| SamurAI [Local] Collector | SamurAI [Cloud] Collector |
|---|---|
Supported Microsoft Security products
The Microsoft Graph Security API supports collection of alerts for multiple Microsoft Security products. An updated list can be found in the Microsoft documentation. Support for the following products has been validated by Samurai MDR:
- Microsoft Entra ID Protection
- Microsoft 365 Defender
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Microsoft Defender for Cloud
Prerequisites
The user must have Global administrative access to the Microsoft 365 Defender and Microsoft Azure Portal.
Recommended Advanced Settings for Defender for Endpoint
If you are a customer with the Incident Response (IR) Retainer, in order to ensure an optimal service delivery and a quick turnaround from activation to remediation by the NTT Incident Response team the below features are recommended to be enabled in Defender for Endpoint:
- Live response
- Live response for servers
- Live response unsigned script execution
Follow the Microsoft documentation - Configure advanced features in Defender for Endpoint to enable the features.
To complete this Integration you will need to perform actions in both the Azure Portal and SamurAI Portal:
1. Azure Portal
2. From the SamurAI Portal
- Complete the Microsoft Graph (Security) Integration
Application Registration
- Follow the steps outlined within section entitled Register an application in the Microsoft Graph API documentation using the following parameters.
Field Name Parameter Supported account type Accounts in this organizational directory only Redirect URL Leave blank
- Follow the steps outlined within section entitled Add a client secret in the Microsoft Graph API documentation.
- Follow the steps outlined within section entitled Configure permissions for Microsoft Graph in the Microsoft Graph API documentation. Select the following permissions.
SecurityAlert.Read.All
Enable the Samurai MDR SOC access to Microsoft 365 Defender
The steps outlined below are required for the Samurai SOC to perform remote isolation and further analysis through the Microsoft 365 Defender portal. You may also wish to refer to the Microsoft documentation - Granting managed security service provider (MSSP) access
Prerequisites
Ensure role-based access control (RBAC) is enabled in your Microsoft Defender Security Center.
To enable RBAC in Microsoft Defender Security Center, navigate to Settings > Permissions > Roles and Turn on roles from a user account with Global Administrator or Security Administrator rights.
This feature also requires an Entra ID P2 plan for the Privileged Identity Management feature.
Create an Entra ID Group and assign role
To create an Entra ID group for NTT, perform the following steps:
Log in to Entra ID admin center
Navigate to Groups > All groups > New group
Select Security from the Group type list
Ensure that Microsoft Entra roles can be assigned to the group is set to Yes
After creating the group, follow the steps in Assign Microsoft Entra roles to groups to assign the Security Reader role to the newly created group.
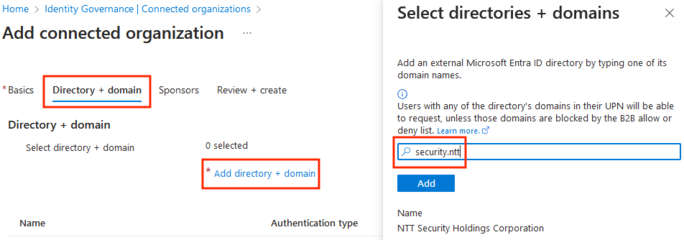
Add NTT as Connected Organization
Perform the following steps to add NTT as a connected organization:
- Navigate to Identity Governance
- Click Connected organizations
- Click Add connected organization
- On the Basics tab*,* specify a Name and Description
- On the Directory + domain tab, perform the following steps:
- Click Add directory + domain
- In the Select directories + domains field, search for security.ntt
Create a Resource Catalog
In the Entra ID portal under Identity Governance perform the following steps:
- Navigate to the Catalogs tab
- Click New catalog
- Specify a Name and Descriptions, keep other values default
- Click Create
Create an Access Package
An access package enables you to do a one-time set up of resources and policies that automatically administers access for the life of the access package.
To create a new access package, perform the following steps:
Navigate to Identity Governance
Click Access packages
Click New access package
Specify a Name and Description*,* select the Catalog created in the previous step
In the Resource roles tab, add the group created in previously and set Role to Member
In the Requests tab, ensure the following options are set (leave other settings as default):
Set Users who can request access to For users not in your directory
Under Select connected organizations, select NTT
Set Require approval to Yes
Under First Approver, add at least one fallback approver
Set Enable new requests to Yes
In the Lifecycle tab, set Access Reviews to No
After creating the access package provide the My Access portal link to NTT.
Define your Sponsors
Sponsors are the people responsible for approving requests made by NTT staff. You may define internal and/or external sponsors.
Internal sponsors are select individuals from within your organization who can approve requests from NTT. External sponsors are select individuals from within NTT who can approve these on your behalf.
NTT recommends selecting external sponsors and obtaining a list of names during the MDR Onboarding. These names include managers and team leads who support the service.
Setting up sponsors is a time-consuming process as it requires approving access requests from NTT staff. Therefore, NTT recommends you define external sponsors to enable NTT to manage this process.
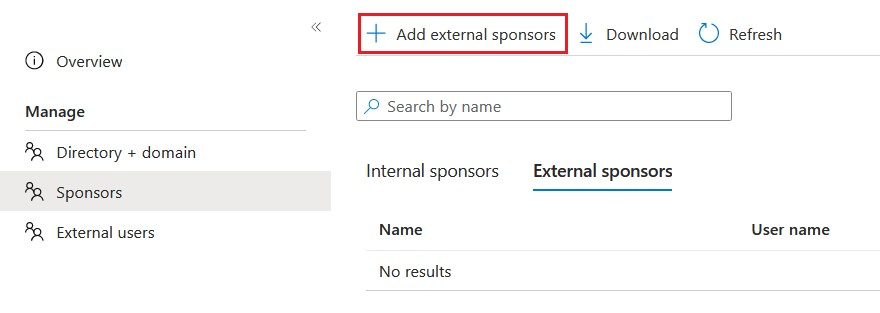
Initial NTT users will need to be approved by the selected Fallback approvers, after which they can be added as external sponsors.
To add external sponsors, select the Connected Organization and then Sponsors.
Complete the Microsoft Graph (Security) Integration
- Login to the SamurAI Portal
- Click Telemetry and select Integrations from the main menu
- Select Create
- Locate and click Microsoft Graph (Security)
- Click Next (we leverage a Samurai Cloud Collector)
- Enter Tenant ID, Application ID and Client Secret as created in Application Registration
- Click Finish
Our Integration guide was accurate at the time of writing but vendors change things frequently! If you find errors or anything is outdated, let us know by raising a request in the SamurAI MDR Portal and we shall get it updated.