Cisco Firepower DBL Configuration Guide
The guide outlined steps to automatically integrate DBL with Cisco Firepower. The maximum list size for DBL is 20,000. This maximum is subject to change without notice due to device specifications and performance.
Submit a ticket
To continue with this configuration guide you must first submit a ticket via the Samurai MDR portal. Add the following information within your request:
| Ticket field | Information |
|---|---|
| Title | DBL Onboarding Request for Cisco Firepower device(s) |
| Description | Add hostname and IP address (internet facing) of your Cisco Firepower devices. For example: mycfw1.acme.org, 19.16*.2*.2 If enrolling multiple devices please add each device on individual line* |
Submit the ticket and you will hear back from us with additional information (e.g DBL URL) to continue with the configuration below.
Connection Requirements
You will need to ensure your Firepower device(s) can reach a specific URL to obtain the DBL. This information will be provided to you once subscribed.
| Parameter | Note |
|---|---|
| Connection Port | TCP / 80 |
| DBL URL | NTT will provide a unique URL to you to download the DBL URL list |
Table 1: Connections requirements
To complete this integration you have to:
- Have submitted a ticket via the Samurai MDR portal and have been provided the necessary DBL endpoint URL/IP address.
From your Cisco Firepower Management Console (FMC):
- Create a feed that captures the DBL URLs
- Set Security Intelligence Settings for DBL URL
- Confirm Blocking
- Create a feed that captures the DBL IP list
- Set Security Intelligence Settings for DBL IP
Create a feed that captures the DBL URLs
Login to your FMC
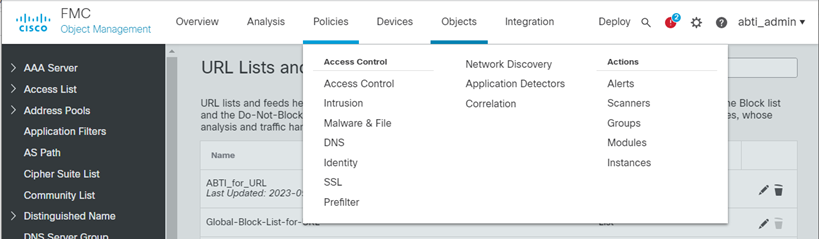
Click Objects – Object Management
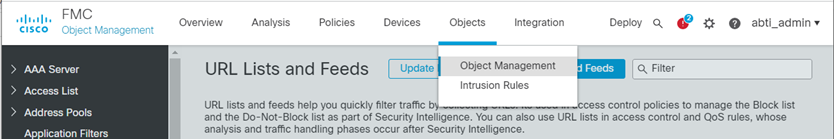
- Click Security Intelligence – URL Lists and Feeds in the left pane.
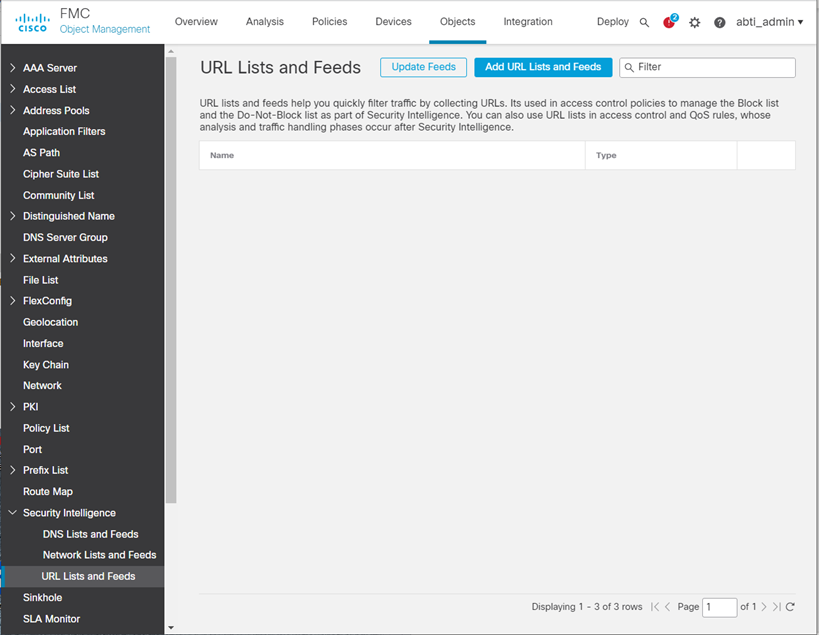
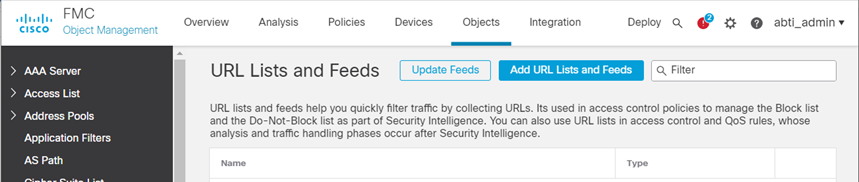
- Click Add URL Lists and Feeds
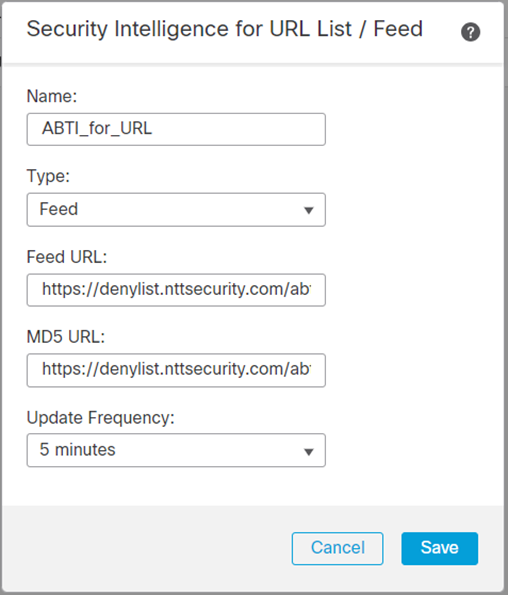
- Enter the following information in Security Intelligence for URL List/Feed and click Save
| Parameter | Entry |
|---|---|
| Name | whatever you want, in our example we have used ABTI_for_URL |
| Feed URL | Feed URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| MD5 URL | MD5 URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| Update Frequency | (Optional) - If you set the Update Frequency to less than 30 minutes, the MD5 URL is required |
Set Security Intelligence Settings
Set the feed you created in Create a feed that captures the DBL URLsto Security Intelligence.
- Click Policies – Access Control
- Select the Policy for which you want to set the Feed
(For example: Select sample-fp-policy as depicted below)
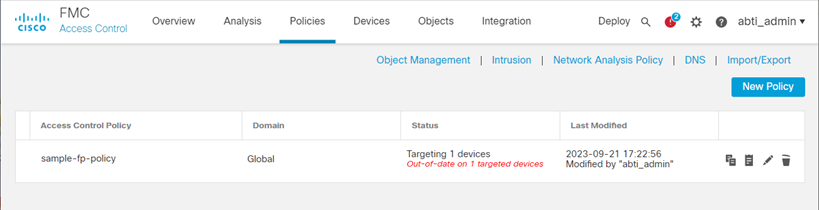
If you do not have a Policy, create one from New Policy and follow the procedure
Select Security Intelligence
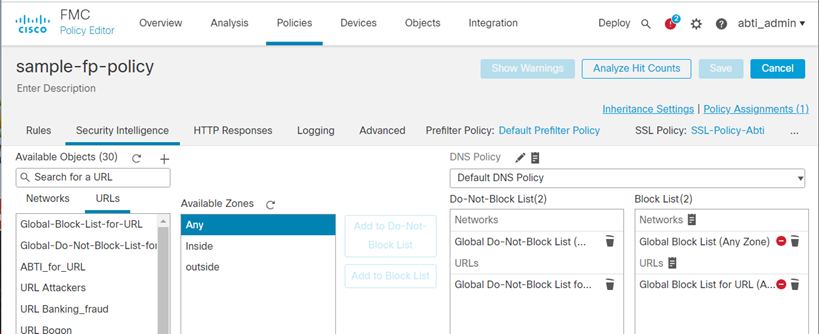
- Select URLs
- Select the Feed you created in Create a feed that captures the DBL URLs(our example was ABTI_for_URL)
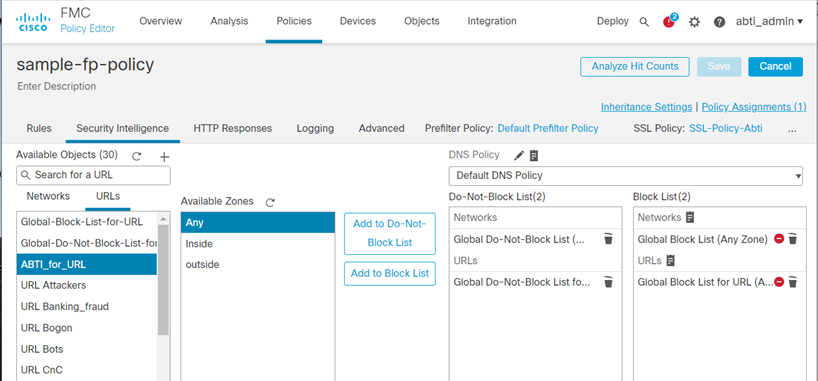
- Under Available Zones, select Any and click Add to Block List
- Click Save
- Click Deploy
Confirm Blocking
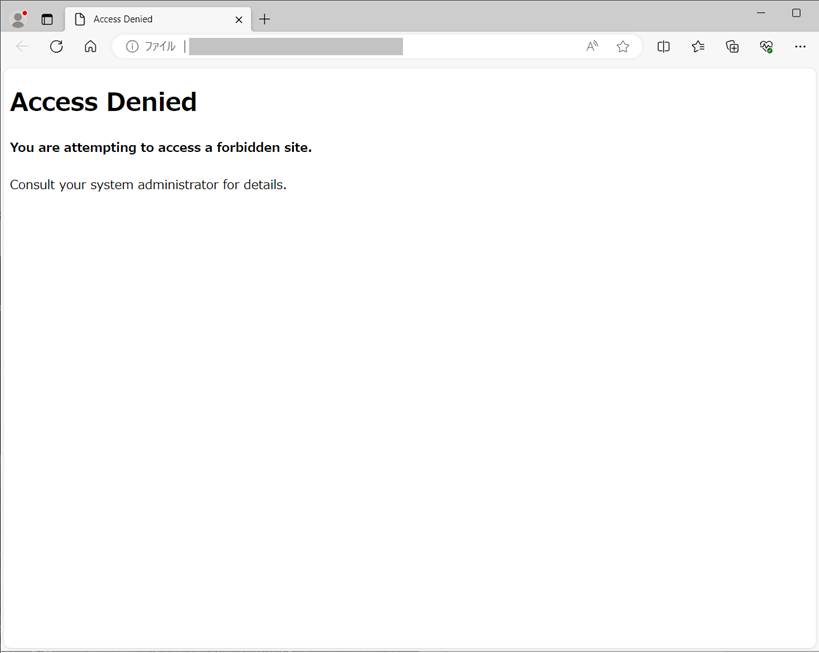
Verify that the test URL is blocked.
- From a browser that leverages the Cisco Firepower inspection path, access the following test URL:
- Verify that it is blocked. If blocking does not occur check through the configuration again. Our example block screen looks like this:
Create a feed that captures the DBL IP list
- Click Objects – Object Management
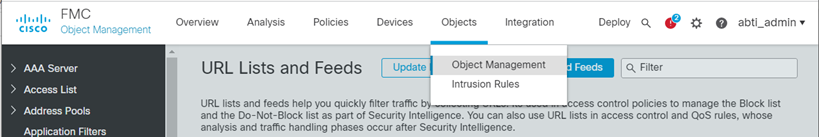
- Click Security Intelligence – Network Lists and Feeds in the left pane
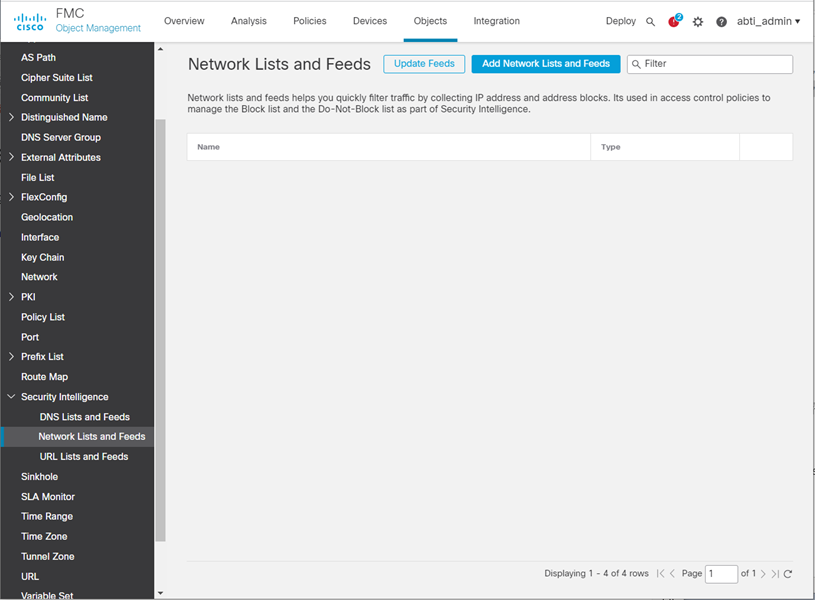
Click Add Network Lists and Feeds
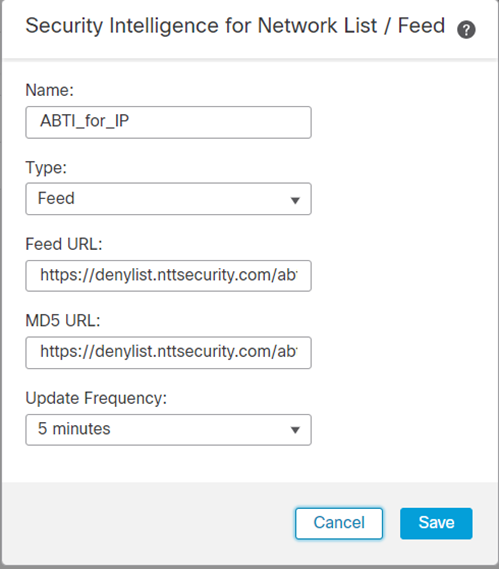
Enter the following information in Security Intelligence for URL List/Feed and click Save
| Parameter | Entry |
|---|---|
| Name | whatever you want, in our example we have used ABTI_for_IP |
| Feed URL | Feed URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| MD5 URL | MD5 URL will be provided to you upon enablement of the add-on Our screen captures display an example URL |
| Update Frequency | (Optional) - If you set the Update Frequency to less than 30 minutes, the MD5 URL is required |
Set Security Intelligence Settings for DBL IP
- Click Policies – Access Control**
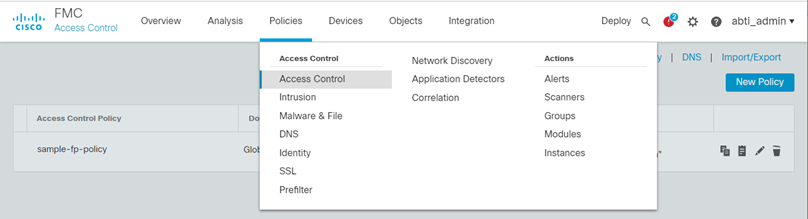
- Select the Policy for which you want to set the Feed
(For example: Select sample-fp-policy as depicted below)
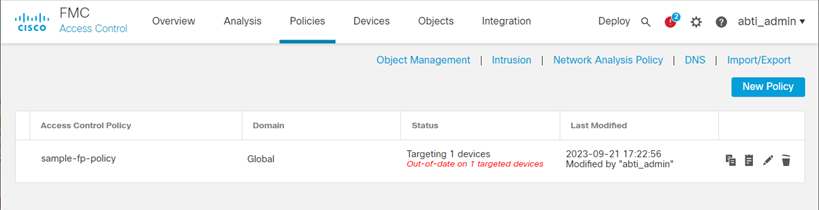
If you do not have a Policy, create one from New Policy and follow the procedure
Select Security Intelligence
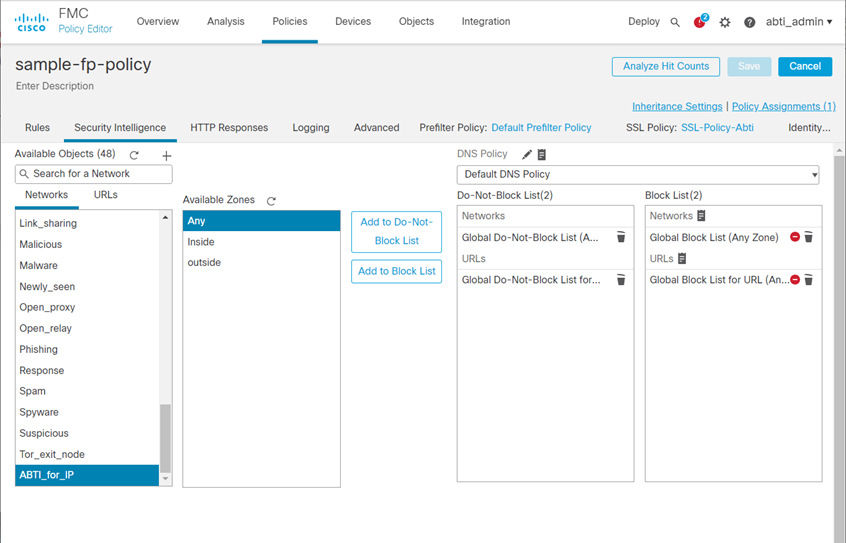
- Select Networks
- Select the Feed you created in Create a feed that captures the DBL IP list (our example was ABTI_for_IP)
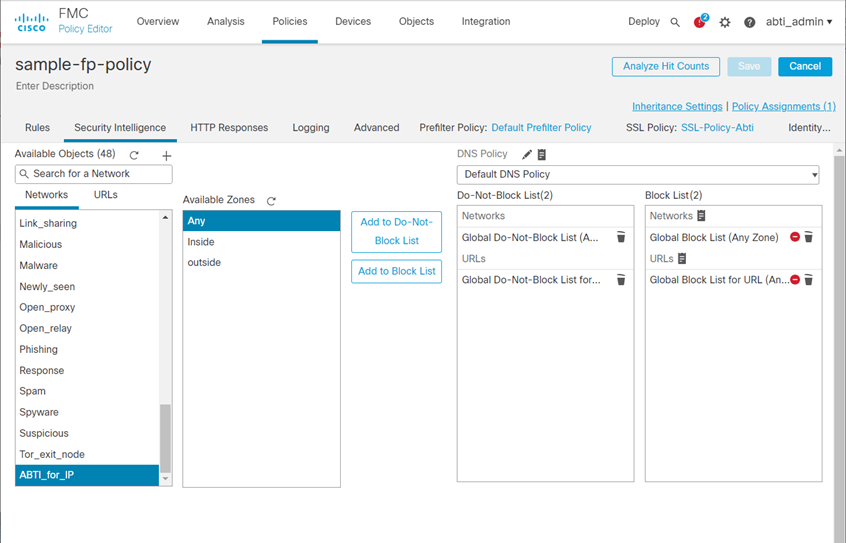
- Under Available Zones, select Any and click Add to Block List
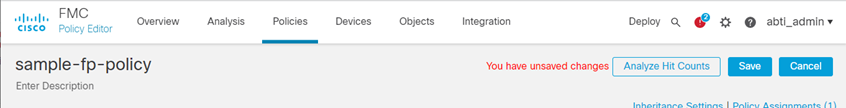
- Click Save
- Click Deploy
Our Dynamic Block List (DBL) configuration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a ticket in the Samurai MDR portal and we shall get it updated.