Security Incidents
Security Incidents represent actionable security concerns or threat(s) identified as a result of an investigation by our SOC analysts. The Security Incident contains information about the threat(s) and how best to mitigate or minimize the risk.
Security Incidents are reported to you following our Incident Management process and are associated with tickets within the SamurAI Portal and downloadable in PDF format if desired.
Security Incident Notification
As per the Managed Detection and Response Service Description, notifications are provided by telephone or email based on severity:
- Critical severity: Phone / E-mail notifications.
- Low, Medium, High severity: E-mail notifications.
Information capture for notifications are completed during the MDR on-boarding process, however you can update contact details or telephone numbers by raising a ticket, during Threat Reviews and contact with your Cybersecurity Advisor (CSA).
Viewing Security Incidents
To access Security Incidents, click on  Security Incidents from the main menu.
Security Incidents from the main menu.
A visual indicator is displayed beside the Security Incidents menu item displaying the total number of Security Incidents that require your attention and are awaiting your response/action.
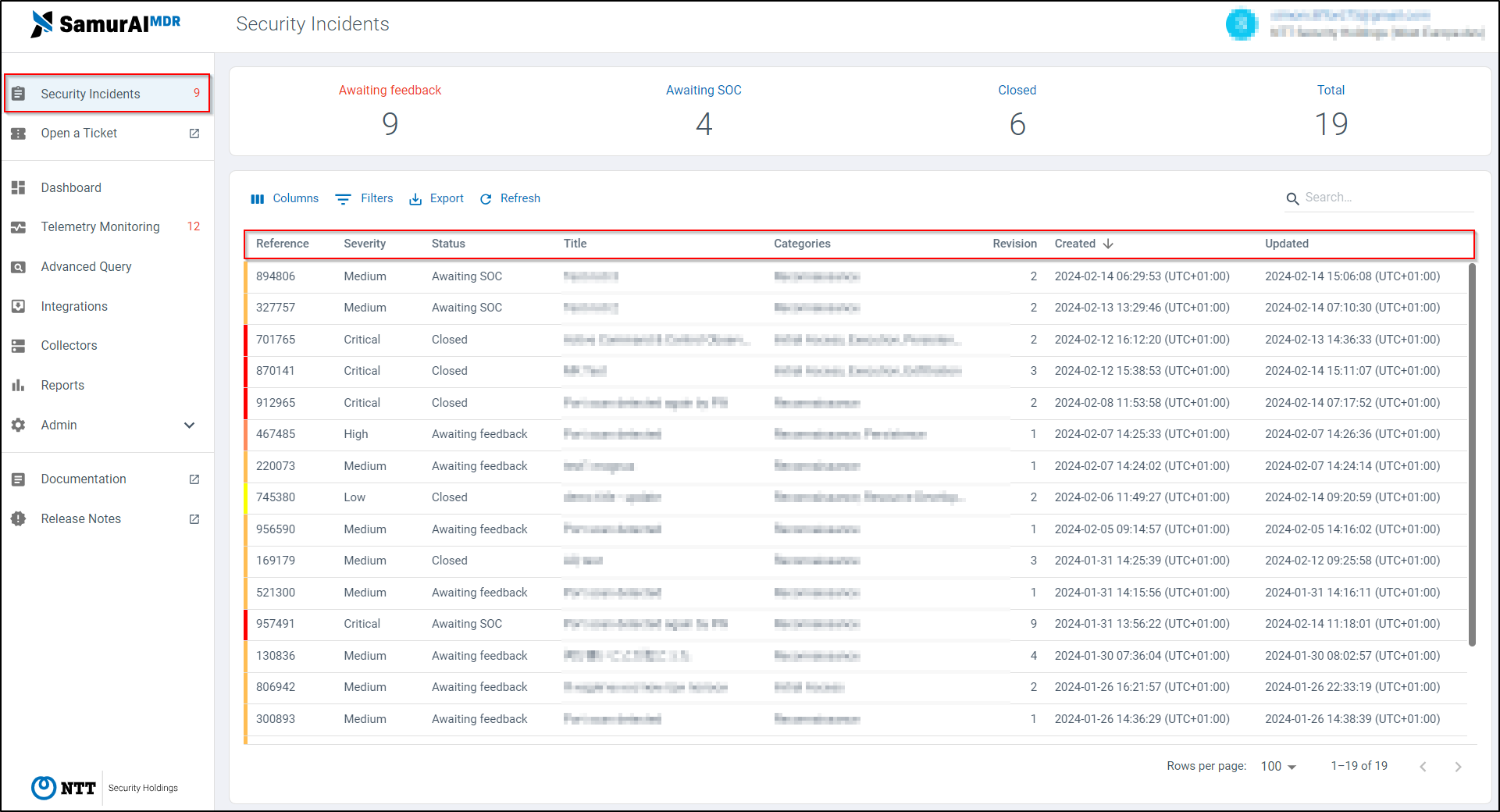
Figure 1: Example Security Incidents
Security Incident Dashboard

Figure 2: Example dashboard
The Security Incidents dashboard panel displays summary information as:
- Awaiting feedback: Security Incidents awaiting your feedback and/or action
- Awaiting SOC: Security Incidents awaiting response from the SOC
- Closed: all closed Security Incidents
- Total: Total Security Incidents
Security Incident Fields
Find information related to all Security Incident fields (outlined red in Figure 1):
1. Reference
- Reference number of the Security Incident.
2. Severity
- All Security Incidents are categorized with a severity that describes the reported threat.
| Severity | Description |
|---|
| Critical | Security Incidents with severe impact that threatens to have a significant adverse impact on the affected systems. These issues have a high probability of spreading or propagating, pose a threat to confidential or otherwise sensitive data or system. Critical security incidents require immediate attention for remediation or mitigation. |
| High | Security incidents where if exploited, these threats could lead to compromise of the system and/or loss of information. Should be investigated in a timely fashion. |
| Medium | Minor security incidents with low risk of spreading or propagation. Should be tracked and followed-up but generally medium threat severity incidents require no immediate action. |
| Low | Observed security related event that could be an indicator of threat or interesting from other perspectives but no direct security incident or threat. |
- The Security Analyst will make an informed decision in assigning the threat severity taking into consideration the specific situation and past experience.
- The assigned severity level will provide you an easy means to quickly assess how important a threat is, and the level of priority which should be assigned in addressing it. This will allow you to re-prioritize your actions so that you can start mitigating any threats quickly.
3. State
- Each Security Incident has an assigned state which quickly allows you to determine who is responsible for follow up.
| State | Description |
|---|
| Awaiting Feedback | Security Incident has been created or updated and is awaiting your feedback / response |
| Awaiting SOC | Security Incident is currently awaiting feedback / input from the SOC. |
| Closed | The Security Incident is Closed |
4. Title
- A “one-liner” that describes the content of the reported Security Incident. This field is used when listing tickets and within notifications.
5. MITRE ATT&CK
- To make it easier to understand the threat and perform additional mitigations actions, we categorize a threat according to tactics in the MITRE ATT&CK IT and OT framework.
A threat can be categorized with multiple MITRE tactics.
For more details about MITRE ATT&CK tactics:
Reflecting the MITRE tactics, provides the possibility to use MITRE techniques to do additional threat hunting and mitigation.
6. Revision
- If a threat changes, emerges or new relevant info is available, a new revision of the Security Incident will be created. The revision number is reflected in this field.
7. Created
- Date and time of creation of the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC).
8. Updated:
- Date and time of last update to the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC).
You can filter and sort on any of the available fields as well as disable and enable for your desired view. You can also export the list to CSV for download.
The search function will search within all incident details including comments and evidence.
What now?
Click on a Security Incident to view more detail and work directly with our SOC within the Situation Room.
1 - The Situation Room
We adopted the term ‘Situation Room’, often used by military and political establishments as an intelligence management center to monitor and deal with crisis situations.
The SamurAI MDR Situation Room is where you will find detailed information for any given Security Incident reported to you and allows you to communicate with our SOC Analysts.
Enter The Situation Room
To enter the Situation Room, click a Security Incident reported to you from the Security Incident List.

Figure 1: Example Situation Room
The Situation Room is structured as follows, click on the links to learn more:

Figure 2: Example incident information
To the left of the window, high level information about the Security Incident will be displayed, some of which is also summarized under the all Security Incidents menu. For clarity we have also included the field information below:
1. Incident Reference # / Title
- Reference number of the Security Incident
- A “one-liner” that describes the content of the reported Security Incident.
Any actions that the SOC have taken will be shown below the reference number and title e.g host isolation
2. Severity
- All Security Incidents are categorized with a severity that describes the reported threat.
| Severity | Description |
|---|
| Critical | Security Incidents with severe impact that threatens to have a significant adverse impact on the affected systems. These issues have a high probability of spreading or propagating, pose a threat to confidential or otherwise sensitive data or system. Critical security incidents require immediate attention for remediation or mitigation. |
| High | Security incidents where if exploited, these threats could lead to compromise of the system and/or loss of information. Should be investigated in a timely fashion. |
| Medium | Minor security incidents with low risk of spreading or propagation. Should be tracked and followed-up but generally medium threat severity incidents require no immediate action. |
| Low | Observed security related event that could be an indicator of threat or interesting from other perspectives but no direct security incident or threat. |
3. Status
- Each Security Incident has an assigned status which quickly allows you to determine who is responsible for follow up.
| State | Icon | Description |
|---|
| Awaiting Feedback |  | Security Incident has been created or updated and is awaiting your feedback / response |
| Awaiting SOC |  | Security Incident is currently awaiting feedback / input from the SOC. |
| Closed |  | The Security Incident is Closed. |
4. Created
- Date and time of creation of the Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default.
5. Updated
- Date and time of update to Security Incident in the format [yyyy:mm:dd], [hh:mm:ss] with time represented in Universal Time Coordinated (UTC) by default. This may indicate multiple revisions of the Security Incident.
6. MITRE Categories
- To make it easier to understand the threat and perform additional mitigation actions, we categorize a threat according to tactics in the MITRE ATT&CK IT and OT framework.
A threat can be categorized under multiple MITRE tactics.
For more details about MITRE ATT&CK tactics:
Reflecting the MITRE tactics, provides the possibility to use MITRE techniques to conduct additional threat hunting, respond and mitigate threats.
Towards the top of the window additional information is displayed:

Figure 3: Additional information
7. Revision
- If a threat changes, emerges or new relevant information is available, a new revision of the Security Incident will be created and the revision number displayed. e.g Revision 2,3,4.
- You are notified of any new revisions (which is also displayed within the Communication Channel) with the latest revision being displayed as default.
- Selecting the drop down allows you to select the revision number which will update details and evidence appropriately.
8. PDF
- Allows you to download the Security Incident and all details in PDF format.
9. Close Incident
- Allows you to Close the Security Incident.
10. Status
- Icon depiction of the current Security Incident Status. See item (3).
Details
Security Incident details are included within this section as:
Summary
A short summary of the Security Incident.
Description
In this section, the SOC clearly describes the relevant threat and outlines why this poses a risk. The description includes steps and findings through the analysis process where the SOC has used enrichment data and performed Threat Hunting and correlation. The SOC will add Evidence data to support the findings.
The Incident Description can be short or extensive depending on the what is needed to accurately describe the reported threat and associated risk.
Recommendations
A set of actionable mitigation step(s) that can be performed by you to mitigate the threat and bring it to closure. This may include signatures that we recommend to block.
The Recommendations might not be the only way to mitigate the threat. Rather, they provide a suggested approach from the SOC. Ultimately, the choice of the most appropriate mitigation approach rests with the client. When performing mitigation, it is also necessary to understand risks associated with mitigation actions, as there could be impacts on availability and in some cases even data loss could occur. These kinds of impacts may either be known side-effects of mitigation or there may be potential risks associated with errors which could occur during mitigation.
Hosts
Specific hosts applicable to the Security Incident are listed in the table with details which may include IP Address, Hostname, User, Endpoint ID and any actions taken by the SOC e.g if the SOC has isolated an endpoint.
Communication Channel
The Communications Channel provides messaging functionality allowing you to communicate with SOC Analysts in real-time. The editor allows you to construct and format text as desired, your messages are displayed to the left of the Communications Channel whilst all SOC messages are displayed to the right.
Emoji support is also available.
- Windows: Press Windows + . (period) to open the emoji picker.
- macOS: Press Control + Command + Space to open the emoji and symbol picker.

Figure 4: Communications channel
After typing your message ensure to click on
 Send Message
Send MessageEvidence
Evidence is provided with any given Security Incident to corroborate a SOC analyst investigation and ultimately the Security Incident.
Evidence may be included by the SOC analysts or by a user and will display a timestamp of when it was added building a timeline. Evidence may include:
- Alert data - vendor/product alerts and/or SamurAI platform alerts
- Log data- log data
- Files - e.g PCAP files if available
You can also upload supporting evidence for the security incident, click on Upload File and provide a description (optional) and select the file to upload. The maximum size limit for the file is 50MB.
Selecting the drop down  allows you to view or download the Evidence. For Log data you can pivot to Advanced Query by clicking the link to view the log data and complete further investigation as required.
allows you to view or download the Evidence. For Log data you can pivot to Advanced Query by clicking the link to view the log data and complete further investigation as required.
Indicators
If any Indicators of Compromise (IoC) have been identified applicable to the Security Incident, they will be listed in the table. Indicator types may include (but are not limited to):
- Domain
- IPv4 address
- IPv6 address
- IPv4 address with port
- IPv6 address with port
- MD5
- SHA1
- SHA256
- Email
- URL
At the SOC Analyst discretion, they may perform actions based on high confidence IoCs. This may include (based on the type of IoC):
- Add to Dynamic Block List with the intention for any technology subscribed to block the IoC.
- Perform an automated retroactive hunt leveraging the SamurAI Hunting Engine. This automated search is against the last 30 days of data stored within the SamurAI platform. Any findings may result in a new Security Incident.
- Perform a manual retroactive search in certain cases which fall outside of automated scope.
Change History
If there are multiple revisions of the Security Incident, a change history will be displayed providing full visibility into each change.
What Now?
Please refer to our Incident Management process as it is important you understand what is expected of you in the result of a Security Incident as well as our responsibilities.
 Security Incidents from the main menu.
Security Incidents from the main menu.





 allows you to view or download the Evidence. For Log data you can pivot to
allows you to view or download the Evidence. For Log data you can pivot to