIRST EVENT OR OCCURRENCE GIVING RISE TO SUCH LIABILITY. THE PARTIES AGREE THAT THE LIMITATIONS OF THIS SECTION 19 ARE ESSENTIAL AND THAT NTT WOULD NOT PERMIT YOU TO USE THE NTT SERVICES ABSENT THE TERMS OF THIS SECTION 19. THIS SECTION 19 SHALL SURVIVE AND APPLY EVEN IF ANY REMEDY SPECIFIED IN THESE TERMS SHALL BE FOUND TO HAVE FAILED OF ITS ESSENTIAL PURPOSE. THE PROVISIONS OF THIS SECTION 19 ALLOCATE THE RISKS PURSUANT TO THESE TERMS BETWEEN THE PARTIES, AND THE PARTIES HAVE RELIED ON THE LIMITATIONS SET FORTH HEREIN IN DETERMINING WHETHER TO ENTER INTO THESE TERMS.
Export Compliance, Sanctions. You acknowledge that the NTT Services may be subject to export restrictions by the United States government and import restrictions by certain foreign governments. You shall not and shall not authorize any third-party to remove or export from the United States or allow the export or re-export of any part of the NTT Services or any direct product thereof: (i) into (or to a national or resident of) any embargoed or terrorist-supporting country; (ii) to anyone on the U.S. Commerce Department’s Table of Denial Orders or U.S. Treasury Department’s list of Specially Designated Nationals; (iii) to any country to which such export or re-export is restricted or prohibited, or as to which the United States government or any agency thereof requires an export license or other governmental approval at the time of export or re-export without first obtaining such license or approval; or (iv) otherwise in violation of any export or import restrictions, laws or regulations of any United States or foreign agency or authority. You agree to the foregoing and warrant that you are not located in, under the control of, or a national or resident of any such prohibited country or on any such prohibited party list. The NTT Services are further restricted from being used for the design or development of nuclear, chemical, or biological weapons or missile technology, or for terrorist activity, without the prior permission of the United States government.
You warrant that neither you or any entity or person that has direct or indirect control of fifty percent or more of your shares are not subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”). You agree that if at any time you become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under the Terms, or the performance of the Terms exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate the NTT Services upon such Sanctions becoming effective.
A breach of this Section 20 shall be a material default for the purpose of Section 12.
Ownership. NTT exclusively owns and reserves all right, title and interest in and to the NTT Services, documentation, service descriptions, our Confidential Information, and all anonymized or aggregated data resulting from use and operation of the NTT Services and that do not identify a natural person as the source of the information, as well as any feedback, recommendations, correction requests, or suggestions from you or any End User about the Services (“Contributions”).
Suggestions and Contributions. If you submit suggestions or contributions (“Contributions”) you agree that: (a) NTT is not under any obligation of confidentiality with respect to your Contributions; (b) NTT may use or disclose (or choose not to use or disclose) your Contributions for any purpose and in any way; (c) NTT will own your Contributions; and (d) you are not entitled to any compensation or reimbursement of any kind from NTT under any circumstances for your Contributions.
Additional Addenda. Your use of the NTT Services, and associated software are subject to the NTT Privacy Policy, Cookie Statement and Data Processing Agreement. To the extent your use of the NTT Service allows you to use the associated software, or you otherwise access and use the NTT software, such access and use shall be subject to the Software Terms of Use.
Data Protection. The terms of the Data Processing Agreement made part hereof (“Data Processing Agreement”) shall apply when personal data is being processed pursuant to these Terms. Additionally, personal data may be disclosed in accordance with the Privacy Policy. You acknowledge that you have read the “Privacy Policy” and understand that it sets forth how NTT will collect, store, use and disclose your data including personal data. If you do not agree with our Privacy Policy, then you must stop using the NTT Service immediately.
Survival. Upon termination of these Terms, your payment obligations, the terms of this Section 25, and the terms of the following Sections will survive (i.e. still apply): Section 10 (Billing & Payment), Section 14 (Confidentiality), Section 15 Warranty Disclaimer, Section 16 (Indemnification by NTT), Section 17 (Indemnification by You), Section 18 (Conditions of Indemnification), Section 19 (Limitation of Damages and Remedies), Section 21 (Ownership), Section 25 (Survival), Section 26 (Governing Law), and Section 28 (Agreement to Arbitration).
Governing Law. The enforceability and interpretation of Section 28 (Agreement to Arbitrate) will be determined by the Federal Arbitration Act (including its procedural provisions). Apart from Section 28, these Terms will be governed by and interpreted according to the laws of the State of California without regard to conflicts of laws and principles that would cause laws of another jurisdiction to apply; provided, if your principal place of business is in the European Union, Iceland, Liechtenstein, Norway, Switzerland or the United Kingdom, these Terms will be governed by the substantive laws of Sweden without regard to conflicts of laws and principles that would cause laws of another jurisdiction to apply. These Terms will not be governed by the United Nations Convention on Contracts for the International Sale of Goods. Except as provided in Section 28 (Agreement to Arbitration), any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in either the state or federal courts of San Francisco, California, and we each consent to the personal jurisdiction of these courts; provided, if pursuant to this Section 26 the laws of Sweden govern these Terms, legal suit, action or proceedings arising out of or related to these Terms or the NTT Services shall be instituted in the courts of Sweden.
Venue. Except as provided in Section 28 (Agreement to Arbitration), any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in either the state or federal courts of San Francisco, California, where the laws of California govern and we each consent to the personal jurisdiction of these courts; provided, where the laws of Sweden govern these Terms, any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in the applicable courts of Stockholm, Sweden, and we each consent to the personal jurisdiction of these courts.
Agreement to Arbitration. Except for a disputes relating to you, your affiliates’, NTT or NTT’s affiliates’ intellectual property (e.g., trademarks, trade dress, domain names, trade secrets, copyrights or patents) (the “Excepted Disputes”). NTT and you agree to arbitrate. If a dispute cannot be resolved, you or any of your affiliates on one hand and NTT and any of NTT’s affiliates on the other hand, all agree to resolve any dispute relating to these Terms or in relation to the NTT Services by binding arbitration in San Francisco, California. This applies to all claims under any legal theory, except Excepted Disputes. It also applies even after you have stopped using your customer account(s) or closed it. If NTT and you have a dispute about whether this agreement to arbitrate can be enforced or applies to our dispute, we all agree that the arbitrator will decide that, too.
Each of us can bring a claim in small claims court either in San Francisco, California, or the county where you live, or some other place we both agree on, if it qualifies to be brought in that court. In addition, if any of us brings a claim in court that should be arbitrated or any of us refuses to arbitrate a claim that should be arbitrated, the other of us can ask a court to force us to go to arbitration to resolve the claim (i.e., compel arbitration). Any of us may also ask a court to halt a court proceeding while an arbitration proceeding is ongoing.
Prior to filing any arbitration, both parties jointly agree to seek to resolve any dispute between us by mediation conducted by the American Arbitration Association (AAA), with all mediator fees and expenses paid equally by the parties. If mediation is not successful, either party may initiate an arbitration proceeding with AAA. You can look at AAA’s rules and procedures on their website http://www.adr.org or you can call them at 1-800-778-7879. The arbitration will be governed by the then-current version of AAA’s Commercial Arbitration Rules (the “Rules”) and will be held with a single arbitrator appointed in accordance with the Rules. To the extent anything described in this Section 28 conflicts with the Rules, the language of this Section 28 applies. Each of us will be entitled to get a copy of non-privileged relevant documents in the possession or control of the other party and to take a reasonable number of depositions. All such discovery will be in accordance with procedures approved by the arbitrator. This Section 28 does not alter in any way the statute of limitations that would apply to any claims or counterclaims asserted by either party. The arbitrator’s award will be based on the evidence admitted and the substantive law of the State of California and the United States, as applicable, and will contain an award for each issue and counterclaim. The award will provide in writing the factual findings and legal reasoning for such award. The arbitrator will not be entitled to modify these Terms. Except as provided in the Federal Arbitration Act, the arbitration award will be final and binding on the parties. Judgment may be entered in any court of competent jurisdiction.Free Evaluation and Beta Test. NTT may, directly or through a reseller, offer You access to the Samurai Services for a free trial evaluation or invite You to participate in a beta test program. If You are permitted to access the Samurai Services on a free trial basis, You acknowledge and agree that the provisions of this Section 29 shall apply. In the event of a conflict between any other terms of the Terms of Service and the provisions of this Section 29, the provisions of this Section 29 shall control. A free trial evaluation may be requested by submitting a free trial evaluation request form and is subject to approval by NTT, in its sole discretion. The free trial access period is limited to thirty (30) days and will expire automatically without further action by You or NTT. During the free trial evaluation period NTT will monitor Your use and communicate with you regarding the Service. The free trial does not include managed services. Other terms and conditions may apply. See the free trial evaluation request form. If you are invited by NTT to participate in a beta test of certain Samurai Services (“Beta Program”), your usage of the subject Samurai Services will be subject to these Terms of Service and the additional beta program terms (the “Beta Terms”). With respect to the Beta Program, in the event of a conflict between these Terms of Service and the Beta Program Terms, the Beta Program Terms will take precedence. IN AN EVALUATION OR BETA, THE SERVICE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT.
Miscellaneous. Neither these Terms nor the licenses granted hereunder are assignable or transferable by you (and any attempt to do so shall be void). NTT may freely assign, delegate, license and/or transfer these Terms, in whole or in part, without consent. You and NTT are independent contractors in the performance of each and every part of these Terms. Nothing in these Terms is intended to create or shall be construed as creating an employer-employee relationship or a partnership, agency, joint venture, or franchise. These Terms shall be deemed to have been made in and shall be construed pursuant to the laws of California without regard to conflicts of laws provisions thereof, and without regard to the United Nations Convention on the International Sale of Goods or the Uniform Computer Information Transactions Act. Subject to the foregoing, the provisions hereof are for the benefit of the parties only and not for any other person or entity. Any notice, report, approval, authorization, agreement or consent required or permitted hereunder shall be in writing; notices shall be sent to the address the applicable party has or may provide by written notice or, if there is no such address, the most recent address the party giving notice can locate using reasonable efforts. No failure or delay in exercising any right hereunder will operate as a waiver thereof, nor will any partial exercise of any right or power hereunder preclude further exercise. If any provision shall be adjudged by any court of competent jurisdiction to be unenforceable or invalid, that provision shall be limited or eliminated to the minimum extent necessary so that these Terms shall otherwise remain in full force and effect and enforceable. This is the complete and exclusive statement of the mutual understanding of the parties with respect to the license granted herein and supersedes and cancels all previous written and oral agreements and communications relating to such license and any waivers or amendments shall be effective only if executed in writing by NTT; however, any pre-printed or standard terms of any purchase order, confirmation, or similar form, unless signed by NTT after the effectiveness hereof, shall have no force or effect. You are responsible for the information you provide or make available to the NTT Services and you must ensure it is accurate, not misleading and does not contain material that is obscene, defamatory, or infringing on any rights of any third party; does not contain malicious code and is not otherwise legally actionable. The substantially prevailing party in any action to enforce these Terms will be entitled to recover its attorney’s fees and costs in connection with such action. Except as described in Section 28 (Agreement to Arbitrate), if any provision of these Terms is held by a court or other tribunal of competent jurisdiction to be unenforceable, that provision will be limited or eliminated to the minimum extent necessary to make it enforceable and, in any event, the rest of these Terms will continue in full force and effect. NTT’s failure to enforce at any time any provision of these Terms, or any other of your obligations does not waive our right to do so later. And, if we do expressly waive any provision of these Terms, or any of your other obligations, that does not mean it is waived for all time in the future. Any waiver must be in writing and signed by NTT and you to be legally binding. No failure, delay or default in performance of any obligation of a party shall constitute an event of default or breach of these Terms to the extent that such failure to perform, delay or default arises out of a cause, existing or future, that is beyond the control and without negligence of such party, including action or inaction of governmental, civil or military authority; fire; strike, lockout or other labor dispute; flood, terrorist act; war; riot; theft; earthquake and other natural disaster. The party affected by such cause shall take all reasonable actions to minimize the consequences of any such cause. In the event of a conflict between a provision of these Terms and the provisions of an Order subject to these Terms, the provision of the Order will control.
5.4.6.2 - Terms of Service (v2.0 2023-10-24)
This document has been superseded. For the latest version please click HERE.
These NTT Security Holdings Corporation (“NTT”) Terms of Service (these “Terms”) apply to your purchase of NTT’s Samurai Managed Detection and Response service, related managed services and applicable documentation and applicable Service Descriptions (“Samurai Services”), and consulting services and applicable Service Descriptions (“Consulting Services”, and together with Samurai Services, the “NTT Services”) directly from NTT or through any of NTT’s authorized resellers as identified in the quote, order form or online ordering document applicable to the NTT Services (the “Order”). The Service Descriptions for the Samurai Services and Consulting Service are found here. The purpose of these Terms is to establish the terms and conditions under which you will access, use and receive NTT Services as described in the “Order”. These Terms shall take precedence over any other agreements, contracts or general terms that Customer may have entered into with a reseller as it relates to the NTT Services only. An Order is an integral part of these Terms and is fully incorporated herein.
These Terms are solely between NTT and you; any third party to whose services the NTT Services may allow connection is not a party to these Terms. Separate license terms apply to your use of such third-party services.
To be eligible to register for a customer account in order to use or receive the NTT Services, you must review and accept these Terms by clicking on the “I Accept” or “Get Started” button or other mechanism provided. If you are accepting these Terms on behalf of a company or other legal entity, you represent and warrant that you have the authority to bind that company or other legal entity to these Terms, and, in such event, “you” and “your”, whether or not capitalised, will refer to that company or other legal entity. You and NTT may be referred to as a “Party” or, together, as the “Parties”.
The NTT Services are subject to these Terms, the related documentation and Service Descriptions, and any applicable Order submitted by you and expressly accepted by NTT. All documentation related to these Terms can be found here.
You acknowledge and agree that you have read, understood and agreed to these terms. If you do not agree with all the terms, conditions and limitations of these terms, you should not click the “I Accept” or “Get Started” button and you are not authorized to receive the NTT services. Written approval by NTT is not a prerequisite to the validity or enforceability of these terms and no solicitation of any such written approval by or on behalf of NTT shall be construed as an inference to the contrary. Acceptance by NTT is expressly conditional on your assent to these terms to the exclusion of all other terms; if these terms are considered an offer by NTT, acceptance is expressly limited to these terms.
Important note: these terms limit our liability to you. For more details, go to Section 18.
In addition, disputes related to terms or related to your use of the services generally must be resolved by a dispute resolution process which may lead to binding arbitration. For more details, go to Sections 25 and 27.
Changes to These Terms. NTT may update these Terms from time to time by providing you with prior written notice of material updates at least thirty (30) days in advance of the effective date. Notice will be given in your account portal or via an email to the email address of the owner of your account. This notice will highlight the intended updates. Except as otherwise specified by NTT, updates will be effective upon the effective date indicated at the top of these Terms of Service. The updated version of these Terms will supersede all prior versions. Following such notice, your continued access or use of the NTT Services on or after the effective date of the changes to the Terms constitutes your acceptance of any updates. If you do not agree to any updates, you should stop using the NTT Services. If you cease using the NTT Services for this reason you will receive a refund of the unused portion of subscription fees paid in advance. Every user will be required to accept the Software Terms of Use upon first login. You are required to accept these Terms before using the Service and upon changes to these Terms.
Your Account: Login. To access, use, or receive, the NTT Services or related software, you will be asked to create a customer account. As part of the account creation process, you’ll be asked to provide your email address, create a password, and verify that you’re a human being by providing a telephone number to which we’ll send you a verification code to enter into a form. When registering for an account, you must provide true, accurate, current, and complete information, about yourself as requested during the account creation process. You must keep that information true, accurate, current, and complete, after you create each account.
Your Responsibility. You are solely responsible for all access, use, and receipt, (whether or not authorized) of the NTT Services under your customer account(s) and for all acts and omissions of you or anyone to whom you provide access to or otherwise permit to use or receive the NTT Service (“Users”). You agree to take all reasonable precautions to prevent unauthorized access to or use of the NTT Service and will notify us promptly of any unauthorized access or use. We will not be liable for any loss or damage arising from unauthorized use of your custoData Protection.mer account(s). You will be solely responsible, at your own expense, for acquiring, installing and maintaining all hardware, software and other equipment as may be necessary for you to connect to, access, use or receive the NTT Services.
Access to Services. During the term and subject to and conditioned on your payment of applicable fees and compliance with all the terms and conditions of these Terms, NTT will make the NTT Service available to you in accordance with these Terms, the applicable documentation and Service Descriptions, and any applicable Order, on a limited, non-exclusive and non-transferable basis, for use, access and receipt by you, limited to, in the case of Samurai Services, the number of Users for whom access to the NTT Services has been purchased.
Restrictions and Unauthorized Use. You shall not (and shall not authorize any third party to): (i) decompile, disassemble, or otherwise reverse-engineer the NTT Services or attempt to reconstruct or discover any source code, underlying ideas, algorithms, file formats or programming interfaces of the NTT Services by any means whatsoever; (ii) sell, sublicense, rent, loan, lease, distribute, market, or commercialize the NTT Services for any purpose, including timesharing or service bureau purposes; (iii) remove any product identification, proprietary, copyright or other notices contained in the NTT Services; (iv) modify or create a derivative work of any part of the NTT Services, or incorporate the NTT Services into or with other products or software not contemplated by these Terms or the documentation (v) use the NTT Services for any competitive purpose or publicly disseminate performance information or analysis (including, without limitation, benchmarks) from any source relating to the NTT Services, or (vi) except for back-up purposes, copy or otherwise reproduce the NTT Services. Further, you will not use the NTT Services in any manner that violates any applicable law. NTT reserves the right to refuse any User access to the NTT Services without notice for any reason, including but not limited to a violation of these Terms. If you violate these Terms NTT reserves the right to issue you a warning regarding the violation or immediately suspend or terminate any or all accounts you have created using the NTT Services.
Applications and APIs. In some cases, it may be necessary for you to grant NTT access to an API or an Application which NTT is required to access in order to provide the NTT Services. You hereby grant NTT the right to access, use, assess and test the application(s) and/or application programming interface(s) (“API(s)”) in connection with providing NTT Services. You acknowledge and agree that NTT’s access and use of the application(s) and/or API(s) to provide NTT Services, is not subject to any “Terms of Use” or other terms or conditions that may be posted on, linked or otherwise provided with, the application(s) and/or API(s). You represent that you are either the owner of the application(s) and/or API(s) or have the authority to permit NTT to provide NTT Services in connection with such applications and/or API(s). You shall provide NTT adequate written evidence thereof upon NTT’s In the event any of the applications and/or API(s) are subject to third-party rights, you shall defend, indemnify and hold harmless NTT for any claims against NTT that arise from NTT accessing or using such applications and/or APIs to provide NTT Services.
Reservation of Rights. Each party reserves all rights not expressly granted in these Terms and no licenses are granted by either party to the other party under these Terms except as expressly stated in an Order, whether by implication, estoppel or otherwise. NTT or its licensors own and retain all right, title and interest (including all intellectual property rights) in and to the NTT Services, documentation and associated software, as applicable, including any modifications or improvements thereof, and applicable Service Descriptions.
Third-Party Services. We may use third-party services to help us provide the NTT Services, but such use does not indicate that we endorse the third-party or the third-party services, or applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services. Privacy Policy applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services.
Modification by NTT. Without materially degrading the Service, NTT reserves the right to modify, enhance, or otherwise change, the NTT Services (or any part thereof), including the Service Description, with or without notice.
Taxes. Unless otherwise stated, the fees do not include taxes, levies,
or similar governmental assessments, including value-added, sales, use or withholding taxes assessable by any local, state, provincial or foreign jurisdiction (“Taxes”). You are responsible for paying Taxes assessed in connection with your subscription to the NTT Services except those assessable against NTT or the reseller measured by its net income. You will be invoiced for such Taxes if NTT or the reseller believe it has a legal obligation to do so. You agree to pay such Taxes if so invoiced.Term, Termination. The term for the NTT Services is as specified in the applicable Order for the NTT Service. Unless otherwise specified at the time of purchase, Samurai Services will automatically renew for like term unless a Party provides thirty (30) days prior notice of nonrenewal. Either Party may terminate these Terms or an Order subject hereto upon thirty (30) days written notice to the other Party (the “Notice Period”) in the event of a material breach that the other Party fails to cure within the Notice Period. Further, except in any case where the Order specifies the Samurai Services are subject to a minimum term, you may i) terminate your account or cancel the Samurai Services without cause at any time and for any reason, or for no reason, and ii) receive a refund of the unamortized portion of the prepaid fee for the terminated Samurai Services. Where the Order specifies the Samurai Services are subject to a minimum term, you will have no right to terminate the Samurai Services without cause during the minimum term or any renewal term, or receive a refund of prepaid fees. You acknowledge that you may, as the result of a termination, lose your account and all information and data associated therewith and you shall not be entitled to compensation for any such loss.
Updates, Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy.
Confidential Information. Both Parties acknowledge that they may obtain information relating to the each other’s services or businesses that has not been released to the public, including, but not limited to, code, technology, know-how, ideas, algorithms, testing procedures, structure, interfaces, specifications, documentation, bugs, problem reports, analysis and performance information, and other technical, business, product, and data (“Confidential Information”). A Party shall not disclose Confidential Information to any third party or use Confidential Information for any purpose other than the use of the NTT Services as licensed under these Terms or other purposes for which the Information has been provided. Each Party agrees to use the same degree of care that it uses to protect the confidentiality of its own confidential information of like kind and, in any case, at least a reasonable degree of care. Each Party acknowledges and agrees that no adequate remedy may exist at law for an actual or threatened breach of this Section 14 and that, in the event of an actual or threatened breach of the provisions of this Section 14, the non-breaching party will be entitled to seek immediate injunctive and other equitable relief, without waiving any other rights or remedies available to it.
Warranty Disclaimer. THE NTT SERVICES, THE DOCUMENTATION AND SERVICE DESCRIPTIONS ARE PROVIDED “AS IS” AND “AS AVAILABLE” WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT. YOUR USE OF THE NTT SERVICES IS AT YOUR SOLE RISK. IN ADDITION, WHILE NTT ATTEMPTS TO PROVIDE A GOOD USER EXPERIENCE, WE CANNOT AND DO NOT REPRESENT OR WARRANT THAT THE NTT SERVICES WILL ALWAYS BE SECURE OR ERROR-FREE OR THAT THE NTT SERVICES WILL ALWAYS FUNCTION WITHOUT DELAYS, DISRUPTIONS, OR IMPERFECTIONS. THE FOREGOING DISCLAIMERS SHALL APPLY TO THE EXTENT PERMITTED BY APPLICABLE LAW.
Indemnification by NTT. NTT will indemnify and defend you from and against any claim brought by a third party against you by reason of your use of a Samurai Service, as permitted hereunder, alleging that such Samurai Service infringes or misappropriates a third party’s valid patent, copyright,
or trade secret (a “Claim”). NTT shall, at its expense, defend such IP Claim and pay damages finally awarded against you in connection therewith, including the reasonable fees and expenses of the attorneys engaged by NTT for such defense, provided that (a) you promptly notify NTT of the threat or notice of such IP Claim; (b) NTT will have the sole and exclusive control and authority to select defense attorneys, and defend and/or settle any such IP Claim (however, NTT shall not settle or compromise any claim that results in liability or admission of any liability by you without your prior written consent); and (c) you fully cooperate with NTT in connection therewith. If use of a Service by you, your agents or users has become, or, in NTT’s opinion, is likely to become, the subject of any such Claim, NTT may, at NTT’s option and expense, (i) procure for you the right to continue using the Samurai Service(s) as set forth hereunder; (ii) replace or modify a Service to make it non-infringing; or (iii) if options (i) or (ii) are not commercially reasonable or practicable as determined by NTT, terminate your subscription to the Samurai Service(s) and repay you, on a pro-rata basis, any subscription fees previously paid to NTT for the corresponding unused portion of the term of your subscription for such Samurai Service(s). NTT will have no liability or obligation to indemnify you with respect to any Claim if such claim is caused in whole or in part by (x) compliance with designs, data, instructions or specifications provided by you; (y) modification of the Samurai Service(s) by anyone other than NTT; or (z) the combination, operation or use of the Samurai Service(s) with other hardware or software where a Service would not by itself be infringing. The provisions of this Section 15 state the sole, exclusive and entire liability of NTT to you and constitute your sole remedy with respect to a Claim brought by reason of access to or use of a Service by you, your agents or users.Indemnification by You. You agree to defend, indemnify and hold NTT, harmless from and against any loss, liability, claim, demand, damages, costs and expenses, including reasonable attorney’s fees, arising out of or in connection with: (i) your use of and access to the NTT Service; (ii) your violation of any term of these Terms; (iii) your violation of any third party right, including without limitation any copyright, property, or privacy right or any third party agreement; (iv) any information you provide on or through the Service, or NTT’s access or use of applications or APIs (each, a “Claim”). As used in this Section 16, “you” shall include anyone accessing the Service using your password.
Conditions of Indemnification. As a condition of the foregoing indemnification obligations set forth in Sections 15 and 16: (a) the indemnified party (“Indemnified Party”) will promptly notify the indemnifying party (“Indemnifying Party”) of any Infringement Claim or Customer Indemnifiable Claim, as applicable (collectively referred to as a “Claim”), provided, however, that the failure to give such prompt notice shall not relieve the Indemnifying Party of its obligations hereunder except to the extent that the Indemnifying Party was actually and materially prejudiced by such failure; (b) the Indemnifying Party will have the sole and exclusive authority to defend or settle any such Claim (provided that, the Indemnifying Party will obtain the Indemnified Party’s consent in connection with any act or forbearance required by the Indemnified Party, which consent will not be unreasonably withheld); and (c) the Indemnified Party will reasonably cooperate with the Indemnifying Party in connection with the Indemnifying Party’s activities hereunder, at the Indemnifying Party’s expense. The Indemnified Party reserves the right, at its own expense, to participate in the defense of a Claim. Notwithstanding anything herein to the contrary, the Indemnifying Party will not settle any Claims for which it has an obligation to indemnify pursuant to this Section 17 admitting liability or fault on behalf of the Indemnified Party, nor create any obligation on behalf of the Indemnified Party without the Indemnified Party’s prior written consent.
Limitation of Damages and Remedies. IN NO EVENT SHALL NTT OR ITS LICENSORS BE LIABLE UNDER CONTRACT, TORT, STRICT LIABILITY OR OTHER LEGAL OR EQUITABLE THEORY FOR ANY INDIRECT, INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH YOUR USE OF THE NTT SERVICES, THIRD-PARTY USE OF THE NTT SERVICES ENABLED BY YOU, OR YOUR OR THIRD-PARTY USE OF ANY DATA OR SOFTWARE ENABLED BY YOU VIA THE NTT SERVICES. NTT SHALL NOT BE LIABLE FOR LOSS, INACCURACY, INCOMPLETENESS, OR RELEASE OF DATA, COST OF PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, SYSTEM DOWNTIME, GOODWILL, PROFITS OR OTHER BUSINESS LOSS, REGARDLESS OF LEGAL THEORY, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. NOTWITHSTANDING ANYTHING HEREIN TO THE CONTRARY, THE TOTAL LIABILITY OF NTT ARISING OUT OF THESE TERMS, INCLUDING BUT NOT LIMITED TO DAMAGES OR LIABILITY OF NTT ARISING OUT OF CONTRACT, TORT, BREACH OF WARRANTY, INFRINGEMENT OR OTHERWISE, SHALL NOT IN ANY EVENT EXCEED THE FEES PAID BY YOU WITH RESPECT TO THE SPECIFIC NTT SERVICE WHICH CAUSED THE CLAIM DURING THE TWELVE (12) MONTHS PRIOR TO THE FIRST EVENT OR OCCURRENCE GIVING RISE TO SUCH LIABILITY. THE PARTIES AGREE THAT THE LIMITATIONS OF THIS SECTION 18 ARE ESSENTIAL AND THAT NTT WOULD NOT PERMIT YOU TO USE THE NTT SERVICES ABSENT THE TERMS OF THIS SECTION 18. THIS SECTION 19 SHALL SURVIVE AND APPLY EVEN IF ANY REMEDY SPECIFIED IN THESE TERMS SHALL BE FOUND TO HAVE FAILED OF ITS ESSENTIAL PURPOSE. THE PROVISIONS OF THIS SECTION 18 ALLOCATE THE RISKS PURSUANT TO THESE TERMS BETWEEN THE PARTIES, AND THE PARTIES HAVE RELIED ON THE LIMITATIONS SET FORTH HEREIN IN DETERMINING WHETHER TO ENTER INTO THESE TERMS.
Export Compliance, Sanctions. You acknowledge that the NTT Services may be subject to export restrictions by the United States government and import restrictions by certain foreign governments. You shall not and shall not authorize any third-party to remove or export from the United States or allow the export or re-export of any part of the NTT Services or any direct product thereof: (i) into (or to a national or resident of) any embargoed or terrorist-supporting country; (ii) to anyone on the U.S. Commerce Department’s Table of Denial Orders or U.S. Treasury Department’s list of Specially Designated Nationals; (iii) to any country to which such export or re-export is restricted or prohibited, or as to which the United States government or any agency thereof requires an export license or other governmental approval at the time of export or re-export without first obtaining such license or approval; or (iv) otherwise in violation of any export or import restrictions, laws or regulations of any United States or foreign agency or authority. You agree to the foregoing and warrant that you are not located in, under the control of, or a national or resident of any such prohibited country or on any such prohibited party list. The NTT Services are further restricted from being used for the design or development of nuclear, chemical, or biological weapons or missile technology, or for terrorist activity, without the prior permission of the United States government. You warrant that neither you or any entity or person that has direct or indirect control of fifty percent or more of your shares are not subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”). You agree that if at any time you become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under the Terms, or the performance of the Terms exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate the NTT Services upon such Sanctions becoming effective. A breach of this Section 19 shall be a material default for the purpose of Section 11.
Ownership. NTT exclusively owns and reserves all right, title and interest in and to the NTT Services, documentation, Service Descriptions, our Confidential Information, and all anonymized or aggregated data resulting from use and operation of the NTT Services and that do not identify a natural person as the source of the information, as well as any feedback, recommendations, correction requests, or suggestions from you or any End User about the Services (“Contributions”).
Suggestions and Contributions. If you submit suggestions or contributions (“Contributions”) you agree that: (a) NTT is not under any obligation of confidentiality with respect to your Contributions; (b) NTT may use or disclose (or choose not to use or disclose) your Contributions for any purpose and in any way; (c) NTT will own your Contributions; and (d) you are not entitled to any compensation or reimbursement of any kind from NTT under any circumstances for your Contributions.
Additional Terms. Your use of the NTT Services, and associated software are subject to the NTT Privacy Policy, Cookie Statement and Data Processing Agreement. To the extent your use of the NTT Service allows you to use the associated software, or you otherwise access and use the NTT software, such access and use shall be subject to the Software Terms of Use.
Data Protection. The terms of the Data Processing Agreement shall apply when personal data is being processed pursuant to these Terms. Additionally, personal data may be disclosed in accordance with the Privacy Policy. You acknowledge that you have read the Privacy Policy and understand that it sets forth how NTT will collect, store, use and disclose your data including personal data. If you do not agree with our Privacy Policy, then you must stop using the NTT Service immediately.
Survival. Upon termination of these Terms, your payment obligations, the terms of this Section 24, and the terms of the following Sections will survive (i.e. still apply): Section 13 (Confidentiality), Section 14 Warranty Disclaimer, Section 15 (Indemnification by NTT), Section 16 (Indemnification by You), Section 17 (Conditions of Indemnification), Section 18 (Limitation of Damages and Remedies), Section 20 (Ownership), Section 24 (Survival), Section 25 (Governing Law), and Section 27 (Agreement to Arbitration).
Governing Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
Venue. Except as provided in Section 27 (Agreement to Arbitration), any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in the applicable courts of Stockholm, Sweden, and we each consent to the personal jurisdiction of these courts.
Agreement to Arbitration. Except for a disputes relating to you, your affiliates’, NTT or NTT’s affiliates’ intellectual property (e.g., trademarks, trade dress, domain names, trade secrets, copyrights or patents) (the “Excepted Disputes”) the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute resolution. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty-day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
Beta Test. NTT may, directly or through a reseller, invite you to participate in a beta test program. If you are invited by NTT to participate in a beta test of certain Samurai Services features (“Beta Program”), your usage of the subject Samurai Services features will be subject to these Terms of Service and NTT’s additional beta program terms . In the event of a conflict between these Terms of Service and the Beta Program Terms, the Beta Program Terms will take precedence. IN A BETA, THE SERVICE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT.
Service True-Up. NTT reserves the right to review the number of endpoints you have onboarded to the Samurai Service and, should that number exceed the number your subscription includes, to adjust (“True-Up”) your service charges to reflect the number onboarded as of the date of the review revealing the excess endpoints (“True-Up Date”). The revised service charge will be applied from the True-Up Date and reflected in your next billing point and for the remainder of your service term or until a further change to the number of endpoints onboarded is made. The service is designed with a log volume allowance of 5GB per endpoint per month. If your log volumes exceed this allowance NTT reserves the right to True-Up your service charge by the number of endpoints needed to cover the excess log volume.
Marketing. Each Party agrees that the use of the other Party’s trademarks, service marks, and/or logos shall be subject the other Party’s prior consent.
Miscellaneous. Neither these Terms nor the licenses granted hereunder are assignable or transferable by you (and any attempt to do so shall be void). NTT may freely assign, delegate, license and/or transfer these Terms , in whole or in part, to an affiliate upon written notice to you.. For purposes of this provision regarding assignment by NTT, “affiliate” shall mean any entity controlling, controlled by or under common control with NTT. You and NTT are independent contractors in the performance of each and every part of these Terms. Nothing in these Terms is intended to create or shall be construed as creating an employer-employee relationship or a partnership, agency, joint venture, or franchise. Subject to the foregoing, the provisions hereof are for the benefit of the parties only and not for any other person or entity. Any notice, report, approval, authorization, agreement or consent required or permitted hereunder shall be in writing; notices shall be sent to the address the applicable party has or may provide by written notice or, if there is no such address, the most recent address the party giving notice can locate using reasonable efforts. No failure or delay in exercising any right hereunder will operate as a waiver thereof, nor will any partial exercise of any right or power hereunder preclude further exercise. If any provision shall be adjudged by any court of competent jurisdiction to be unenforceable or invalid, that provision shall be limited or eliminated to the minimum extent necessary so that these Terms shall otherwise remain in full force and effect and enforceable. This is the complete and exclusive statement of the mutual understanding of the parties with respect to the license granted herein and supersedes and cancels all previous written and oral agreements and communications relating to such license and any waivers or amendments shall be effective only if executed in writing by NTT; however, any pre-printed or standard terms of any purchase order, confirmation, or similar form, unless signed by NTT after the effectiveness hereof, shall have no force or effect. You are responsible for the information you provide or make available to the NTT Services and you must ensure it is accurate, not misleading and does not contain material that is obscene, defamatory, or infringing on any rights of any third party; does not contain malicious code and is not otherwise legally actionable. The substantially prevailing party in any action to enforce these Terms will be entitled to recover its attorney’s fees and costs in connection with such action. Except as described in Section 27 (Agreement to Arbitrate), if any provision of these Terms is held by a court or other tribunal of competent jurisdiction to be unenforceable, that provision will be limited or eliminated to the minimum extent necessary to make it enforceable and, in any event, the rest of these Terms will continue in full force and effect. NTT’s failure to enforce at any time any provision of these Terms, or any other of your obligations does not waive our right to do so later. And, if we do expressly waive any provision of these Terms, or any of your other obligations, that does not mean it is waived for all time in the future. Any waiver must be in writing and signed by NTT and you to be legally binding. No failure, delay or default in performance of any obligation of a party shall constitute an event of default or breach of these Terms to the extent that such failure to perform, delay or default arises out of a cause, existing or future, that is beyond the control and without negligence of such party, including action or inaction of governmental, civil or military authority; fire; strike, lockout or other labor dispute; flood, terrorist act; war; riot; theft; earthquake and other natural disaster. The party affected by such cause shall take all reasonable actions to minimize the consequences of any such cause. In the event of a conflict between a provision of these Terms and the provisions of an Order subject to these Terms, the provision of the Order will control.
5.4.6.3 - Terms of Service (v3.0 2025-06-11)
This document has been superseded. For the latest version please click HERE.
These NTT Security Holdings Corporation (“NTT”) Terms of Service (these “Terms”) apply to your purchase of NTT’s Samurai Managed Detection and Response service, related managed services and applicable documentation and applicable Service Descriptions (“Samurai Services”), and consulting services and applicable Service Descriptions (“Consulting Services”, and together with Samurai Services, the “NTT Services”) directly from NTT or through any of NTT’s authorized resellers as identified in the quote, order form or online ordering document applicable to the NTT Services (the “Order”). The Service Descriptions for the Samurai Services and Consulting Service are found here. The purpose of these Terms is to establish the terms and conditions under which you will access, use and receive NTT Services as described in the “Order”. These Terms shall take precedence over any other agreements, contracts or general terms that Customer may have entered into with a reseller as it relates to the NTT Services only. An Order is an integral part of these Terms and is fully incorporated herein.
These Terms are solely between NTT and you; any third party to whose services the NTT Services may allow connection is not a party to these Terms. Separate license terms apply to your use of such third-party services.
To be eligible to register for a customer account in order to use or receive the NTT Services, you must review and accept these Terms by clicking on the “I Accept” or “Get Started” button or other mechanism provided. If you are accepting these Terms on behalf of a company or other legal entity, you represent and warrant that you have the authority to bind that company or other legal entity to these Terms, and, in such event, “you” and “your”, whether or not capitalised, will refer to that company or other legal entity. You and NTT may be referred to as a “Party” or, together, as the “Parties”.
The NTT Services are subject to these Terms, the related documentation and Service Descriptions, and any applicable Order submitted by you and expressly accepted by NTT. All documentation related to these Terms can be found here.
You acknowledge and agree that you have read, understood and agreed to these terms. If you do not agree with all the terms, conditions and limitations of these terms, you should not click the “I Accept” or “Get Started” button and you are not authorized to receive the NTT services. Written approval by NTT is not a prerequisite to the validity or enforceability of these terms and no solicitation of any such written approval by or on behalf of NTT shall be construed as an inference to the contrary. Acceptance by NTT is expressly conditional on your assent to these terms to the exclusion of all other terms; if these terms are considered an offer by NTT, acceptance is expressly limited to these terms.
Important note: these terms limit our liability to you. For more details, go to Section 18.
In addition, disputes related to terms or related to your use of the services generally must be resolved by a dispute resolution process which may lead to binding arbitration. For more details, go to Sections 25 and 27.
Changes to These Terms. NTT may update these Terms from time to time by providing you with prior written notice of material updates at least thirty (30) days in advance of the effective date. Notice will be given in your account portal or via an email to the email address of the owner of your account. This notice will highlight the intended updates. Except as otherwise specified by NTT, updates will be effective upon the effective date indicated at the top of these Terms of Service. The updated version of these Terms will supersede all prior versions. Following such notice, your continued access or use of the NTT Services on or after the effective date of the changes to the Terms constitutes your acceptance of any updates. If you do not agree to any updates, you should stop using the NTT Services. If you cease using the NTT Services for this reason you will receive a refund of the unused portion of subscription fees paid in advance. Every user will be required to accept the Software Terms of Use upon first login. You are required to accept these Terms before using the Service and upon changes to these Terms.
Your Account: Login. To access, use, or receive, the NTT Services or related software, you will be asked to create a customer account. As part of the account creation process, you’ll be asked to provide your email address, create a password, and verify that you’re a human being by providing a telephone number to which we’ll send you a verification code to enter into a form. When registering for an account, you must provide true, accurate, current, and complete information, about yourself as requested during the account creation process. You must keep that information true, accurate, current, and complete, after you create each account.
Your Responsibility. You are solely responsible for all access, use, and receipt, (whether or not authorized) of the NTT Services under your customer account(s) and for all acts and omissions of you or anyone to whom you provide access to or otherwise permit to use or receive the NTT Service (“Users”). You agree to take all reasonable precautions to prevent unauthorized access to or use of the NTT Service and will notify us promptly of any unauthorized access or use. We will not be liable for any loss or damage arising from unauthorized use of your custoData Protection.mer account(s). You will be solely responsible, at your own expense, for acquiring, installing and maintaining all hardware, software and other equipment as may be necessary for you to connect to, access, use or receive the NTT Services.
Access to Services. During the term and subject to and conditioned on your payment of applicable fees and compliance with all the terms and conditions of these Terms, NTT will make the NTT Service available to you in accordance with these Terms, the applicable documentation and Service Descriptions, and any applicable Order, on a limited, non-exclusive and non-transferable basis, for use, access and receipt by you, limited to, in the case of Samurai Services, the number of Users for whom access to the NTT Services has been purchased.
Restrictions and Unauthorized Use. You shall not (and shall not authorize any third party to): (i) decompile, disassemble, or otherwise reverse-engineer the NTT Services or attempt to reconstruct or discover any source code, underlying ideas, algorithms, file formats or programming interfaces of the NTT Services by any means whatsoever; (ii) sell, sublicense, rent, loan, lease, distribute, market, or commercialize the NTT Services for any purpose, including timesharing or service bureau purposes; (iii) remove any product identification, proprietary, copyright or other notices contained in the NTT Services; (iv) modify or create a derivative work of any part of the NTT Services, or incorporate the NTT Services into or with other products or software not contemplated by these Terms or the documentation (v) use the NTT Services for any competitive purpose or publicly disseminate performance information or analysis (including, without limitation, benchmarks) from any source relating to the NTT Services, or (vi) except for back-up purposes, copy or otherwise reproduce the NTT Services. Further, you will not use the NTT Services in any manner that violates any applicable law. NTT reserves the right to refuse any User access to the NTT Services without notice for any reason, including but not limited to a violation of these Terms. If you violate these Terms NTT reserves the right to issue you a warning regarding the violation or immediately suspend or terminate any or all accounts you have created using the NTT Services.
Applications and APIs. In some cases, it may be necessary for you to grant NTT access to an API or an Application which NTT is required to access in order to provide the NTT Services. You hereby grant NTT the right to access, use, assess and test the application(s) and/or application programming interface(s) (“API(s)”) in connection with providing NTT Services. You acknowledge and agree that NTT’s access and use of the application(s) and/or API(s) to provide NTT Services, is not subject to any “Terms of Use” or other terms or conditions that may be posted on, linked or otherwise provided with, the application(s) and/or API(s). You represent that you are either the owner of the application(s) and/or API(s) or have the authority to permit NTT to provide NTT Services in connection with such applications and/or API(s). You shall provide NTT adequate written evidence thereof upon NTT’s In the event any of the applications and/or API(s) are subject to third-party rights, you shall defend, indemnify and hold harmless NTT for any claims against NTT that arise from NTT accessing or using such applications and/or APIs to provide NTT Services.
Reservation of Rights. Each party reserves all rights not expressly granted in these Terms and no licenses are granted by either party to the other party under these Terms except as expressly stated in an Order, whether by implication, estoppel or otherwise. NTT or its licensors own and retain all right, title and interest (including all intellectual property rights) in and to the NTT Services, documentation and associated software, as applicable, including any modifications or improvements thereof, and applicable Service Descriptions.
Third-Party Services. We may use third-party services to help us provide the NTT Services, but such use does not indicate that we endorse the third-party or the third-party services, or applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services. Privacy Policy applicable to the corresponding third party or third-party service. We are not responsible for nor do we endorse these third-party websites or the organizations sponsoring such third-party websites or their products or services, whether or not we are affiliated with such third-party websites. You agree that we are not responsible or liable for any loss or damage of any sort incurred as a result of any such dealings you may have on or through a third-party website or as a result of the presence of any third-party advertising on the NTT Services.
Modification by NTT. Without materially degrading the Service, NTT reserves the right to modify, enhance, or otherwise change, the NTT Services (or any part thereof), including the Service Description, with or without notice.
Taxes. Unless otherwise stated, the fees do not include taxes, levies,
or similar governmental assessments, including value-added, sales, use or withholding taxes assessable by any local, state, provincial or foreign jurisdiction (“Taxes”). You are responsible for paying Taxes assessed in connection with your subscription to the NTT Services except those assessable against NTT or the reseller measured by its net income. You will be invoiced for such Taxes if NTT or the reseller believe it has a legal obligation to do so. You agree to pay such Taxes if so invoiced.Term, Termination. The term for the NTT Services is as specified in the applicable Order for the NTT Service. Unless otherwise specified at the time of purchase, Samurai Services will automatically renew for like term unless a Party provides thirty (30) days prior notice of nonrenewal. Either Party may terminate these Terms or an Order subject hereto upon thirty (30) days written notice to the other Party (the “Notice Period”) in the event of a material breach that the other Party fails to cure within the Notice Period. Further, except in any case where the Order specifies the Samurai Services are subject to a minimum term, you may i) terminate your account or cancel the Samurai Services without cause at any time and for any reason, or for no reason, and ii) receive a refund of the unamortized portion of the prepaid fee for the terminated Samurai Services. Where the Order specifies the Samurai Services are subject to a minimum term, you will have no right to terminate the Samurai Services without cause during the minimum term or any renewal term, or receive a refund of prepaid fees. You acknowledge that you may, as the result of a termination, lose your account and all information and data associated therewith and you shall not be entitled to compensation for any such loss.
Updates, Support. Any updates or support services or service level agreements for the NTT Services will be provided as stipulated in the NTT Support Policy.
Confidential Information. Both Parties acknowledge that they may obtain information relating to the each other’s services or businesses that has not been released to the public, including, but not limited to, code, technology, know-how, ideas, algorithms, testing procedures, structure, interfaces, specifications, documentation, bugs, problem reports, analysis and performance information, and other technical, business, product, and data (“Confidential Information”). A Party shall not disclose Confidential Information to any third party or use Confidential Information for any purpose other than the use of the NTT Services as licensed under these Terms or other purposes for which the Information has been provided. Each Party agrees to use the same degree of care that it uses to protect the confidentiality of its own confidential information of like kind and, in any case, at least a reasonable degree of care. Each Party acknowledges and agrees that no adequate remedy may exist at law for an actual or threatened breach of this Section 14 and that, in the event of an actual or threatened breach of the provisions of this Section 14, the non-breaching party will be entitled to seek immediate injunctive and other equitable relief, without waiving any other rights or remedies available to it.
Warranty Disclaimer. THE NTT SERVICES, THE DOCUMENTATION AND SERVICE DESCRIPTIONS ARE PROVIDED “AS IS” AND “AS AVAILABLE” WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT. YOUR USE OF THE NTT SERVICES IS AT YOUR SOLE RISK. IN ADDITION, WHILE NTT ATTEMPTS TO PROVIDE A GOOD USER EXPERIENCE, WE CANNOT AND DO NOT REPRESENT OR WARRANT THAT THE NTT SERVICES WILL ALWAYS BE SECURE OR ERROR-FREE OR THAT THE NTT SERVICES WILL ALWAYS FUNCTION WITHOUT DELAYS, DISRUPTIONS, OR IMPERFECTIONS. THE FOREGOING DISCLAIMERS SHALL APPLY TO THE EXTENT PERMITTED BY APPLICABLE LAW.
Indemnification by NTT. NTT will indemnify and defend you from and against any claim brought by a third party against you by reason of your use of a Samurai Service, as permitted hereunder, alleging that such Samurai Service infringes or misappropriates a third party’s valid patent, copyright,
or trade secret (a “Claim”). NTT shall, at its expense, defend such IP Claim and pay damages finally awarded against you in connection therewith, including the reasonable fees and expenses of the attorneys engaged by NTT for such defense, provided that (a) you promptly notify NTT of the threat or notice of such IP Claim; (b) NTT will have the sole and exclusive control and authority to select defense attorneys, and defend and/or settle any such IP Claim (however, NTT shall not settle or compromise any claim that results in liability or admission of any liability by you without your prior written consent); and (c) you fully cooperate with NTT in connection therewith. If use of a Service by you, your agents or users has become, or, in NTT’s opinion, is likely to become, the subject of any such Claim, NTT may, at NTT’s option and expense, (i) procure for you the right to continue using the Samurai Service(s) as set forth hereunder; (ii) replace or modify a Service to make it non-infringing; or (iii) if options (i) or (ii) are not commercially reasonable or practicable as determined by NTT, terminate your subscription to the Samurai Service(s) and repay you, on a pro-rata basis, any subscription fees previously paid to NTT for the corresponding unused portion of the term of your subscription for such Samurai Service(s). NTT will have no liability or obligation to indemnify you with respect to any Claim if such claim is caused in whole or in part by (x) compliance with designs, data, instructions or specifications provided by you; (y) modification of the Samurai Service(s) by anyone other than NTT; or (z) the combination, operation or use of the Samurai Service(s) with other hardware or software where a Service would not by itself be infringing. The provisions of this Section 15 state the sole, exclusive and entire liability of NTT to you and constitute your sole remedy with respect to a Claim brought by reason of access to or use of a Service by you, your agents or users.Indemnification by You. You agree to defend, indemnify and hold NTT, harmless from and against any loss, liability, claim, demand, damages, costs and expenses, including reasonable attorney’s fees, arising out of or in connection with: (i) your use of and access to the NTT Service; (ii) your violation of any term of these Terms; (iii) your violation of any third party right, including without limitation any copyright, property, or privacy right or any third party agreement; (iv) any information you provide on or through the Service, or NTT’s access or use of applications or APIs (each, a “Claim”). As used in this Section 16, “you” shall include anyone accessing the Service using your password.
Conditions of Indemnification. As a condition of the foregoing indemnification obligations set forth in Sections 15 and 16: (a) the indemnified party (“Indemnified Party”) will promptly notify the indemnifying party (“Indemnifying Party”) of any Infringement Claim or Customer Indemnifiable Claim, as applicable (collectively referred to as a “Claim”), provided, however, that the failure to give such prompt notice shall not relieve the Indemnifying Party of its obligations hereunder except to the extent that the Indemnifying Party was actually and materially prejudiced by such failure; (b) the Indemnifying Party will have the sole and exclusive authority to defend or settle any such Claim (provided that, the Indemnifying Party will obtain the Indemnified Party’s consent in connection with any act or forbearance required by the Indemnified Party, which consent will not be unreasonably withheld); and (c) the Indemnified Party will reasonably cooperate with the Indemnifying Party in connection with the Indemnifying Party’s activities hereunder, at the Indemnifying Party’s expense. The Indemnified Party reserves the right, at its own expense, to participate in the defense of a Claim. Notwithstanding anything herein to the contrary, the Indemnifying Party will not settle any Claims for which it has an obligation to indemnify pursuant to this Section 17 admitting liability or fault on behalf of the Indemnified Party, nor create any obligation on behalf of the Indemnified Party without the Indemnified Party’s prior written consent.
Limitation of Damages and Remedies. IN NO EVENT SHALL NTT OR ITS LICENSORS BE LIABLE UNDER CONTRACT, TORT, STRICT LIABILITY OR OTHER LEGAL OR EQUITABLE THEORY FOR ANY INDIRECT, INCIDENTAL, SPECIAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH YOUR USE OF THE NTT SERVICES, THIRD-PARTY USE OF THE NTT SERVICES ENABLED BY YOU, OR YOUR OR THIRD-PARTY USE OF ANY DATA OR SOFTWARE ENABLED BY YOU VIA THE NTT SERVICES. NTT SHALL NOT BE LIABLE FOR LOSS, INACCURACY, INCOMPLETENESS, OR RELEASE OF DATA, COST OF PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES, SYSTEM DOWNTIME, GOODWILL, PROFITS OR OTHER BUSINESS LOSS, REGARDLESS OF LEGAL THEORY, EVEN IF NTT HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. NOTWITHSTANDING ANYTHING HEREIN TO THE CONTRARY, THE TOTAL LIABILITY OF NTT ARISING OUT OF THESE TERMS, INCLUDING BUT NOT LIMITED TO DAMAGES OR LIABILITY OF NTT ARISING OUT OF CONTRACT, TORT, BREACH OF WARRANTY, INFRINGEMENT OR OTHERWISE, SHALL NOT IN ANY EVENT EXCEED THE FEES PAID BY YOU WITH RESPECT TO THE SPECIFIC NTT SERVICE WHICH CAUSED THE CLAIM DURING THE TWELVE (12) MONTHS PRIOR TO THE FIRST EVENT OR OCCURRENCE GIVING RISE TO SUCH LIABILITY. THE PARTIES AGREE THAT THE LIMITATIONS OF THIS SECTION 18 ARE ESSENTIAL AND THAT NTT WOULD NOT PERMIT YOU TO USE THE NTT SERVICES ABSENT THE TERMS OF THIS SECTION 18. THIS SECTION 19 SHALL SURVIVE AND APPLY EVEN IF ANY REMEDY SPECIFIED IN THESE TERMS SHALL BE FOUND TO HAVE FAILED OF ITS ESSENTIAL PURPOSE. THE PROVISIONS OF THIS SECTION 18 ALLOCATE THE RISKS PURSUANT TO THESE TERMS BETWEEN THE PARTIES, AND THE PARTIES HAVE RELIED ON THE LIMITATIONS SET FORTH HEREIN IN DETERMINING WHETHER TO ENTER INTO THESE TERMS.
Export Compliance, Sanctions. You acknowledge that the NTT Services may be subject to export restrictions by the United States government and import restrictions by certain foreign governments. You shall not and shall not authorize any third-party to remove or export from the United States or allow the export or re-export of any part of the NTT Services or any direct product thereof: (i) into (or to a national or resident of) any embargoed or terrorist-supporting country; (ii) to anyone on the U.S. Commerce Department’s Table of Denial Orders or U.S. Treasury Department’s list of Specially Designated Nationals; (iii) to any country to which such export or re-export is restricted or prohibited, or as to which the United States government or any agency thereof requires an export license or other governmental approval at the time of export or re-export without first obtaining such license or approval; or (iv) otherwise in violation of any export or import restrictions, laws or regulations of any United States or foreign agency or authority. You agree to the foregoing and warrant that you are not located in, under the control of, or a national or resident of any such prohibited country or on any such prohibited party list. The NTT Services are further restricted from being used for the design or development of nuclear, chemical, or biological weapons or missile technology, or for terrorist activity, without the prior permission of the United States government. You warrant that neither you or any entity or person that has direct or indirect control of fifty percent or more of your shares are not subject to any economic, trade or financial sanctions or other trade restrictions administered or enforced by the United Nations, the European Union, the United Kingdom, the United States of America or any other relevant jurisdiction, including, without limitation, the EU Consolidated list of persons, groups and entities subject to EU financial sanctions, the U.S. Treasury Department Office of Foreign Assets Control list of Specially Designated Nationals and Blocked Persons or any similar list maintained by any EU member state (“Sanctions”). You agree that if at any time you become subject to any Sanctions which prohibit or restrict NTT’s performance of or rights under the Terms, or the performance of the Terms exposes NTT, or creates a risk of NTT being exposed, to any Sanctions, including, without limitation, any extraterritorial or secondary sanctions, NTT may suspend or terminate the NTT Services upon such Sanctions becoming effective. A breach of this Section 19 shall be a material default for the purpose of Section 11.
Ownership. NTT exclusively owns and reserves all right, title and interest in and to the NTT Services, documentation,Service Descriptions, our Confidential Information, and all anonymized or aggregated data resulting from use and operation of the NTT Services and that do not identify a natural person as the source of the information, as well as any feedback, recommendations, correction requests, or suggestions from you or any End User about the Services (“Contributions”).
Suggestions and Contributions. If you submit suggestions or contributions (“Contributions”) you agree that: (a) NTT is not under any obligation of confidentiality with respect to your Contributions; (b) NTT may use or disclose (or choose not to use or disclose) your Contributions for any purpose and in any way; (c) NTT will own your Contributions; and (d) you are not entitled to any compensation or reimbursement of any kind from NTT under any circumstances for your Contributions.
Additional Terms. Your use of the NTT Services, and associated software are subject to the NTT Privacy Policy,Cookie Statement and Data Processing Agreement. To the extent your use of the NTT Service allows you to use the associated software, or you otherwise access and use the NTT software, such access and use shall be subject to the Software Terms of Use.
Data Protection. The terms of the Data Processing Agreement shall apply when personal data is being processed pursuant to these Terms. Additionally, personal data may be disclosed in accordance with the Privacy Policy. You acknowledge that you have read the Privacy Policy and understand that it sets forth how NTT will collect, store, use and disclose your data including personal data. If you do not agree with our Privacy Policy, then you must stop using the NTT Service immediately.
Survival. Upon termination of these Terms, your payment obligations, the terms of this Section 24, and the terms of the following Sections will survive (i.e. still apply): Section 13 (Confidentiality), Section 14 Warranty Disclaimer, Section 15 (Indemnification by NTT), Section 16 (Indemnification by You), Section 17 (Conditions of Indemnification), Section 18 (Limitation of Damages and Remedies), Section 20 (Ownership), Section 24 (Survival), Section 25 (Governing Law), and Section 27 (Agreement to Arbitration).
Governing Law. This Agreement shall be governed in all respects by the laws of Sweden, without regard to its choice of law rules. Application of the U.N. Convention of Contracts for the International Sale of Goods is expressly excluded.
Venue. Except as provided in Section 27 (Agreement to Arbitration), any legal suit, action or proceeding arising out of or related to these Terms or the NTT Services shall be instituted in the applicable courts of Stockholm, Sweden, and we each consent to the personal jurisdiction of these courts.
Agreement to Arbitration. Except for a disputes relating to you, your affiliates’, NTT or NTT’s affiliates’ intellectual property (e.g., trademarks, trade dress, domain names, trade secrets, copyrights or patents) (the “Excepted Disputes”) the parties agree that as a condition precedent to the institution of any action regarding disputes arising under or in connection with this Agreement all such disputes shall first be submitted to mediation before a professional mediator selected by the parties. Such mediation shall be conducted at a mutually agreed time and place, shall not be less than two days in length, and the costs and expenses of the mediation, including but not limited to the mediator’s fees, shall be split equally between the parties. The parties agree that they will participate in the mediation in good faith. The parties further agree that any and all disputes, claims or controversies arising out of or relating to this Agreement that are not resolved by mutual agreement in mediation within sixty days of the request of a party for such a mediation, shall be submitted to binding arbitration to be held in[ Stockholm, Sweden, in accordance with the then-current rules of the Arbitration Institute of the Stockholm Chamber of Commerce (the “Rules’). One arbitrator shall be selected in accordance with the Rules; provided, any arbitrator shall be independent, impartial arbiter with at least ten years of experience in the area of dispute resolution. If a mediation process is not established or one party fails to agree on a mediation process or fails to participate in the mediation as agreed herein, the other party can commence arbitration prior to the expiration of the sixty-day period. The decision of the arbitrator shall be final, conclusive and binding on the parties to the arbitration. Judgment may be entered on the arbitrator’s decision in any court of competent jurisdiction. The parties shall share equally in the costs of the arbitration. In any suit or arbitration to enforce any right or remedy under this Agreement or to interpret any provision of this Agreement, the prevailing party will be entitled to recover its costs, including reasonable attorneys’ fees, including without limitation, costs and fees incurred on appeal or in a bankruptcy or similar action; provided, however, that prior to the initiation of such suit or arbitration the prevailing party participated in good faith in mediation as set forth above or offered in good faith to participate in mediation and the other party refused or failed to participate in such mediation proceedings.
Beta Test. NTT may, directly or through a reseller, invite you to participate in a beta test program. If you are invited by NTT to participate in a beta test of certain Samurai Services features (“Beta Program”), your usage of the subject Samurai Services features will be subject to these Terms of Service and NTT’s additional beta program terms. In the event of a conflict between these Terms of Service and the Beta Program Terms, the Beta Program Terms will take precedence. IN A BETA, THE SERVICE IS PROVIDED “AS IS, WHERE IS” WITH NO WARRANTY OF ANY KIND. NTT MAKES NO OTHER WARRANTY, EXPRESS OR IMPLIED AND ALL OTHER WARRANTIES ARE HEREBY DISCLAIMED, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, AND NON-INFRINGEMENT.
Service True-Up. NTT reserves the right to review the number of endpoints you have onboarded to the Samurai Service and, should that number exceed the number your subscription includes, to adjust (“True-Up”) your service charges to reflect the number onboarded as of the date of the review revealing the excess endpoints (“True-Up Date”). The revised service charge will be applied from the True-Up Date and reflected in your next billing point and for the remainder of your service term or until a further change to the number of endpoints onboarded is made. The service is designed with a log volume allowance of 5GB per endpoint per month. If your log volumes exceed this allowance NTT reserves the right to True-Up your service charge by the number of endpoints needed to cover the excess log volume.
Proof of Value. NTT may, but is not obligated to, offer you a Samurai MDR Proof of Value (POV) subscription as described in the Samurai MDR Service Description. The offer will be made by delivery of a quote. Commencing on acceptance of the quote, you will be entitled to use the Samurai MDR Service for a maximum of 90 days at the reduced price stated in the quote. There is no option to extend or renew the POV subscription. The fee paid for the POV subscription is non-refundable. At any time during the term of the POV subscription and upon notice to NTT you may elect to terminate the POV subscription without further obligation or convert it to a full commercial Samurai MDR subscription. If you choose to convert to a full commercial Samurai MDR subscription you will receive a quote from NTT. Upon acceptance of the quote the POV subscription will end, the full Samurai MDR subscription will commence, and you will a receive a coupon for value equal to the POV subscription fee which you may redeem solely for the purchase of NTT Services. The coupon has no cash value. If you elect to terminate your POV subscription, or upon its expiration, the Samurai tenant and all data, logs, and configurations associated with your account and the Samurai tenant itself will be irrevocably deleted.
Payment for Services. NTT will bill and you agree to pay, (i) for Samurai Services a subscription fee for the term in advance commencing on the subscription date, order date, or renewal date, and (ii) for Consulting Services in accordance with the order. If you choose to upgrade your subscriptions for Samurai Services during your subscription term, any incremental subscription fees associated with such upgrade will be charged in accordance with the remaining subscription term and any renewal and you will be invoiced by NTT or the reseller promptly following the date of upgrade of renewal. Payment will be due 30 days after invoice unless stated otherwise on your quotation.
Marketing. Each Party agrees that the use of the other Party’s trademarks, service marks, and/or logos shall be subject the other Party’s prior consent.
Miscellaneous. Neither these Terms nor the licenses granted hereunder are assignable or transferable by you (and any attempt to do so shall be void). NTT may freely assign, delegate, license and/or transfer these Terms , in whole or in part, to an affiliate upon written notice to you.. For purposes of this provision regarding assignment by NTT, “affiliate” shall mean any entity controlling, controlled by or under common control with NTT. You and NTT are independent contractors in the performance of each and every part of these Terms. Nothing in these Terms is intended to create or shall be construed as creating an employer-employee relationship or a partnership, agency, joint venture, or franchise. Subject to the foregoing, the provisions hereof are for the benefit of the parties only and not for any other person or entity. Any notice, report, approval, authorization, agreement or consent required or permitted hereunder shall be in writing; notices shall be sent to the address the applicable party has or may provide by written notice or, if there is no such address, the most recent address the party giving notice can locate using reasonable efforts. No failure or delay in exercising any right hereunder will operate as a waiver thereof, nor will any partial exercise of any right or power hereunder preclude further exercise. If any provision shall be adjudged by any court of competent jurisdiction to be unenforceable or invalid, that provision shall be limited or eliminated to the minimum extent necessary so that these Terms shall otherwise remain in full force and effect and enforceable. This is the complete and exclusive statement of the mutual understanding of the parties with respect to the license granted herein and supersedes and cancels all previous written and oral agreements and communications relating to such license and any waivers or amendments shall be effective only if executed in writing by NTT; however, any pre-printed or standard terms of any purchase order, confirmation, or similar form, unless signed by NTT after the effectiveness hereof, shall have no force or effect. You are responsible for the information you provide or make available to the NTT Services and you must ensure it is accurate, not misleading and does not contain material that is obscene, defamatory, or infringing on any rights of any third party; does not contain malicious code and is not otherwise legally actionable. The substantially prevailing party in any action to enforce these Terms will be entitled to recover its attorney’s fees and costs in connection with such action. Except as described in Section 27 (Agreement to Arbitrate), if any provision of these Terms is held by a court or other tribunal of competent jurisdiction to be unenforceable, that provision will be limited or eliminated to the minimum extent necessary to make it enforceable and, in any event, the rest of these Terms will continue in full force and effect. NTT’s failure to enforce at any time any provision of these Terms, or any other of your obligations does not waive our right to do so later. And, if we do expressly waive any provision of these Terms, or any of your other obligations, that does not mean it is waived for all time in the future. Any waiver must be in writing and signed by NTT and you to be legally binding. No failure, delay or default in performance of any obligation of a party shall constitute an event of default or breach of these Terms to the extent that such failure to perform, delay or default arises out of a cause, existing or future, that is beyond the control and without negligence of such party, including action or inaction of governmental, civil or military authority; fire; strike, lockout or other labor dispute; flood, terrorist act; war; riot; theft; earthquake and other natural disaster. The party affected by such cause shall take all reasonable actions to minimize the consequences of any such cause. In the event of a conflict between a provision of these Terms and the provisions of an Order subject to these Terms, the provision of the Order will control.
5.4.7 - Third Party Software Terms
5.4.7.1 - Third Party Software Terms (v1 2025-06-11)
This document has been superseded. For the latest version please click HERE.
Dated: December 2022
All rights to NTT’s software products (“NTT Software”) not expressly granted by NTT are reserved. No part of the NTT Software may be used, reproduced, modified, distributed, displayed, performed, reverse engineered or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without prior written permission of NTT, except as otherwise expressly permitted by the license terms below with respect to the applicable third party software or files.
The logos and all other trademarks, logos and service marks displayed on NTT software, products or website (“Marks”) are the property of NTT or third parties. You are not permitted to use these Marks without the prior written consent of the respective Mark owner.
Notwithstanding the foregoing, certain components of the NTT Software may be governed by additional terms or by a separate license as described below.
The following third-party software or files may be included in or distributed with the NTT Software. Some software or files require NTT to license it to you with additional terms or under separate license terms below, and in such case, those software and files are licensed to you as described below and either, as applicable, (1) with the terms below in addition to the terms of your license, subscription or other similar agreement with NTT for the applicable NTT Software, or (2) separately under the terms below and not under the terms of such agreement with NTT.
To the extent the license for any open source software requires NTT to make available to you the corresponding source code and/or modifications (the “Source Files”), you may obtain a copy of the applicable Source Files by sending a written request, with your name, address, and applicable NTT Software, including, where applicable, the version to: NTT Security Holdings Corporation c/o david.stokes@security.ntt. All requests should clearly specify: Open Source Files Request, Attention: OSS. This offer to obtain a copy of the Source Files is valid for three years from the date you acquired the NTT Software.
Host OS
- CentOS 7 See CentOS Project Licensing Policy; and GPL v2 License.
- Ubuntu20.04/22.04 See Ubuntu Intellectual Property Rights Policy; Terms and Policies
Software
- Debian: See Debian Social Contract 1.2
- Docker Engine: See Apache License V2
- Suricata: See The Suricata Open Source Manifesto. And See GPL v2 License.
- Stenographer: Copyright by Contributors. See Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- Redis: Copyright by Contributors. See BSD 3-Clause License.
- Kafka: Copyright by Contributors. See Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- Telegraf: Copyright 2015-2020 Influx Data Inc. See The MIT License.
- Prometheus: Copyright by Contributors. See Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- OpenJDK(Java): See OpenJDK Legal Documents.
- Rsyslog: See GPL v3 License.
- Fluent Bit: Copyright by Contributors. See Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- RCDCap: Copyright 2012 Zdravko Velinov. See RCDCap License Terms; GPLv3.
- Cython. Copyright by Contributors. Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- Nginx. See nginx/License at master – nginx/nginx
- Python. “Copyright © 2001-2023 Python Software Foundation. See PSF License Agreement.
- PIP. See The MIT License.
- gpg. See GPL v3 License.
- jq. See The MIT License.
- tcpstat. See BSD 2-Clause License.
- Tini. See The MIT License.
- wget. SeeGPL v3 License.
- curl. See The MIT License.
- git. See GPL v2 License.
- Expect. Public Domain – no license terms.
- iftop. See GPL v2 License.
- tshark. See GPL v2 License.
- tcpdump. See BSD 3-Clause License.
- Ca-certificates. See CentOS, Ubuntu, Debian.
- p11-kit. See BSD 3-Clause License.
- tar. See GPL v2 License.
- github.com/aleroyer/rsyslog_exporter. See Apache License, Version 2.0. This software is made available on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
- github.com/kardianos/govendor. See BSD 3-Clause License.
- github.com/michaloo/go-cron. See The MIT License.
Appendix
Certain third-party licenses are available for your review below. NTT is not responsible to you for any typographical, formatting or other errors in the licenses, whether resulting from reproduction by NTT or otherwise. You acknowledge that the licenses may be updated or amended from time to time by their sponsors, and NTT is not responsible to you for any failure to reflect any such update or amendment to the Licenses below.
Apache License v2.0
This component is licensed under the Apache License, Version 2.0 (the “License”); you may not use this file except in compliance with the License. You may obtain a copy of the License at:
TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
- Definitions.
“License” shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document.
“Licensor” shall mean the copyright owner or entity authorized by the copyright owner that is granting the License.
“Legal Entity” shall mean the union of the acting entity and all other entities that control, are controlled by, or are under common control with that entity. For the purposes of this definition, “control” means (i) the power, direct or indirect, to cause the direction or management of such entity, whether by contract or otherwise, or (ii) ownership of fifty percent (50%) or more of the outstanding shares, or (iii) beneficial ownership of such entity.
“You” (or “Your”) shall mean an individual or Legal Entity exercising permissions granted by this License.
“Source” form shall mean the preferred form for making modifications, including but not limited to software source code, documentation source, and configuration files.
“Object” form shall mean any form resulting from mechanical transformation or translation of a Source form, including but not limited to compiled object code, generated documentation, and conversions to other media types.
“Work” shall mean the work of authorship, whether in Source or Object form, made available under the License, as indicated by a copyright notice that is included in or attached to the work (an example is provided in the Appendix below).
“Derivative Works” shall mean any work, whether in Source or Object form, that is based on (or derived from) the Work and for which the editorial revisions, annotations, elaborations, or other modifications represent, as a whole, an original work of authorship. For the purposes of this License, Derivative Works shall not include works that remain separable from, or merely link (or bind by name) to the interfaces of, the Work and Derivative Works thereof.
“Contribution” shall mean any work of authorship, including the original version of the Work and any modifications or additions to that Work or Derivative Works thereof, that is intentionally submitted to Licensor for inclusion in the Work by the copyright owner or by an individual or Legal Entity authorized to submit on behalf of the copyright owner. For the purposes of this definition, “submitted” means any form of electronic, verbal, or written communication sent to the Licensor or its representatives, including but not limited to communication on electronic mailing lists, source code control systems, and issue tracking systems that are managed by, or on behalf of, the Licensor for the purpose of discussing and improving the Work, but excluding communication that is conspicuously marked or otherwise designated in writing by the copyright owner as “Not a Contribution.”
“Contributor” shall mean Licensor and any individual or Legal Entity on behalf of whom a Contribution has been received by Licensor and subsequently incorporated within the Work.
Grant of Copyright License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable copyright license to reproduce, prepare Derivative Works of, publicly display, publicly perform, sublicense, and distribute the Work and such Derivative Works in Source or Object form.
Grant of Patent License. Subject to the terms and conditions of this License, each Contributor hereby grants to You a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable (except as stated in this section) patent license to make, have made, use, offer to sell, sell, import, and otherwise transfer the Work, where such license applies only to those patent claims licensable by such Contributor that are necessarily infringed by their Contribution(s) alone or by combination of their Contribution(s) with the Work to which such Contribution(s) was submitted. If You institute patent litigation against any entity (including a cross-claim or counterclaim in a lawsuit) alleging that the Work or a Contribution incorporated within the Work constitutes direct or contributory patent infringement, then any patent licenses granted to You under this License for that Work shall terminate as of the date such litigation is filed.
Redistribution. You may reproduce and distribute copies of the Work or Derivative Works thereof in any medium, with or without modifications, and in Source or Object form, provided that You meet the following conditions:
You must give any other recipients of the Work or Derivative Works a copy of this License; and
You must cause any modified files to carry prominent notices stating that You changed the files; and
You must retain, in the Source form of any Derivative Works that You distribute, all copyright, patent, trademark, and attribution notices from the Source form of the Work, excluding those notices that do not pertain to any part of the Derivative Works; and
If the Work includes a “NOTICE” text file as part of its distribution, then any Derivative Works that You distribute must include a readable copy of the attribution notices contained within such NOTICE file, excluding those notices that do not pertain to any part of the Derivative Works, in at least one of the following places: within a NOTICE text file distributed as part of the Derivative Works; within the Source form or documentation, if provided along with the Derivative Works; or, within a display generated by the Derivative Works, if and wherever such third-party notices normally appear. The contents of the NOTICE file are for informational purposes only and do not modify the License. You may add Your own attribution notices within Derivative Works that You distribute, alongside or as an addendum to the NOTICE text from the Work, provided that such additional attribution notices cannot be construed as modifying the License.
You may add Your own copyright statement to Your modifications and may provide additional or different license terms and conditions for use, reproduction, or distribution of Your modifications, or for any such Derivative Works as a whole, provided Your use, reproduction, and distribution of the Work otherwise complies with the conditions stated in this License.
Submission of Contributions. Unless You explicitly state otherwise, any Contribution intentionally submitted for inclusion in the Work by You to the Licensor shall be under the terms and conditions of this License, without any additional terms or conditions. Notwithstanding the above, nothing herein shall supersede or modify the terms of any separate license agreement you may have executed with Licensor regarding such Contributions.
Trademarks. This License does not grant permission to use the trade names, trademarks, service marks, or product names of the Licensor, except as required for reasonable and customary use in describing the origin of the Work and reproducing the content of the NOTICE file.
Disclaimer of Warranty. Unless required by applicable law or agreed to in writing, Licensor provides the Work (and each Contributor provides its Contributions) on an “AS IS” BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. You are solely responsible for determining the appropriateness of using or redistributing the Work and assume any risks associated with Your exercise of permissions under this License.
Limitation of Liability. In no event and under no legal theory, whether in tort (including negligence), contract, or otherwise, unless required by applicable law (such as deliberate and grossly negligent acts) or agreed to in writing, shall any Contributor be liable to You for damages, including any direct, indirect, special, incidental, or consequential damages of any character arising as a result of this License or out of the use or inability to use the Work (including but not limited to damages for loss of goodwill, work stoppage, computer failure or malfunction, or any and all other commercial damages or losses), even if such Contributor has been advised of the possibility of such damages.
Accepting Warranty or Additional Liability. While redistributing the Work or Derivative Works thereof, You may choose to offer, and charge a fee for, acceptance of support, warranty, indemnity, or other liability obligations and/or rights consistent with this License. However, in accepting such obligations, You may act only on Your own behalf and on Your sole responsibility, not on behalf of any other Contributor, and only if You agree to indemnify, defend, and hold each Contributor harmless for any liability incurred by, or claims asserted against, such Contributor by reason of your accepting any such warranty or additional liability.
##Runtime Library Exception to the Apache License 2.0##
As an exception, if you use this Software to compile your source code and portions of this Software are embedded into the binary products as a result, you may redistribute such product without providing attribution as would otherwise be required by Sections 4(a), 4(b) and 4(d) of the License.
BSD 2-Clause Plus Patent License
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
Subject to the terms and conditions of this license, each copyright holder and contributor hereby grants to those receiving rights under this license a perpetual, worldwide, non-exclusive, no-charge, royalty-free, irrevocable (except for failure to satisfy the conditions of this license) patent license to make, have made, use, offer to sell, sell, import, and otherwise transfer this software, where such license applies only to those patent claims, already acquired or hereafter acquired, licensable by such copyright holder or contributor that are necessarily infringed by:
(a) their Contribution(s) (the licensed copyrights of copyright holders and non-copyrightable additions of contributors, in source or binary form) alone; or
(b) combination of their Contribution(s) with the work of authorship to which such Contribution(s) was added by such copyright holder or contributor, if, at the time the Contribution is added, such addition causes such combination to be necessarily infringed. The patent license shall not apply to any other combinations which include the Contribution.
Except as expressly stated above, no rights or licenses from any copyright holder or contributor is granted under this license, whether expressly, by implication, estoppel or otherwise.
DISCLAIMER
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDERS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
BSD 3-Clause “New” or “Revised” License
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1.Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
2.Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3.Neither the name of the copyright holder nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
GPL v2.0
GNU GENERAL PUBLIC LICENSE
Version 2, June 1991
Copyright (C) 1989, 1991 Free Software Foundation, Inc.
59 Temple Place - Suite 330, Boston, MA 02111-1307, USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public License is intended to guarantee your freedom to share and change free software to make sure the software is free for all its users. This General Public License applies to most of the Free Software Foundation’s software and to any other program whose authors commit to using it. (Some other Free Software Foundation software is covered by the GNU Library General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish), that you receive source code or can get it if you want it, that you can change the software or use pieces of it in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights.
We protect your rights with two steps: (1) copyright the software, and (2) offer you this license which gives you legal permission to copy, distribute and/or modify the software.
Also, for each author’s protection and ours, we want to make certain that everyone understands that there is no warranty for this free software. If the software is modified by someone else and passed on, we want its recipients to know that what they have is not the original, so that any problems introduced by others will not reflect on the original authors’ reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that redistributors of a free program will individually obtain patent licenses, in effect making the program proprietary. To prevent this, we have made it clear that any patent must be licensed for everyone’s free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
- This License applies to any program or other work which contains a notice placed by the copyright holder saying it may be distributed under the terms of this General Public License. The “Program”, below, refers to any such program or work, and a “work based on the Program” means either the Program or any derivative work under copyright law: that is to say, a work containing the Program or a portion of it, either verbatim or with modifications and/or translated into another language. (Hereinafter, translation is included without limitation in the term “modification”.) Each licensee is addressed as “you”.
Activities other than copying, distribution and modification are not covered by this License; they are outside its scope. The act of running the Program is not restricted, and the output from the Program is covered only if its contents constitute a work based on the Program (independent of having been made by running the Program). Whether that is true depends on what the Program does.
- You may copy and distribute verbatim copies of the Program’s source code as you receive it, in any medium, provided that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to this License and to the absence of any warranty; and give any other recipients of the Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty protection in exchange for a fee.
- You may modify your copy or copies of the Program or any portion of it, thus forming a work based on the Program, and copy and distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is derived from the Program or any part thereof, to be licensed as a whole at no charge to all third parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it, when started running for such interactive use in the most ordinary way, to print or display an announcement including an appropriate copyright notice and a notice that there is no warranty (or else, saying that you provide a warranty) and that users may redistribute the program under these conditions, and telling the user how to view a copy of this License. (Exception: if the Program itself is interactive but does not normally print such an announcement, your work based on the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the Program, and can be reasonably considered independent and separate works in themselves, then this License, and its terms, do not apply to those sections when you distribute them as separate works. But when you distribute the same sections as part of a whole which is a work based on the Program, the distribution of the whole must be on the terms of this License, whose permissions for other licensees extend to the entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with a work based on the Program) on a volume of a storage or distribution medium does not bring the other work under the scope of this License.
- You may copy and distribute the Program (or a work based on it, under Section 2) in object code or executable form under the terms of Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which must be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than your cost of physically performing source distribution, a complete machine-readable copy of the corresponding source code, to be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding source code. (This alternative is allowed only for noncommercial distribution and only if you received the program in object code or executable form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it. For an executable work, complete source code means all the source code for all modules it contains, plus any associated interface definition files, plus the scripts used to control compilation and installation of the executable. However, as a special exception, the source code distributed need not include anything that is normally distributed (in either source or binary form) with the major components (compiler, kernel, and so on) of the operating system on which the executable runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated place, then offering equivalent access to copy the source code from the same place counts as distribution of the source code, even though third parties are not compelled to copy the source along with the object code.
You may not copy, modify, sublicense, or distribute the Program except as expressly provided under this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program is void, and will automatically terminate your rights under this License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated so long as such parties remain in full compliance.
You are not required to accept this License, since you have not signed it. However, nothing else grants you permission to modify or distribute the Program or its derivative works. These actions are prohibited by law if you do not accept this License. Therefore, by modifying or distributing the Program (or any work based on the Program), you indicate your acceptance of this License to do so, and all its terms and conditions for copying, distributing or modifying the Program or works based on it.
Each time you redistribute the Program (or any work based on the Program), the recipient automatically receives a license from the original licensor to copy, distribute or modify the Program subject to these terms and conditions. You may not impose any further restrictions on the recipients’ exercise of the rights granted herein. You are not responsible for enforcing compliance by third parties to this License.
If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to patent issues), conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License, they do not excuse you from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your obligations under this License and any other pertinent obligations, then as a consequence you may not distribute the Program at all. For example, if a patent license would not permit royalty-free redistribution of the Program by all those who receive copies directly or indirectly through you, then the only way you could satisfy both it and this License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the section is intended to apply and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to contest validity of any such claims; this section has the sole purpose of protecting the integrity of the free software distribution system, which is implemented by public license practices. Many people have made generous contributions to the wide range of software distributed through that system in reliance on consistent application of that system; it is up to the author/donor to decide if he or she is willing to distribute software through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of this License.
If the distribution and/or use of the Program is restricted in certain countries either by patents or by copyrighted interfaces, the original copyright holder who places the Program under this License may add an explicit geographical distribution limitation excluding those countries, so that distribution is permitted only in or among countries not thus excluded. In such case, this License incorporates the limitation as if written in the body of this License.
The Free Software Foundation may publish revised and/or new versions of the General Public License from time to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of this License which applies to it and “any later version”, you have the option of following the terms and conditions either of that version or of any later version published by the Free Software Foundation. If the Program does not specify a version number of this License, you may choose any version ever published by the Free Software Foundation.
- If you wish to incorporate parts of the Program into other free programs whose distribution conditions are different, write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation, write to the Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the free status of all derivatives of our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END OF TERMS AND CONDITIONS
How to Apply These Terms to Your New Programs
If you develop a new program, and you want it to be of the greatest possible use to the public, the best way to achieve this is to make it free software which everyone can redistribute and change under these terms.
To do so, attach the following notices to the program. It is safest to attach them to the start of each source file to most effectively convey the exclusion of warranty; and each file should have at least the “copyright” line and a pointer to where the full notice is found.
one line to give the program’s name and an idea of what it does. Copyright (C) yyyy name of author
This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details.
You should have received a copy of the GNU General Public License along with this program; if not, write to the Free Software Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA.
Also add information on how to contact you by electronic and paper mail.
If the program is interactive, make it output a short notice like this when it starts in an interactive mode:
Gnomovision version 69, Copyright (C) year name of author Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type ‘show w’. This is free software, and you are welcome to redistribute it under certain conditions; type ‘show c’ for details.
The hypothetical commands ‘show w’ and ‘show c’ should show the appropriate parts of the General Public License. Of course, the commands you use may be called something other than ‘show w’ and ‘show c’; they could even be mouse-clicks or menu items whatever suits your program.
You should also get your employer (if you work as a programmer) or your school, if any, to sign a “copyright disclaimer” for the program, if necessary. Here is a sample; alter the names:
Yoyodyne, Inc., hereby disclaims all copyright interest in the program ‘Gnomovision’ (which makes passes at compilers) written by James Hacker.
signature of Ty Coon, 1 April 1989
MIT License
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the “Software”), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED “AS IS”, WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
PSF LICENSE AGREEMENT
- This LICENSE AGREEMENT is between the Python Software Foundation (“PSF”), and
the Individual or Organization (“Licensee”) accessing and otherwise using Python
3.11.2 software in source or binary form and its associated documentation.
- Subject to the terms and conditions of this License Agreement, PSF hereby
grants Licensee a nonexclusive, royalty-free, world-wide license to reproduce,
analyze, test, perform and/or display publicly, prepare derivative works,
distribute, and otherwise use Python 3.11.2 alone or in any derivative
version, provided, however, that PSF’s License Agreement and PSF’s notice of
copyright, i.e., “Copyright © 2001-2023 Python Software Foundation; All Rights
Reserved” are retained in Python 3.11.2 alone or in any derivative version
prepared by Licensee.
- In the event Licensee prepares a derivative work that is based on or
incorporates Python 3.11.2 or any part thereof, and wants to make the
derivative work available to others as provided herein, then Licensee hereby
agrees to include in any such work a brief summary of the changes made to Python
3.11.2.
- PSF is making Python 3.11.2 available to Licensee on an “AS IS” basis.
PSF MAKES NO REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED. BY WAY OF
EXAMPLE, BUT NOT LIMITATION, PSF MAKES NO AND DISCLAIMS ANY REPRESENTATION OR
WARRANTY OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE OR THAT THE
USE OF PYTHON 3.11.2 WILL NOT INFRINGE ANY THIRD PARTY RIGHTS.
- PSF SHALL NOT BE LIABLE TO LICENSEE OR ANY OTHER USERS OF PYTHON 3.11.2
FOR ANY INCIDENTAL, SPECIAL, OR CONSEQUENTIAL DAMAGES OR LOSS AS A RESULT OF
MODIFYING, DISTRIBUTING, OR OTHERWISE USING PYTHON 3.11.2, OR ANY DERIVATIVE
THEREOF, EVEN IF ADVISED OF THE POSSIBILITY THEREOF.
- This License Agreement will automatically terminate upon a material breach of
its terms and conditions.
- Nothing in this License Agreement shall be deemed to create any relationship
of agency, partnership, or joint venture between PSF and Licensee. This License
Agreement does not grant permission to use PSF trademarks or trade name in a
trademark sense to endorse or promote products or services of Licensee, or any
third party.
- By copying, installing or otherwise using Python 3.11.2, Licensee agrees
to be bound by the terms and conditions of this License Agreement.
 ) will be displayed if notifications are disabled
) will be displayed if notifications are disabled